
I have been working in IT for over 20 years, but somehow my hands did not reach containers. In theory, I understood how they work and how they work. But since I had never encountered them in practice, I was not sure how exactly the gears under the hood were turning and turning.
Also, I had no idea how they were doing with security. But then again, the theory sounds nice, and the old song "when security increases, usability decreases" stuck in my head. So I thought that since everything is so easy to do with containers, then the safety is below the baseboard. As it turned out, I was right.
For a quick start, I signed up for a Black Hat 2020 course titled " From Rags to Riches: Infiltrating and Securing Docker Swarm and Kubernetes Environments ."
, Sheila A. Berta Sol Ozzan, , Docker, Kubernetes. — Docker microk8s — , , , .
«» , , , .
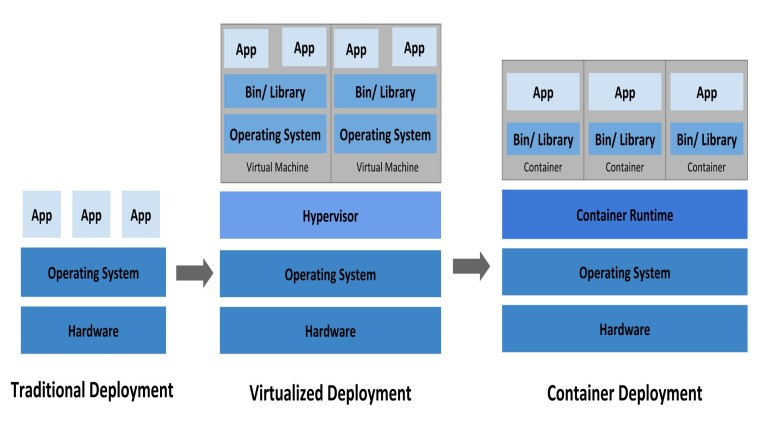
, , . , , , , - — . , , , . , , , . Kubernetes, , . .
.
root: , , . .
docker.sock : root , Docker , Docker (/var/run/docker.sock), , . , .
: . , .
Docker API : Docker API, , . Shodan , — . TrendMicro .
root: , root , . uid --user CLI, USER Dockerfile.
: -. nmap ifconfig Docker ( ), - . . . , , , .
docker.sock: , . , Docker, , .
Docker : 2017 . , , .
— Docker \ microk8s ( Kubernetes). Docker Linux MacOS, — microk8s Windows, Linux MacOS.
\ Docker, - : , , « Docker». , Docker. best practice — , .