
With every update to .Net Core, Microsoft proves that .Net Core is the most powerful, versatile, and complete framework available for developing powerful desktop , mobile , cloud and web applications. Unlike a desktop or mobile application, a web application runs on a public address, which is one of the reasons why the security of a web application is of great importance. Although Asp.Net Core is designed with security best practices in mind , there are still some vulnerabilities that we should watch out for before and after the release of our Asp.Net Coreapplications.
In this article, we will look at several security gaps in Asp.Net Core web applications and their possible solutions. Let's start by listing some of the important security considerations for our .Net Core application .
- Make your login more secure
- Only transmit sensitive data encrypted
- Remember to clear your cookies on exit
- Always use SSL
- Never store sensitive data in your database explicitly
- Audit trails and logging are very important
- Never expose original technical errors to the end user
- Cross Site Scripting (XSS)
- Try to hide the version of your .Net Core
- Cross Site Request Forgery (CSRF)
- LINQ can protect against SQL injection
- Add checks during deserialization
- Always keep up to date versions of your frameworks and libraries
1. Make your login more secure
The login page is the front door of any application. Consider an application like an admin panel. If an unauthorized person gains access to your application, they can control the entire system. Thus, your first step should always be to make your login more secure.
Here are some tips for securing your application's entry point.
USE COMPLEX ACCOUNTS
Never use usernames like admin and passwords like 12345 , or your name or personal information. Anyone can take advantage of this flaw, and the bot can pick up such credentials in an incredibly short time.
PROTECT YOUR LOGIN AGAINST
BRUTFORS Brute Force is the most common type of attack, which uses various algorithms to brute force username and password combinationsin order to guess the login credentials. In addition, a large number of login attempts can overload your server, which can result in DoS (Denial of Service) and downtime for the real users of your application.
Brute-force attacks take less time to guess simple usernames and passwords , but they can also guess complex combinations using trivial brute force attacks .
So how do you protect your Asp.Net application from brute force attacks?
Here are some tips to prevent brute-force attacks :
- Use Captcha on your login page, because bots can't handle captchas yet.
- IP .
- , admin user, .
- , (A-Z a-z), (0-9) (!, @,., #, $,%, ^, &, * ..).
How to implement the above recommendations?
The above guidelines may seem tricky to implement for beginner Asp.Net Core developers, but don't worry, there is an excellent HackerSpray library to help you protect your work from brute force attacks . All you need to do is configure it.
ALWAYS USE .NET CORE IDENTITY
Asp.Net Core has many built-in libraries and tools to secure your applications. Authorization also has a great implementation from Microsoft that gives us full customization of login and registration according to security best practices.
2. Transfer sensitive data only in encrypted form
Never explicitly send your sensitive information, such as password or credit card credentials , to the server for verification. Hackers can steal this data by intercepting it before sending it to the server.
Always use a hashing algorithm like md5 or SHA256 for passwords and encryption algorithms like AES or DES on the client side, for example using jQuery .

3. Remember to clear cookies on exit
When logging in to the Asp.Net Core application , we save some necessary data in the Session to maintain the user's login until he logs out. In some applications, we set the session timeout , and sometimes we do not, when the user ticks the checkbox indicating their desire to stay logged in on the login page.
At the same time, the AspNetCore.Session cookie is added to the browser to keep track of the logged in user.

Therefore, when we log out, we also need to remove the cookies created by our application from the browser , since the hackermay use this information for unauthorized logins. This is also called a Session Fixation attack .
4. Always use SSL
SSL stands for Secure Socket Layer . It encrypts communication between client and server with a very complex key.
You can simply tell your Asp.Net Core application's Starup.cs to always use a secure cookie policy.

5. Never store sensitive data in your database explicitly
Almost every web application for storing user data needs a database , which hackers attack in most cases precisely to steal this user data. So, let's say you store your users' credentials like passwords and billing specifications in your database in great detail and in a clean way. It turns out that anyone who gets unauthorized access to your database can use this data for their own selfish purposes.
Therefore, always store sensitive data in your database using hashing or encryption .
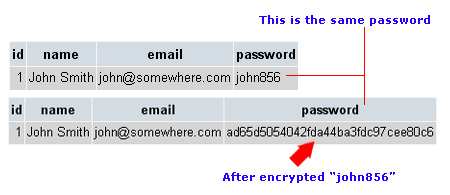
6. Audit trails and logging are very important
Audit trails or activity logs are very important to keep abreast of what's going on in your application. If someone generates a large number of failed login attempts , then the administrator should receive an email informing him of this.
For example, whether a user creates a new instance of an application user or changes the roles of an existing one, his every action should be reflected in the logs of your Asp.net Core application .

7. Never expose original technical errors to the end user.
Some exceptions can reveal important information about your application, or even sometimes show a few lines of code to the end user. The attackers are smart guys, they can use the information provided by your exception to hack your application.
Therefore, before deploying the application to production, make sure that you have created a page to display the error to the user for all types of exceptions and correctly saved the errors in the log of your application.

8. Cross Site Scripting (XSS)
In XSS (Cross-Site Scripting) attacks, hackers send malicious scripts through input fields to steal user credentials and other sensitive data.
Let's say we have a form for adding a product to an application. The hacker adds a new product and in the product description field, he simply inserts a JavaScript code snippet. When our application displays this product on the product page with a description, the hacker's malicious script will also run, and it will receive the data it needs.
I found the image below in the XSS article on Cloudflare . This will help you submit XSS more easily.

So how to protect our Asp.Net Core application from cross-site scripting attacks?
You can secure your web application by following these tips:
- Use regular expressions both client-side and server-side, and only store validated data in your database .
- HTML encryption with Razor helps to handle such scripts.
- XXS can also be done with URL encryption , so check the URL parameters and encrypt them with UrlEncoder .
Here's a great article from Microsoft on protecting your application from XSS.
9. Try to hide your .Net Core version
In every HTTP response from the server that we receive in response to our request sent from the browser, there is always information about the version on which the application was developed. Such information makes it easier for an attacker to work , saving him time and allowing him to target a specific version of .Net .
It is necessary to create more obstacles for hackers and make their work more difficult by hiding the version information of the .Net Framework .
Here's how to hide the .Net Core version :
- Remove X-Powered-By from response header.
- <a
href="https://www.nuget.org/packages/NWebsec.AspNetCore.Middleware/">NWebsec.AspNetCore.Middleware
Install
AddServerHeader = falseto remove the Server: Kestrel header.
You can remove X-Powered-By using this simple code snippet in your
web.config
<httpProtocol>
<customHeaders>
<remove name="X-Powered-By" />
</customHeaders>
</httpProtocol>10. Cross-site request forgery (CSRF)
Do you know the purpose of the attribute
[ValidateAntiForgeryToken]in your .Net Core Web APIs ? Perhaps you also noticed the code asp-antiforgery="true"in your cshtmlfile?
First we need to understand CSRF (Cross-Site Request Forgery or XSRF) , then we will try to understand the purpose of the above tag and attribute.
Let's say you're using e-banking from your bank account to send money to your friend, and all of a sudden you get a FaceBook link from a woman with a pretty avatar. When you open this link, it asks you to click here to earn $ 1000... You simply click and, since you are logged in and authorized to use your e-banking, this malicious link runs a script and sends money from your account to the hacker's account.
The image below clearly demonstrates CSRF.
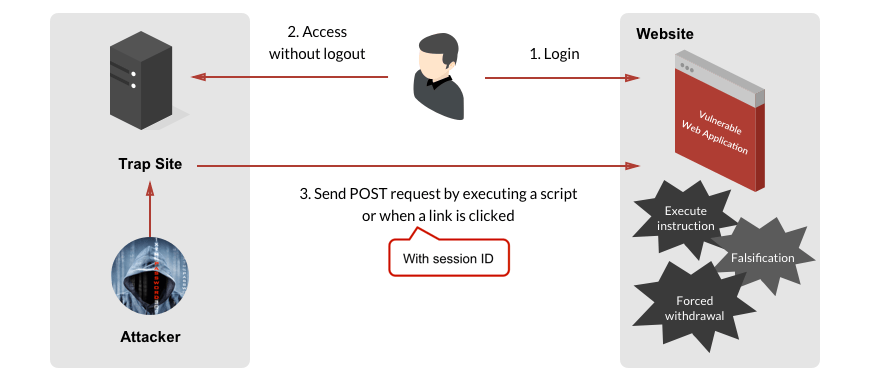
How can you protect your application from CSRF?
asp-antiforgery="true"creates an anti-forgery token, and [ValidateAntiForgeryToken]verifies on the server side if the token is valid and protects you from cross-site request forgery .
11. LINQ can protect against SQL injection
SQL injection is one of the most commonly used techniques to harm user data for many years.
In this method, the hacker places some conditional or special characters in the input field, which causes the entire request to change execution.
Here's a good example of what SQL injection is .

How to secure your Asp.Net Core application from SQL injection?
Here are some tips:
- Use Entity Framework Core
- Always use parameterized queries.
- Always validate server side input.
- Use stored procedures.
12. Add checks during deserialization
Deserialization is the opposite of serialization, which is the process of converting an object to streams of bytes. Serialization is always performed on the server side to transfer or store objects, and we deserialize the data received in our application from various sources.

Thus, we are open to many harmful streams.
To protect your application from attackers, we need to validate the data before and after deserialization.
13. Always keep up to date versions of your frameworks and libraries
Always update the frameworks and libraries used in your project. Never use outdated libraries in your project, because attackers constantly find vulnerabilities in them.
Check for updates for the NuGet packages used in your project and update them regularly.

CONCLUSION
Nothing is 100% secure, but we must make our application as secure as possible by following best practices. Although .Net Core is considered one of the most secure platforms, we still need to monitor the activity in our application and take quick action in case of any malicious activity.
Thanks for reading my article, I hope it motivates you to think about making your Asp.Net Core application more secure .
I would be glad if you would like to leave your feedback in the comments section below.
Here are some more articles that might interest you:
- TOP OPEN SOURCE ASP.NET CORE CONTENT SYSTEM (CMS)
- CREATING DYNAMIC USER-DEFINED DASHBOARDS USING ASP.NET CORE
- USING NOSQL DATABASE WITH DOTNET CORE EXAMPLE
Learn more about the course
:
- 7 , #/.NET
- C# .NET