
Welcome to the third article in a series on the new cloud-based security management console for personal computers - Check Point SandBlast Agent Management Platform. Let me remind you that in the first article we got acquainted with the Infinity Portal and created a cloud-based service for managing agents, Endpoint Management Service. In the second article, we examined the web management console interface and installed the agent with standard policy on the user's machine. Today we will review the contents of the standard Threat Prevention security policy and test its effectiveness in countering popular attacks.
Threat Prevention Standard Policy: Description
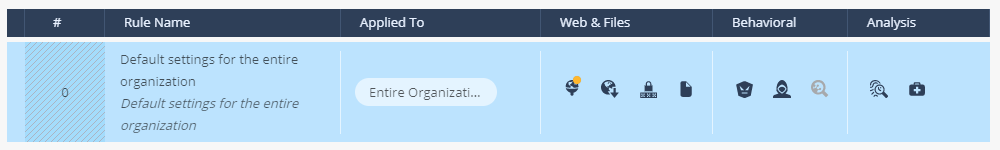
The figure above shows a standard Threat Prevention policy rule, which by default applies to the entire organization (all installed agents) and includes three logical groups of protection components: Web & Files Protection, Behavioral Protection, and Analysis & Remediation. Let's take a closer look at each of the groups.
Web & Files Protection
URL Filtering
URL Filtering -, 5 . 5 , , , Games Instant Messaging, Productivity Loss. URL, , Check Point. , URL, URL Categorization.
Prevent, Detect Off. Detect , URL Filtering . Prevent . Block List, , IP- .csv .
Prevent, Detect Off. Detect , URL Filtering . Prevent . Block List, , IP- .csv .
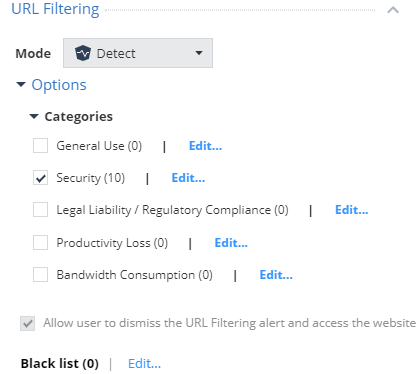
In the standard policy for URL Filtering, the action Detect is set and one category is selected - Security, for which events will be detected. This category includes various anonymizers, sites with a Critical / High / Medium risk level, phishing sites, spam and much more. However, users will still be able to access the resource thanks to the "Allow user to dismiss the URL Filtering alert and access the website" setting.
Download (web) Protection
Emulation & Extraction Check Point « », , PDF. :
, Check Point — .
- Prevent — , ;
- Detect — , , ;
- Off — .
, Check Point — .
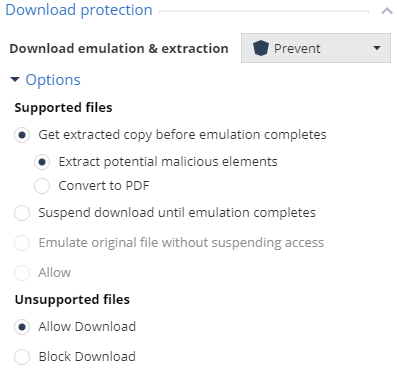
The default policy for Download Protection is set to the Prevent action with the ability to retrieve a copy of the original document cleaned of potentially malicious content, as well as allowing the download of files that are not supported by emulation and cleanup tools.
Credential Protection
Credential Protection 2 : Zero Phishing Password Protection. Zero Phishing , Password Protection . Zero Phishing Prevent, Detect Off. Prevent , . Detect . Password Protection , , : Detect & Alert ( ), Detect Off.

The standard policy for Credential Protection provides a Prevent for any phishing resource that makes it impossible for users to access a potentially malicious site. Protection against the use of corporate passwords is also included, but this function will not work without the specified domains.
Files Protection
Files Protection , , : Anti-Malware Files Threat Emulation. Anti-Malware , . , , . Files Threat Emulation Check Point, Detect.
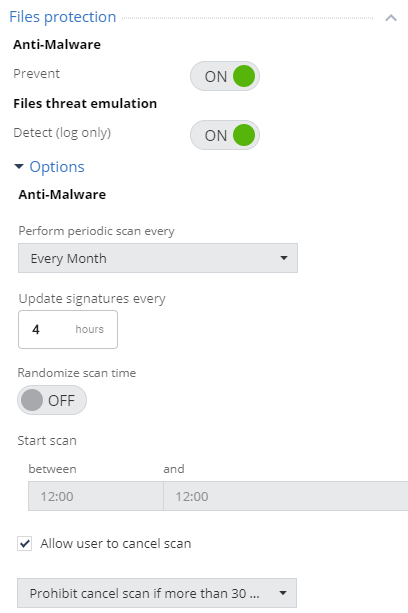
The default policy for Files Protection includes Anti-Malware protection and Malicious file detection using Files Threat Emulation. Regular scans are performed every month and signatures on the user's machine are updated every 4 hours. At the same time, the ability for users to cancel a scheduled scan is configured, but no later than 30 days after the last successful scan.
Behavioral Protection
Anti-Bot, Behavioral Guard & Anti-Ransomware, Anti-Exploit
Behavioral Protection : Anti-Bot, Behavioral Guard & Anti-Ransomware Anti-Exploit. Anti-Bot C&C Check Point ThreatCloud. Behavioral Guard & Anti-Ransomware (, , ) . , , . , , . Anti-Exploit . Behavioral Protection : Prevent, Detect Off.

The standard policy for Behavioral Protection provides Prevent for the Anti-Bot and Behavioral Guard & Anti-Ransomware components, with the restoration of encrypted files in their original directories. The Anti-Exploit component is disabled and not used.
Analysis & Remediation
Automated Attack Analysis (Forensics), Remediation & Response
: Automated Attack Analysis (Forensics) Remediation & Response. Automated Attack Analysis (Forensics) — . Threat Hunting, . Remediation & Response : , .
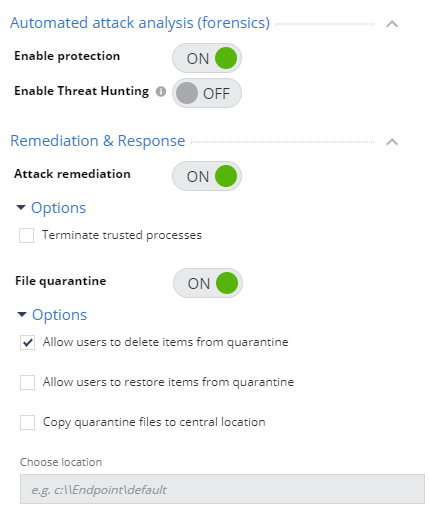
The standard Analysis & Remediation policy includes protection, which includes automatic actions for recovery (terminating processes, restoring files, etc.), as well as the option to send files to quarantine, and users can only delete files from quarantine.
Threat Prevention Standard Policy: Testing
Check Point CheckMe Endpoint

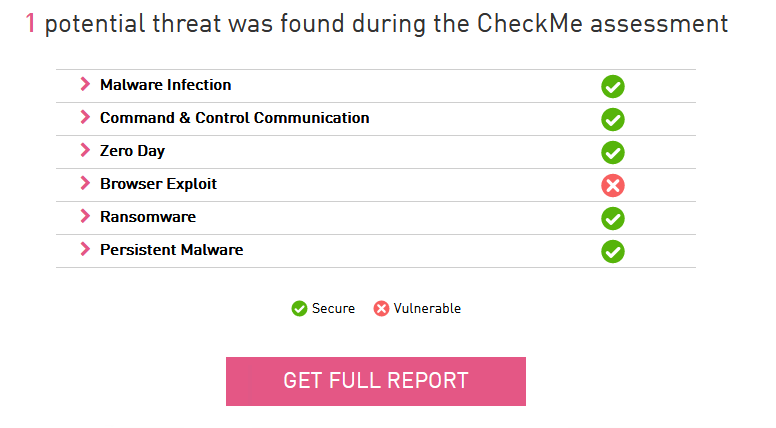
The fastest and easiest way to check the security of a user's machine against the most popular types of attacks is to conduct a test using the Check Point CheckMe resource , which carries out a number of typical attacks of various categories and allows you to get a report on the results of testing. In this case, we used the Endpoint testing option, in which an executable file is downloaded and launched on the computer, and then the verification process begins.

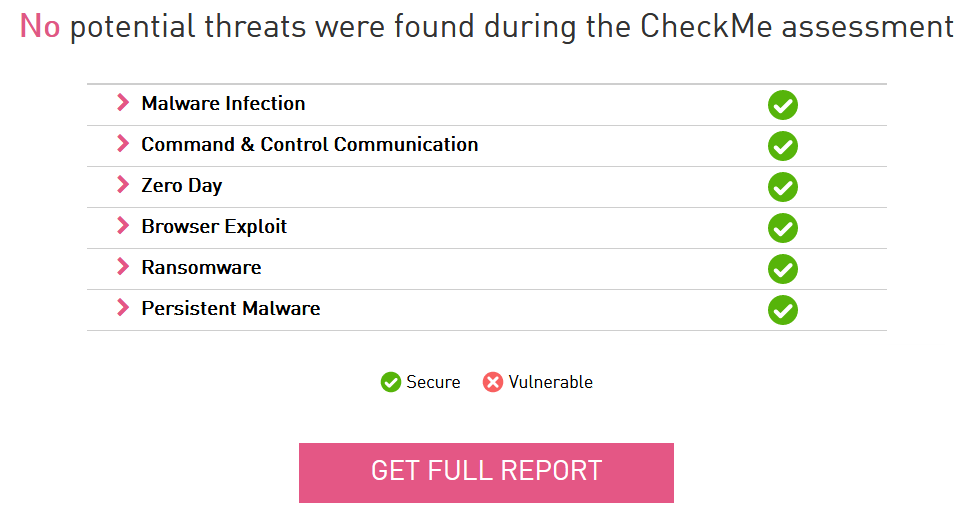
While checking the security of the working computer, SandBlast Agent signals identified and reflected attacks on the user's computer, for example: the Anti-Bot blade reports an infection, the Anti-Malware blade has detected and deleted the malicious file CP_AM.exe, and the Threat Emulation blade has installed that the CP_ZD.exe file is malicious. As a result of testing with CheckMe Endpoint, we have the following result: out of 6 categories of attacks, the standard Threat Prevention policy failed only in one category - Browser Exploit. This is because the standard Threat Prevention policy does not include the Anti-Exploit blade. It should be noted that without SandBlast Agent installed, the user's computer was scanned only for the Ransomware category.

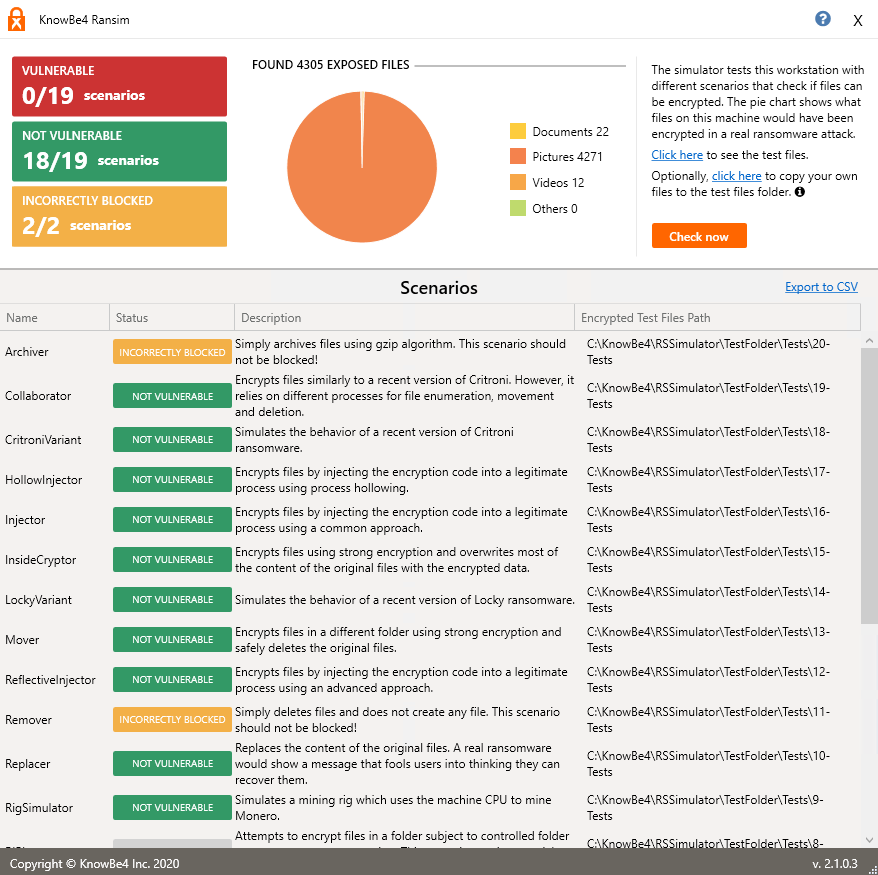
KnowBe4 RanSim
To test the Anti-Ransomware blade, you can use the free KnowBe4 RanSim solution , which runs a series of tests on the user's machine: 18 ransomware infection scenarios and 1 cryptominer infection scenario. It should be noted that the presence of many blades in the standard policy (Threat Emulation, Anti-Malware, Behavioral Guard) with the Prevent action does not allow this test to run correctly. However, even with a reduced security level (Threat Emulation in Off mode), the Anti-Ransomware blade test shows good results: 18 out of 19 tests passed successfully (1 did not start).
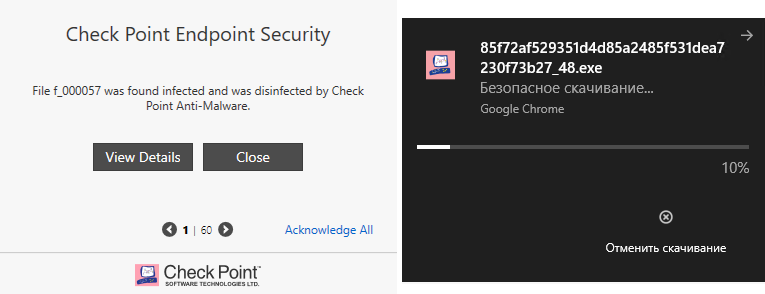
Malicious files and documents
It is instructive to check the operation of different blades of the standard Threat Prevention policy using malicious files of popular formats downloaded to the user's machine. This test involved 66 files in PDF, DOC, DOCX, EXE, XLS, XLSX, CAB, RTF formats. The test results showed that SandBlast Agent was able to block 64 malicious files out of 66. Infected files were deleted after downloading, or cleaned of malicious content using Threat Extraction and retrieved by the user.
Recommendations for Improving Threat Prevention Policy
1. URL Filtering
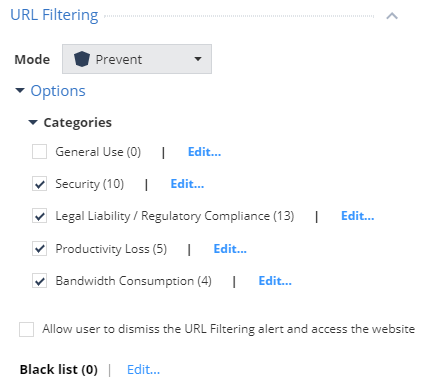
The first thing that needs to be fixed in the standard policy to increase the security level of the client machine is to move the URL Filtering blade to Prevent and specify the appropriate categories to block. In our case, all categories were selected, except for General Use, since they include most of the resources to which you need to restrict access to users at the workplace. It is also advisable for such sites to remove the ability for users to skip the warning window by unchecking the "Allow user to dismiss the URL Filtering alert and access the website" parameter.
2. Download Protection
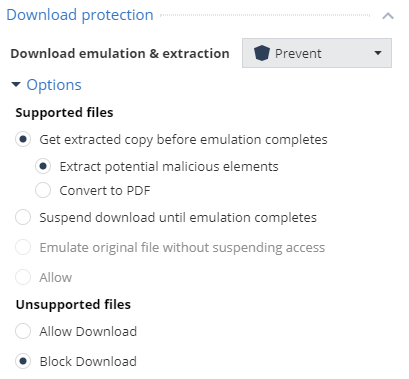
The second parameter to pay attention to is the ability for users to download files that are not supported by Check Point emulation. Since in this section we are looking at the security enhancements to the standard Threat Prevention policy, the best option would be to disallow the download of unsupported files.
3. Files Protection

You should also pay attention to the settings for protecting files - in particular, the parameters of periodic scanning and the ability of the user to postpone forced scanning. In this case, you need to take into account the time frame of the user's work, and a good option from the point of view of security and performance is to configure the execution of forced scanning every day, and the time is randomly selected (from 00:00 to 8:00), and the user can postpone the scan for a maximum of one week.
4. Anti-Exploit
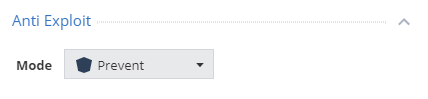
A significant drawback of the standard Threat Prevention policy is the disabled Anti-Exploit blade. It is recommended to enable this blade with the Prevent action to protect the workstation from exploit attacks. With this fix, the CheckMe retest succeeds without detecting vulnerabilities on the user's work machine.
Conclusion
To summarize: in this article, we got acquainted with the components of the standard Threat Prevention policy, tested this policy using various methods and tools, and also described recommendations for improving the settings of the standard policy to increase the security level of the user's machine. In the next article in this series, we will move on to exploring Data Protection policy and look at the Global Policy Settings.
A large selection of materials on Check Point from TS Solution . In order not to miss the following publications on the SandBlast Agent Management Platform - follow the updates on our social networks ( Telegram , Facebook , VK , TS Solution Blog , Yandex.Den ).