
During the pandemic, the European Commission approached me with a proposal to develop a privacy-protected social contact tracking token, which you can read about on the Simmel project page . And soon, Singapore announced the development of the TraceTogether token. As part of this event, I was invited to participate in the review of their solution... The urgency of the COVID-19 situation and the significant complexity of creating supply chains led to the fact that we found ourselves in a situation with the landing gear of an aircraft that touched the runway. Given the many privacy and technology concerns, the situation was tricky and could not be captured in a series of tweets. Therefore, I will describe my impressions in the form of short essays. Since I managed to work with TraceTogether for only an hour, for the most part I will talk about the context in which I will evaluate this token.
Tracking social contacts
The idea is simple: if you get sick, then you need to identify people with whom you have been in close contact and check if they are sick. If done quickly enough, the spread of COVID-19 can be contained and much of society will continue to function normally.
But there are some subtleties in the implementation that I tried to digest. Dr. Vivian Balakrishnan, Acting Minister of the Smart Nation Initiative , briefly informed us at the meeting that the Exposure Notification system developed by Apple and Google did not show the "graph". To get a sense of how important it is for epidemiologists to build a contact graph, I drew a few diagrams to illustrate contact tracing scenarios.
Let's start with the simplest scenario.
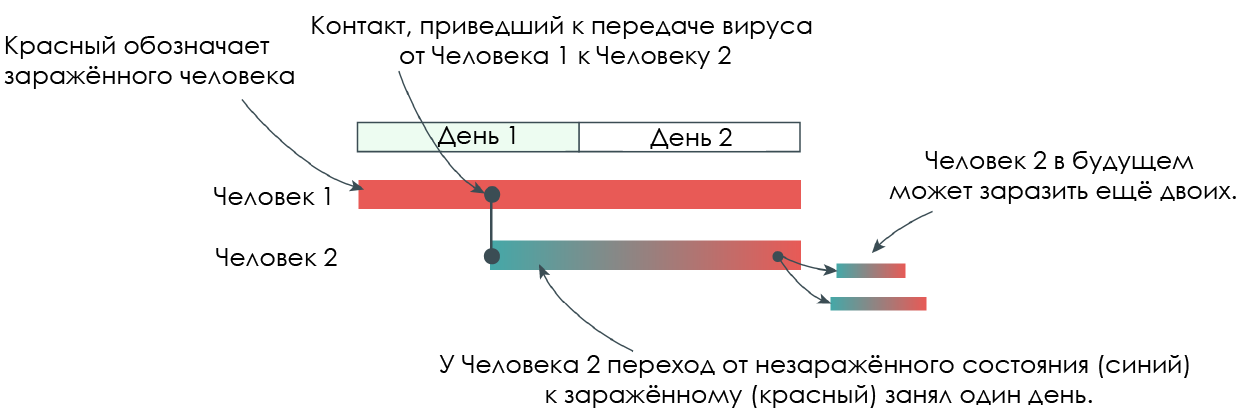
The diagram shows two people. On the first day Person 1 is already infected, but symptoms are mild. In the middle of the day, he is in contact with Person 2. After a short incubation period, Person 2 becomes infectious at the end of the second day. During this time, he may not have symptoms. In the future, he may infect two more. The example shows that if Person 2 is isolated early enough, two new infections can be prevented.
Now let's look at a more complex scenario without contact tracking. We will continue to consider Human 1 as a carrier with mild or no symptoms, but infectious at the same time: this is the so-called " supercarrier ".
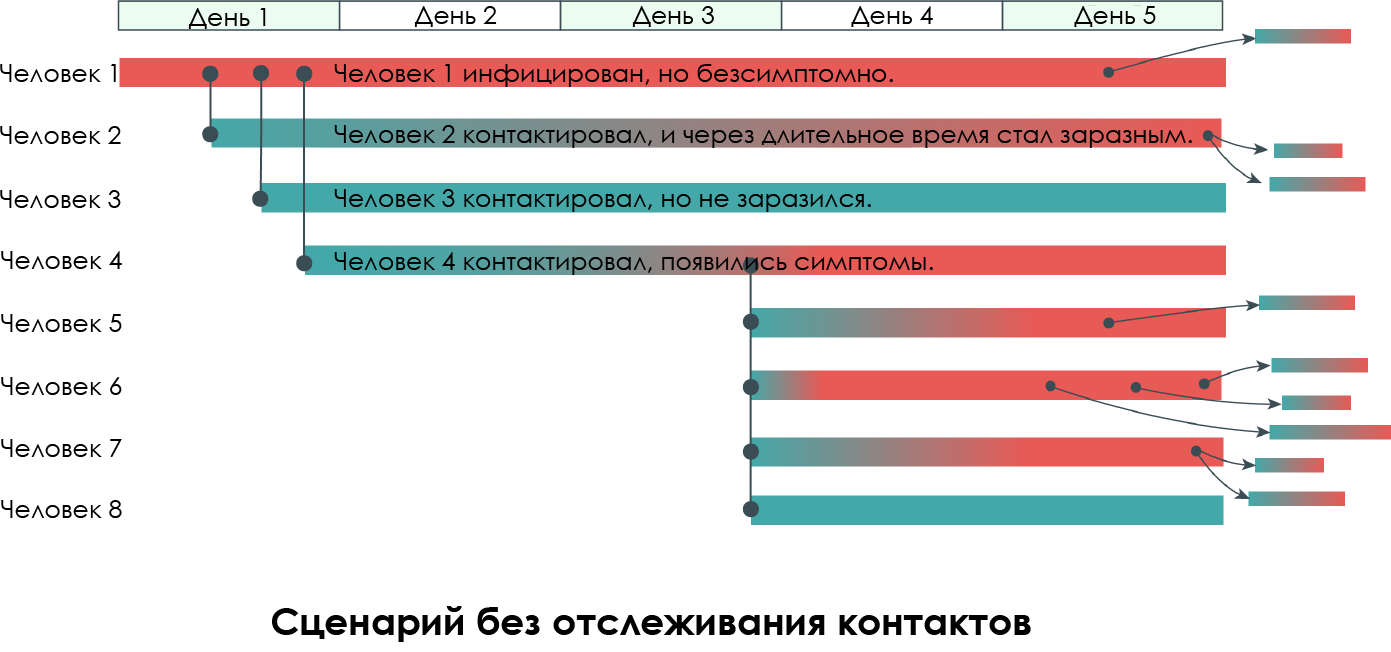
This graph shows the timelines of eight people. Person 1 is completely responsible for infecting several people over the course of several days. Please note that the incubation periods before a person becomes infectious is different for everyone. Moreover, infectiousness may not be accompanied by symptoms.
Now let's add contact tracking.
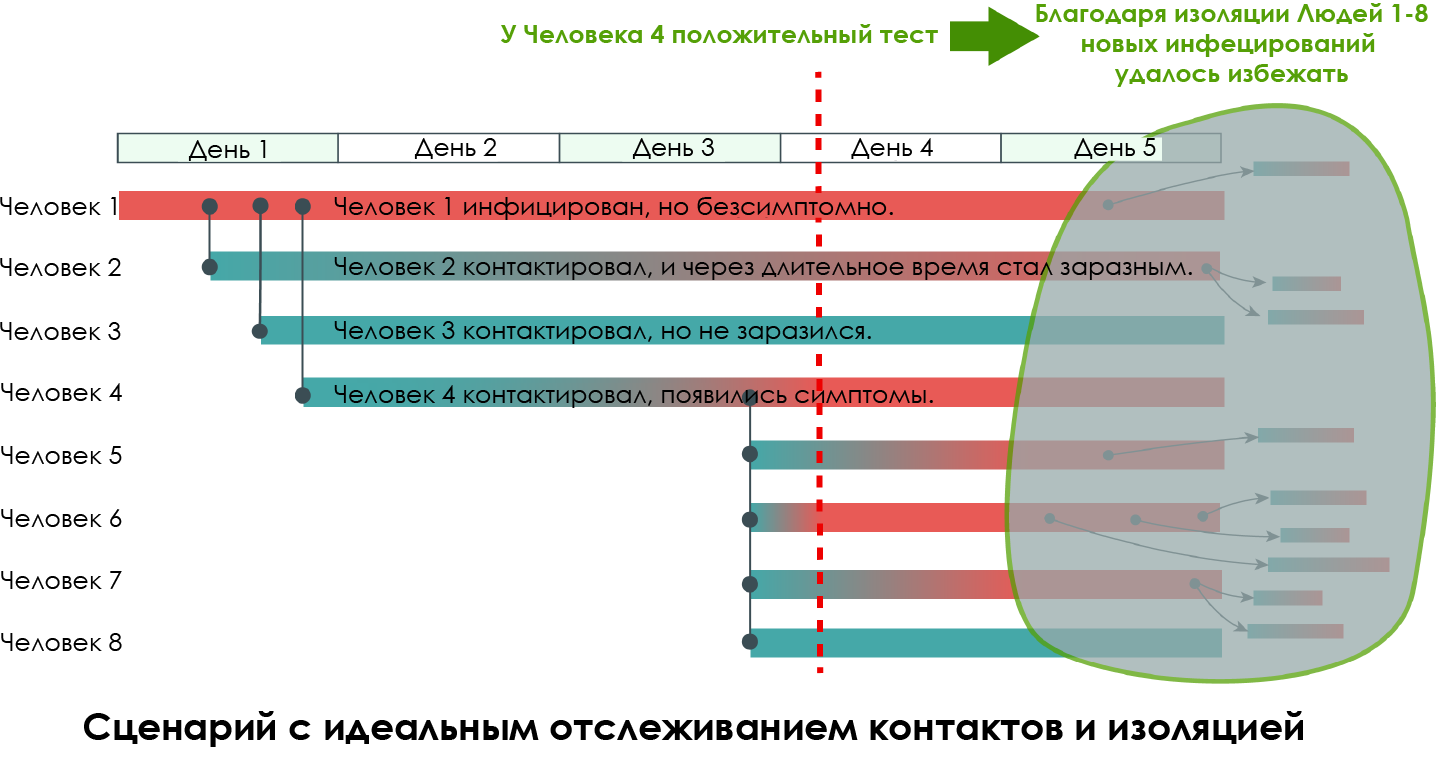
The scenario is the same, but with the "platonic ideal" of contact tracing and isolation. Person 4 develops symptoms, tests and tests positive on the fourth day. All contacts with him are isolated, and dozens of his colleagues and friends avoid infection in the future. Importantly, contact graph analysis also reveals common contacts between Person 4 and Person 2, thereby identifying Person 1 as the original asymptomatic carrier.
There is a slight difference between "contact tracing" and "contact notification". The Exposure Notification system from Apple and Google only notifies of direct contacts of an infected person. The significance of this subtlety is hinted at by the fact that it was originally called "Contact Tracking with Privacy Protocol", butit was renamed in April.
To better understand the limitations of notifying infected contacts, let's look at another scenario. It is similar to the previous one, only instead of tracking the entire graph, we will only notify the direct contacts of the first person who has symptoms - that is, Person 4.
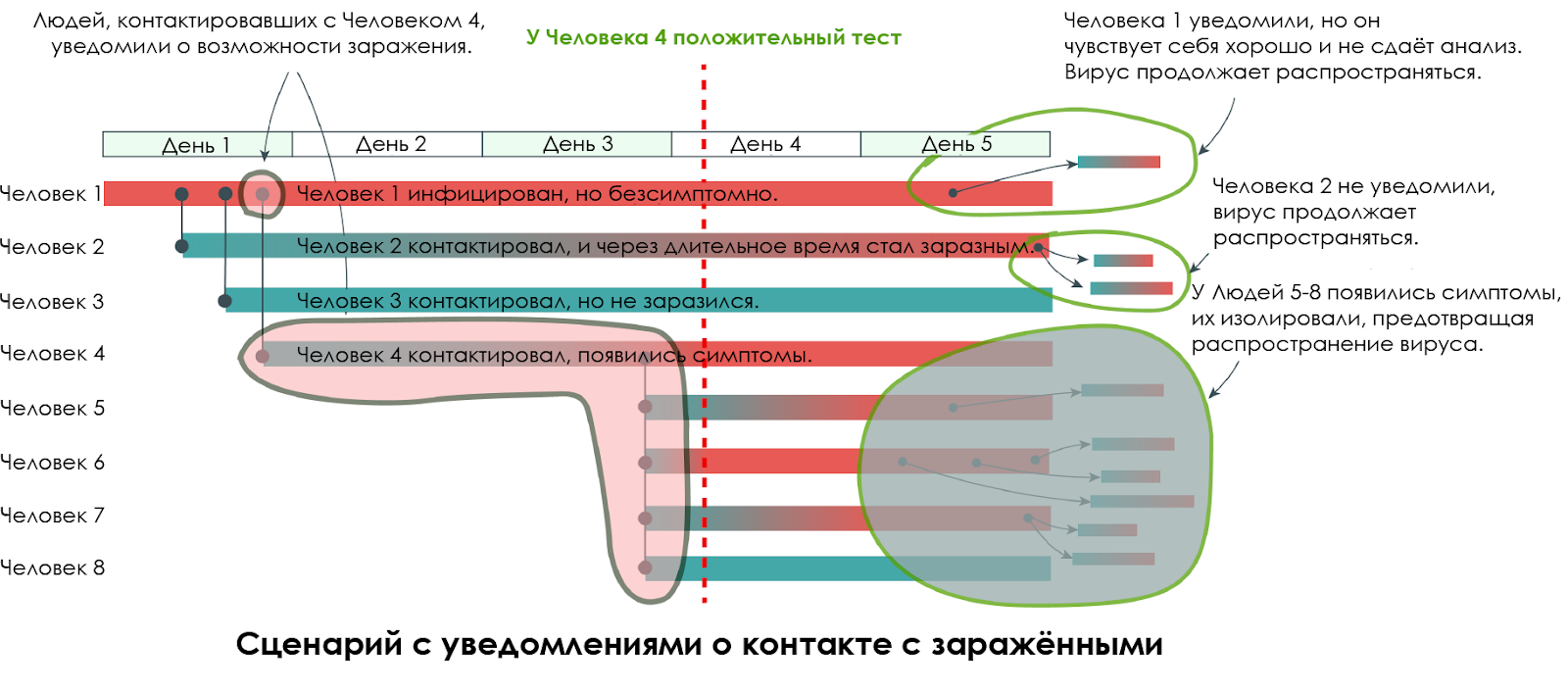
If limited to notifications, carriers with mild or no symptoms, like Person 1, will receive misleading notifications that they have been in contact with a positive person, when in fact it was Person 1 who infected Person 4 with the virus. Person 1 - feeling good but contagious - will continue to live as usual, apart from his surprise that his entire environment is infected with the virus. Therefore, some infections cannot be avoided. Moreover, Person 2 is a hidden node in relation to Person 4, because Person 2 is not included in the notification list for direct contacts of Person 4.
In short, the Exposure Notification system itself does not allow determining the cause-and-effect relationships of infections. A complete contact graph helps to identify a carrier with mild or no symptoms. Moreover, it is already known that a significant proportion of carriers are asymptomatic. These people are contagious, but they feel good and visit crowded metro stations, eat in public places. In the conditions of Singapore, asymptomatic carriers can create dozens of clusters of new infections within days, if not hours, in contrast to less densely populated countries like the United States, where infected can only contact a few people during the day.
The inability to quickly identify and isolate super carriers with mild symptoms prompted the development of the TraceTogether device, which allows tracking social contacts with the construction of a complete graph.
About privacy and contact tracing
Of course, full contact tracing has very serious privacy implications. And the absence of this tracking has significant potential health and life risks. There is a proven solution that does not violate privacy: advanced interlocking, like an automatic circuit breaker. Of course, this requires additional costs.
Of the three elements - privacy, health and economy - we can only choose two. There are active debates on this topic, but this is beyond the scope of the article. From a discussion point of view, let's assume that contact tracing is being implemented. In this case, it is the responsibility of technicians like us to try to find a compromise between reducing privacy and promoting public policy.
In early April to Sean Cross and me throughNLnet was approached by representatives of the European Commission's NGI program and proposed to develop a hardware token for tracking social contacts while maintaining privacy. This is how “ Simmel ” was born . The solution is not perfect, but Simmel still has important privacy features:
- Strong isolation of user data . By disabling the collection and generalization from smartphone sensors, we get rid of the risk of leakage of GPS data or other geolocation information. It also makes metadata-based attacks against privacy very difficult.
- . . , , . , .
- . , . ( ).
- . , , (, ).
Why a hardware solution?
Doesn't a software solution have numerous advantages?
The TraceTogether team said Singapore needs hardware tokens to better serve low-income citizens and iPhone users. The former cannot afford to buy a smartphone, while the latter can only use Apple-approved protocols like Exposure Notification (which does not allow full contact tracking).
Simmel's solution demonstrates that I am a fan of hardware token, but only from a privacy perspective. Apps and smartphones in general harm people's privacy. If she really bothers you, then leave your smartphone at home. Below is an explanatory table. Red crosses represent known potential privacy violations in certain usage scenarios.
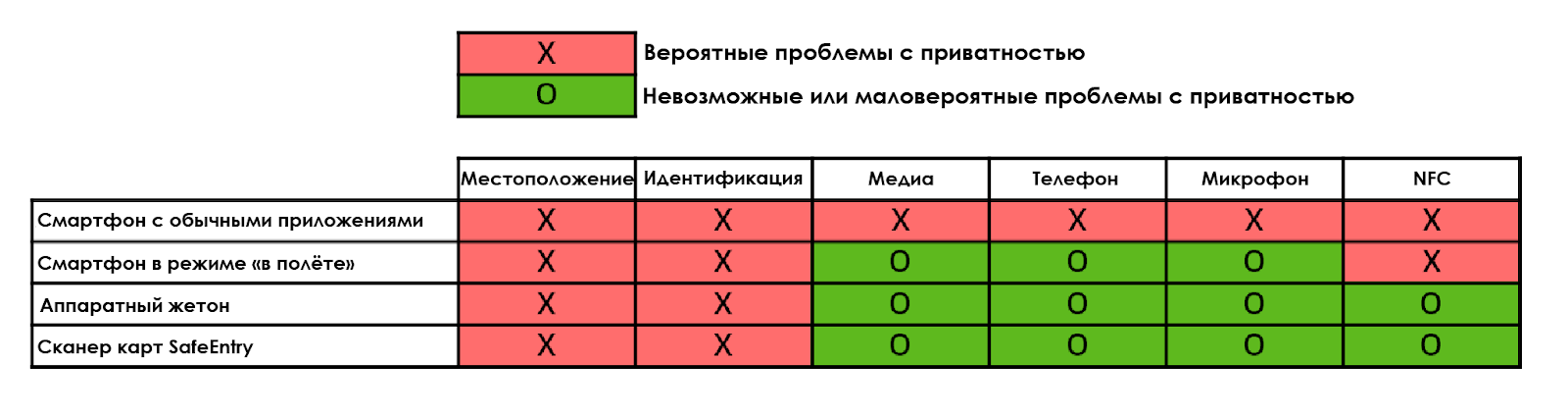
A tracking token (as Singapore suggests) will help the authorities identify your location and identity. Technically, this happens when you turn in a token to a healthcare facility. However, it is likely that the authorities will deploy tens of thousands of receivers on the island to record the movement of tokens in real time. This is a problem, but compare to your smartphone, which usually transmits a range of unique and unencrypted identifiers, from IMEI to Wi-Fi MAC address. Since all of these identifiers are not anonymized by default, they can be used by anyone, not just the authorities, to identify you and locate you. However, the construction of TraceTogether does not significantly affect the status quo in terms of "big infrastructure" attacks on the privacy of individuals.
It is important that the token uses an anonymization scheme to transfer the ID, so it cannot disclose your identity or location data to third parties, this information is available only to the authorities. Compare this to the SafeEntry ID card scanner when you have to hand over your ID to the staff at SafeEntry kiosks. This is a less secure solution because employees can read your data (including your home address) by scanning a card, so there are red crosses in the Location and Identification columns.
Going back to the smartphone, "regular apps" - like Facebook, Pokemon Go, Grab, TikTok, Maps - are often installed at most resolutions. Such a smartphone actively and constantly discloses your location, photos and videos, phone calls, data from the microphone and from the address book, as well as NFC data (used for contactless payment or information transfer) to a wide range of companies. Although every company swears that it will "anonymize" your data, there is so much data transferred that it is enough to press almost one button to de- anonymize... What's more, your data is tracked by intelligence agencies around the world, thanks to the broad powers of governments around the world to legally obtain data from local service providers. Not to mention the constant risk of facing intruders, exploits or fake interfaces that are designed to convince, trick, or coerce you into revealing your data.
Let's say you're quite paranoid and reasonably turn on airplane mode on your iPhone most of the time. Do you think there is nothing to worry about? You are wrong. For example, in this mode, the iPhone still uses a GPS receiver and NFC . I also found out that the iPhone has random and unexplained spikes in Wi-Fi activity.
In general, I can give the following main arguments in favor of the hardware token protecting privacy better than the application:
There is no collection and generalization of data from different sensors
The data collected by the token is severely limited by the fact that it is not able to summarize information from different sensors, as smartphones do. And although I only worked with the device for an hour, I can say with high confidence that TraceTogether hardly has any other capabilities beyond the required Bluetooth Low-Energy (BLE) transmitter. Where did I get it? It's all about physics and economics:
- : , . , , ? , , BLE.
- : , . , , . .

TraceTogether 1000 mAh battery. Your smartphone battery has roughly three times the capacity and requires daily recharging.
Financial arguments are weaker than physical ones, because the authorities can always prepare a limited number of "special" tokens of any value to track individually selected people. However, in this case, physics plays a role: no amount of money invested by the authorities in the development can break the laws of physics. If Singapore can develop a massive battery that in this form factor will power a smartphone sensor for months - well, let's say, the world will be completely different.
Civic hegemony over social contact statistics
If we assume that the final version of TraceTogether does not allow using BLE to read data (I hope we will confirm this at a future hackathon), then citizens have absolute ownership of their contact statistics, at least until they transfer it to someone.
Thus, the authorities, probably unintentionally, are pushing people to resist the TraceTogether system: a person can break his token and "log out" at any time (but just pull out the battery first, otherwise you can burn the apartment). Either act more carefully and “forget the badge at home,” or wear it in a metallized envelope to block the signal. The physical embodiment of the token also means that after the pandemic is taken under control, the destruction of tokens will also mean the destruction of data on them, unlike the application. Indeed, often when you uninstall the software, the icon just disappears from the screen, and some data files remain in the bowels of the device.
In other words, the physical implementation of the token means that a serious discussion of privacy can run parallel to the collection of data about social contacts. Even if today you are not sure about the merits of TraceTogether, wearing a token allows you to postpone the final decision whether to trust the authorities until you are asked to turn in the token for data extraction.
If it turns out that the authorities are using BLE receivers on the island, or a strange token of a suspicious device is found, then the government risks losing not only people's trust, but also access to the full contact tracing graph, because people begin to get rid of tokens en masse. It restores a certain balance of power where the government can and will be held accountable for its social contract, even if we all collect contact tracing data.
Next steps
When I was asked to do an independent review of the TraceTogether token, I replied that I would not hide anything - and to my surprise, they still invited me to a meeting.
This article describes the context within which I will be evaluating the token. Exposure notification capabilities are not sufficient to isolate asymptomatic carriers of the virus, and a complete contact tracing graph can help solve this problem.
The good news is that the hardware token represents a safer opportunity to continue the privacy discussion while improving data collection. Ultimately, the deployment of the hardware token system depends on the citizens themselves, and therefore the authorities must maintain or win our trust in order to safeguard the national interest during the pandemic.