Non-paper security
It is easy to guess that the analyst is collecting and processing information. The daily work of an information security analyst at Positive Technologies is to prepare reports and presentations based on the results of consulting projects. Among such projects are:
- penetration testing (pentests),
- service of Red team vs blue team ,
- security analysis of web and mobile applications,
- analysis of the security of banking systems (RBS, ATMs, payment terminals),
- security analysis of telecommunication networks,
- security analysis of industrial control systems,
- investigation of cyber incidents .
This list (and this is far from all areas) clearly demonstrates that the analyst must simultaneously immerse himself in various topics and constantly improve his knowledge. That is why it is wrong to compare this work with “paper” security. Every report that an analyst writes is centered around a practical component.
For example, for several years now, our company has been helping to raise the level of information security of one of the companies in Japan. Analysts are actively involved in a series of projects that take place at the customer's site in Tokyo. The analyst's job includes not only writing a detailed report, but also consulting the customer on all issues related to the results of the project. The analysts explain how and under what conditions the identified vulnerabilities can be exploited by cybercriminals and what attacks can lead to. In addition, he manages to expand his own horizons, traveling around Tokyo after hours.
The result of the analyst's work is not the same type of regulations and not policies, not stereotyped documents and not theoretical models of threats or a violator. This is a description of real ways to penetrate a local network from the Internet and attacks on the IT systems of operating companies. Let's take a simple example.
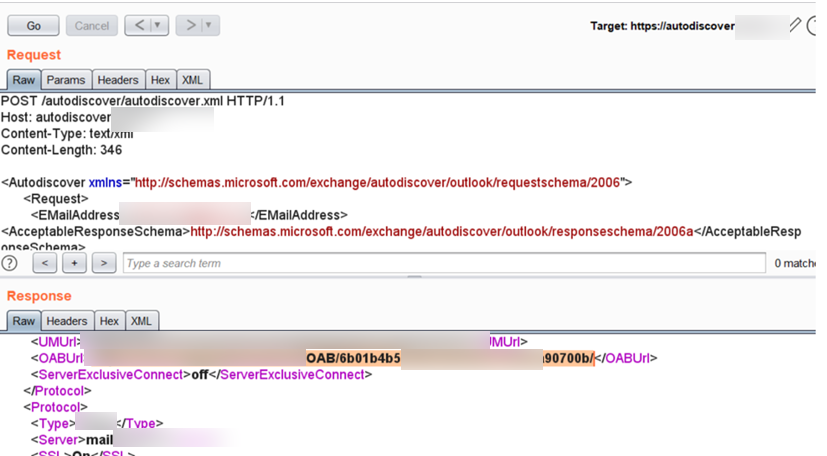
Figure 1. An example of data received from a pentester
After receiving a screenshot from the pentester as confirmation of the attack, as in Figure 1, the analyst realizes that an attempt was made to find the company's address book and download all the email addresses of employees from the web version of Outlook. He describes in the report the entire course of the attack, as well as the security flaws that allowed it to be carried out, and recommendations for eliminating these flaws or compensating measures for protection. As a rule, the next stage of such an attack is the selection of passwords for the received addresses.
The analyst makes a detailed analysis of all discovered vulnerabilities and the techniques used by the pentester, which means that he must have a good understanding of how each vulnerability is exploited, what this vulnerability is, what tools are used to attack and how to prevent it. Of course, he must be able to correctly state this in the report, describe the recommendations so that a specialist on the customer's side can easily understand the problem and eliminate it.
Between cybersecurity and business
In some ways, the work of an analyst is similar to the tasks of a technical writer who receives a draft and creates a final document. But this is only part of the job. As part of the project activities, the analyst constantly communicates with technical specialists, discusses the discovered vulnerabilities, clarifies all the details of the attack. This allows him to get a good grasp of the technical essence of the issue, so that he can then be able to reveal it in the report as detailed as possible.
The analyst should be able to present the results of a penetration test at any level - technical and “business”. A technical report allows an information security administrator to eliminate vulnerabilities, but such a document will be completely incomprehensible to the manager. The CEO will not waste precious time on a two-hundred-page document and try to delve into information security terminology. For example, how would you talk about SQL injection and CSRF in order processing if the chairman of a large corporation was listening?
Also, the analyst must understand how a possible attack will affect the performance of individual systems and what risks this may pose for the business. This is why analysts are periodically recruited to defend a project in front of management or prepare a short presentation and a one-page resume. There were even cases when an analyst prepared a short report on the results of a cyber incident for the minister. Needless to say, such documents require a special approach.
Research and communication with journalists
There is another part of the work - research. The knowledge gained in projects is unique, because it is based on practically implemented attacks on existing IT systems. The analyst becomes the custodian of such knowledge.
If a technical specialist conducting a pentest is immersed in one selected area of work, and the range of his tasks is quite typical, then the analyst regularly connects to many diverse projects, which means that he has an overall picture of the level of information security in the context of industries. He can assess which vulnerabilities are more common depending on the type of system, in which companies the protection is worse, and which attack techniques are most relevant.
For example, we recently conducted a large study on the topic of targeted attacks against companies in Russia. The result was four articles in which we showed what tactics and techniques are used by cyber groups attacking Russian business in the credit and financial sector , industry , the fuel and energy complex and government agencies . Not long before that, we analyzed advertisements on underground forums in the dark web , where they sell and buy various tools and services for cyberattacks, and estimated how much it might cost to organize one such attack for criminals.
Our other research can be found on the company's website .

2. Positive Technologies
The results of a large pool of work on security analysis can also be generalized and presented in an impersonal form to the entire information security community. The analyst brings together the expertise of various Positive Technologies divisions, writes articles that are published on the company's website, as well as in magazines, newspapers, blogs, social networks and other media, conducts webinars and speaks at conferences. In order to cover the most pressing problems of information security and help the interested audience to understand complex issues, the analyst gives comments to journalists, participates in live broadcasts on television and radio, and in press conferences. Izvestia, Kommersant, RBC, RIA Novosti are just a few examples of publications that regularly cover the results of our experts' work.This approach helps to convey the most interesting trends in the field of information security to the community and increase the general literacy of people in information security.
Analysts are unique in the market
At the university or in advanced training courses, they provide only a base - the analyst cannot get there the knowledge that he receives in the process of work. The analyst is constantly developing and enriching the collection of his knowledge through participation in projects. Each new project provides an opportunity to learn new attack methods and see how they are implemented in practice. Immersion in different topics allows you to constantly expand your horizons. This is a unique opportunity to develop professionally.
The knowledge gained in work can be applied in other professions. There are examples when an analyst moved to the pentest department. Or when an analyst became a successful consulting project manager. But there are those who, on the contrary, want to engage in data analysis and develop in this area.
Senior students and specialists from different areas of information security came to our team: an engineer-designer of security systems, an associate professor of a department at a university, a reverse engineer, a specialist in certification of security products, specialists in consulting in the field of personal data protection. There are also candidates of technical sciences. The level of training of analysts is also confirmed by international certificates: our experts have such certificates as OSCP, CISSP, CEH.
How to become an analyst
If, after reading this article, you realize that you already have all the qualities that will allow you to join our team and you want to grow with us, send your resume to career@ptsecurity.com and we will meet for an interview. If you are not confident in your abilities, but understand the penetration test and vulnerabilities, we are ready to consider successful candidates for junior positions. The development of specialists is one of our priority tasks.