
In the late Soviet Union, the so-called theory of inventive problem solving (TRIZ) gained great popularity, which, among other things, makes it possible to find methods for improving technical systems. In it, Heinrich Altshuller introduced the concept of "an ideal technical system, in which the costs of obtaining a useful effect are equal to zero." In other words, the solution is the better, the simpler it is, and the ideal solution is when there is no system, and its functions are performed. This old forgotten method allows you to take a fresh look at the future development of new IT industries. In many areas of IT, we will meet with the "idealization" of systems and processes. This “idealization” is associated with the withering away of redundant procedures and unjustified costs in maintaining the target functions of information systems.
Personal data problem
Not all companies are faced with information security tools such as DLP or SIEM systems, but almost everyone knows what 152-FZ and personal data protection (PD) are. A huge number of specialists work in the field of bringing to the regulations 152-FZ. Most of this work is bureaucratic and useless and consists only in writing the necessary set of documents for Roskomnadzor. In reality, the number of personal data leakage incidents only grows every year. Let's try to figure out what the "ideal" legislation on the protection of personal data should look like. As it is already clear from the logic of reasoning above, the “ideal” legislation on personal data is one that does not exist, but at the same time no one steals personal data and does not use it for other purposes. In other words,the ideal set of procedures for working with personal information of users implies the impossibility of deviating from them, even in the absence of a law that obliges them to protect. Technically, it should be impossible to copy and send data to another resource that is not intended for their processing, it is impossible to get access to personal data for those who should not have it. It looks like a utopian fairy tale, but let's dive a little deeper into this problem. Paradoxically, we already have the entire technology stack for building such an ideal future; it remains only to understand why we do not yet live in this beautiful reality.Technically, it should be impossible to copy and send data to another resource that is not intended for their processing, it is impossible to get access to personal data for those who should not have it. It looks like a utopian fairy tale, but let's dive a little deeper into this problem. Paradoxically, we already have the entire technology stack for building such an ideal future; it remains only to understand why we do not yet live in this beautiful reality.Technically, it should be impossible to copy and send data to another resource that is not intended for their processing, it is impossible to get access to personal data for those who should not have it. It looks like a utopian fairy tale, but let's dive a little deeper into this problem. Paradoxically, we already have the entire technology stack for building such an ideal future; it remains only to understand why we do not yet live in this beautiful reality.why are we not yet living in this beautiful reality.why are we not yet living in this beautiful reality.
Ideal model for working with personal data
Below I will try to describe what an ideal model of working with PD might look like from my point of view. Only the owner of personal data can be the owner and manager of personal data - that is, in the ideal model, only the owner of the PD has access to them and can permit any operations with them. It is technically impossible to access or change data without the consent of the owner. The idea of storing personal data and not showing it to anyone is faced with the need to use it by various companies and services. We can conditionally divide them into the following groups:
- State organizations (Pension Fund, FTS, FSS, etc.).
- Power departments.
- Companies-employers (here - institutes for students, schools and kindergartens for pupils, etc.).
- Banks.
- Companies selling goods.
- Service Providers.
I hope I didn't miss anyone. Let us analyze for each separate group why they need to use personal data and whether it is possible (again in the “ideal world”) to refuse it.
- , . ? , , — , , , . , . , , - . , - «» ( ). . , , , 3 16 . : , , , .
- . , . , .
- . , , ., - , . — ( ).
- : , . , - . . . , - . . , .
- , : , , - - . , - .
- , : , , , (, ), «» - .
Let's consider the scheme according to which all the subjects presented above can work.
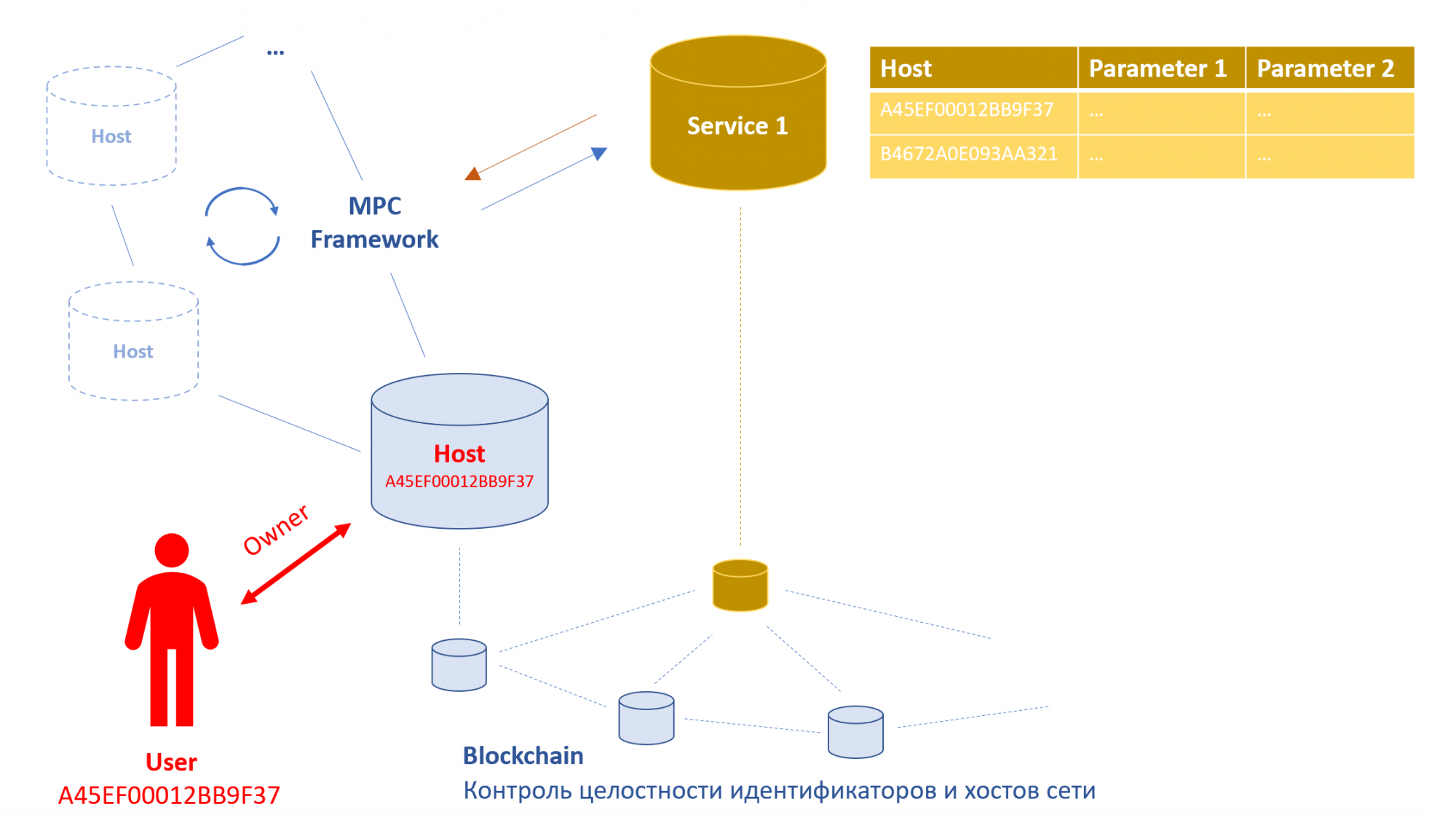
Of course, this scheme does not claim to be the only correct one. Here we will rather try to describe the possible structure of an “ideal” system for working with PD, proving that it exists in principle (at least in theory).
The entire system for working with personal data consists of entities: hosts (PD storage) and services (who, for some reason, needs access to PD). A blockchain network can be used to confirm the integrity of the entire structure. It will establish the reliability of services (confirm that they are exactly who they say they are). Here you can talk about the implementation of the Decentralized Public Key Infrastructure technology... At the same time, the blockchain network guarantees the integrity of host data and transactional chains for changing this data.
Let's say we have a user named User . The system assigns it a unique identifier A45EF00012BB9F37 . In order for this identifier not to turn into the user's PD by itself, it would be correct to make it dynamic. For such dynamism, you can use techniques similar to those developed in the Moving Target Defense methodology for, for example, randomizing the attributes of an enterprise LAN . User A45EF00012BB9F37is the owner of the host of the same name. This host is the only place - the storage of the user's PD. No other members store his personal data. A person does not sign any papers on consent to store and process their PD somewhere else.
It should be noted that the user owns his host very conditionally. He, of course, has the status of the owner, but he cannot arbitrarily delete and modify the host data. Also, he cannot deny some requests to the host, for example, from government agencies. At the same time, he can see the entire history of requests and requests to his data and monitor its correctness, as well as approve or reject requests to the host from commercial companies. For example, if he ordered pizza in an online store, then the host may receive a request to send the address in an SMS message to the courier. If the pension fund makes payments to citizens with children from 3 to 16 years old, then the corresponding request will come to the host from the MPC framework. The user sees it, but can no longer reject it at will.
The next important element of the "ideal" system is the very framework MPC ( multi-party-computation). It is required to request data from hosts. The system will be ideal only when it will not divulge any information unnecessarily. If some analytical agency wanted to know the average age of Moscow residents, then it does not need to request information about the age and address of each user in the system. The MPC framework can extract the final value without receiving any PD from the hosts. Also, in order to avoid processing "unnecessary" PDs, homomorphic cryptography can be used for all requests the recipient of which is the user himself. For example, the traffic police can completely form a protocol on an administrative offense without even knowing to whom it subscribes, and the user himself decrypts the messages and sees the document.
Without detailed architectural detailing of the above diagram, many flaws can be found in it. For example, it may seem that storing everything in a PD in one place is extremely dangerous from the point of view of reliability: something may break and all data will be lost. However, it is possible to reproduce a distributed cluster of host storage, the reliability of which in terms of probable data loss will be even an order of magnitude higher compared to how the data is stored now. Similarly, there are decisions on the issue of arbitration of rights in the system, so that there is no superadmin in it, and as a result, no critical vulnerability. At least a few more articles can be devoted to this, but they will lead us away from the main idea - the feasibility of an ideal scheme for working with PD.
Moving towards a perfect world
Despite the fact that the current technological stack allows us to almost completely eliminate the processing of PD by third parties, such a transition requires a large amount of organizational changes. The main obstacle to these changes is the value of the accumulated arrays of personal data. Today, PD arrays are of significant value for both commercial and government structures.
For commercial companies, this is a direct marketing channel, as well as an additional resource for generating cash flow. There are different approaches to assessing the cost of PD - for example, based on the analysis of the profit structure of operators... In this logic, the personal data of an average citizen of the Russian Federation can cost 926 US dollars, and a citizen of the United States - 6105 the same dollars per year. This does not mean that you can take your personal data and sell it to someone for $ 926: this figure is taken from the total income of all commercial companies for one calendar year, taking into account the proceeds received from the use of the personal data of a particular citizen. Of course, the loss of personal data will lead the company to financial costs. However, if all companies are “simultaneously” deprived of personal data, then the average statistical loss of revenue will not occur, since commercial structures are more likely to share user channels with each other with their finite capacity. Here we are talking aboutthat the market is in equilibrium and it is unlikely that someone will be the first to refuse to accumulate PD on their own initiative.
For government agencies, unhindered access to personal information is an additional resource for increasing powers. In the described "ideal" scheme, any request for data from the authorities will be logged and recorded in the system. Any unreasonable request cannot go unnoticed. If you did not go to the polls, and the corresponding GAS for some reason made a request for the formation of a ballot, then you definitely understand that something was wrong. Any use of your data in government systems becomes as transparent as possible for you and as opaque as possible for others. This can only be afforded by a crystal-clear and confident government.
However, the current balance between the desire of key “stakeholders” to retain access to personal data and the ineffectiveness of existing mechanisms for working with them does not mean that there will be no movement towards rejection of personal data. Such initiatives already exist, but the movement towards an "ideal world" is likely to last longer than we would like.
Several possible scenarios for such a transition can be considered:
- . . , , . . — , , .
- . . , «» . , , (IDaaS), . , - . IDaaS-, , , - IDaaS. , , , . , .
- . , , « » . , 20 . «» . , «» AuthaaS (Authentication as a Service). - . .
The destruction of personal data operators will inevitably lead to changes in the IT market. Of course, this will affect the companies that provide services for the protection of personal data, but here we will focus on non-obvious conclusions. The greatest changes can be expected in the following directions.
Decline in the role of corporations.In literature and cinema, it is customary to consider apocalyptic-technogenic scenarios of the future, when a person is completely controlled by the state, as, for example, in the work of George Orwell "1984". This idea is widely exploited, in connection with which the idea of the future total digital control is rooted in the minds of citizens - so that any ideas about the digitalization of our life are perceived negatively. However, I would consider such an apocalyptic scenario more like an unnatural path of technological development. The natural path (described in this article) implies an increase in control on the part of citizens and a decrease in the corresponding resource on the part of the state and large corporations. Paradoxical as it may seem, it is the digital illiteracy of the population that slows down the path of natural development and helps the implementation of scenarios of total digital control.
Increased market dynamics. Any marketer knows that the cost of retaining an existing customer is several times lower than the cost of attracting a new one. There are CRR (customer retention rate - a coefficient showing the ability of a business to retain existing customers) and CAC (customer acquisition cost). If the company does not accumulate the user's PD, is unable to send him spam, etc., this will lead to an inevitable decrease in CRR. However, it will also cause a decrease in CAC, which is good for small and medium-sized businesses: with a greater market dynamics, they have an increased chance of getting customers. Also, large companies in this scenario lose the added value that could have been generated by accumulating PD, and thereby further reduce the entry price for small businesses.
Personal data monetization. The scheme of interaction between market participants, in which only a user can store and process his PD, increases his importance as a participant in information exchange. If earlier it was possible to get personal data from the user, write it down to yourself, and then also impose advertising and calls with surveys, now this will become impossible. We will have huge arrays of user "bigdata", but its owners will be the users themselves, without whose consent it will become impossible to work with it. As a result, a person will be able to "sell" the right to send certain requests to his host through the MPC framework, and the cost of these requests can be ranked depending on the format of the information.
Unified access to big data... The problem described above generates another change in the market. There will be no opportunity to increase their competitiveness by accumulating "bigdata". Now large retail chains, analyzing transactions, can easily find out that milk X is 80 rubles. in Khovrino it is sold 47% better than milk Y at 110 rubles. A small grocery store cannot know about this. In the future, their analytical skills will level out.
Improving the quality of services . This is a completely non-obvious conclusion from the disappearance of PD operators, but the more non-market mechanisms of competition are eliminated, the more market instruments to change the very CRR and CAC must be used. And the key factor here is the quality of services.
Increasing the share of outsourcing in information security... Today, in small companies, the information security department is one person, and up to 50% of his working time (and sometimes more) this person spends on the preparation of sets of documents for the protection of personal data and on the implementation of regulations for working with PD in the company. If the need for this work disappears, then the dedicated information security specialist will be redundant. This will lead to more and more companies leaving for outsourcing of information security services.
conclusions
Perhaps 20 years from now, we will look back with sympathy, realizing how many useless personal data protection procedures we had in 2020. By themselves, they do not create useful added value, "nightmare" small businesses and only increase the volume of unauthorized processing and trade of personal data. The market for personal data protection services is huge today and continues to grow. According to the fulfillment of the requirements of the GDPR, it is estimated at $ 2.6 billion by 2023 . It was not possible to find such a market assessment for compliance with 152-FZ, but I am sure that the figure will also be impressive. And this market will disappear in the next 10 years or more, since it unnecessarily increases the costs of companies and does not provide real protection.
Already now there are many developments that allow to reduce the amount of work with PD unnecessarily. This can also include the protocol for the exchange of personal data, which was announced just the other day by NPK Kryptonit . However, despite the already existing technical ability to liquidate the vast majority of PD operators, we are faced with organizational difficulties and resistance from key market “stakeholders”.
If we talk about the scenarios of possible transformation, then I see the variant of "inorganic growth" discussed above as the most probable. It is already possible to observe how many large market players are trying to accumulate IDaaS services. Quite successful in this regard, for example, China Mobile, which provides identification tokens to more than a thousand applications, eliminating the need to collect registration information and store personal data. The integration of such initiatives with state information systems may in the near future create a model of working with PD that is close to the “ideal” one.