
We write regularly about how hackers often rely on non-malicious hacking techniques to avoid detection. They literally “survive on the grass” using standard Windows tools, thereby bypassing antiviruses and other utilities for detecting malicious activity. As defenders, we now have to deal with the dire consequences of such clever hacking techniques: a well-placed employee can use the same approach to stealthily steal data (company intellectual property, credit card numbers). And if he takes his time, but works slowly and unnoticed, it will be extremely difficult - but still possible, with the right approach and the right tools - to detect such activity.
On the other hand, I would not want to demonize employees, since no one wants to work in a business environment straight from Orwell's 1984. Fortunately, there are a number of practical steps and life hacks that can make life a lot harder for insiders. We will look at the stealthy attack methods used by hackers by employees with some technical background. And a little further we will discuss options for reducing such risks - we will study both the technical and organizational options for action.
What's wrong with PsExec?
Edward Snowden, rightly or not, has become synonymous with insider data theft. By the way, don't forget to take a look at this post about other insiders who also deserve some fame status. One important point to emphasize about the methods that Snowden used is that as far as we know, he did not install any external malicious software!
On the contrary, Snowden applied a bit of social engineering and used his position as a system administrator to collect passwords and create credentials. Nothing fancy - no mimikatz , man-in-the-middle attacks or metasploit .
Organizations are not always in Snowden's unique position, but there are a number of lessons to be aware of from the concept of “grazing survival” - not to perform any harmful actions that can be detected, and be especially careful about using credentials. Remember this thought.
Psexec and its cousin crackmapexec have impressed countless pentesters, hackers and information security bloggers. And in combination with mimikatz, psexec allows attackers to navigate within the network without having to know the clear text password.
Mimikatz intercepts the NTLM hash from the LSASS process, and then passes the token or credentials - the so-called. "Pass the hash" attack- in psexec, allowing an attacker to log on to another server on behalf of another user. And with each subsequent move to a new server, the attacker collects additional credentials, expanding the range of his capabilities in finding available content.
When I first started working with psexec, it seemed magical to me - thanks to Mark Russinovich , the genius psexec developer - but I also know about its noisy components. He's never secretive!
The first interesting fact about psexec is that it uses Microsoft's extremely complex SMB network file protocol . Psexec uses SMB to send small binaryfiles to the target system by placing them in the C: \ Windows folder.
Next, psexec creates a Windows service using the copied binary and starts it under the extremely "unexpected" name PSEXECSVC. At the same time, you can actually see all this, as I did, watching the remote machine (see below).

Psexec calling card: "PSEXECSVC" service. It launches a binary file that was placed over SMB in the C: \ Windows folder.
As a final step, the copied binary opens an RPC connection to the target server and then accepts control commands (by default through the Windows cmd shell), running them and redirecting input and output to the attacker's home machine. In this case, the attacker sees the basic command line - the same as if he was connected directly.
Lots of components and a very noisy process!
Psexec's sophisticated internal process explains the message that puzzled me during my first tests a few years ago: "Starting PSEXECSVC ..." followed by a pause before the command line appears.
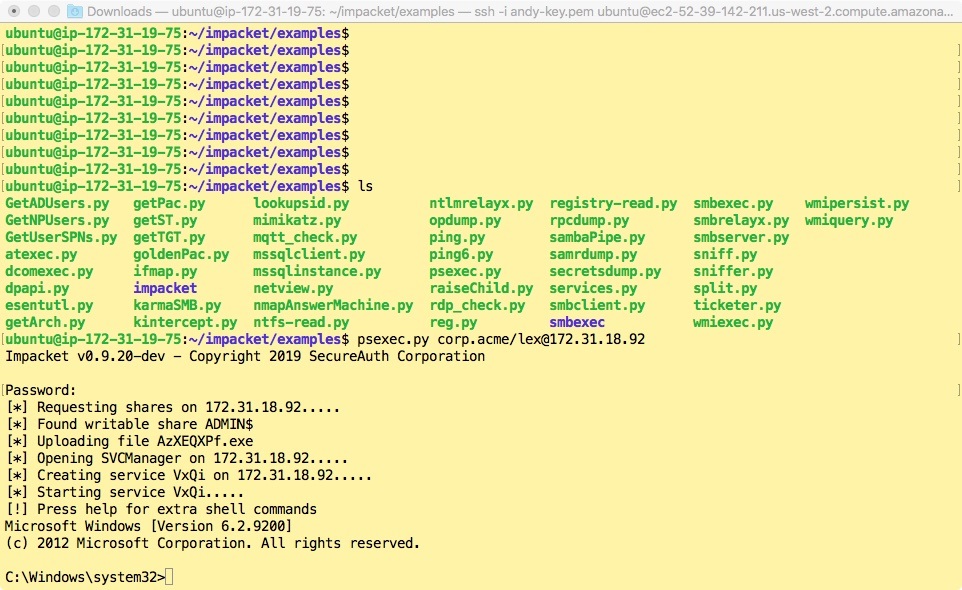
Psexec from Impacket really shows what's going on under the hood.
No wonder: psexec did a lot of work under the hood. If you are interested in a more detailed explanation, check out this great description here.
Obviously, when used as a system administration tool, which was the original purpose of psexec, there is nothing wrong with the buzzing of all these Windows mechanisms. For an attacker, however, psexec would create complications, and for a cautious and cunning insider like Snowden, psexec or a similar utility would be too much of a risk.
And then comes Smbexec
SMB is a clever and stealthy way of transferring files between servers, and hackers have infiltrated SMB directly for centuries. I suppose everyone already knows that you shouldn't open SMB ports 445 and 139 to the Internet, right?
At Defcon in 2013, Eric Milman ( brav0hax ) released smbexec so that penetration testers could try out stealthy SMB hacking. I don't know the whole story, but then Impacket refined smbexec further. In fact, for my testing, I downloaded the scripts from Impacket in python from Github .
Unlike psexec, smbexec avoidstransferring a potentially detectable binary file to the target machine. Instead, the utility lives entirely off the grass by running the local Windows command line.
This is what it does: it sends a command from the attacking machine via SMB to a special input file, and then creates and runs a complex command line (like a Windows service) that will seem familiar to Linux users. In short: it launches a native Windows cmd shell, redirects the output to another file, and then sends it over SMB back to the attacker's machine.
The best way to understand this is to study the command line, which I was able to grab from the event log (see below).
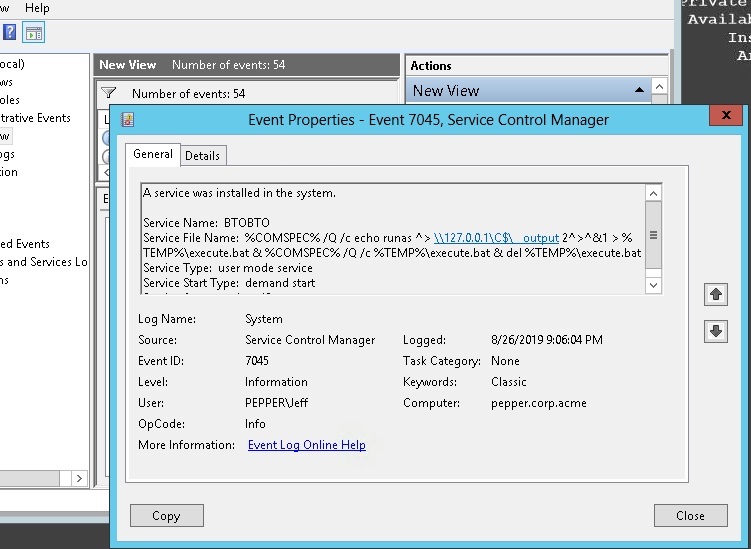
Isn't this the greatest way to redirect I / O? By the way, service creation has event ID 7045.
Like psexec, it also creates a service that does all the work, but the service is then removed - it is only used once to run the command and then disappears! An information security officer monitoring the victim's machine will not be able to detect obvious indicators of an attack: there is no malicious executable file, no persistent service is installed, and there is no evidence of RPC being used, since SMB is the only means of transferring data. Brilliant!
At the same time, a "pseudo-shell" is available from the attacker's side with delays between sending a command and receiving a response. But this is quite enough for an attacker - either an insider or an outside hacker who already has a foothold - to start looking for interesting content.

To output data back from the target machine to the attacker's machine, smbclient is used . Yes, this is the same Samba utility , but modified for the Python script by Impacket. In fact, smbclient allows you to covertly organize FTP over SMB transfers.
Let's take a step back and think about what it can do for the employee. In my fictional scenario, let's say a blogger, financial analyst, or high-paid security consultant is allowed to use a personal laptop for work. As a result of some magical process, she takes offense at the company and "goes all out." Depending on the laptop operating system, it either uses the Python version from Impact, or the Windows version of smbexec or smbclient as an .exe file.
Like Snowden, she learns another user's password either by peeping it over her shoulder, or she is lucky and she stumbles upon a text file with the password. And using these credentials, she begins to dig around the system at a new level of privileges.
Hacking DCC: We Don't Need Any Stupid Mimikatz
In my previous pentest posts, I used mimikatz a lot. This is a great tool for intercepting credentials - NTLM hashes and even clear-text passwords hidden inside laptops and waiting to be used.
Times have changed. Monitoring tools have become better at detecting and blocking mimikatz. Information security administrators have also gained more options to mitigate the risks associated with pass the hash attacks (hereinafter referred to as PtH).
So what does a smart employee have to do to collect additional credentials without using mimikatz?
Impacket includes a utility called secretsdumpwhich fetches credentials from the Domain Credential Cache, or DCC for short. As far as I understand, if a domain user logs into the server, but the domain controller is not available, DCC allows the server to authenticate the user. Anyway, secretsdump allows you to dump all of these hashes, if available.
DCC hashes are not NTML hashes and cannot be used for a PtH attack .
Well, you can try to crack them to get the original password. However, Microsoft got smarter with DCC and it became extremely difficult to crack DCC hashes. Yes, there is hashcat , "the world's fastest password picker," but it requires a GPU to run efficiently.
Instead, let's try to think like Snowden. The employee can do face-to-face social engineering and possibly find out some information about the person whose password she wants to crack. For example, find out if this person's online account has ever been hacked and examine their clear text password for any clues.
And this is the scenario that I decided to go. Let's suppose that an insider finds out that his boss, Cruella, has been hacked several times on different web resources. After analyzing several of these passwords, he realizes that Cruella prefers to use the baseball team name format "Yankees" followed by the current year, "Yankees2015".
If you are currently trying to reproduce this at home, you can download a small, "C"code that implements the DCC hashing algorithm and compile it. John the Ripper added DCC support by the way, so you can use it too. Let's assume an insider doesn't want to get involved in learning about John the Ripper and likes to run "gcc" in legacy C code.
While portraying the role of an insider, I ran several different combinations and in the end I was able to find that Cruella's password was "Yankees2019" (see below). Mission Complete!

With a little social engineering, a bit of fortune telling, and a pinch of Maltego, you're on your way to cracking the DCC hash.
I propose to end this. We'll come back to this question in other posts and look at even more slow and stealthy attack methods, while continuing to rely on the excellent set of utilities from Impacket.