Earlier articles covered several broad topics about the Cisco StealthWatch monitoring solution . Let me remind you that StealthWatch is a solution for monitoring network traffic for security incidents and the legitimacy of network interaction. StealthWatch is based on collecting NetFlow and IPFIX from routers, switches and other network devices.
Links to all articles in the cycle:
1) StealthWatch: basic concepts and minimum requirements. Part 1
2) StealthWatch: deployment and configuration. Part 2
3) StealthWatch: analysis and investigation of incidents. Part 3
4) StealthWatch: Integration with Cisco ISE. Part 4
5)Stealthwatch Cloud. Fast, convenient and efficient solution for cloud and enterprise infrastructures. Part 5
Monitoring, in particular Cisco StealthWatch, is primarily a threat and attack detection solution. All monitoring solutions do not imply threat prevention, but it is often required. StealthWatch has out of the box integration with Cisco ISE (Identity Services Engine). The integration consists in the fact that StealthWatch detects a security incident, and Cisco ISE quarantines the host until the administrator hands it out of quarantine.
This article discusses the integration setup and an example of triggering.
Cisco ISE is
In short, Cisco ISE is a Network Access Control (NAC) solution for providing context-aware access control to users on the internal network. Cisco ISE allows you to:
- Create guest access quickly and easily
- Detect BYOD devices (such as employees' home PCs that they bring to work)
- Centralize and apply security policies to domain and non-domain users using SGT security group labels ( TrustSec technology )
- Check computers for certain software installed and compliance with standards (posturing)
- Classify and profile endpoint and network devices
- Provide endpoint visibility
- Send logs of events logon / logoff of users, their accounts (identity) on NGFW to form user-based policy
- Do everything that the AAA server can do
Many colleagues in the industry have written about Cisco ISE, I recommend that you familiarize yourself with: the practice of implementing Cisco ISE , how to prepare for the implementation of Cisco ISE, and integration with Cisco FirePOWER .
How quarantine works
The workflow of the “add / remove from quarantine” ANC policy (Adaptive Network Control) in Cisco ISE is depicted below:

- The user must first log into the corporate network through the WLC (access point controller). Then a REST API quarantine request is sent from the Policy Administration Node .
- (Monitoring Node), , PrRT PSN (Policy Service Node, ISE). CoA .
- .
- .
- RADIUS (Monitoring Node).
- .
- , .
- , .
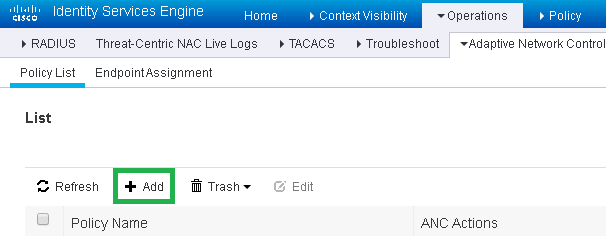
1. In the Cisco ISE web interface, go to the Operations> Policy List tab and create a new policy by clicking Add .
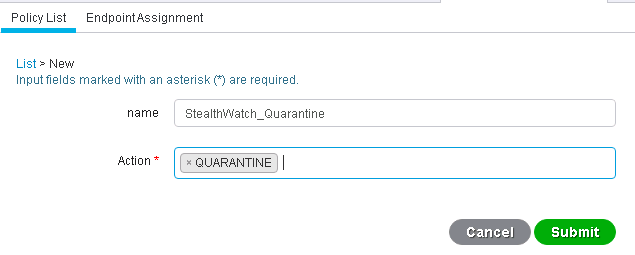
2. Let's name it StealthWatch_Quarantine and select the action “Quarantine ” and click Submit .
3. The next step is to configure the policy. Go to Policy> Policy Sets and click on the rightmost arrow under the View column .
4. In the Authorization Policy> Global Exceptions tab , a new rule is created (click on the “+”). Next, in the Conditions column, click “+” again and select the Session ANCPolicy attribute . Action in this ruleEquals - StealthWatch_Quarantine .
In the Profile> DenyAccess column and optionally in the Security Groups column, you can specify your security group (for example, guests or marketing department). Finally, save the changes.

5. In the Operations> Live Logs tab (RADIUS or TACACS), you can view the logs by user or address. Suppose we find user wesley.

6. Go to the StealthWatch web interface and find this user in the Monitor> Users tab .
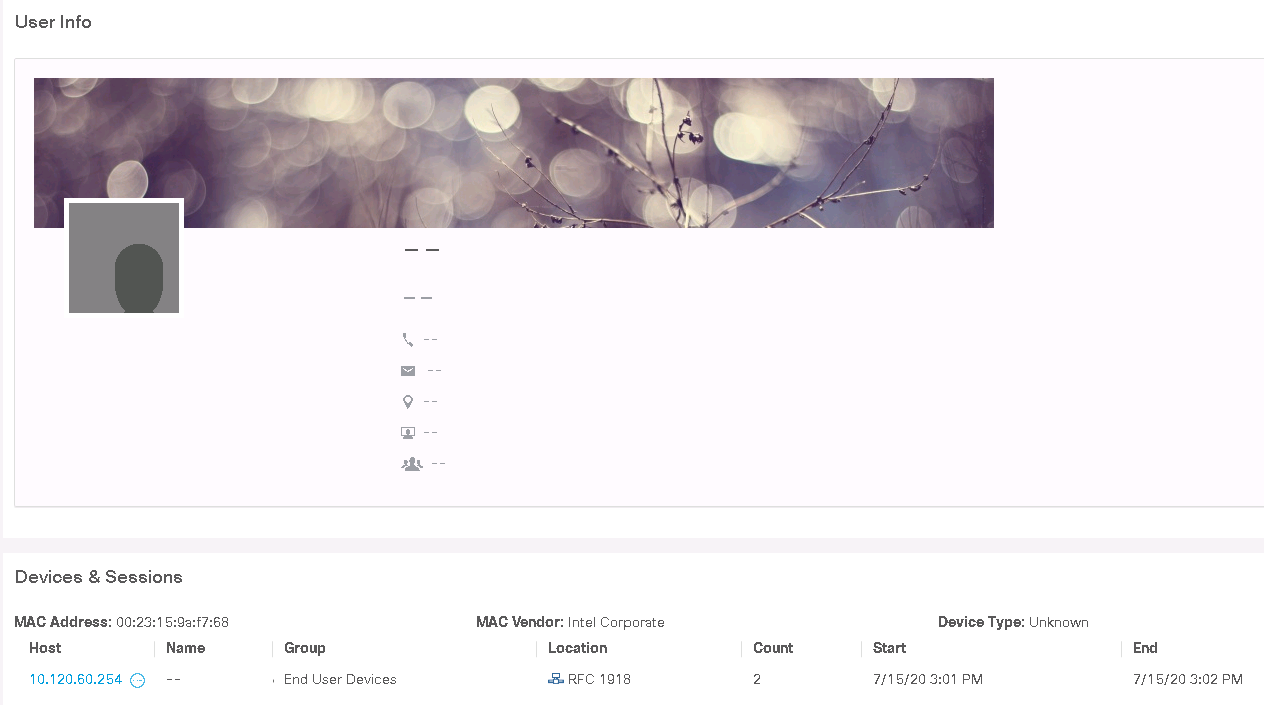
7. Go to its host by clicking on the IP address.
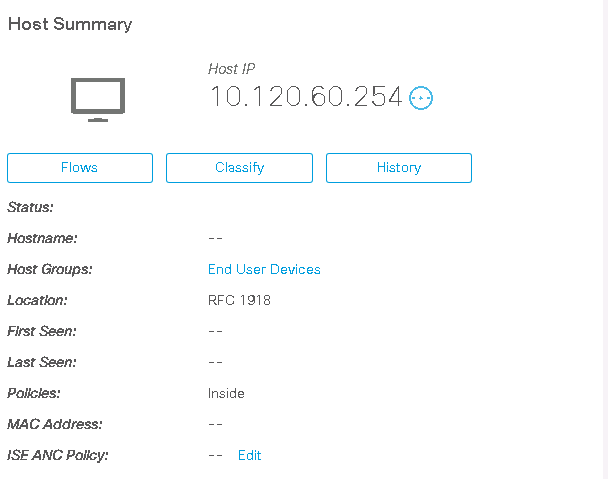
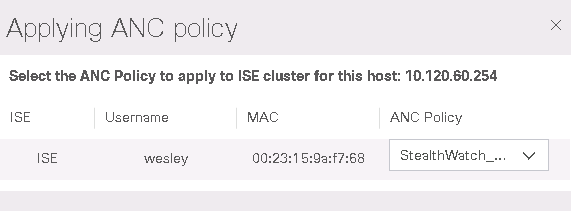
8. In ISE ANC Policy, select Edit> StealthWatch_Quarantine> Save... The host is quarantined pending further investigation.
Additionally, the ANC policy can use the actions port_shutdown (shutdown of a network device port) and port_bounce (shutdown / no shutdown of a device). For example, if the malware has managed to spread over an entire VLAN, then it would be more logical and faster to disable the port on the access-level switch, rather than quarantine each host.
Conclusion
Just as Cisco StealthWatch is a worthy security incident monitoring solution, Cisco ISE is an excellent user access control solution. The integration of these two solutions really works and allows you to minimize the response time to information security incidents.
Soon, Cisco promises to add an automatic response to selected incidents and apply ANC policies to them, or you can write a script yourself. Both StealthWatch and ISE have an open REST API . However, this automatic integration should be configured only after a long time, when StealthWatch has formed the correct host behavior models and the number of false positives is minimal.
More information on the Cisco StealthWatch is available on the website . In the near future we are planning several more technical publications on various information security products. If you are interested in this topic, then stay tuned to our channels ( Telegram , Facebook , VK , TS Solution Blog )!