There are two ways to make the owner of a smartphone forever happy with annoying ads. In the first case, the application registers the advertising load in the system partition by hacking the smartphone using one of the methods of obtaining root rights. The second option is that advertising is already built into the phone by the manufacturer: most often this happens with inexpensive devices. According to Kaspersky Lab, up to 15% of users who encounter adware are dealing with system adware. In addition to intrusive banners, most modules can download anything to a user's smartphone, including malware.
The functionality of some of the modules is impressive. For example, Trojan-Dropper.AndroidOS.Agent.pe is embedded in the system application responsible for drawing the interface, which is basically impossible to remove while keeping the phone working. The xHelper Trojan examined in April does the same thing . Trojan.AndroidOS.Sivu.c covers legitimate applications or the home screen with banners, displays advertisements in notifications, but can also download and install arbitrary code on a smartphone. Trojan-Downloader.AndroidOS.Facmod.a is embedded in the SystemUI module, it is present in some smartphones by default, it can open a browser unnoticed by the user and load pages with ads.
The report also mentions “vendor ad units”. In particular, such a business modelused in a number of models by Xiaomi. We found similar functions in Meizu smartphones, but the ad module there, in addition to displaying banners, could download and execute JavaScript code.
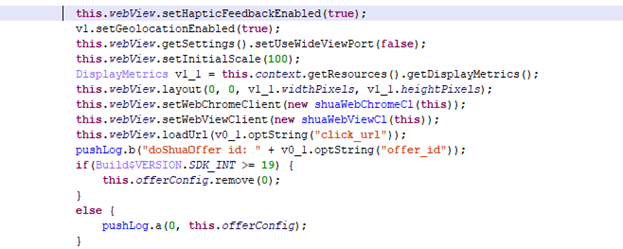
The study also analyzes other questionable pieces of code found in Meizu smartphones. The general conclusion is this: we can assume that the advertising business model has the right to exist, but in some smartphones the code responsible for this is simply dangerous. At a minimum, a vendor can use it to profit from displaying banners, installing sponsored apps, and more. But if attackers somehow gain access to the ad network, banner features can easily turn into a backdoor.
Also worth mentioning is a recent studyby Malwarebytes: its experts found on a smartphone with Android 7.1 a backdoor built into the application for managing settings. The set of functions is very similar to the one described above: downloading applications, displaying ads, communicating with the command center for complete control over the device. The tested smartphone is cheap and is used by a government agency that distributes devices to the poor. In this and other cases of a factory backdoor or adware, users can only hope for the release of custom firmware by enthusiasts.
What else happened
Check Point Software specialists investigate the Joker Trojan, which regularly pops up on Google Play. In January this year, the store's moderators removed 17,000 applications loaded with malicious code, but they periodically come back in slightly modified form.
Report ( news , source in PDF ) on the security of routers of the German Fraunhofer Institute. 127 devices were examined, vulnerabilities were found in all, an average of 53 critical problems in each.
A critical vulnerability was found and closed in the Zoom client for Windows in the next version 5.1.3. No details have been released yet, but the video above shows PoC.
Research on vulnerabilities in TP-Link Casa IP cameras. Nothing serious, but the implementation of a web interface for managing devices allows you to identify user logins and then try to guess a password, for example, from numerous leaks.
Critical vulnerability in Adning plugin for WordPress sites.
Another set of vulnerabilities was discovered and closed in the Citrix Application Delivery Controller and Citrix Gateway software.
An interesting study of the vulnerability in Facebook, which allowed deleting any photo of any user.