
Welcome to the fourth article in the Check Point SandBlast Agent Management Platform series. In previous articles ( first , second , third ), we described in detail the interface and capabilities of the web management console, as well as reviewed the Threat Prevention policy and tested it against various threats. This article is devoted to the second security component - the Data Protection policy, which is responsible for protecting the data stored on the user's machine. We will also look at the Deployment and Global Policy Settings sections in this article.
Data Protection Policy

The Data Protection policy allows only authorized users to access data stored on a production machine using Full Disk Encryption and Boot Protection. The following options for configuring disk encryption are currently supported: for Windows - Check Point Encryption or BitLocker Encryption, for MacOS - File Vault. Let's consider in more detail the capabilities and settings of each of the options.
Check Point Encryption
Check Point Encryption is the standard disk encryption method in the Data Protection policy and encrypts all system files (temporary, system, remote) in the background without affecting the health of the user machine. After encryption, the drive becomes inaccessible to unauthorized users. The main setting for Check Point Encryption is "Enable Pre-boot", which enables users to authenticate before loading the operating system. This option is recommended for use because it prevents the use of authentication bypass tools at the operating system level. It is also possible to configure the temporary bypass parameters for the Pre-boot function:

- Allow OS login after temporary bypass — Pre-boot ;
- Allow pre-boot bypass (Wake On LAN – WOL) — pre-boot , Ethernet;
- Allow bypass script — Pre-boot Pre-boot;
- Allow LAN bypass — pre-boot .
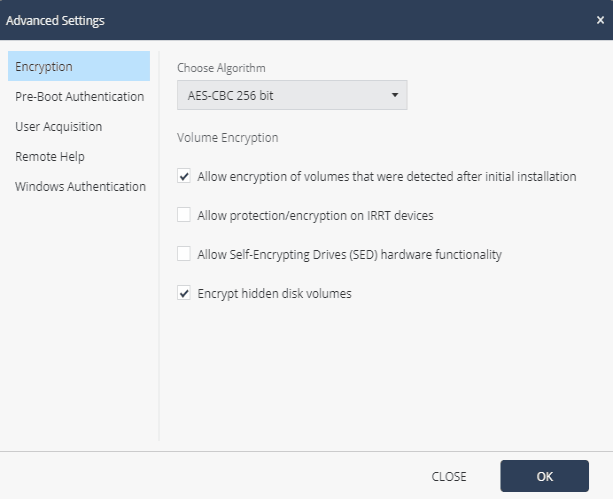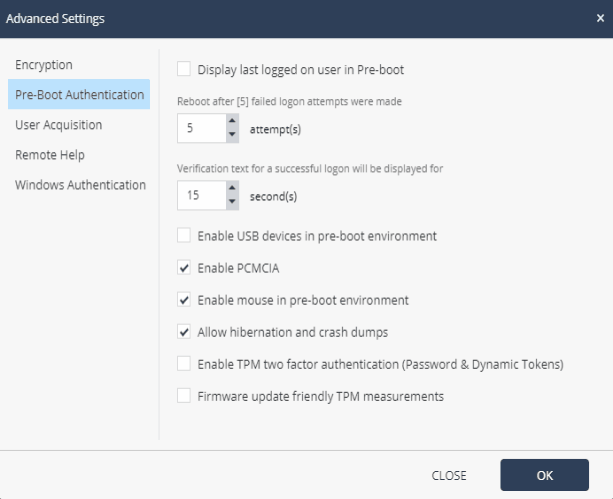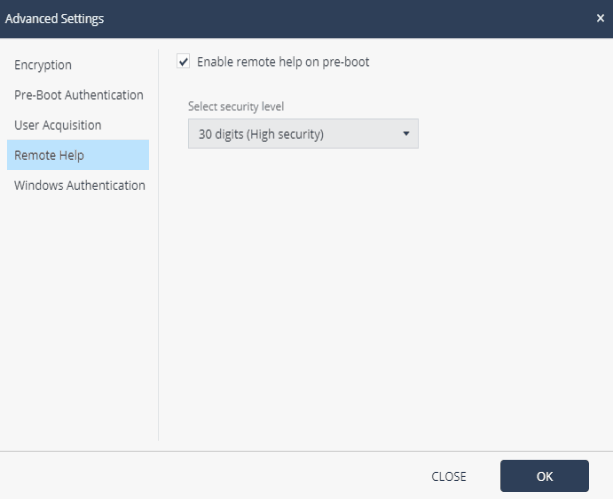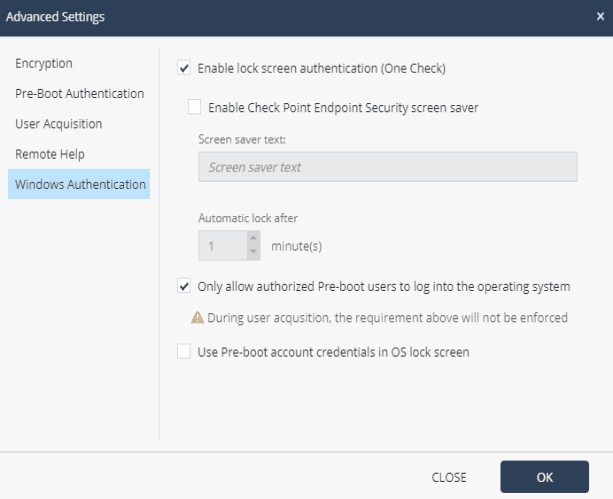
Pre-boot temporary bypass options above are not recommended for no apparent reason (such as maintenance or troubleshooting) and the best security solution is to enable Pre-boot without specifying temporary bypass rules. If it is necessary to bypass Pre-boot, it is recommended to set the minimum necessary time frames in the temporary bypass parameters so as not to reduce the protection level for a long time. Also, when using Check Point Encryption, it is possible to configure advanced settings for the Data Protection policy, for example, to more flexibly configure encryption settings, configure various aspects of the Pre-boot function and Windows authentication.
BitLocker Encryption
BitLocker is part of the Windows operating system and allows you to encrypt hard drives and removable media. Check Point BitLocker Management is a Windows Services component that automatically starts with the SandBlast Agent client and uses the BitLocker management API. When you select BitLocker Encryption as the drive encryption method in the Data Protection policy, you can configure the following options:
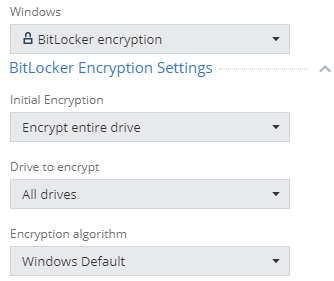
- Initial Encryption - initial encryption settings, allow you to encrypt the entire drive (Encrypt entire drive), which is recommended for machines with existing user data (files, documents, etc.), or encrypt only data (Encrypt used disk space only), which is recommended for new ones Windows installations;
- Drives to encrypt - select drives / partitions for encryption, allows you to encrypt all drives (All drives) or only a partition with an operating system (OS drive only);
- Encryption algorithm - the choice of an encryption algorithm, the recommended option is Windows Default, it is also possible to specify XTS-AES-128 or XTS-AES-256.
File Vault
File Vault is Apple's standard encryption tool and ensures that only authorized users can access the user's computer data. With File Vault installed, the user must enter a password to start the system and gain access to encrypted files. Using File Vault is the only way to ensure the protection of stored data in the Data Protection policy for users of the MacOS operating system.

For File Vault, the option “Enable automatic user acquisition” is available, which requires user authorization before starting the disk encryption process. If this function is enabled, it is possible to specify the number of users that must log in before SandBlast Agent applies the Pre-boot function, or specify the number of days after which the Pre-boot function will be automatically implemented for all authorized users, if during this period, at least one user is authorized in the system.
Data recovery
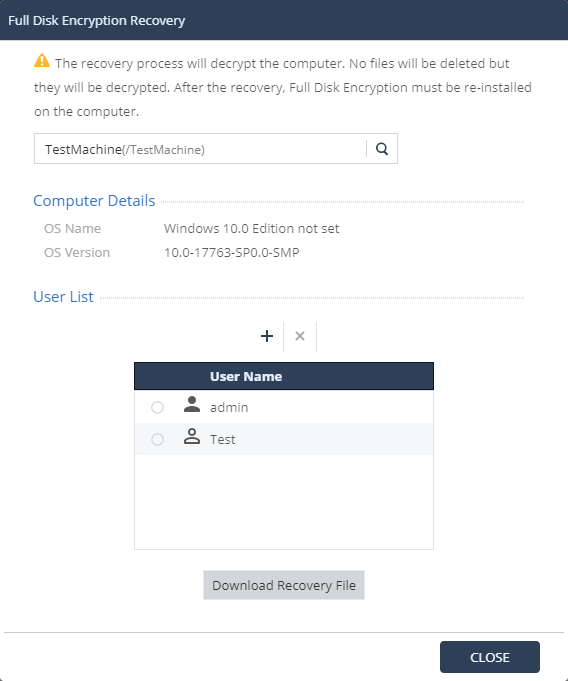
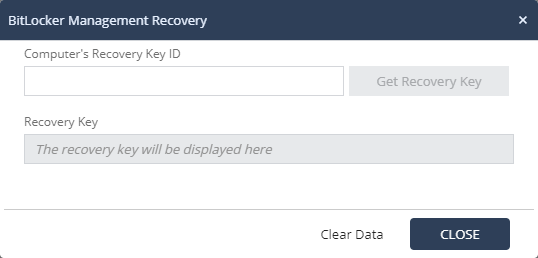
In case of problems with the system boot, you can use various methods of data recovery. The administrator can initiate the process of restoring encrypted data from the Computer Management → Full Dick Encryption Actions section. When using Check Point Encryption, you can decrypt the previously encrypted drive and gain access to all stored files. After this procedure, you must restart the disk encryption process for the Data Protection policy to work. When choosing BitLocker as the encryption method for the disk for data recovery, you must enter the Recovery Key ID of the problem computer to generate the Recovery Key, which must be entered by the user to gain access to the encrypted disk.
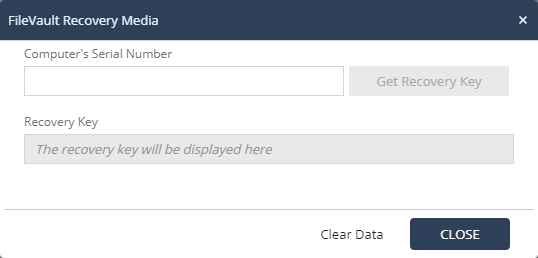
For MacOS users using File Vault to protect the stored information, the recovery process consists in the administrator generating a Recovery Key based on the Serial Number of the problem machine and entering this key, followed by a password reset.
Deployment policy
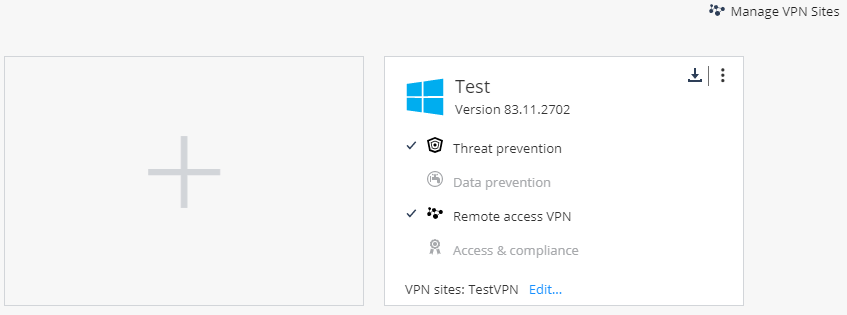
Since the release of the second article , which examined the web management console interface, Check Point managed to make some changes to the Deployment section - now it contains the Software Deployment subsection , in which the configuration (enabling / disabling blades) for already installed agents is configured, and the subsection Export Package , in which you can create packages with pre-installed blades for further installation on user machines, for example, using Active Directory Group Policies. Consider the Software Deployment subsection, which includes all SandBlast Agent blades.
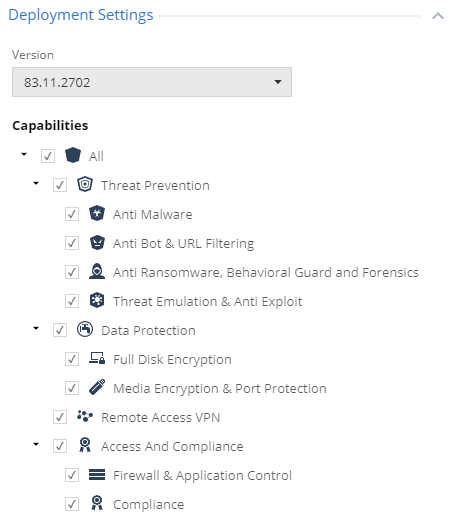
Let me remind you that only Threat Prevention blades are included in the standard Deployment policy. Taking into account the previously discussed Data Protection policy, you can now enable this category for installation and operation on a client machine with SandBlast Agent. It makes sense to enable the Remote Access VPN function, which will allow the user to connect, for example, to the corporate network of the organization, as well as the Access and Compliance category, which includes Firewall & Application Control functions and checking the user's machine for compliance with the Compliance policy.
Export Package
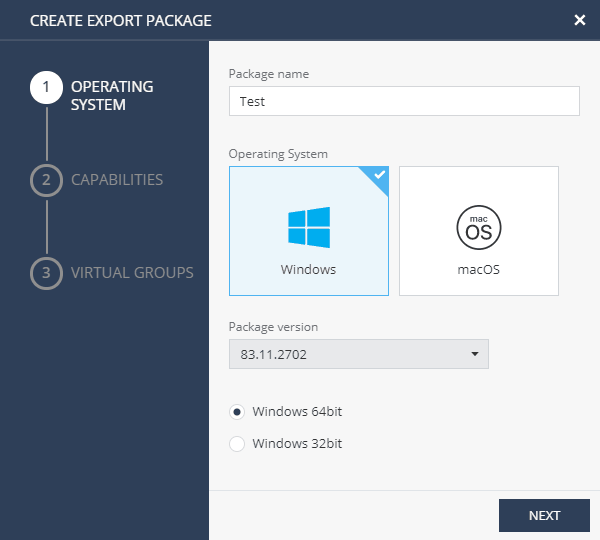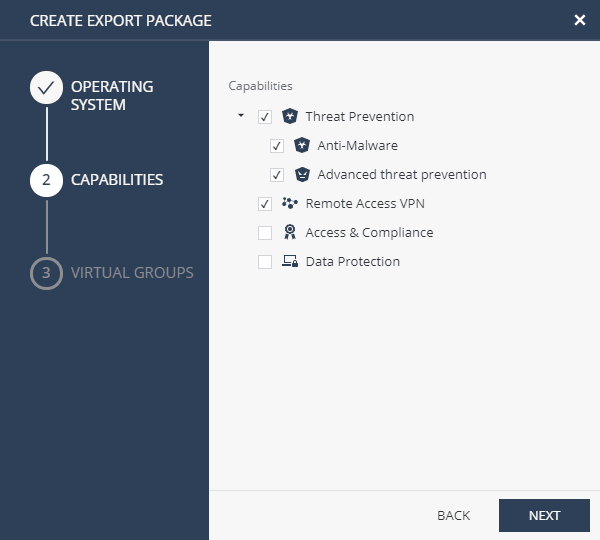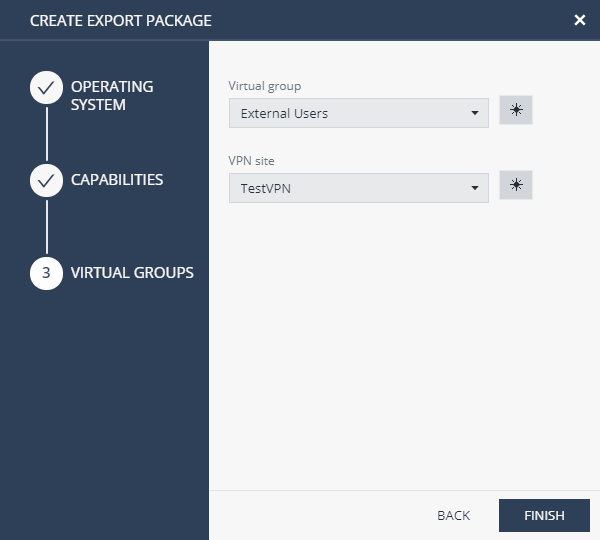
Export Packages : , ( Windows ) , . , , VPN Site (VPN Site Export Packages → Manage VPN Sites). , VPN.

Export Packages : , ( Windows ) , . , , VPN Site (VPN Site Export Packages → Manage VPN Sites). , VPN.

Global Policy Settings
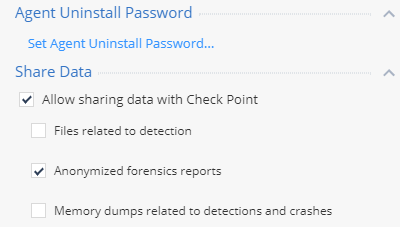
One of the most important parameters is configured in the Global Policy Settings - the password for removing SandBlast Agent from the user's machine. After installing the agent, the user will not be able to uninstall it without entering the password, which by default is the word " secret " (without quotes). However, this standard password is easy to find in public sources, and when implementing the SandBlast Agent solution, it is recommended to change the default password to remove the agent. In the Management Platform, with a standard password, the policy can be set only 5 times, so changing the password to delete is inevitable.
In addition, the Global Policy Settings configures data parameters that can be sent to Check Point to analyze and improve the ThreatCloud service.
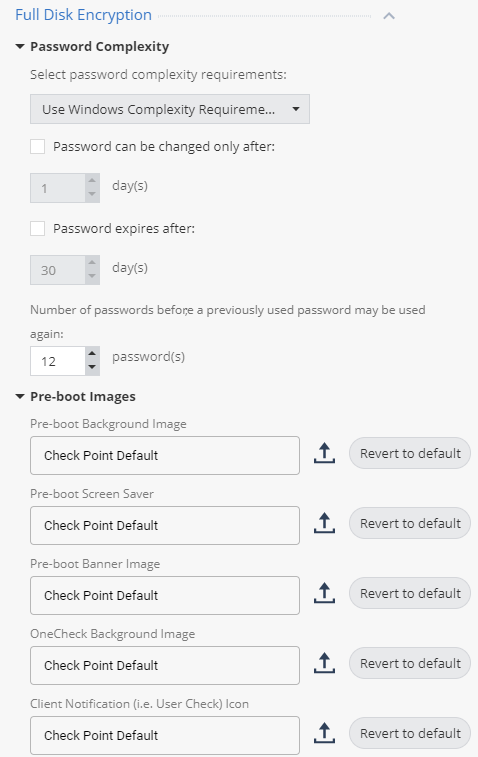
From the Global Policy Settings, some parameters of the disk encryption policy are also configured, namely, the password requirements: complexity, duration of use, the ability to use a previously valid password, etc. In this section, you can upload your own images instead of the standard ones for Pre-boot or OneCheck.
Install policy
After familiarizing yourself with the capabilities of the Data Protection policy and configuring the corresponding settings in the Deployment section, you can start installing a new policy that includes disk encryption using Check Point Encryption and the rest of the SandBlast Agent blades. After installing the policy in the Management Platform, the client will receive a message to install the new version of the policy now or move the installation to a different time (maximum 2 days). After downloading and installing the new policy, SandBlast Agent will prompt the user to restart the computer to enable Full Disk Encryption protection.
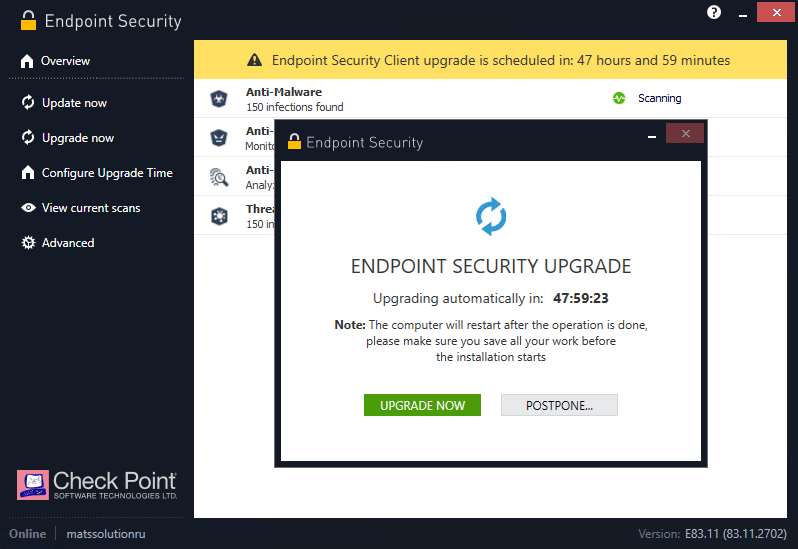
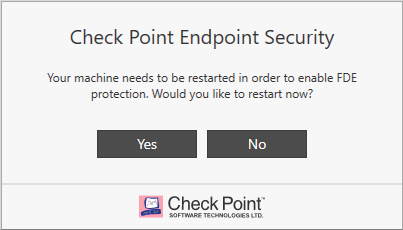
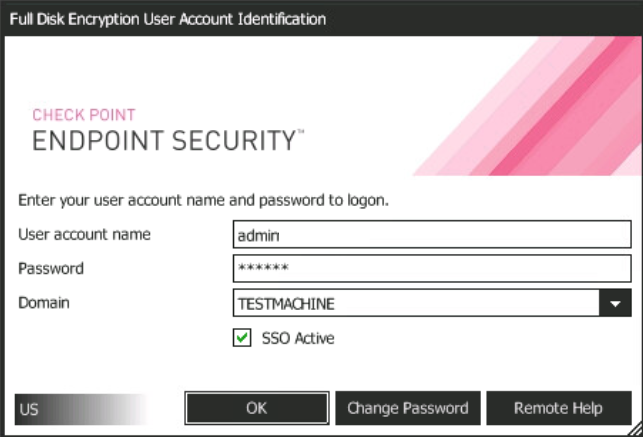
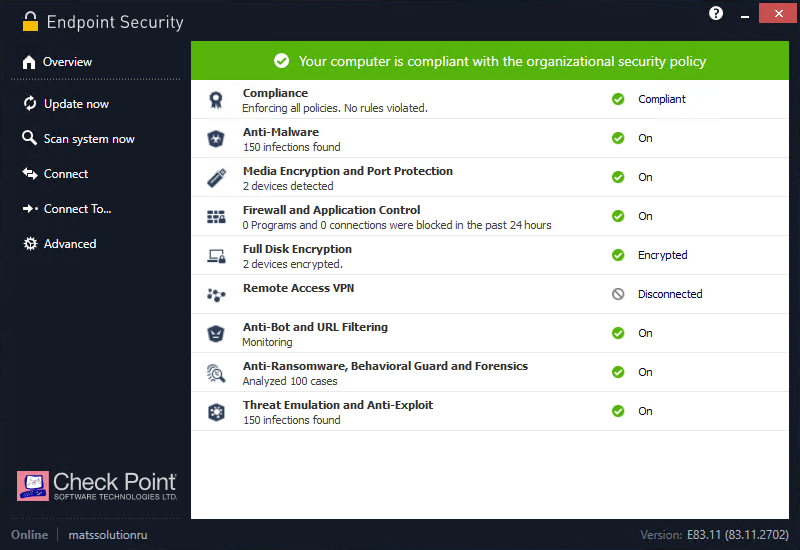
After rebooting, the user will need to enter their credentials in the Check Point Endpoint Security authentication window - this window will appear every time before the operating system starts (Pre-boot). It is possible to select the Single Sign-On (SSO) option to automatically use credentials for Windows authentication. In case of successful authentication, the user gains access to his system, and the disk encryption process begins behind the scenes. This operation does not affect the performance of the machine in any way, although it can take a long time (depending on the amount of disk space). Once the encryption process is complete, we can verify that all blades are up and running, the drive is encrypted, and the user's machine is protected.
Conclusion
To summarize: in this article, we examined the capabilities of the SandBlast Agent to protect information stored on the user's machine using disk encryption in the Data Protection policy, studied the settings for distributing policies and agents through the Deployment section and installed a new policy with disk encryption rules and additional blades on the user's machine ... In the next article in the series, we will take a closer look at the logging and reporting capabilities in the Management Platform and the SandBlast Agent client.
A large selection of materials on Check Point from TS Solution . In order not to miss the following publications on the SandBlast Agent Management Platform - follow the updates on our social networks ( Telegram , Facebook , VK ,TS Solution Blog , Yandex.Zen ).