
Good afternoon, colleagues! Today we are starting a new series of articles dedicated to information security solutions from Group-IB. The company has been working in the information security market for over 17 years and during this time has acquired very significant competencies, carrying out projects not only in Russia and the CIS countries, but also in the international market. The area of protecting infrastructure from complex targeted attacks closes the Group-IB Threat Detection System (TDS) complex, which consists of several different modules. The solution specializes in protecting corporate and industrial networks and is mainly aimed specifically at countering modern attacks. In this article, we will consider the architecture and functionality of the entire complex.
Group-IB Threat Detection System (TDS) consists of several modules:
- TDS Sensor;
- TDS Decryptor;
- TDS Sensor Industrial;
- TDS Polygon;
- TDS Huntpoint;
- TDS Huntbox.
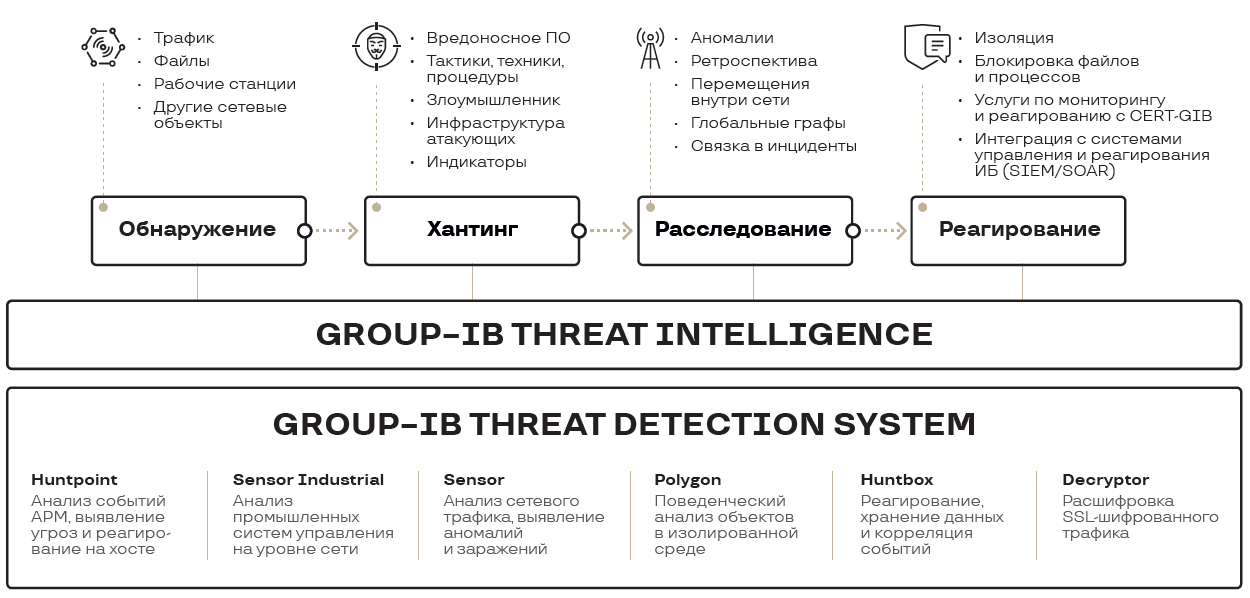
Each module performs specific functions, consider the main tasks of the Threat Detection System.
Solution architecture

The system is designed to improve the information security of an enterprise: protection of corporate and technological segments. The technologies used by the TDS system make it possible to effectively detect threats at various phases of the MITER ATT & CK matrix :
- Zero-day threats;
- Exploits, trojans, backdoors, malicious scripts for desktop, server and mobile platforms;
- Hidden data transmission channels;
- Attacks using legitimate tools (living-off-the-land).
It is important to note that a strong advantage of the Group-IB TDS complex is an integrated approach to network protection: from a single control center it is possible to manage all modules that are installed both in the corporate segment and in the technological segment. Solutions of this class are well suited for protecting enterprises and organizations where ICS are used. All the certificates required in Russia for compliance with Federal Law 187 have been received by the product.
But this does not mean that the system is tailored only for industrial traffic. Initially, the system was developed for traffic inspection in corporate networks - mail, file storages, user traffic flows. And all this is not on the perimeter, but inside the network , which allows you to detect and prevent especially critical information security incidents:
- the fact that the user downloaded an infected file;
- the spread of malware infection on user PCs in the domain;
- attempts to exploit vulnerabilities by an intruder inside the network;
- horizontal movement of intruders within the network.
The perimeter devices are highly unlikely to detect the incidents described above if they have already somehow entered the network. However, as elsewhere, it all depends on the setting. The Group-IB TDS modules must be in the right place and correctly configured, therefore, below we will give a brief description of the complex's features and its functionality.
TDS Sensor

TDS Sensor is a module for deep analysis of network traffic and detection of threats at the network level, as well as integration with various subsystems. Sensor allows you to identify:
- Interaction of infected devices with cybercriminals' command centers;
- ;
- .
The internal database of signatures and ML engines was developed by Group-IB. Attack signatures are classified and correlated by Group-IB cyber intelligence specialists and CERT analysts, and ML classifiers are developed in close cooperation with forensic experts and analysts of all major services, after which they are updated to TDS, this allows timely response to modern targeted attacks. It also detects anomalies to identify hidden tunnels in high-level protocols and the possible propagation of threats in the internal infrastructure and between segments. Integration of the product with third-party systems is possible: with mail, ICAP, with file storages, SIEM, etc.
The device operates in mirroring mode , so the solution cannot influence the processes involved in legitimate traffic.
TDS Decryptor
The question logically arises: since the TDS Sensor operates on mirrored traffic, then how to work with https connections, without which it is impossible to inspect the state of the infrastructure security? In this case, it will be necessary to integrate the TDS Decryptor module into the infrastructure - a software and hardware complex designed to open and analyze the contents of encrypted sessions, which allows to increase the visibility and level of traffic control of the protected infrastructure, as well as the quality of detection of targeted attacks. TDS Decryptor works in discontinuity, replaces certificates, and sends the decrypted session to the TDS Sensor.
TDS Sensor Industrial
To detect attacks in the technological segment of the enterprise, Group-IB has recently developed the TDS Sensor Industrial module. By analyzing data packets of technological protocols with its own behavioral rules, TDS Sensor Industrial allows detecting the transfer of illegitimate control commands between the levels of the APCS, detecting the use of service commands of the APCS for the purpose of flashing the PLC, replacing the control program, stopping technological processes, and other violations.
The module supports both open protocols - CIP, DNP3, IEC 60870-5-104, IEC 61850-MMS, Modbus TCP, OPC-DA, OPC-UA, MQT, and some proprietary - Siemens, Schneider Electric, Rockwell Automation, Emerson. If the required protocol is not on the compatibility list, Group-IB experts are ready to add it within a few weeks.
TDS Sensor Industrial does not affect technological processes in any way, everything works in mirror mode. A good addition to the system will be the use of the TDS Huntpoint module on the APM of operators and engineers, which will record actions on critical machines inside.
TDS Polygon
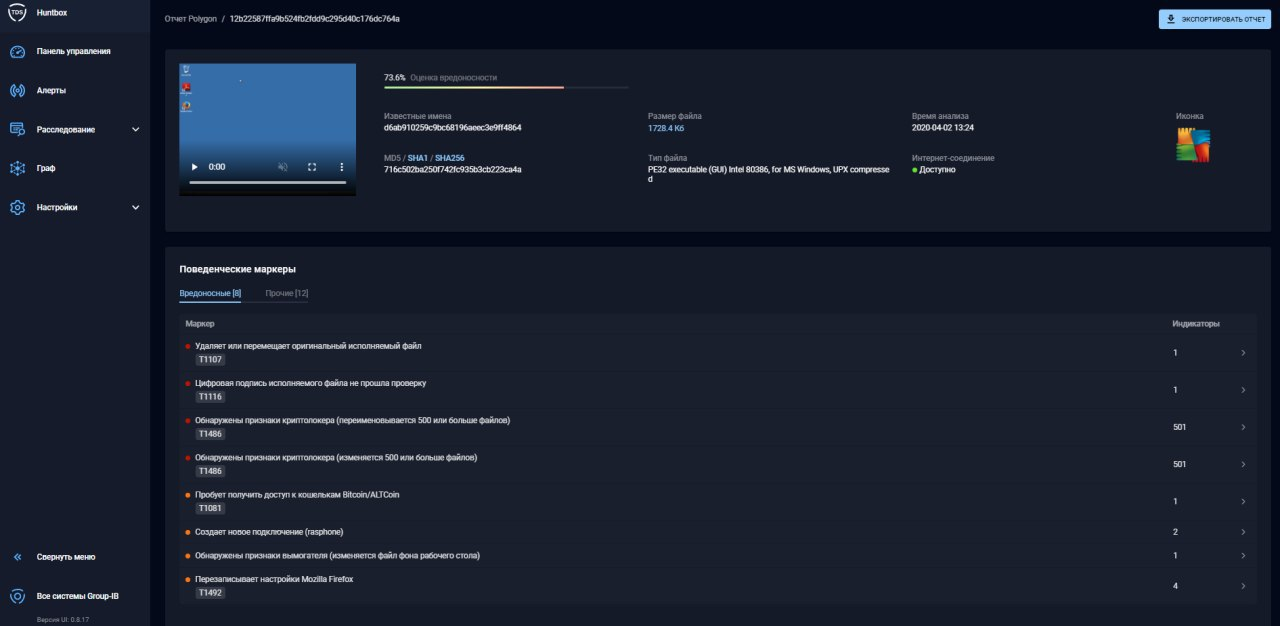
Using a single TDS Sensor module may not be enough to detect attacks, you also need to scan files that are distributed over the network. This functionality is provided by TDS Polygon. This module is intended for behavioral analysis of suspicious objects in an isolated virtual environment. TDS Sensor extracts files from network traffic on the SPAN port or takes them from file storages and sends them to TDS Polygon for analysis. You can also configure the integration of the mail server and TDS Sensor, as a result of which all messages with attachments and links will be scanned by the product.
Files are scanned on several virtual machines - Windows XP, Windows 7, Windows 10 in two bit versions - x32 / x64, as well as using two system languages - Russian / English. Moreover, the system itself determines the need to use a particular bit or version in case the malicious signs of an object were underestimated or not detected. The system is equipped with virtualization hiding functionality and detects attempts to bypass protection means with a malicious file. For example, if malware creates a pending task, TDS Polygon will "speed up" the system time to detonate the malware. Or if the attackers sent an email with an empty link, TDS Polygon will “follow” the file until it finds it there (this type of attack is quite common). More complex examples of HPO detonation are also possible (reactions to OS reboot,closing auxiliary software, etc.). The module also actively uses machine learning and the previously described signatures to detect malicious activity.
In addition, a convenient service is connecting the solution to the Group-IB security center - CERT-GIB, whose specialists monitor and analyze events detected by TDS Sensor and TDS Polygon in real time. CERT-GIB experts immediately notify the organization's specialists about critical threats by email and phone, as well as provide recommendations for their elimination and accompany users until they fully escalate. Support works 24 * 7, 365 days a year.
TDS Huntpoint

Malware does not always spread across the entire network; sometimes it is enough to infect only one desired workstation. Or, the malware completely bypassed the network and entered the device using removable media. Therefore, there may be situations when the TDS Sensor does not detect any events. In this case, Group-IB offers the use of the TDS Huntpoint agent solution.
TDS Huntpoint is a module of the Group-IB Threat Detection System (TDS) product that allows you to record the history of user behavior , track processes occurring on the system to detect malicious activity, and collect additional contextual information to detect malicious behavior on the host.
Like TDS Sensor, TDS Huntpoint will send files for analysis to TDS Polygon. And in the event of malware infiltrating a PC, TDS Huntpoint, on command from the TDS command center, isolates that host from the network. As part of this module, the company implements such areas as computer forensics, response to hosts and threat hunting.
TDS Huntbox
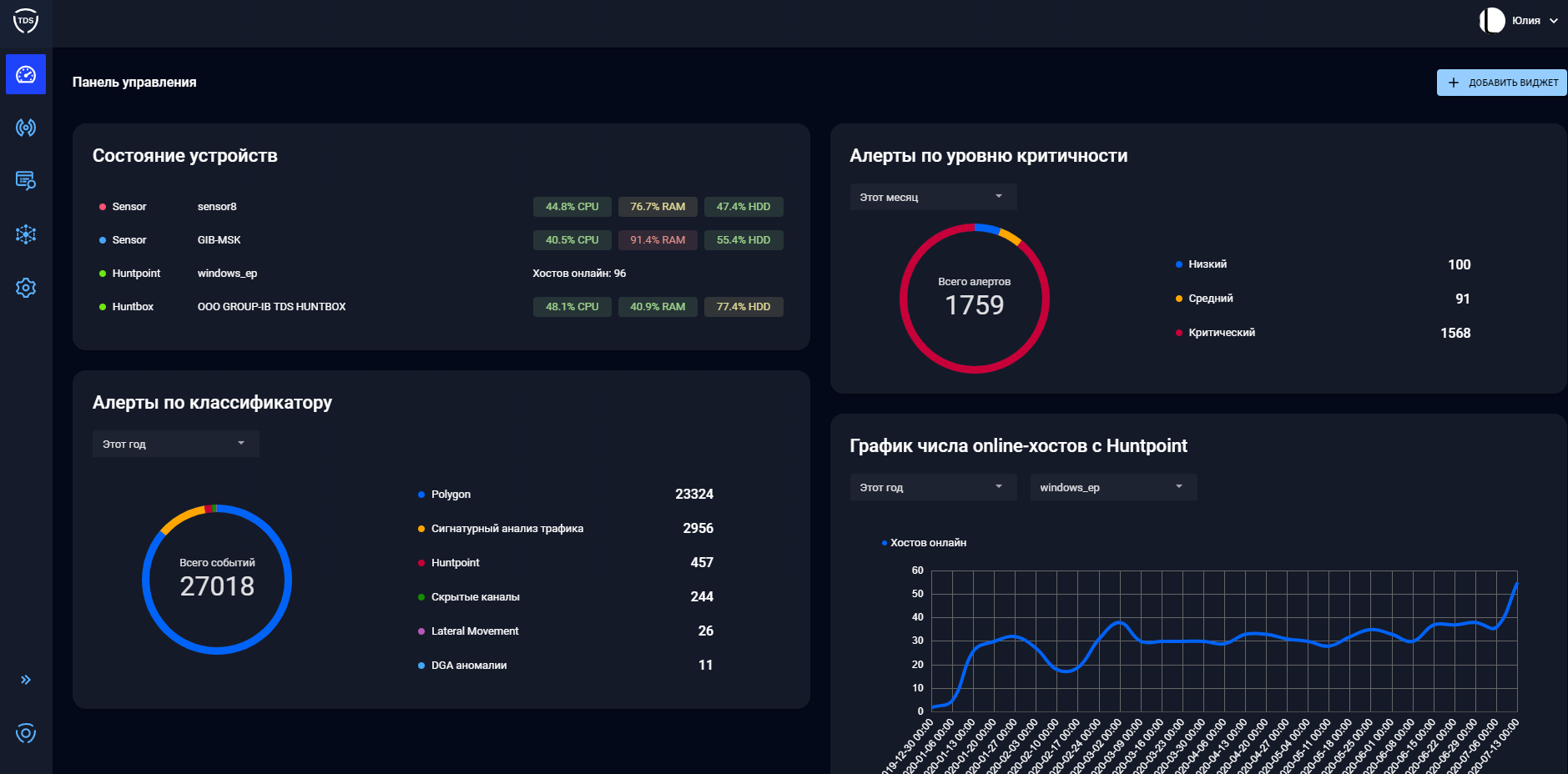
TDS Huntbox is a control center , monitoring, storage of events and updates, installed within the customer's infrastructure. TDS Huntbox integrates with other components of the TDS complex (Sensor, Polygon, Huntpoint) and significantly expands the functionality of the solution through new features.
System features:
- Detection Infrastructure Management;
- Orchestration and management of all TDS components from a single interface;
- Big data analysis, identification of new tools and infrastructure of attackers;
- Storage of logs and analytical information on incidents;
- Visualization of an incident at an early stage of an attack;
- Building a network graph;
- Remote response at end stations (TDS Huntpoint);
- Hunt for threats.
For an information security specialist who will work with this product, this platform is the main one, since all identified information security incidents are analyzed on it.
Typical operation of all Group-IB modules

To summarize, the entire complex operates on mirrored traffic, except for integrations with mail or file storage. Active blocking of traffic passage can be organized by configuring Sensor as an ICAP server or by putting it in a gap for mail traffic. TDS Decryptor is required to decrypt https traffic. The use of the TDS Huntpoint is recommended for monitoring critical user machines. Based on this information, it becomes clear that the main work of an information security specialist should go on monitoring events and alerts, and this work must take place constantly. In the event of an event, a specialist, receiving information from the event, must check the endpoint and take measures to counter the threat. This means that there must be employees who will actively monitor current events and take seriously the issue of using the system.
For its part, Group-IB is doing a lot of work to minimize False Positive events, thereby facilitating the work of an engineer and leaving only those events that pose a threat and which need to be responded to.
Conclusion
Group-IB Threat Detection System is a serious solution for protecting the internal corporate network, and should be of particular interest to those organizations that need to protect the industrial network. It is also worth mentioning once again that the solution belongs to the anti-APT class, which means that this functionality can be a significant addition to the existing protection system for any large organization that needs to constantly monitor the state of the internal infrastructure.
In the future, we plan to publish detailed reviews for each TDS module separately, with various test examples. So stay tuned ( Telegram , Facebook , VK , TS Solution Blog ), Yandex.Den .