
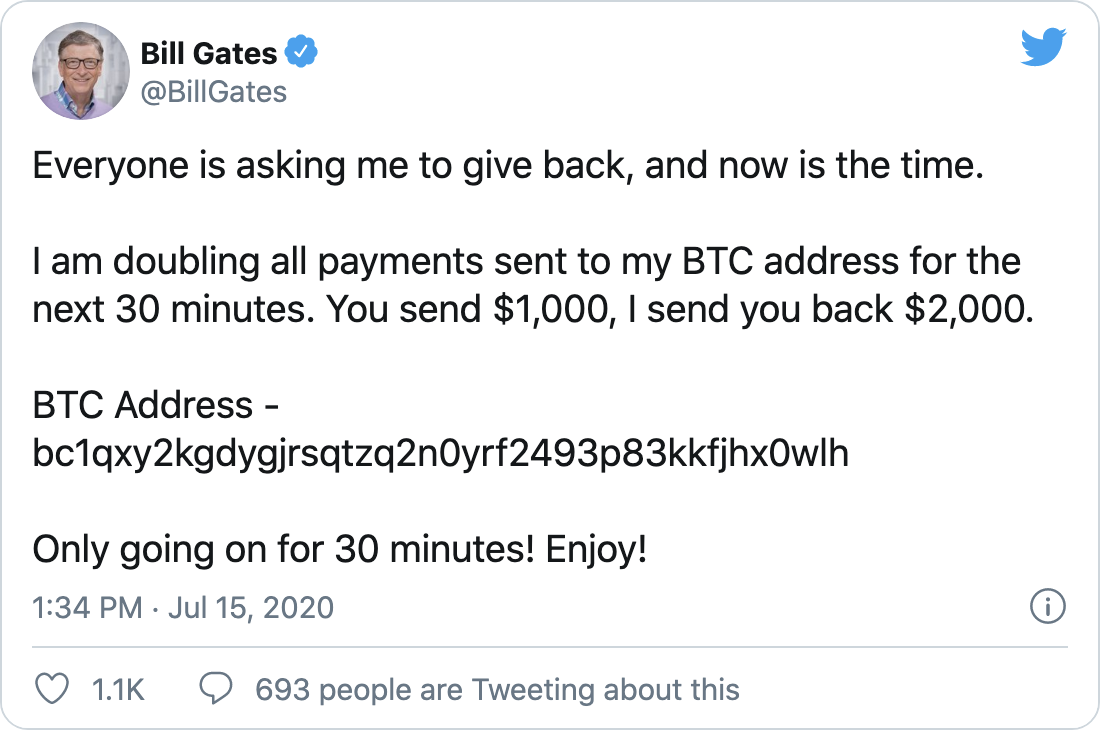
The Twitter hack occurred in the afternoon (late evening Moscow time) on Wednesday 15 June. Several popular accounts began to distribute to cryptocurrencies at once - an offer to send money to a bitcoin wallet with a promise to return double the amount. Twitter users have been familiar with this type of scam for a couple of years; fake accounts were usually used for distribution, very similar to the microblogging of the same Elon Musk. Only this time, the messages were sent from the accounts of real people.
Self-Study Links :
- Review article at Threatpost .
- Official Post in Twitter blog.
- An article by Brian Krebs that reproduces the sequence of events before the accounts were hacked.
- Motherboard Twitter.
- The New York Times .
- .
A few hours before the hacking of popular accounts, the same people stole the account with the short name @ 6 . It belonged to hacker Adrian Lamo, who passed away in 2018. Since then, the account was managed by his friend, who noticed the theft of the account thanks to a message to the linked phone number. In general, the owner of @ 6 disabled the option to reset the password via SMS to avoid the common method of theft by replacing the SIM card. But the attackers somehow managed to replace the email address associated with the account and disable two-factor authentication. They forgot to untie the phone or did not have time.
After a while, a cryptoscam was sent from the accounts. Almost all victims had a verified account - these are marked with a blue checkmark, indicating that the identity of the owner has been verified. A temporary solution by the Twitter administration was to block posting from verified accounts. In addition to Bill Gates, Jeff Bezos and others, attackers have hacked accounts of companies and organizations related to cryptocurrencies, including, for example,Bitcoin...
The first debriefing of the incident appeared on Twitter on Thursday July 16, and on Saturday the company posted a more detailed description of the hack. More precisely, the blog post avoids specific wording, probably in order not to reveal the inner workings of the social network. They reported the following: the attackers misled one or more employees of the company and used their accounts to access internal systems. They also managed to bypass two-factor authentication. As a result, 130 accounts were hit, and 45 were compromised. In eight cases, the attackers performed a full export of the data, most likely obtaining a complete archive of not only public tweets, but also private messages.
This is where the facts end and the speculation begins, backed up only by anonymous sources. According to Brian Krebs, representatives of the criminal community specializing in stealing accounts by reissuing SIM cards are responsible for the hacking. Among them, the so-called OG (original gang) accounts, ancient Twitter accounts (and not only) with short names are of particular value - so they were among the first to hack @ 6. How did they get access to the admin area? There are two versions: psychological manipulation by a company employee or illegal access to the corporate Twitter chat in Slack, in the logs of which it was possible to dig up the keys. Officially, Twitter does not comment on these versions.
The scandal turned out to be notable, with serious consequences and the hope for some improvement in the security of the social network. After all, why do employees of a company have unlimited control over any account? The consequences of the hack would be much more serious if the attackers did not lure the cryptocurrency, but published political messages or something that could affect the value of the shares of a public company. Twitter and other social networks have become a critical infrastructure: through them, users receive messages about the impending storm and interact with politicians and corporations. They are too important to be so vulnerable. Compared to the worst-case scenarios, nothing serious happened: four hours of shame for Twitter and $ 180,000 in a crypto wallet for the hackers.
What Else Happened: Microsoft
Research and Bulletin on Serious Issue in Windows DNS Server. Affected server OS versions starting with Windows Server 2003. The vulnerability is classified as wormable - it can be used for sequential infection of servers and, in the worst case, gain domain administrator rights on the corporate network.
Fixed major vulnerabilities in Adobe Creative Cloud client and Media Encoder. A ten-point vulnerability in SAP NetWeaver, which affects 40 thousand customers, allows you to gain full control over the enterprise ERP system.
Journalists of The Register publishedhis version of the recent incident with Samsung Blu-ray players, which at some point went into a cyclic reboot. The reason was a malformed XML file that got to devices as part of a firmware update. The only solution to the problem is to take the device to a service.
And finally, about the leaks. The darkweb sells 142 million customer records for MGM Grand. Also, a database (several terabytes) of logs of seven VPN providers from Hong Kong was found in the public domain . They all share a common guideline, and they all claimed not to store user logs.