Here is the interface of a typical password generator :
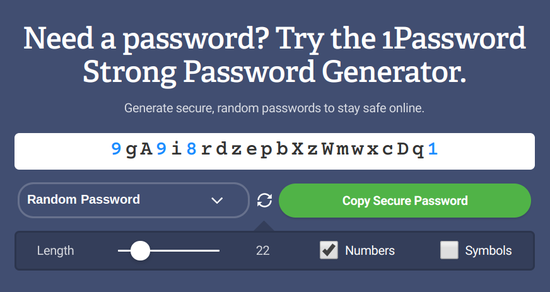
Pay attention to the Length slider: here it can change the password length from 8 to 100 characters, and in other tools it can be much more. What is the best value for passwords?
A good password is all you have when you get hacked
To understand what a good password is, let's see what happens in the camp of the enemy!
When you create an account, the service saves your password in one of numerous formats. The service can put the password directly into the database (in plain text) or generate a hash from it using one of numerous algorithms . Most Popular:
- MD5
- SHA-1
- Bcrypt
- Scrypt
- Argon2
The advantage of storing hashes instead of the passwords themselves is that there are no passwords in the database . And that's right, because you only need to prove that you know your password, but it doesn't matter. When you login, the entered password is hashed using the same algorithm, and if the result matches the value recorded in the database, then you have proven that you know the password. And if the database is hacked, then it will not be possible to recover passwords.
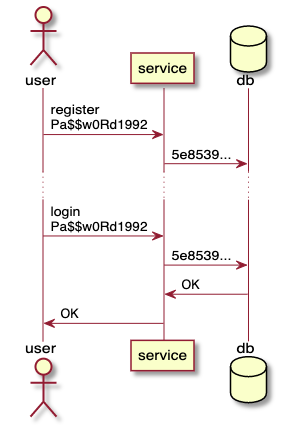
Storing hashes.
Cracking password
Password cracking is when an attacker tries to reverse a hash function and recover a password from the hash. With a good hashing algorithm, this is impossible. But nothing prevents an attacker from trying to enter different values in the hope of getting the same hash. If a match occurs, then the password has been recovered from the hash.
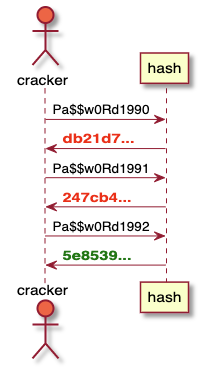
Cracking a password.
And here the choice of a good algorithm is important . SHA-1 was designed with fast hashing in mind, making life easier for attackers. Bcrypt, Scrypt and Argon2 were designed with high computational costs in mind to slow down cracking as much as possible, especially on dedicated machines. And this is a very important aspect.
If you focus only on the speed, the password SHA-1, which is impossible to crack, as follows:
0OVTrv62y2dLJahXjd4FVg81.
A secure password that you created using a properly configured Argon2, looks like this:
Pa$$w0Rd1992.
As you can see, choosing the correct hashing algorithm turns a weak password into an unbreakable one.
And don't forget thatit only depends on the implementation of the service you are registering with . And you cannot know the quality of the implementation. You can ask, but either they will not answer you, or they will unsubscribe that "we are serious about security."
Do you think companies take security seriously and use good hashing algorithms? Take a look at the list of compromised databases, especially the hashes used in them. In many cases, MD5 was used, most often SHA-1, and bcrypt was used in some places. Some stored passwords in plain text . This is the reality to be considered.
Moreover, we only know which hashes were used in the compromised databases, and it is highly likely that companies that used weak algorithms were unable to protect their infrastructure. Take a look at the list, I'm sure you'll find familiar names. Just because a company looks big and respectable doesn't mean it's doing everything right.
You choose the password
What can you do as a user? If passwords are stored in plain text, then there's nothing to be done. Once the database is stolen, the complexity of your password won't matter.
With properly configured algorithms, the complexity of your password is also not important, it can be
12345or asdf.
However, in intermediate cases , especially when using SHA-1, the complexity of the password matters . Hashing functions are generally not designed for passwords, but if you are using a complex password, it compensates for the algorithms' weaknesses.
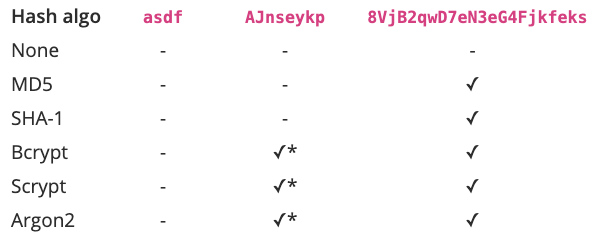
Depends on the configuration. These algorithms have various security components and, if properly configured, can prevent hacking.
Conclusion: with a strong password, you are protected from more hacks than with a weak password. And since you don't know how secure the password store is, you cannot know how “secure enough” the service will be. So assume the worst when your choice of password still matters.
Password uniqueness is not enough
Okay, but why on earth would you think about using a password manager and generating a unique password for each site? In this case, you are invulnerable to credential stuffing - when a known pair of mailbox and password is checked on different services in the hope that the person used this data in different places. This is a serious threat because password reuse is one of the top security concerns. You will be protected from this by generating a unique password for each site.
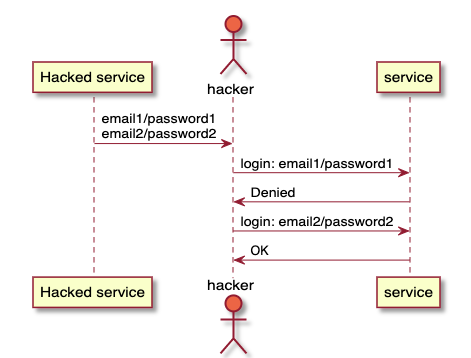
Credential stuffing.
And if the database is stolen and all its contents become known to hackers, then why would you still protect your password?
The fact is that you do not know if the database has been hacked and you continue to use the service. Then hackers will have access to all your future activity on this site. You can add your bank card details later and they'll know about it. A strong password means that hackers will not be able to log in under your account and will not be able to compromise your future actions.
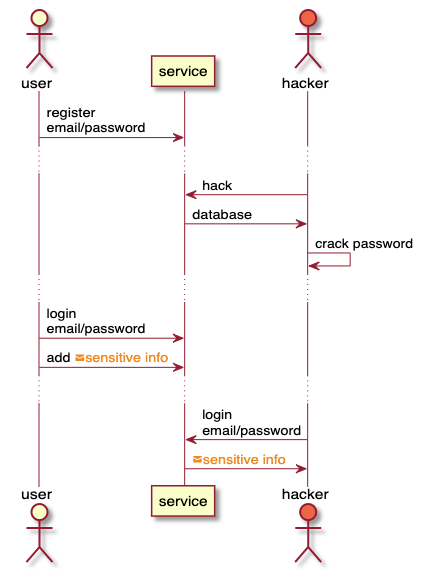
Using the service after hacking.
How to evaluate password strength using entropy
The strength of a password is characterized by entropy - a numerical representation of the amount of randomness that is contained in the password. Since we are talking about large numbers, it
1 099 511 627 776 (2^40)is easier for us to say “40 bits of entropy” instead . And since cracking a password is an enumeration of options, the more there are, the more time you need to spend on cracking.
For random characters generated password manager, the entropy is calculated by the following formula:
log2(< > ^ <>).
It's clear with the length, but what is the number of different characters? It depends on the character classes included in the password.

For example, a password of 10 random uppercase and lowercase letters has a
log2(52 ^ 10) = 57 bit of entropy.
To calculate the specific entropy (its amount in one symbol of a given class), you can use the equation
log2(n ^ m) = m * log2(n). We get:, <> * log2(< >)where the second part is the specific entropy. Let's recalculate the previous table using this formula:

To calculate the strength of a password, you need to take the character classes that are included in the password, take the entropy values for these classes and multiply by the length. For the example above, we got a 10 uppercase and lowercase password
5.7 * 10 = 57 . But if you increase the length to 14, then the entropy will jump to 79.8 bits. And if you leave 10 characters, but add a class of special characters, then the total entropy will be 64 bits.
The above equation allows you to quickly calculate the entropy of the password, but there is a catch. The formula is correct only if the symbols are independent of each other . And this only applies to the generated passwords. The combination
H8QavhV2gusatisfies this criterion and has 57 bits of entropy.
But if you use easier-to-remember passwords like
Pa$$word11, then their entropy will be much lower with the same number of symbols. The cracker does not have to go through all possible combinations; he just needs to go through the words from the dictionary with some changes.
Thus, all calculations with multiplying the length by the specific entropy are only valid for the generated passwords .
Entropy Guide
The more entropy a password has, the more difficult it is to crack it. But how much entropy is enough? In general, about 16 characters will be behind the eyes, such a password has 95-102 bits of entropy, depending on the character classes. What is the minimum threshold? 80 bit? 60? Or even 102 bits are too small?
There is an algorithm that rivals a bad hashing algorithm in speed, but it is much better studied: this is AES.
It is used in all government and military organizations, which means its durability is sufficient. And it works fast. So if an AES key with a certain amount of entropy cannot be cracked, then a password with a bad (but not cracked) hash will benefit.
The National Institute of Standards and Technology has determined the key sizes that will be sufficient for the foreseeable future. Thererecommend using AES-128 during the "2019-2030 and later" period. As the name implies, we are talking about 128 bits of entropy.
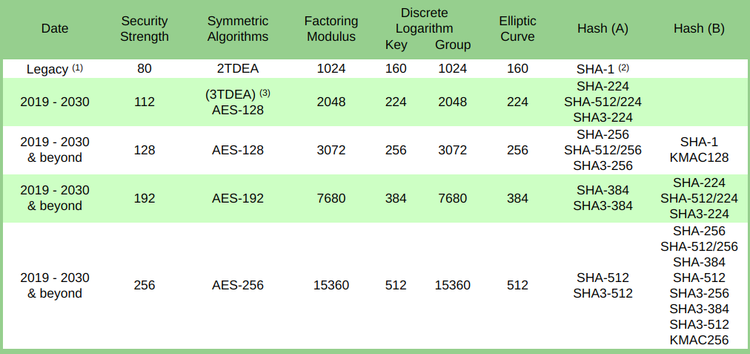
Another recommendation recommends making keys at least 112 bits in size:
To provide cryptographic strength for the needs of the Federal Government, at least 112 bits are required today (for example, for encrypting or signing data).
To get 128 bits of entropy using uppercase and lowercase letters and numbers, you need a password length
22 ((5.95 * 22 = 131 ).
Other considerations
Why not use special characters? I try not to use them because they break the boundaries of the word. That is, it takes three clicks to select a special character instead of two, and this can lead to an error if I do not accidentally insert the rest of the password into the field.
And if you use only letters and numbers, then with a double click, the entire password will be highlighted.
What if there is a length limit? On some sites, the password cannot be up to 22 characters long. Sometimes passwords can only be very short, for example, no more than 5 digits. Then all that remains is to use the password as long as possible.
There are also guidelines for password sites, and the length limitation clearly conflicts with these guidelines. Here's what says National Institute of Standards and Technology:
You must support passwords up to at least 64 characters long. Encourage users to make easy-to-remember secrets of any length, using any characters (including spaces) to help them remember.
And remember, sites' password protection ranges from terrible to excellent, and they won't tell you what the real situation is. If the maximum allowable password length is small, then it seems that such a site is on the bad end of the scale.
Conclusion
Passwords should be strong, even if you don't use the same combinations in different places. The strength of a password is measured by entropy, and you need to strive for a value of 128 bits. Passwords with a length of 22 characters, consisting of uppercase and lowercase letters and numbers, are sufficient for this.
This will protect you in the event that the service is compromised and a weak but not compromised hashing algorithm is used.