Some statistics
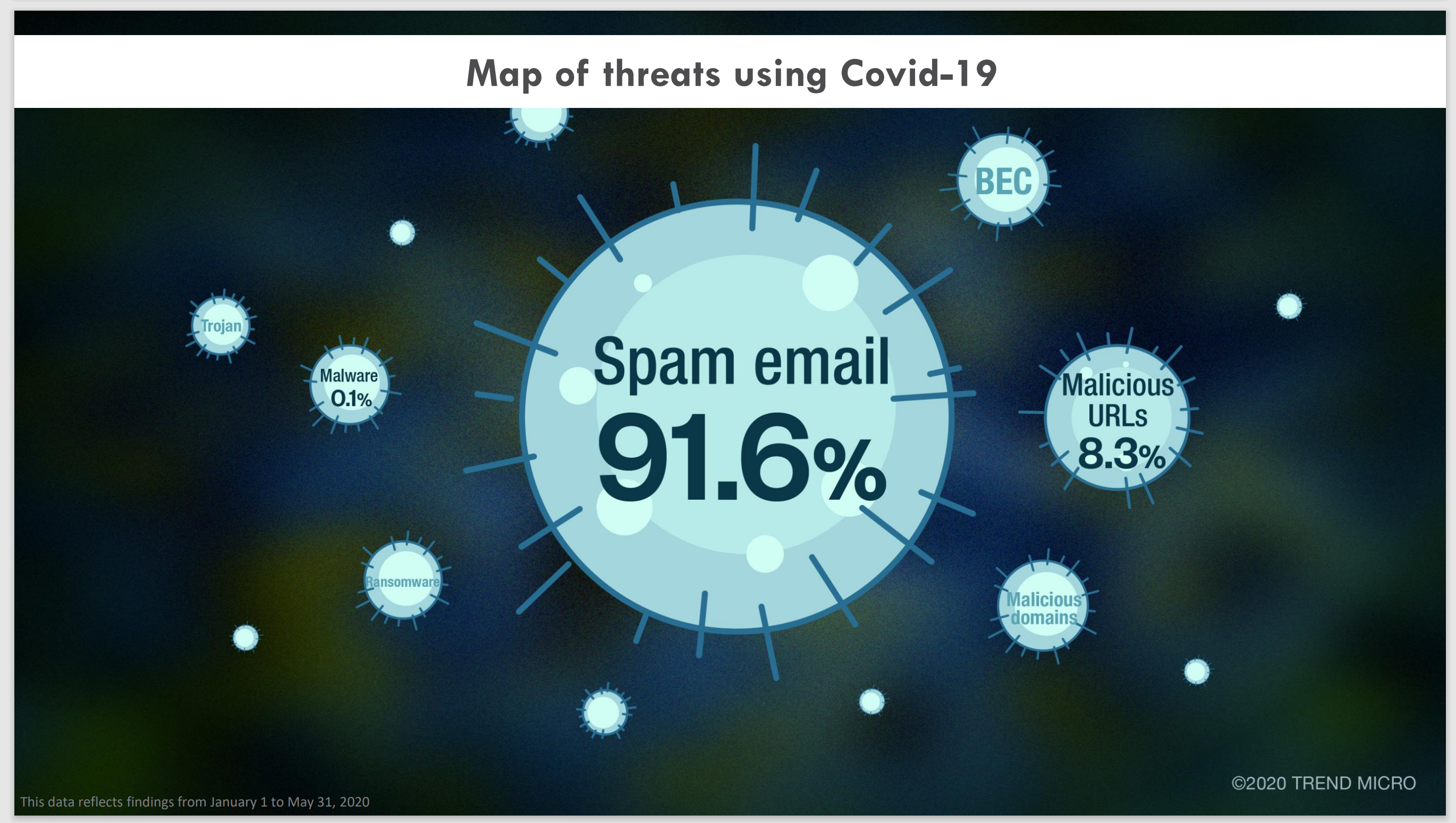
A map of distribution vectors used by COVID-19 branded campaigns. Source: Trend Micro
The main tool for cybercriminals is still spam mailings, and despite warnings from government agencies, citizens continue to open attachments and follow links in fraudulent emails, contributing to the further spread of the threat. The fear of contracting a dangerous infection leads to the fact that, in addition to the COVID-19 pandemic, one has to fight cyber pandemic - a whole family of "coronavirus" cyber threats.
The distribution of users who clicked on malicious links looks quite logical:

Distribution by country of users who opened a malicious link from a letter in January-May 2020. Source: Trend Micro
In the first place by a wide margin, users from the United States, where at the time of this writing, there were almost 5 million cases. Russia, which is also among the leading countries in terms of COVID-19 cases, is in the top five in terms of the number of particularly gullible citizens.
Cyberattack pandemic
The main topics that cybercriminals use in fraudulent emails are delivery delays due to the pandemic and coronavirus-related notifications from the Ministry of Health or the World Health Organization.

The two most popular scam email topics. Source: Trend Micro The
most common “payload” in such emails is Emotet, a ransomware ransomware that appeared back in 2014. The covid rebranding helped malware operators increase campaign profitability.
The arsenal of covid scammers also includes:
- fake government websites to collect bank card data and personal information,
- informer sites on the spread of COVID-19,
- fake portals of the World Health Organization and Centers for Disease Control,
- mobile spies and blockers masquerading as useful programs for informing about infection.
Prevention of attacks
In a global sense, the strategy for dealing with a cyber pandemic is similar to that used in the fight against common infections:
- detection,
- response,
- prevention,
- forecasting.
Obviously, the problem can be overcome only through the implementation of a set of measures focused on the long term. The list of measures should be based on prevention.
Just as it is proposed to keep distance, wash hands, disinfect purchases and wear masks to protect against COVID-19, phishing attack monitoring systems, as well as intrusion prevention and control tools, can exclude the possibility of a successful cyber attack.
The problem with such tools is a large number of false positives, which require huge resources to process. The use of basic security mechanisms - conventional antiviruses, application control tools, and site reputation assessment - can significantly reduce the number of notifications about false positive events. In this way, the security team will be able to pay attention to new threats, since known attacks will be blocked automatically. This approach allows you to evenly distribute the load and maintain a balance of efficiency and safety.
Tracking the source of infection is essential during a pandemic. Likewise, identifying the starting point for the implementation of the threat in cyber attacks allows you to systematically protect the company's perimeter. To ensure security at all points of entry into IT systems, tools of the EDR (Endpoint Detection and Response) class are used. By capturing everything that happens on the endpoints of the network, they allow you to restore the chronology of any attack and find out which node was used by cybercriminals to penetrate the system and spread over the network.
The disadvantage of EDR is a large number of unrelated notifications from different sources - servers, network equipment, cloud infrastructure, and email. Exploring scattered data is a time-consuming manual process that can lead to overlooking something important.
XDR as a cyber vaccine
The XDR technology, which is a development of EDR, aims to solve the problems associated with the large number of alerts. The “X” in this abbreviation denotes any infrastructure object to which the discovery technology can be applied: mail, network, servers, cloud services, and databases. Unlike EDR, the collected information is not just transferred to SIEM, but is collected in a universal storage, in which it is systematized and analyzed using Big Data technologies.

Block diagram of interaction between XDR and other Trend Micro solutions
This approach, compared to the mere accumulation of information, allows you to detect more threats by using not only internal data, but also the global threat base. Moreover, the more data is collected, the faster threats will be identified and the higher the accuracy of alerts.
The use of artificial intelligence makes it possible to minimize the number of alerts, since XDR generates high-priority alerts enriched with a wider context. As a result, SOC analysts are able to focus on notifications that require immediate action, rather than manually checking each message to calculate relationships and context. This will significantly improve the quality of forecasts of future cyber attacks, on which the effectiveness of the fight against cyber pandemic depends.
Accurate prediction is achieved by collecting and correlating different types of detection and activity data from Trend Micro sensors deployed at different levels within an organization - endpoints, network devices, email, and cloud infrastructure.
The use of a single platform greatly facilitates the work of an information security service, since it receives a structured and prioritized list of alerts, working with a single window for presenting events. Rapid identification of threats makes it possible to quickly respond to them and minimize the consequences of them.
Our recommendations
The centuries-old experience of fighting epidemics shows that prevention is not only more effective than treatment, but also has a lower cost. As modern practice shows, computer epidemics are no exception. Preventing infection of the company's network is much cheaper than paying a ransom to ransomware and paying counterparties compensation for unfulfilled obligations. Garmin
recently paid the ransomware $ 10 millionto get a decoder program for your data. To this amount should be added the losses from the inaccessibility of services and reputational damage. A simple comparison of the result obtained with the cost of a modern security solution allows us to draw an unambiguous conclusion: prevention of information security threats is not a case where savings are justified. The consequences of a successful cyberattack will cost the company significantly more.