
Just the other day , Check Point experts discovered a new vulnerability in Windows-based DNS servers. Those. virtually every corporate network is at risk. The name of this vulnerability is CVE-2020-1350 | Windows DNS Server Remote Code Execution Vulnerability . CVSS Score - 10.0. According to Microsoft, all versions of Windows Server are affected.
The vulnerability targets a buffer overflow and requires little or no user interaction. Under the cut, you will find a video with the implementation of this attack, its detailed description, and most importantly, how to protect yourself right now.
Attack video
Short description
How to protect yourself?
Method 1. Update
Install the update urgently on Windows Server, which acts as a DNS server.
Method 2. Workaround
If it is currently not possible to install an update, then you can reduce the maximum length of DNS messages to avoid buffer overflows.
reg add "HKEY_LOCAL_MACHINE \ SYSTEM \ CurrentControlSet \ Services \ DNS \ Parameters" / v "TcpReceivePacketSize" / t REG_DWORD / d 0xFF00 / f && net stop DNS && net start DNS
Method 3. IPS
If you are using IPS at the network perimeter (for example, as part of a UTM or NGFW solution), then make sure you have a signature (it can come after an update). This is how it looks in Check Point:
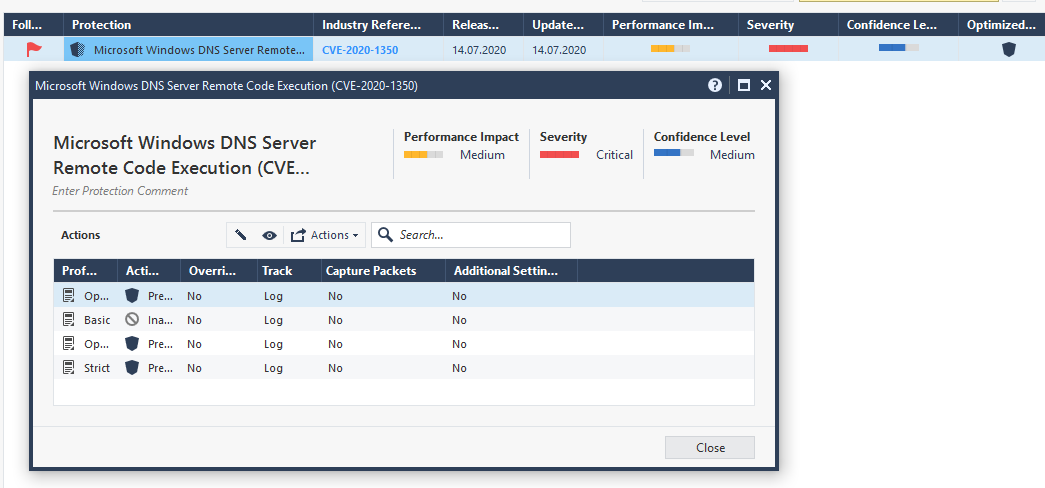
There should be Prevent. If you need help setting up - write .
We will try to update the information as it becomes available. Stay tuned for updates in our channels ( Telegram , Facebook , VK , TS Solution Blog )!