task arises to "close" the loophole.

There are plenty of applications for remote control over the network: Chrome remote desktop, AmmyAdmin, LiteManager, TeamViewer, Anyplace Control, etc. If the Chrome remote desktop has an official manual on combating the availability of access to the service, TeamViewer has license restrictions on time or requests from the network and users "gritting their teeth" one way or another "shine" at the admins, then the favorite of many for personal use - AnyDesk so far requires special attention, especially if the boss said "No!"
 |
If you know what blocking a network packet by its contents is and you are satisfied with it, then the rest of the material is
not intended for you. |
Trying to go from the opposite, the site itself says what should be allowed for the program to work, respectively, the DNS record * .net.anydesk.com was blocked . But AnyDesk is not easy, it doesn't care about blocking a domain name.
Update 15.08.
The correct solution to block AnyDesk suggested prymalbeets123:
relays.net.anydesk.com
391 . , .
[bash#]host relays.net.anydesk.com
391 . , .
Once I solved the problem of blocking "Anyplace Control" which came to us with some dubious software and it was solved by blocking only a few IPs (I insured the antivirus). The task with AnyDesk, after I manually collected more than a dozen IP addresses, encouraged me to get away from routine manual labor.
It was also discovered that in "C: \ ProgramData \ AnyDesk" there are a number of files with settings, etc., and events about connections and failures are collected in the ad_svc.trace file .
1. Observation
As already mentioned, blocking * .anydesk.com did not give any results in the program's work, it was decided to analyze the program's behavior in stressful situations . TCPView from Sysinternals in hand and go!

1.1. It can be seen that several processes of interest to us are "hanging", and only the one that is connected to the address from the outside is of interest to us. The ports to which it is connected are being sorted out, from what I saw it: 80, 443, 6568. :) 80 and 443 we definitely cannot be blocked.
1.2. After blocking the address through the router, another address is quietly selected.
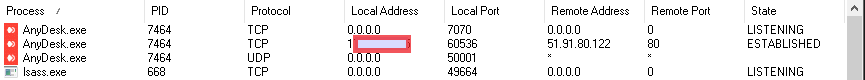
| 1.3. The console is our EVERYTHING! We determine the PID and here I was a little lucky that AnyDesk was installed by the service, respectively, the required PID is the only one. | 1.4. We determine the IP address of the service server by the process PID. |
 |
|
2. Preparation
Since the program for detecting IP addresses will probably only work on my PC, I have no limitations in convenience and laziness therefore C #.
2.1. All methods for identifying the desired IP address are already known to be implemented.
string pid1_;// PID AnyDesk
using (var p = new Process())
{p.StartInfo.FileName = "cmd.exe";
p.StartInfo.Arguments = " /c \"tasklist.exe /fi \"imagename eq AnyDesk.exe\" /NH /FO CsV | findstr \"Services\"\"";
p.StartInfo.UseShellExecute = false;
p.StartInfo.RedirectStandardOutput = true;
p.StartInfo.CreateNoWindow = true;
p.StartInfo.StandardOutputEncoding = Encoding.GetEncoding("CP866");
p.Start();
string output = p.StandardOutput.ReadToEnd();
string[] pid1 = output.Split(',');//
pid1_ = pid1[1].Replace("\"", "");// 2
}Similarly, we find the service that established the connection, I will give only the main line
p.StartInfo.Arguments = "/c \" netstat -n -o | findstr /I " + pid1_ + " | findstr \"ESTABLISHED\"\"";The result of which will be:
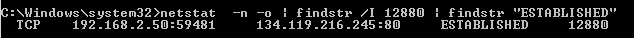
From the row, similarly to the previous step, extract the 3rd column, and remove everything after the ":". As a result, we have our desired IP.
2.2. IP blocking in Windows. If Linux has Blackhole and iptables, then the method of blocking an IP address in one line, without using a firewall, turned out to be unusual in Windows,
but what tools were ...
route add __IP_ mask 255.255.255.255 10.113.113.113 if 1 -pThe key parameter " if 1 " is to send the route to Loopback (You can display the available interfaces by running route print). AND IMPORTANT! Now the program needs to be run with administrator rights , since changing the route requires elevation.
2.3. Displaying and saving the detected IP addresses is a trivial task and does not require explanation. If you think about it, you can also process the ad_svc.trace file of AnyDesk itself, but I didn't think about that right away + maybe there is a limitation on it.
2.4. The strange uneven behavior of the program is that when the taskkill process of the service in Windows 10, it restarts automatically, in Windows 8 it ends, leaving only the console process and without reconnecting, in general it is illogical and inaccurate.
Removing the process that has connected to the server allows you to "force" reconnection to the next address. It is implemented similarly to the previous commands, so I only cite:
p.StartInfo.Arguments = "/c taskkill /PID " + pid1_ + " /F";Additionally, we launch the AnyDesk program.
// path_pro
if (File.Exists(path_pro)){
Process p1 = Process.Start(path_pro);}2.5. We will check the status of AnyDesk 1 time per minute (or more often?), And if it is connected i.e. ESTABLISHED connection - block this IP, and again all over again - wait until it connects, block and wait.
3. Attack The
code was "sketched", to visualize the process it was decided to " + " indicate the found and blocked IP, and " . " - to repeat the check without a successful connection from AnyDesk.
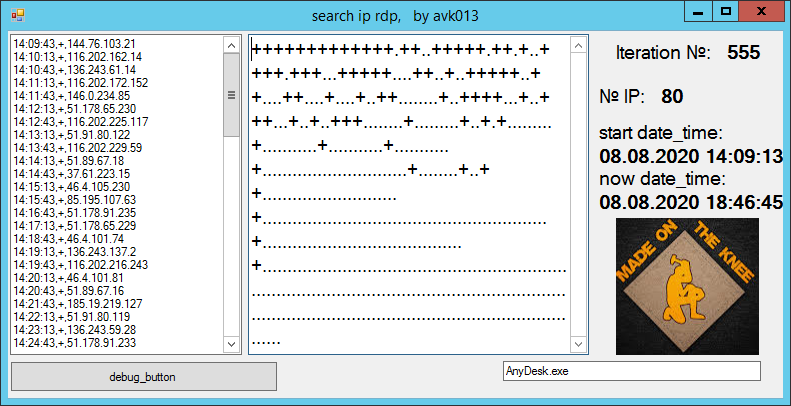
→ Project code
As a result ...
The program worked on several computers with different Windows OS, AnyDesk versions 5 and 6. About 80 addresses were collected in 500 iterations. Over 2500 - 87 and so on ...
Over time, the number of blocked IPs reached 100+.
Link to the final text file (blacklist) with addresses: >> one << and >> two <<
It's done! The pool of IP addresses through the script is added to the rules of the main router and AnyDesk simply cannot create an external connection.
There is a strange moment, according to the initial logs it can be seen that the address boot-01.net.anydesk.com is involved in the transfer of information... Of course, we blocked all * .net.anydesk.com hosts as a general rule, but this is not weird. Each time a normal ping from different computers, this domain name gives a different IP. Check in Linux:
host boot-01.net.anydesk.com
like DNSLookup only gives one IP address, but this address is variable. When analyzing a TCPView connection, we return PTR records of IP addresses of the type relay - *. Net.anydesk.com .
Theoretically: since a ping sometimes goes to an unknown unblocked host boot-01.net.anydesk.com, we can find these ip and block it, make this implementation a regular script under Linux OS, you don't need to install AnyDesk here. Analysis has shown that these IPs often " overlap"with the ones found from our list. Perhaps this is just this host, to which the program connects before it starts to search for known IPs. Probably I will later supplement the article with the 2nd part of searching for hosts, although at the moment the program itself does not install external connection in general.
Update 15.08.2020 : user Habr @ prymalbeets123 drew my attention to the fact that there is a host relays.net.anydesk.comwhich corresponds to 391 IP addresses, the file with their list can be found at the above links as correct. It is noticed that I have fewer addresses collected by monitoring the AnyDesk program, but there are those that are not included in the general 391 and they are resolved by "left" domain names, it turns out that I also "collected" the addresses of those who initiated the connection to my computer :).
I hope you didn't see anything illegal in the above, and the creators of AnyDesk will treat my actions in a sporty way.