
Welcome to a new series of articles dedicated to protecting personal workplaces using the Check Point SandBlast Agent solution and the new cloud-based management system - SandBlast Agent Management Platform . We reviewed the SandBlast Agent in articles on malware analysis and describing the features of the new version of E83.10 , and we have long promised to publish a full course of articles on deploying and administering agents. And the Management Platform cloud agent management system presented by Check Point within the Infinity Portal is best suited for this - it will take only a few minutes from the moment of registering on the portal to starting the agent scan of the workstation and detecting malicious activity.
Why SandBlast Agent?
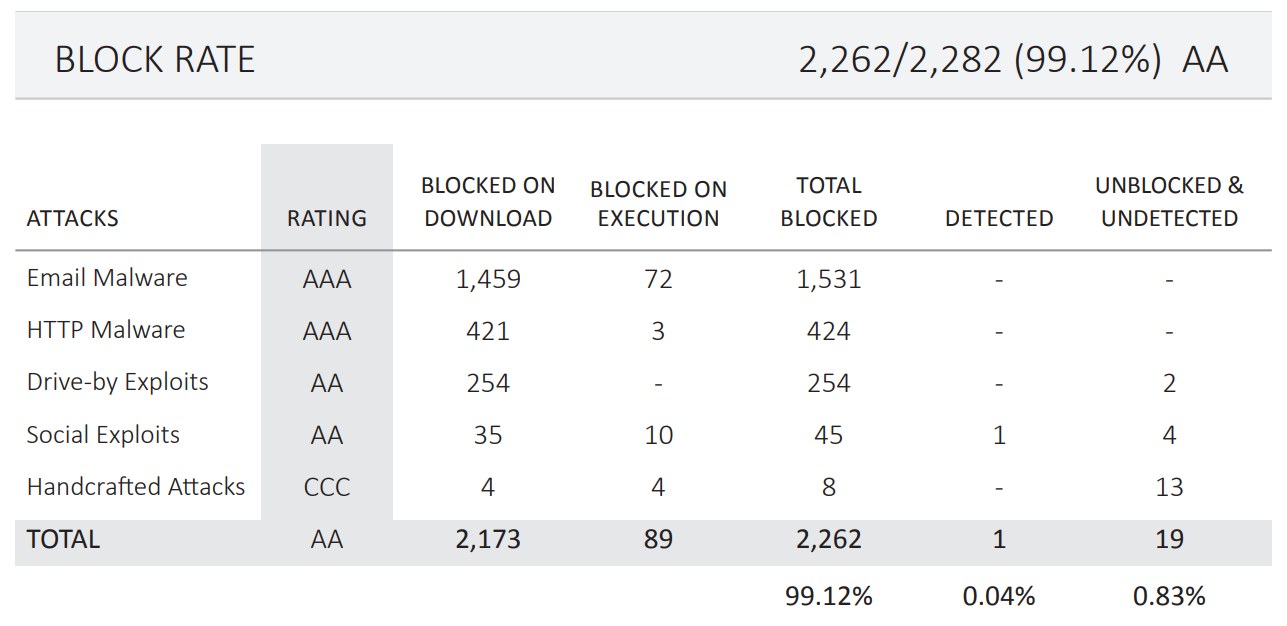
According to the latest 2020 NSS Labs Advanced Endpoint Protection (AEP) Market Test, Check Point SandBlast Agent was rated AA and Recommended with the following test results:
- Blocking rate in WEB-traffic - 100%;
- Email blocking rate - 100%;
- Offline threat blocking rate - 100%;
- The blocking rate of bypass attempts is 100%;
- The overall blocking rate is 99.12%;
- The False-positive value is 0.8%.
SandBlast Agent provides a high level of security for user workstations through the collaboration of several components, called "blades" in Check Point terminology. A short description of the blades used in SandBlast Agent:
- Threat Emulation — «», , ;
- Threat Extraction — « », ;
- Anti-Exploit — (Microsoft Office, Adobe PDF Reader, .) ;
- Anti-Bot — -, , «» ;
- Zero-Phishing — , ;
- Behavioral Guard — , , ;
- Anti-Ransomware — , , Snapshot-;
- Forensics — , , .

In addition to the listed capabilities, SandBlast Agent allows for full disk encryption, as well as encryption of removable media and protection of computer ports, has a built-in VPN client, signature and heuristic anti-malware modules. The capabilities of all SandBlast Agent components will be discussed in more detail in subsequent articles, and now it's time to get acquainted with the actively developing platform - Check Point Infinity.
Check Point Infinity: Gen 5 Threat Protection
Since 2017, Check Point has been developing and promoting a single consolidated security architecture Check Point Infinity , which allows you to successfully protect all components of modern IT infrastructure: network and cloud infrastructure, workstations, mobile devices. The main idea is the ability to manage protection tools of various categories from a single browser-based management console.

Currently, the Check Point Infinity architecture allows you to administer cloud protection solutions - CloudGuard SaaS, network security - CloudGuard Connect, Smart-1 Cloud, Infinity SOC, as well as protecting user devices using SandBlast Agent Management Platform, SandBlast Agent Cloud Management and SandBlast Web Dashboard.
This series of articles will be devoted to the SandBlast Agent Management Platform solution (so far Beta version), which allows you to deploy a cloud management server in a matter of minutes, configure a security policy and distribute agents to user computers.
Infinity Portal & SandBlast Agent Management Platform Getting Started
The process of deploying SandBlast Agent using the Management Platform consists of 5 stages:
- Registration on the Check Point Infinity Portal;
- Registration of the SandBlast Agent Management Platform application;
- Creation of a new Endpoint Management Service for agent management;
- Creating and configuring a policy for agents;
- Deploying agents to users' computers.
This article describes the first three stages, and in subsequent publications we will take a closer look at the remaining two, including examining the interface of the management platform, distributing agents to client computers, configuring policies, and testing the agent's ability to cope with the most popular security threats.
1. Registration on the Infinity Portal
First of all, you need to go to the Infinity Portal website and fill out the registration form, indicating the name of the company, contact information and agree to the terms of use of the service and the portal's privacy policy, as well as go through the reCAPTCHA. It is worth noting that during registration, you can select a country in the data center of which the data collected by the portal will be stored in accordance with the terms of use of the service and the privacy policy. There are only two options: Ireland and the USA. To do this, check the box "Use specific data residency region" and select the country.

Upon successful registration on the portal, a letter will be sent to the mail you indicated confirming that you have access to the Infinity Portal and offering to log in to the portal. It is worth noting that the first time you enter the portal, you may need to select the password reset option for further successful authentication.

2. Registering the SandBlast Agent Management Platform application
After authenticating on the portal and clicking the "Menu" icon (step 1 in the image below), you will be prompted to register an application from the list of available categories: Cloud Protection, Network Protection and Endpoint Protection. Each application deserves a separate course of introductory articles, so we will not dwell on them in more detail and select the SandBlast Agent Management Platform application in the Endpoint Protection category (step 2 in the image below).

Having selected the application, then you must agree with the terms of use of the service and the portal's privacy policy, and after clicking the "TRY NOW" button, access to the interface for creating Endpoint Management services opens.

3. Creating a new Endpoint Management Service
The last step is to create a new service for Endpoint Management, which is a web interface for managing agents. The process, as before, is extremely simple: select the "New Endpoint Management Service" option (as shown in the figure below), fill in the data for your new service (ID, hosting region and password) and press the "CREATE" button.


After completing the process of creating a service, you will receive a letter with parameters that you can use to connect to the cloud management server using the standard Check Point console for agent administration - SmartEndpoint version R80.40. We will not cover management using the standard console, since this series of articles is aimed at demonstrating the capabilities of the SandBlast cloud-based agent management system.

At this point, the process of registering a cloud service to manage the SandBlast Agent personal computer security tool can be considered successfully completed. Before us appears the web interface of the agent administration platform, which will be discussed in detail in our next article from the series "Check Point SandBlast Agent Management Platform".
Conclusion
It's time to take stock of the work done: we have successfully registered on the Infinity Portal, registered the SandBlast Agent Management Platform application on the portal and created a new cloud-based management service, Endpoint Management Service.
In our next article in the series, we will take a closer look at the agent management interface - not a single tab will be left unattended, which will allow us to create a security policy and monitor the state of user machines using logs and reports without any problems in the future.
A large selection of materials on Check Point from TS Solution . In order not to miss the following publications on the SandBlast Agent Management Platform - follow the updates on our social networks ( Telegram , Facebook, VK , TS Solution Blog , Yandex Zen ).