
On April 9, the FSTEC of Russia website published a draft "Methods for determining threats to information security in information systems." The methodology may become the first officially adopted document in the last 12 years, describing the procedure for modeling and determining the relevance of information security threats. Given that the identification of security threats is a fundamental measure in the construction of any protection system, the importance of the Methodology is difficult to overestimate.
In our article, we want to consider and evaluate the regulator's new approach to threat modeling, as well as answer the next question - how much this approach meets the current realities in the field of information security.
How is threat modeling now regulated?
Identification of actual threats to information security is required for a wide variety of objects: ISPDN, GIS, APCS, significant objects of CII, IS of financial organizations (hereinafter referred to as "information systems"). Therefore, processing information using such objects requires a clear understanding of who (or what) and how can cause a breach of information security.
At the same time, the only document currently in force in the field of modeling security threats is the "Methodology for determining actual threats to the security of personal data during their processing in personal data information systems"released back in 2008. In addition to old age, this document boasts a number of points indicating that, unfortunately, it has long lost its relevance and continues to be used only due to the absence of any replacement. A strict link to personal data, the use of the initial system security indicator as a factor influencing the determination of the relevance of threats, the absence of any division of responsibility in matters of modeling security threats when using external hosting are just some of the flaws that continue to be discussed by the information security community.
In such a situation, the owners of information (operators) have to improvise, independently "finalizing" the document for their own needs. This approach, firstly, is not absolutely legal (in its orders, FSTEC insists on using the methodological documents developed by them to determine security threats), and secondly, it is a very non-trivial task, especially in the absence of relevant experience from the executor. In this regard, the new Methodology should become, if not a panacea, then a tool that greatly simplifies the process of modeling information security threats.
Key features of the new technique
Scope of the Methodology The
first and one of the most important distinguishing features of the new Methodology is the scope of its application, which is now not limited to ISPD only. The document should be used to determine threats to the security of information during its processing using any objects, the protection requirements for which are approved by FSTEC. Such objects, as mentioned earlier, include significant objects of CII, ISPD, GIS and other types of systems.
In addition, the document directly provides for the possibility of developing and using industry / departmental / corporate methodologies,taking into account the features of the functioning of objects. There is no procedure for the development and approval of "subsidiary" methods, the only requirement is that they should not contradict the provisions of the Methodology.
Use of FSTEC BDUs in Modeling Security Threats
The main source of information about threats will be FSTEC BDUs, as well as basic and standard models of security threats. If for significant objects of CII and GIS such an approach was assumed earlier, then the question of using (or not using) the NDU in relation to ISPD has now received an unambiguous answer.
This approach looks quite logical, if not for one "but". The fact is that the variety of "basic and typical threat models" today leaves much to be desired - there is only one document published in the public domain that falls under this description, and even that is an extract and is aimed at all the same ISPD.
Does this mean that in the near future after approval of the Methodology, we should expect replenishment in the ranks of basic and typical threat models? The question remains open.
Security Threat Modeling Order The
updated order includes five steps in a specific sequence. The general scheme of the process presented in the Methodology is as follows:
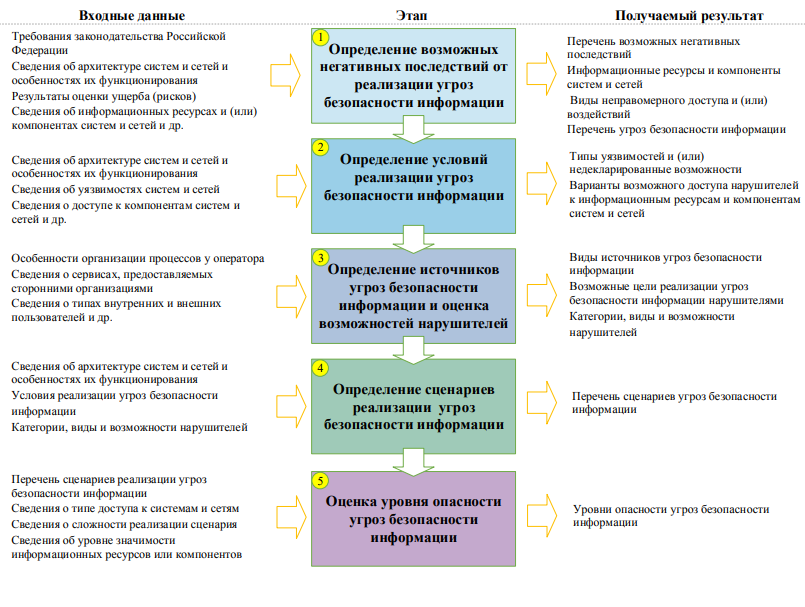
Forthe determination of the relevance of the threat to information security meets the stages from the first to the fourth. In accordance with the Methodology, a security threat will be relevant if there is at least one scenario for its implementation and if its implementation will lead to any negative consequences for the information owner (operator) or the state.
The goal of the fifth stage is to determine the danger of each of the current threats. In fact, this characteristic is for informational purposes only.and does not directly affect either the final document generated based on the simulation results, or the possible options for neutralizing the threat. It can be assumed that this parameter should be used to determine the order of closing the threat, but the small number of possible values of the indicator - "low", "medium", "high" - do not allow doing this with a sufficient degree of detail. Moreover, any of the threats that have come down to this step must be closed one way or another, so forgetting about the “non-dangerous” threat simply will not work. Thus, the true purpose of this parameter remains not fully disclosed.
It should be noted that work on modeling security threats should be carried out either by the owner of the information (operator) independently, or with the involvement of FSTEC licensees. This approach, in accordance with the regulatory documents of the regulator, is applied at the present time.
Determining the relevance of information security threats In
more detail, I would like to dwell directly on the procedure for determining the relevance of security threats.
1. So, at the first stage, it is proposed to determine all possible negative consequences from the implementation of security threats. Either an earlier assessment of damage (risks) should help in thisfrom violation of the main critical processes, either an expert assessment, or information received from the units operating the information system.
With any chosen approach, it is necessary to determine the information resources that ensure the execution of critical processes (information itself, software and hardware, information security tools, etc.) and the main types of illegal access in relation to each of the resources. The manual contains a list of the main types of resources and illegal access to them, as well as examples of identifying possible negative consequences.
2. At the second stage, it is necessary to determinethe presence of potential vulnerabilities and their types, the presence of undeclared capabilities in information systems, as well as the need to access the system to implement each of the security threats.
Penetration testing is the main method for identifying potential vulnerabilities in an information system at the stage of its operation, including taking into account the functionality and settings of protection tools.
3. The next, third step is to identify security violators and assess their capabilities.It is proposed to consider both anthropogenic and technogenic threats as sources of threats: the former are considered absolutely for all information systems, while the latter are only for those systems for which requirements are imposed on the stability and reliability of functioning.
The approach to identifying possible anthropogenic sources of threats - violators - is standard and consists in identifying specific types of violators, their potential and capabilities in the implementation of threats against the protected information system. It is worth noting that if there is a connection between the information system and the Internet, an external intruder with at least a low potential is always considered as an actual source of threats.
It should also be noted that according to the new Methodology,the intruder can have one of four levels of potential (basic, basic increased, medium and high), while the NDU, when describing the source of threats, uses only 3 levels (low, medium, basic). How to correctly provide correlation in this case is a question that also remains unanswered.
4. At the final stage, an analysis of possible tactics and techniques for implementing threats is carried out . To determine possible attack scenarios, the Methodology suggests using the tactics and techniques given in it, as well as additional information from the FSTEC database or other databases of computer attacks (most likely, this refers to the ATT & CK matrix and similar approaches).
There is one more point worth noting regarding the NOS.To date, this resource does not contain any structured information on possible ways to implement threats, and therefore a link to it looks inappropriate.
Excerpt from the matrix of tactics and techniques presented in the document:

In general, the proposed approach stands out significantly for its positive aspects, especially against the background of the order presented in the current methodology. Among the "pluses", at least, the following can be distinguished:
- rejection of inconvenient to use and far from always correct parameters of the initial security of the information system and the likelihood of the threat realization used in the 2008 methodology;
- , ;
- , , – , , ;
- , , ;
- , .
Thus, measures to determine the relevance of security threats are an integral and structured process that can take into account the peculiarities of the functioning of various types of information systems.
At the same time, it is worth noting the fact that the modernization of the approach to determining the relevance of threats made it much more laborious. An executor (or, more likely, a group of executors) is required to have in-depth knowledge of both the system infrastructure and various areas of information security, ranging from legislative norms to understanding (and, preferably, having practical skills) for implementing various types of attacks.
Identification of security threats to infrastructure hosted on external hostingParticular
attention is paid to the issueseparation of responsibilities when modeling threats to information systems located in external data centers and cloud services.
Determination of current security threats in the situation under consideration should be carried out by the information owner in conjunction with the hosting used. In general, hosting determines the current security threats to the infrastructure it provides and brings this information to its client - the owner of the information (operator).
For example, the boundaries of modeling security threats when renting virtual infrastructure are as follows:

If the hosting owner does not perform threat modeling, the Methodology does not recommend using his services.Given the fact that such a recommendatory measure will not always be observed, the question remains about how to be the owner of the information if he decides to use the services of such a hosting.
Keeping the threat model up to date
The results of threat modeling are drawn up in the form of a document in the form presented in the Appendix to the Methodology and approved by the head of the information owner (operator). It should be noted that the document form proposed for use has a fairly standard structure, repeating the main sections of the Methodology, while there is no section indicating the conclusions in it.or any other information explaining what to do next with these threats. This approach, unfortunately, gives the impression of an unfinished document describing the event, taken out of the general context.
But let's move on to the further stages of the threat model life cycle. It is understood that during the entire period of operation of the information system, the threat model should be updatedtaking into account changes in legislative requirements, changes in the architecture and operating conditions of the system, identification of new threats to information security. Thus, the update of the FSTEC BDU should also entail the update of all developed and used models of information security threats. Taking into account the fact that changes in the NOS are relatively frequent (from 1 to 3 times a year, in accordance with the information provided in the database), it will be necessary to return to the issue of updating the threat model regularly.
At the same time, it should be noted that the threat model can be kept up to date in the form of an electronic document. Whether it is necessary in this case to approve such a document with the head and if so, how exactly is still unclear.
Has the new Methodology been successful?
The published draft document demonstrates that in matters of ensuring the security of information systems, the regulator tries to keep up with the times and at the same time take into account the wishes of the owners of such systems.
Of the obvious advantages of the updated Methodology, it is worth noting:
- its versatility and, therefore, the possibility of using it for various types of information systems;
- a structured and understandable approach to determining the relevance of security threats;
- dependence of the relevance of threats on really important factors - the presence of potential negative consequences from the implementation of the threat and scenarios for its implementation.
At the same time, when reading the Methodology, it is clearly felt that this is only a draft, and not the final version of a methodological document:
- repeated mention of the NOS in the context of functions that it does not currently implement;
- ;
- , .
?
The new version of the Methodology is significantly different from the current one. If this document is approved (and so far there is no really significant reason why this may not happen), the owners of information systems will face the question of whether they need to update the existing threat models and, if so, how and when it is necessary do it.
And if the answer to the first question with a high degree of probability will be in the affirmative, then there is nowhere to get information on the subsequent ones. Obviously, some delay is needed when the new Methodology comes into force. Carrying out detailed and high-quality work on threat modeling is a process that requires significant resources, both time and human.
To learn about the practical side of the issue of modeling security threats, including using the new Methodology, continue to follow our information sources.
Vladislav Pavlov
Audit and Consulting Specialist, Acribia