
Not so long ago, I wrote about Netflow / IPFIX monitoring and about Cisco StealthWatch, an analytical solution that allows you to detect events such as scans, the spread of network worms, spyware, illegitimate interactions and various kinds of anomalies.
Links to all articles in the cycle:
1) StealthWatch: basic concepts and minimum requirements. Part 1
2) StealthWatch: deployment and configuration. Part 2
3) StealthWatch: analysis and investigation of incidents. Part 3
4) StealthWatch: Integration with Cisco ISE. Part 4
5) Stealthwatch Cloud. Fast, convenient and efficient solution for cloud and enterprise infrastructures. Part 5
Monitoring cloud infrastructure is no longer a new task, as each major player has its own tools - Amazon CloudWatch or Amazon S3, Google Stackdriver, Azure Monitor. These tools are great for monitoring applications, performance and infrastructure in general, but they do not close security tasks (and the cloud providers themselves are not very concerned about it): the spread of malware, botnet communications, anomaly detection, scanning attempts, illegal access ( including options using legitimate credentials) and much more.
StealthWatch Cloud
StealthWatch Cloud (SWC) is a SaaS solution that resembles Stealthwatch Enterprise (it's not for nothing that Cisco has recently blurred the boundaries between these two solutions in its architecture), but takes into account the specifics of cloud environments. If for Stealthwatch EnterpriseAn important source of information is telemetry based on Netflow, Stealthwatch Cloud uses cloud logs as such data (not limited to logs, receiving other types of telemetry). Then the usual actions for StealthWatch are performed: modeling objects, building their behavioral models, detecting deviations, checking compliance with policies, detecting security events (both built-in and user-defined) and much more. Threats, abnormal and malicious activity are detected faster, as a result, the damage from the incident is reduced or even completely leveled.
At the same time, Stealthwatch Cloud alarms have a function familiar to the 21st century: the customer can evaluate the usefulness of the generated alarm with one click of the mouse. Currently 96%alarms generated for existing StealthWatch Cloud customers were found helpful.
The scope of StealthWatch Cloud is not limited to clouds: the solution can be used to monitor public clouds, private clouds, classic corporate infrastructure, and, of course, a hybrid architecture using any combination of these three components. Considered in Stealthwatch Cloud and multi-tenant security service options.
Deployment options can be thought of as follows

Figure 1. StealthWatch Cloud use cases
StealthWatch Cloud can be used when working with public clouds (Amazon, Azure, Google), private and hybrid clouds, which are built on infrastructure from Kubernetes and, of course, corporate networks.
By the way, Mail.ru is a certified Kubernetes (K8s) partner . K8s pod event logs and traffic flows between these pods are sent to the StealthWatch Cloud. The result is full visibility of the K8s pods, private cloud entities and the detection of security incidents mentioned earlier. Figure 2 shows the interaction diagram.

Figure 2. Scheme of integration of StealthWatch Cloud with Kubernetes
In the case of working with private corporate networks, the installation of a virtual machine (Virtual Sensor is an analogue of Flow Sensor in StealthWatch Enterprise). Figure 3 shows that Netflow, IPFIX, SPAN are sent to the sensor, and the sensor sends information via an encrypted tunnel to the StealthWatch Cloud, where all analytics are performed. Thus, the computing power of the customer is not used at all from the word, and the implementation and the pilot are carried out as quickly as possible.

Figure 3. StealthWatch Cloud integration with a corporate network I
would also like to note that the Virtual Sensor installation entails a lot of positive aspects:
- Integration with Cisco ISE , AD is supported ;
- ETA (Encrypted Traffic Analytics) technology works, which allows detecting malicious connections in encrypted traffic without decrypting it. Moreover, this technology allows you to “parse” HTTPS into TLS versions and cryptographic protocols that are used for connections;
- Signature analysis is available along with signatureless analysis based on telemetry.
There is an option without installing a virtual sensor (Virtual Sensor), but then StealthWatch Cloud will only be able to work with telemetry, that is, signature analysis will not be available.
A few more advantages of StealthWatch Cloud:
- Flexible licensing model for mega-streams (Effective Mega Flows - EMF, where 1 EMF = 1 million logs, which are previously deduplicated, i.e. remain in a single copy, and are counted at the end of the month);
- Support for multi-user environments (this is a plus for partners who provide SOC for outsourcing, you can monitor all customers from one console).
Conclusions :
When working with public, private and hybrid clouds, StealthWatch Cloud detects the following security incidents :
- Abnormal behavior of users, hosts
- Botnet activity
- Brute force
- Remote access attempts, including from unusual geolocations
- Distribution of malicious software and access to malicious URLs
- Violation of interaction roles
- New devices, streams
- Scan attempts
- Flood traffic, storms
- Intrusion detection system (IDS)
- Specific events for AWS, Azure, GCP
When working with private corporate networks, almost all StealthWatch Enterprise functionality is added.
Integration with Amazon Web Services (AWS)
StealthWatch Cloud uses the AWS Lambda API (AWS Automated Code Execution and Compute Management) and Identity and Access Management (IAM) APIs. This allows you to receive information about access policies to instances, changes in program code execution, audit instances, and more.
Additionally, the SWC uses flow data (network layer interactions) from Amazon CloudWatch or Amazon S3 monitoring services. VPC (Virtual Private Cloud) Flow logs are flow data in AWS terminology.
Therefore, from the administrator's side in your Amazon Web Services personal account, you must grant permission to read flows (VPC Flow logs) and event logs from Amazon CloudTrail, Amazon IAM, Amazon GuardDuty, AWS Lambda, Amazon Inspector, and AWS Config, if you are using them.
Figure 4 shows how StealthWatch Cloud and AWS work.
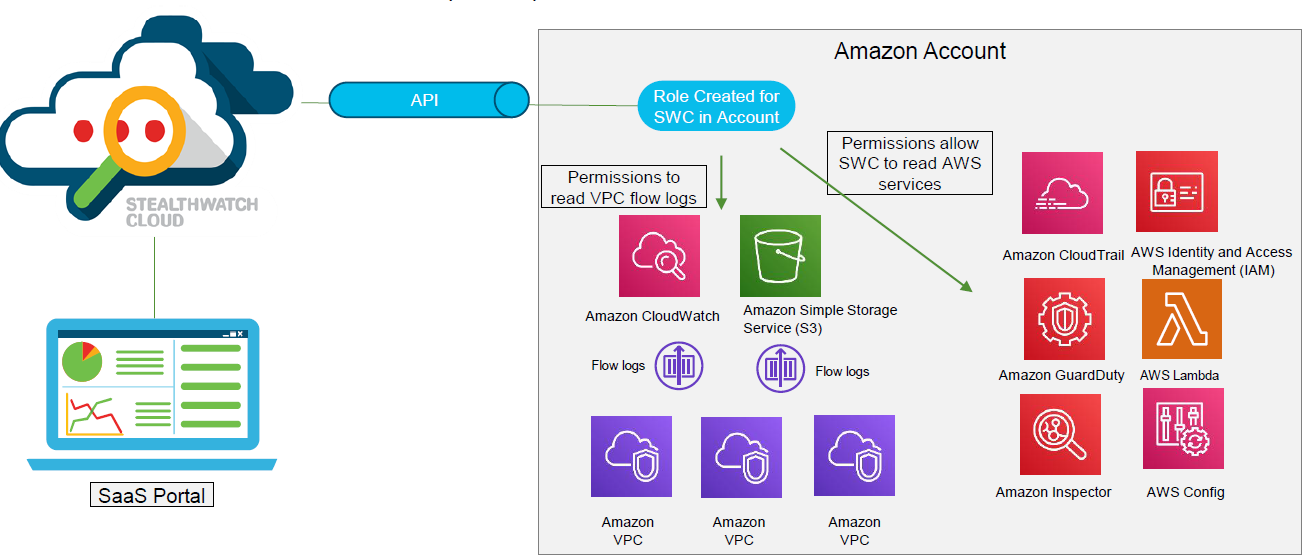
Figure 4. StealthWatch Cloud and AWS workflow
In turn, SWC conducts analytics and displays it on dashboards, allowing you to quickly see the current traffic, infrastructure load and even predict future load - Figure 5.
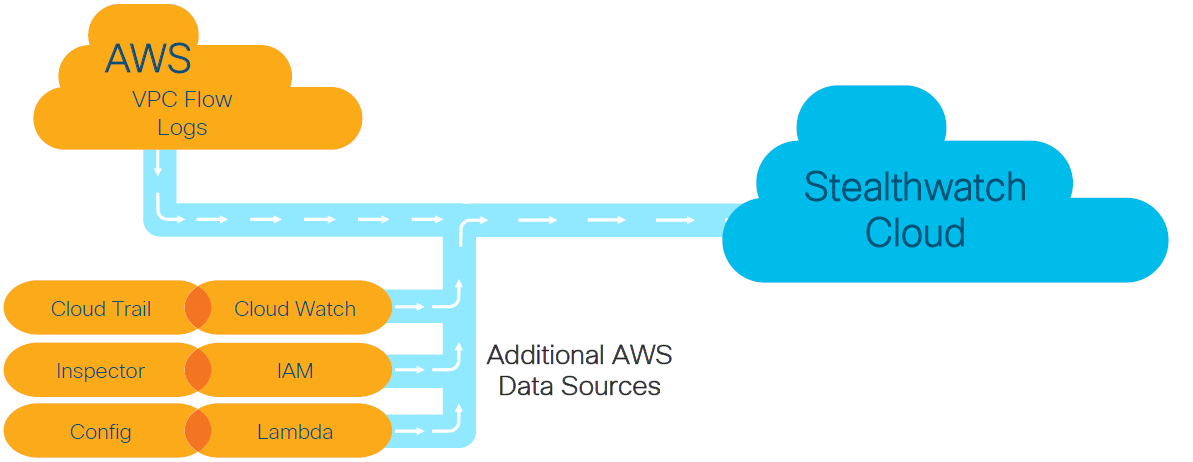
Figure 5. Amazon Web Services monitoring console in StealthWatch Cloud
Integration with Microsoft Azure
For Azure StealthWatch Cloud, it uses the Azure API to read event logs that contain information about north-south and west-east traffic within the cloud infrastructure. Such logs are called NSG Flow logs. In essence, they are similar to Netflow streams, as they contain packet headers.
The big difference from the AWS case is that Azure can send a copy of traffic from virtual machines via VTAP - virtual traffic taps. VTAP is a technology developed by Microsoft but is available for integration with all third party solutions.
Using VTAP is effective because:
- A copy of traffic from the required segments will allow SWC to get full visibility and, as a result, maximum threat detection.
- The load on virtual machines does not increase as VTAP is traffic from the virtual switch, not the machine itself.
- Interaction with SWC is carried out via an encrypted TLS tunnel.
Figure 6 shows the interaction diagram.

Figure 6. Scheme of StealthWatch Cloud and Microsoft Azure
Integration with Google Cloud Platform
When integrating with the Google Cloud Platform (GCP), it is only possible to access the API from the SWC side to read the previously mentioned VPC Flow event logs (the same as those of Amazon) from the Google Stackdriver. Google Stackdriver is a service that collects logs and metrics from GCP, monitors applications, virtual machines and Google Cloud infrastructure in general. However, working only with VPC Flow event logs gives a little less visibility. The scheme of work is shown in Figure 7.
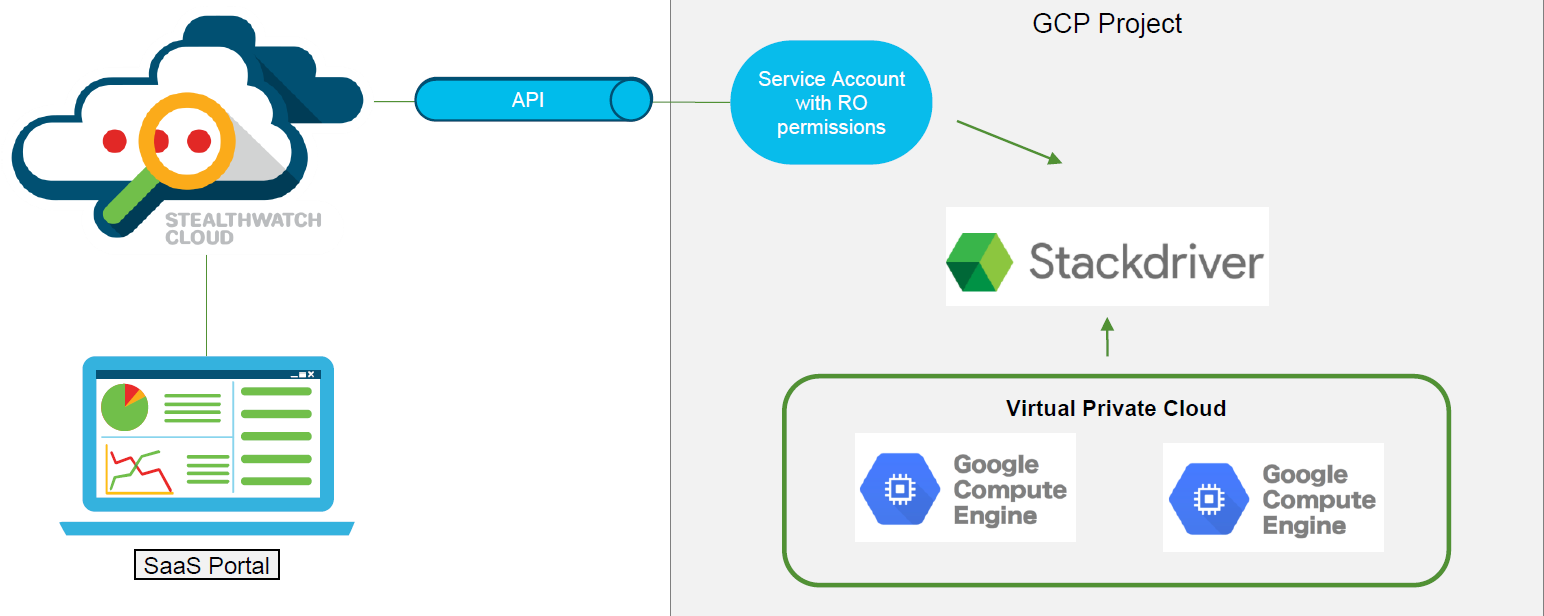
Figure 7. The scheme of work of StealthWatch Cloud and Google Cloud Platform
SWC vs. SWE
While Stealthwatch Cloud and Stealthwatch Enterprise perform similar tasks, their application areas and differences in the main telemetry sources mean different capabilities.
Comparative data are summarized in the table below.
| Compare option | SWC | SWE |
|---|---|---|
| Deployment speed | ||
| ; 4 GB RAM, 2 CPU, 60 GB HDD ( Virtual Sensor) | 36 GB RAM, 6 CPU, 385 GB HDD | |
| ISE | , Virtual Sensor | |
| ETA/Cognitive Threat Analytics | ||
| Kubernetes | ||
| (VPC Flow, NSG Flow) API, Netflow/IPFIX | NetFlow, sFlow, jFlow, cFlow, Netstream, nvzFlow, IPFIX, Packeteer-2 | |
| , AWS, Azure, GCP, Kubernetes | , | |
| - (EMF) | (fps) |
In turn, StealthWatch Cloud is attractive for its speed of deployment (especially for the pilot), and it does not require deploying and maintaining virtual machines, except for the Virtual Sensor. SWC allows you to monitor infrastructure in public, private clouds and supports native integration with a unified information security management platform Cisco SecureX solutions .
How to test it?
There are two options for a free pilot project: by yourself or with a partner. In the case of the first option, it is suggested to refer to the site . The license is issued for 60 days, configuration guides are provided on the same Cisco site. If you want to dive into the details and solve your monitoring tasks as efficiently as possible, please contact us at the link .
Conclusion
StealthWatch Cloud is a multifaceted solution that allows you to get full visibility in the shortest possible time in a private, public or hybrid cloud, be it Amazon Web Services, Microsoft Azure or Google Cloud Platform. At the same time, this solution can be used for monitoring corporate networks, while having almost the same functionality in comparison with the on-premise StealthWatch Enterprise. Saving time, technical and human resources when working with SWC are clear advantages.
In the near future we are planning several more technical publications on various information security products. If you are interested in this topic, then stay tuned in our channels ( Telegram , Facebook , VK ,TS Solution Blog )!