
In this article, we will understand how to decompile ELF files in Cutter using the example of light tasks. Past Introduction to Reverse
Parts : Part 1: C, C ++ and DotNet decompile - Reverse Basics
Part 2: MIPS Reverse and Golang - Reverse Basics
Organizational information
Fake instructions

This is the eighth assignment in this category, and we are being told that there are fake instructions. Let's start by looking at the file information.

I open the program in Cutter - a GUI for radare2 with a built-in ghidra decompiler that has the ability to emulate and more recently debug. And immediately we get an interesting list of functions.

Let's move on to the main function and decompile it.

At the very beginning, the canary is initialized and the number of arguments is checked. After that, 0x1f bytes are allocated, where the specified constant string is copied, the address is saved into the iVar3 variable, and then individual bytes of this string are changed. Next, transformations take place with the string s1, which is of no interest to us. The WPA function is also initialized, and the password we entered is written to the auStack50 address and passed along with the converted iVar3 string to the WPA function, after which the canary value is checked and the program terminated.
Let's move on to the WPA feature.
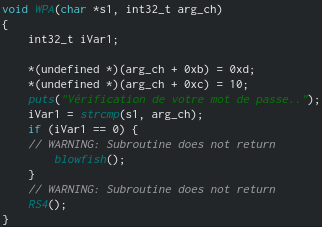
The line previously inserted in the program is changed again, after which the two lines are compared. If they are equal, the blowfish () function will be called, which will display us the correct password for change, otherwise the RS4 () function will be called.
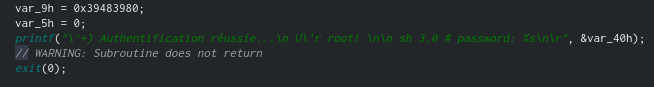
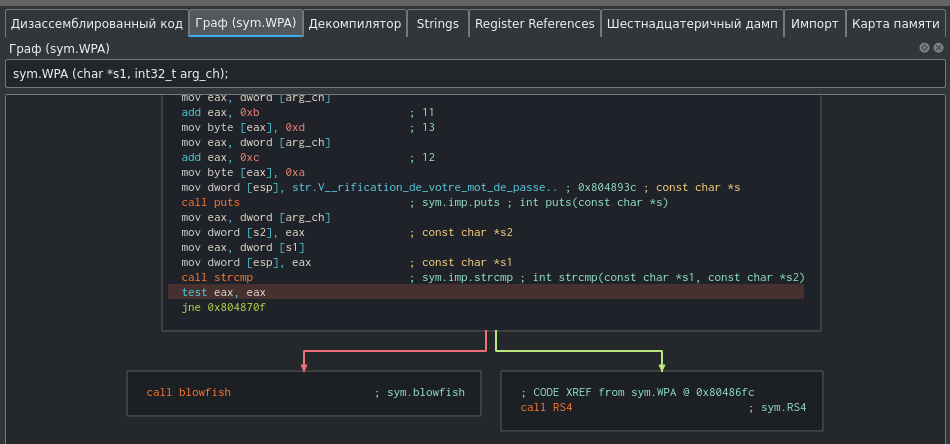
Since the decryption of the previously entered values occurs, we can debug the program and change the result of the comparison. Let's go to where the strings are compared and set a breakpoint.
Now let's start debugging - F9, and enter the program arguments.
Click on the button further on the navigation bar until we reach our breakpoint. The result of comparing strings using the strcmp () function will be written to the EAX register, which will then be checked. Since the strings are not equal, this register contains the value 1.

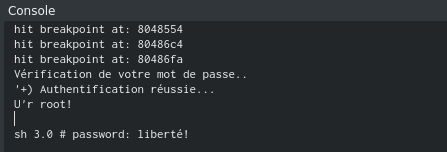
Let's change it to 0 to change the branch of the program's behavior and continue executing. After completion in the Cutter console, we will see the correct answer, which should be submitted on the site.
Ptrace
Download the program and check it.

Nothing fancy, you need to find a password. But there is a little protection against debugging (ptrace) and transitions that need to be edited manually. This is how the graph shows in IDA Pro.

We will also do this task in Cutter, it will automatically correct all transitions.
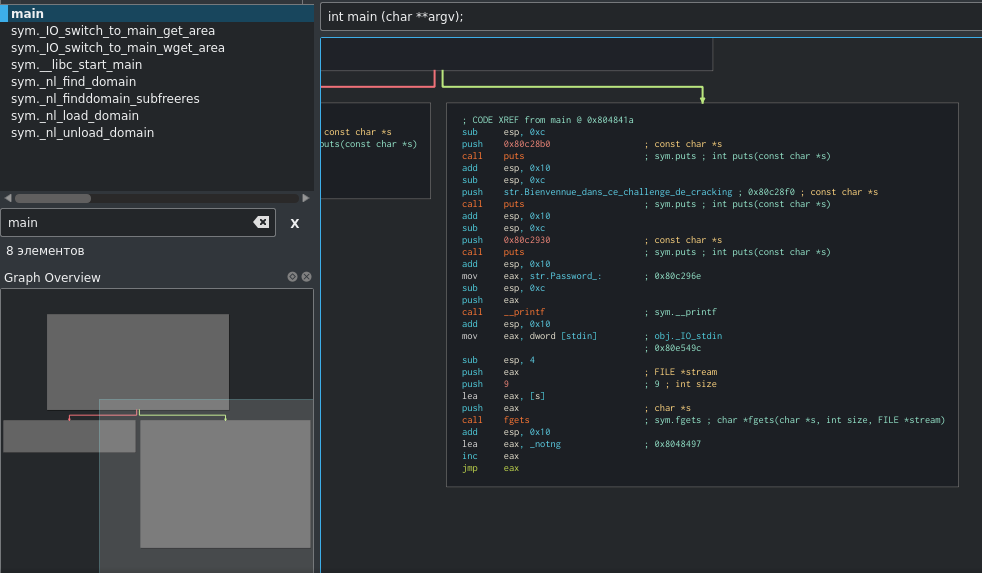
Let's move on to decompiling the main function.
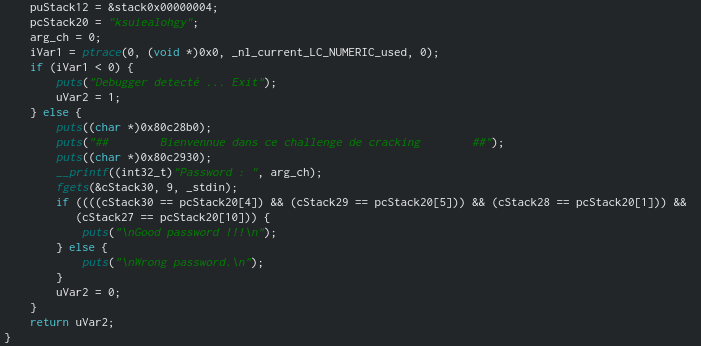
And the correct password is the corresponding 4 letters from the string specified at the very beginning.
ARM ELF
This is a binar for the ARM architecture, we throw it in Cutter and select the main function. From the function graph, we see what we are dealing with, and most likely this is a symbol-by-symbol comparison.

We open the decompiler and analyze the program.

First of all, the presence of the program argument and its length are checked, it must be equal to 6.
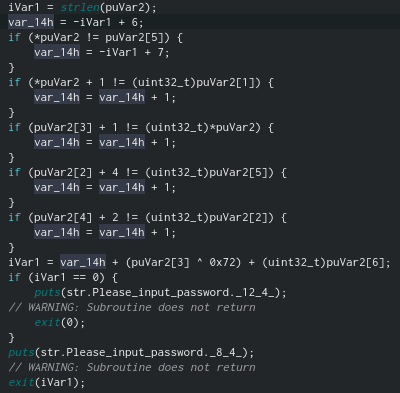
So the variable var_14h acts as an index and takes the value 0. And then a number of comparisons take place, which we will regard as conditions:
str [0] == str [5]
str [0] + 1 == str [1]
str [3] + 1 == str [0]
str [2] + 4 == str [5]
str [4] + 2 == str [2]
0 == str [3] ^ 0x72
Let's implement the algorithm and get the password.

And we get the required password. That's all for now.
You can join us atTelegram . There you can find interesting materials, leaked courses, and software. Let's gather a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.