Modern cars are turning from a mechanical vehicle into electronic gadgets on wheels - they download firmware updates from the Internet, transmit diagnostic information to the manufacturer and have interfaces for remote connection. As a result, cybersecurity risks are added to the usual risks for cars. Our new research is devoted to the study of these threats , the most important conclusions from which we will share in this post.
Features of connected cars
Technological units of a smart car are controlled through electronic control units (ECU). An ECU is a computer that collects data from sensors, switches, buttons connected to it, processes them and sends commands to the actuators. The most important part of each ECU is its firmware - the software on which the reliability of the vehicle's functioning depends. Some vehicles have more than 100 ECUs.
The interaction between ECUs takes place using the CAN / CAN FD, LIN, MOST, Ethernet and FlexRay protocols. Their common feature is increased reliability. They are resilient to failures in the harsh driving environment, but none have built-in security features such as data encryption or device authentication.
In the near future, mass models are expected to be equipped with Advanced Driver Assistance Systems (ADAS), autopilots, and vehicle-to-vehicle (V2V) and road infrastructure (V2I) systems. These systems will help prevent or mitigate road crashes, but they will also create new opportunities for attackers.
The popularity of car sharing has made centralized fleet control functions in demand, for example, the ability to track each car in real time, collect telemetry data and control engine operating modes.
The demand for new technologies is forcing automakers to shorten development and production cycles in order to continue to accelerate the pace of new technologies adoption. The technological sophistication race leaves cybersecurity issues unresolved. The result is logical: new cars contain many potential vulnerabilities.
Car cyberthreats
A car connected to the Internet has a significant number of open ports that could potentially be exploited by cybercriminals. And given the superficial attitude of car developers to safety issues, penetrating any available ECU is a relatively simple task. Having seized control of one module, an attacker can move from one control block to another and carry out a wide variety of attacks, for example:
- DoS- , ;
- - ;
- , , ;
- ;
- , , .
An additional source of threats is often the car owners themselves, who are chip-tuning enthusiasts. They purchase Wi-Fi or Bluetooth scanners that connect to the CAN bus via the OBD-II diagnostic connector. As a rule, the firmware of such scanners does not contain means of protection against attacks, so anyone can sit next to a laptop, take control of the dongle and add a little "chip tuning" at their discretion.
Head-mounted multimedia devices
Another vulnerable element that is rarely taken into account is multimedia head units with GPS navigation and other functions. Car owners often replace standard multimedia systems with alternative ones to get additional features.
Most of these devices run on outdated Android versions that are barely updated. Popular with drivers, the automatic adaptation of the sound volume to the driving speed requires that the head unit be connected to the CAN bus. As a result, a remote attacker can take advantage of known Android vulnerabilities to launch an attack on the CAN bus.
The most unpleasant thing: vulnerable versions of Android are used even in the standard multimedia devices of some cars.
Insecure firmware
Almost every smart car owner wants this car to be faster and more powerful than the manufacturer envisions. And best of all, if you can add the functions of the older model to the cheaper younger model. Garage workshops specializing in such modifications replace the ECU firmware, which is the OS along with the bootloader. These craftsmen are not even bothered by the fact that the firmware files must be signed with the manufacturer's digital signature: by modifying the code in the ECU, they disable signature verification, as a result of which the unit works with any firmware, including malicious ones.
Vulnerabilities in the CAN bus
Developed by Bosch in 1983, the CAN bus was officially introduced in 1986 and first used in production vehicles in 1989. Four years later, ISO adopted CAN as a standard for cars, and since then, this bus and the associated protocol for communication have been used in almost every vehicle.
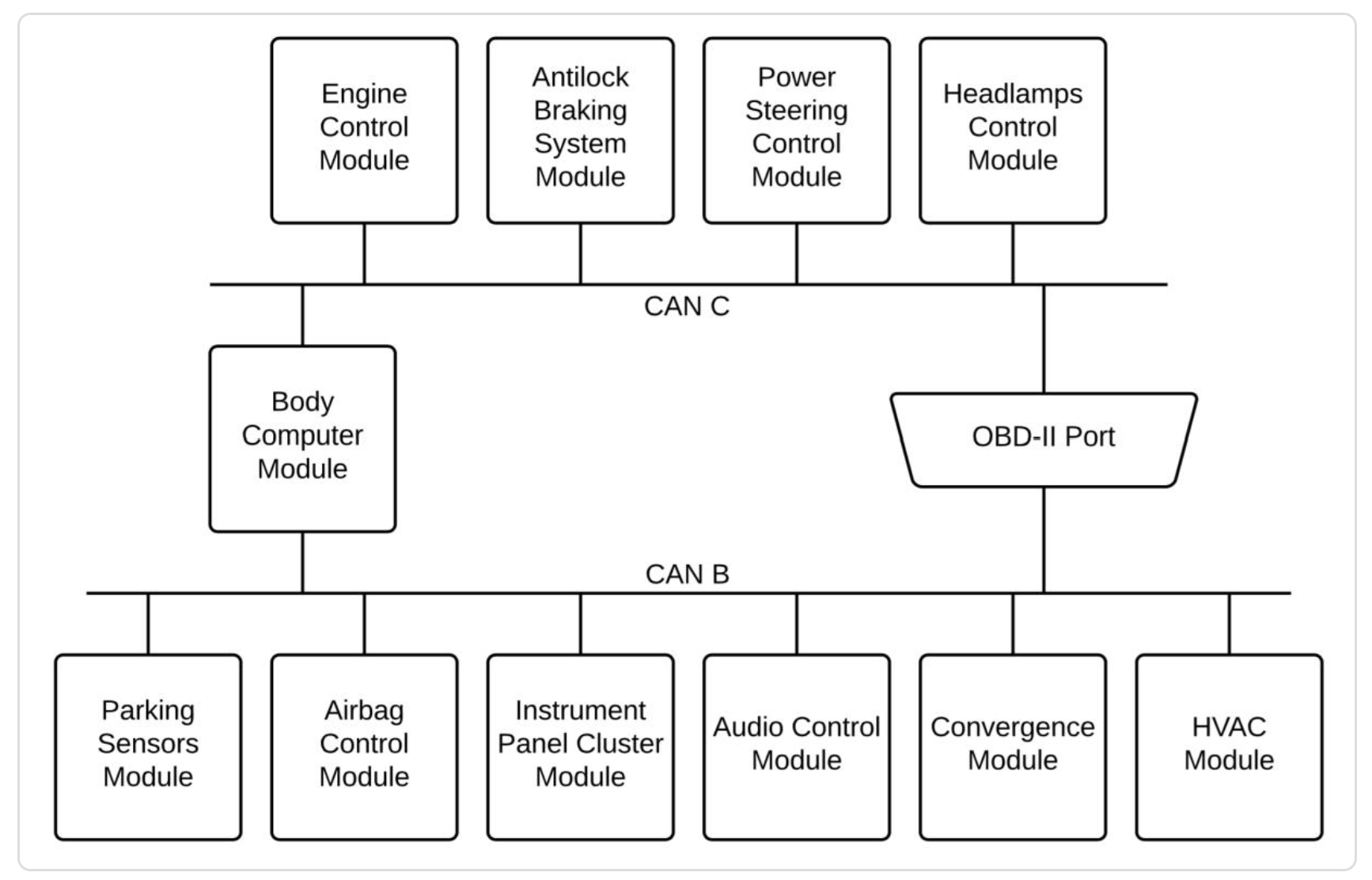
Vehicle systems connected to CAN. Source: Trend Micro
All vehicle devices communicate via the CAN bus. Thanks to this, the head multimedia device recognizes, having received information about the deployed airbags, that you need to call the emergency service and report the accident.
Devices connected to CAN interact with each other, transmitting special messages - frames. These messages can contain a variety of information, including error messages. The joint research team has developed an attack on the CAN bus that exploits the error handling features in this case:
- errors occur when the device reads values that do not match the original expected value on the frame;
- when a device detects such an event, it writes an error message to the CAN bus to "recall" the erroneous frame and notify other devices to ignore it;
- , , CAN, Bus Off, . . CAN - CAN, — , ;
- , , Bus Off, .
This can become dangerous and even fatal, especially if the airbags or ABS can be disabled in this way.
To carry out an attack, it is enough to connect a device to the CAN, which will repeatedly send frames with errors to the CAN. And for connected cars, no device is needed - just take advantage of vulnerabilities in the ECU and launch an attack remotely.
Trend Micro Presentation on CAN Attack:
The above has already been tested in practice. In 2015, Charlie Miller and Chris Valasek demonstrated remote hacking of a connected Jeep Cherokee . The driver, who was warned of the experiment, drove onto the highway, after which the researchers took over control of his car's systems. They turned on the music and air conditioning at full blast, set the windshield wipers to work, and then made the car crawl like a turtle, so that other drivers honked the participant in the experiment, overtaking him. And the worst thing: he could not do anything - the control of the air conditioner, multimedia system and even the gas pedal was intercepted by hackers. After the publication of the results of the experiment , Chrysler recalled 1.4 million vehiclesequipped with the remotely hacked UConnect system through which the researchers hacked the Jeep Cherokee.
To address these pent-up safety concerns, the ISO / SAE industry group has developed a set of guidelines for the safety of connected vehicles - ISO / SAE 21434 .
What the new standard offers
Governing safety everywhere
This means that safety must become a mandatory part of all processes from conception and development to production, operation, maintenance and decommissioning. Risk management should be based on the proven ISO 31000 standard.

Risk management framework in accordance with ISO 31000. Source: Trend Micro
Risk monitoring
In cases of potential security incidents, the standard provides checkpoints for all companies, suppliers and suppliers:
- top-down cybersecurity management must be based on continuous risk monitoring throughout the organization, including production and the entire supply chain;
- To implement top-down cybersecurity, organizations will need a strong cybersecurity culture and an emphasis on quality training;
- leaders at all levels must work to integrate cybersecurity knowledge at all stages of the business and implement it in their departments; to do this, you can use the recommendations of the ISO / IEC 27001 information security management standard.

Measures to ensure the implementation of information security standards in accordance with ISO 27001. Source: Trend Micro.
Cybersecurity Event Assessment
This process determines the level of impact of a cybersecurity event and the appropriate response to it. Each event needs to be analyzed to determine how it affects an object or component. Taking into account the decision to eliminate the risk, the response procedures can be applied in subsequent stages.
Vulnerability analysis
For each identified vulnerability, it is necessary to establish whether it can be used for an attack. All errors and events should be analyzed to identify potential vulnerabilities, for example:
- missing requirements or specifications;
- architectural or design deficiencies, including incorrect design of security protocols;
- weaknesses or incorrect implementation of security protocols, including hardware and software errors;
- weaknesses in company processes and procedures, including misuse and inadequate user training;
- use of obsolete functions, including cryptographic algorithms.
Vulnerability management
To prevent potential criminals from exploiting the discovered vulnerability, the following measures can be taken:
- temporary shutdown of non-critical components;
- risk notification to users;
- development and review of code fixes by the development team;
- creating and deploying security patches.
Update management
For most cars sold, firmware updates can only be done at authorized service centers, because:
- installation of updates for critical ECUs cannot be performed while they are being moved for the safety of users;
- The total size of a software update requiring installation can be several gigabytes, making time and bandwidth important factors limiting its immediate deployment;
- updating the ECU can disable it, which means that they will have to be replaced with serviceable ones at authorized service centers.
As a result, updates are usually only performed when the user receives a malfunction message and not for security reasons. As a result, most cars have not been updated for years.
The new ISO / AWI 24089 "Vehicles - Software Update Engineering" is intended to solve this problem. It is currently in the early stages of development, so it is difficult to say how it will affect the update procedure.
How to be
We propose a multi-layered approach to securing connected vehicles, both using the most up-to-date threat landscape intelligence and providing pre-construction security measures for vehicles, networks and ancillary services. These measures should significantly reduce the likelihood of a successful attack and mitigate its possible consequences.
It is critical to maintain a holistic approach to improving the safety of connected vehicles, while avoiding siled solutions. This is the only way to achieve uniform management control throughout the system.

The recommended approach for securing a connected vehicle is a seamless multi-layer security system. Source: Trend Micro.
To do this, companies and suppliers must implement a reliable and functional solution that
- supports control of connected cars;
- protects against attacks aimed at vehicle, connected networks and backend systems;
- provides a single context for events from each system as they occur.
This ensures a seamless multi-layered response to cyberattacks for protection, detection and response, as well as monitoring all stages of the production and operation of high-tech vehicles.