
Email address is a key element in protecting personal data. It is often linked to other user accounts. Having taken possession of someone else's e-mail, an attacker is able to recover or reset the passwords of the services associated with the hacked account. If a person does not use two-factor authentication (2FA), then he is practically defenseless . Two-factor authentication is also not a panacea, but here the cybercriminal will need additional efforts - you need to reissue the SIM card or intercept the authentication code . Interception is quite difficult to implement, since codes are usually sent via SMS or an authenticator application.

Screenshot of one of the sites offering services for hacking mail accounts
Anyway, hacking mailboxes is a demanded service. Interestingly, it is often not hardened criminals who order it, but suspicious spouses or lovers. A husband or wife just wants to be aware of the online correspondence of their half, so they order a hack. Business competitors also use this opportunity - after all, with a successful hack, you can get access to the secrets of an opponent.
Hacking a mailbox in information security terminology is considered a "targeted" or "targeted" attack. State intelligence such as the NSA and the GRU are engaged in such things, but there is also a black market for services for mere mortals, where you can order a break in any box for a modest fee. This is the hack-for-hire market. It is actively flourishing in the Russian Federation, because here, unlike in Western countries, such petty crimes do not face criminal liability.
Despite its popularity, the infrastructure of this market is not well understood. Little is known about how these hackers work and how much of a threat they pose. But details are gradually emerging. For example, a relatively small market research was conducted by Ariana Mirian of the University of California, San Diego. Results published at the conference "WWW'19: The World Wide Web Conference" and in the scientific journal "Communications of the ACM" (December 2019, Vol. 62 No. 12, Pages 32-37, doi: 0.1145 / 3308558.3313489).
How much does this service cost?
The project team identified and examined 27 retail email hacking services. Most of the services were advertised in Russian. Service cost - from $ 23 to $ 500 for one account. The cheapest way is to get access to the boxes of Russian providers. Western ones are more expensive, and hacking Facebook and Instagram accounts will cost a little less than Yahoo and Gmail.
 Prices for hacking mailboxes and accounts. Illustration: University of California San Diego
Prices for hacking mailboxes and accounts. Illustration: University of California San Diego
Using dummy accounts, Ariana Mirian contacted the perpetrators and ordered to hack the accounts of dummy "victims." Two-factor SMS authentication was enabled on each account.
Experimental technique
The experiment was well thought out. Each of the e-mail boxes involved in the study were filled from the Enron e-mail database . In addition, the project participants created web pages advertising a small business that the victim owned or worked for.
Domains were auctioned to provide the history of each dummy. Through the WHOIS database, this web page was linked to the victim's email address, as well as the email address of the fictitious partner. In general, the researchers thought out and implemented high-quality "traps" to identify all attack vectors.
Additionally, Facebook pages were created for each victim to see if hackers would use them in their attacks. All elements on the Facebook page were private (a third party would not be able to see these elements), with the exception of a profile showing the victim's web page (like a business advertisement).
The activity of each mailbox was automatically logged. Thanks to the help of Google, it was possible to obtain logs of any logging activity in the victims' Google accounts. These logs record attempts to log into an account and IP addresses, brute force attempts, as well as the activation of two-factor authentication in case of a suspicious login attempt.
Finally, all network traffic to the site of each of the "victims" was analyzed. If an attacker visited the site from a Facebook page, this was reflected in the traffic record.
The actions of hackers who tried to hack into accounts were tracked for several weeks. In fact, it turned out that some of the "crackers" are common scammers who took payment and did nothing. Others took payment post factum, that is, they agreed to receive money in case of a successful hack. But even they, having received the task, did nothing. The researchers also note that the "work with clients" of the services for hacking e-mail is extremely poorly organized: someone does not respond to requests at all, someone responds, but with a long delay.
results
Only 5 out of 27 hackers began to fulfill the terms of the task set by the customer.

The experiment and logs allowed us to study the scheme of actions that attackers use to hack an account. In each of the five cases where the hackers took on a task, the capture of the account ended with "success", but only with the assistance of the researcher.
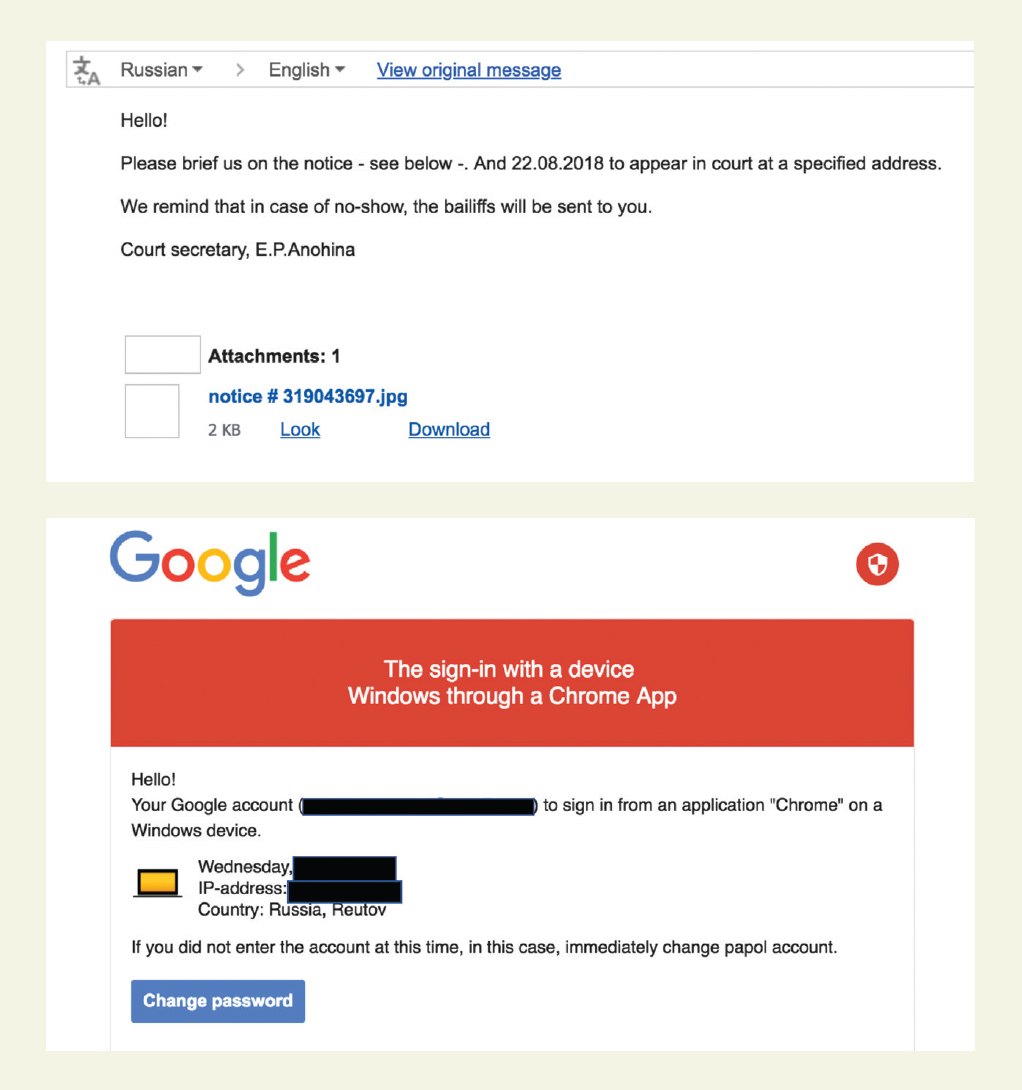
The attackers in one way or another led the "victim" to a phishing page, where they had to enter a password or two-factor authentication code from their account. The project participants acted as deceived users and entered all the necessary data. After that, the hackers cheerfully reported their success.
Interestingly, not a single hired cybercriminal tried to brute force accounts, there were no calls to Facebook accounts or to a partner's email. One in five perpetrators sent a malicious executable file to the victim by mail. The rest used phishing as their main attack vector.
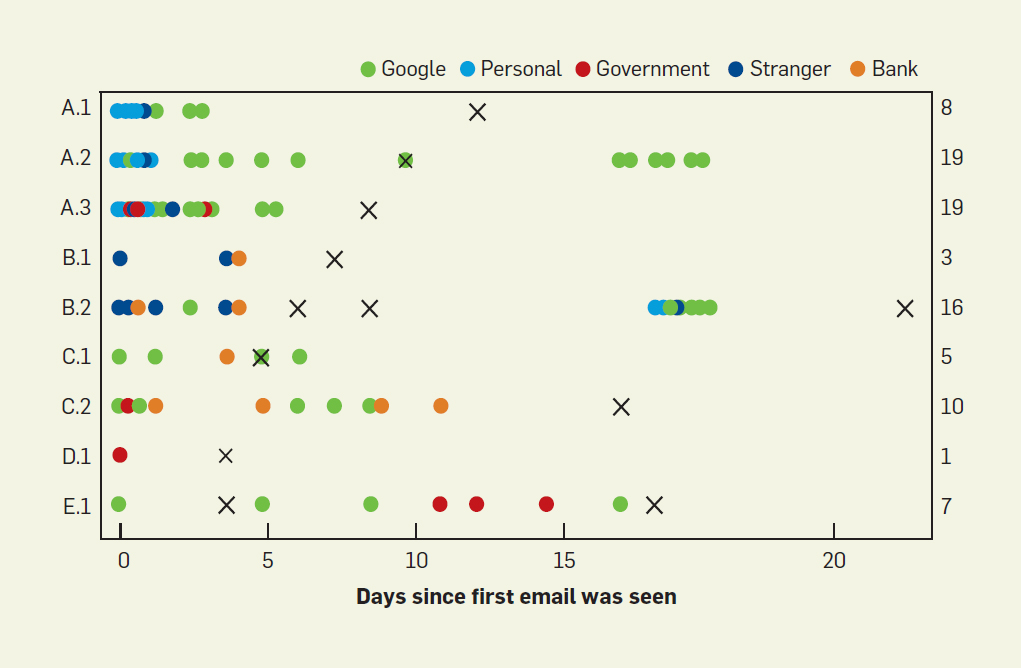

All attacks started with a decoy letter from a reputable organization or person. This was supposed to calm the victim down and lead him to the necessary action - clicking on a link to a phishing resource. The attackers used a variety of dummy figures: the victim's acquaintance, a large bank, a stranger, a government agency, and Google. An image or phishing link was attached to the email.
On average, attackers sent 10 messages within 25 days using different pretexts, as shown in the diagram above. The most popular trick is to fake a Google letter, followed by letters from partners and fake emails from strangers.
By clicking on the phishing link, the victim is taken to a landing page that looks like a Google account login page. After entering the password, a page opens with a request to enter the 2FA code. All hackers who gained access to the account achieved what they wanted with phishing. There were no particularly complicated techniques or sophisticated attacks.
How to avoid becoming a victim of cybercriminals
Any mailbox can be hacked if the victim is negligent and follows a phishing link. It is possible that professionals, subject to urgent need or a large reward, are able to hack the account without phishing, but during the study, such methods were not used. Of course, here the sample itself was not very large.
To protect yourself and your family from such attacks, experts recommend using a USB hardware security dongle for 2FA, as well as being careful - this is a standard recommendation.
Take steps to protect users and email service providers. Google has introduced additional heuristics for user login. Automatic login attempts are also detected and blocked. By the way, after these actions by Google, two hacking services previously contacted by researchers doubled the price of their services.