Today we will start with the fact that at one point I decided, instead of training on vulnerable machines, to test my own Wi-Fi router for vulnerabilities, which I received back in 2015. Then there was a very popular tariff with Beeline, when, along with the Internet connection, the Wi-Fi router itself went for rent for 1 ruble, which I decided to test.
Smart Box router, the latest firmware version is 2.0.38 (Firmware release 2017), since then there have been no updates.

Start
By default, the router has 2 accounts admin and SuperUser, few people know about this, but there is information about this in open sources. The password from SuperUser is the serial number of the router and can be found in the settings in the “Advanced settings> Information” tab or on the sticker under the router. Accordingly, the SuperUser user has more options for configuring the router.
User admin / SuperUser
The router has several types of accounts “User, administrator and manufacturer”, respectively, they have different privileges in terms of router configuration and we take note of this.
OS Command Injection
Yes, the router has a command injection vulnerability.
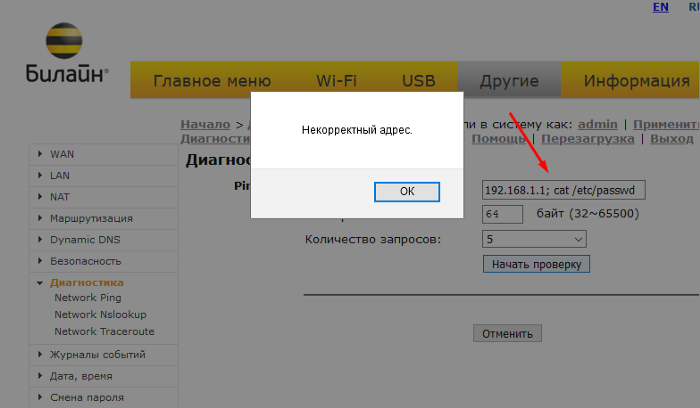
First we login and go to “Advanced Settings> Others> Diagnostics” and we can Ping, nslookup and traceroute using the built-in router functions. Let's try ping and thus execute another command.
Client side protection
As we can see, we are warned that the address is incorrect, but this protection works only on the client side. If we intercept the request and change it, then we will bypass this protection. And I will do it using the Burp Suite pro tool.
 We intercept the request and change its
We intercept the request and change its
Result
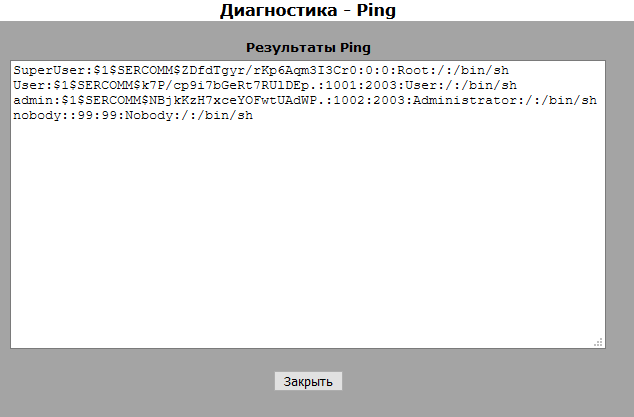
As we can see, instead of ping, a completely different command was executed, which we indicated when intercepting the request. Here we see that the router has 3 accounts (SuperUser, User, admin), I created the User user myself. By default there will be only 2 users (SuperUser and admin). With the help of this vulnerability, I learned about the SuperUser user, then I was very surprised and I became very interested.
This vulnerability is present in nslookup and traceroute and is exploited in the same way, by intercepting a request. Below I attach a PoC video with the exploitation of vulnerabilities.
Ping
Nslookup
Traceroute
Remember in the beginning we took note that there are 3 types of accounts? So, regardless of the type of account, commands are executed with SuperUser privileges, which gives us more options. And yes, the vulnerability is present in any type of account (User, Administrator and Manufacturer).
Vulnerable services
The router has 3 services “OpenSSH 5.2, FTP vsftpd 3.0.2 and Samba 3.0.22”. Services are old versions and many vulnerabilities have been found in them all the time. So that you understand, at the time of this writing, the latest versions of services (OpenSSH 8.2, FTP vsftpd 3.0.3 and Samba 4.12.0). I have selected a couple of exploits for these services for testing and we will start in order.
OpenSSH (5.2)
Vulnerability CVE-2016–6515 allows denial of service DoS.
I log into the router's system via SSH and use the top command to monitor the CPU load and look at the (CPU) field and exploit the vulnerability.
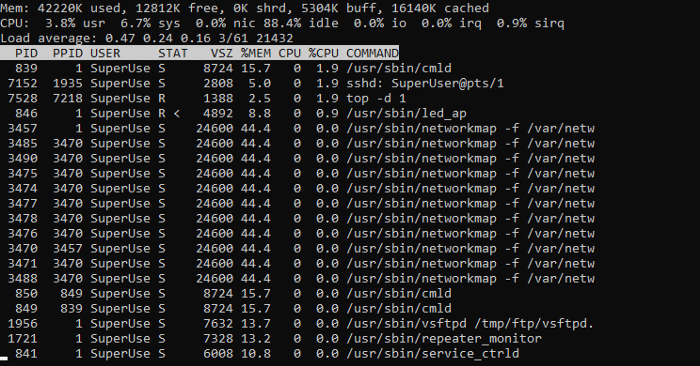
In the normal state

After exploiting the vulnerability
As a result, web pages can take a long time to load, and even at some point the router can freeze and even go into reboot. But I had a funny case when, during the exploitation of this vulnerability, my computer went into reboot with a blue screen of death (Sad smiley), it was very unexpected and strange: D
Below I attach a PoC video with the exploitation of this vulnerability.
Operation CVE-2016–6515
Samba (3.0.22)
The smb loris vulnerability that could cause a denial of service DoS. This vulnerability can be exploited using metasploit, it is located along the path “auxiliary / dos / smb / smb_loris”. As a result, the router will reboot.
Below is a PoC video of the exploitation of the vulnerability.
SMB_Loris exploitation
FTP (vsftpd 3.0.2)
Vulnerability CVE-2015-1419 allows you to bypass access restrictions. Unfortunately, I did not find the exploit, but it also takes place.
https
Yes, the router has the option to enable a secure connection. As I understand it, the encryption protocol SSL 2.0 or 3.0 is used and the certificate is self-signed, which is quite normal for local routers. And in terms of security, SSL has long been outdated and insecure. There are now more secure options like TLS 1.3
Other weak points
During authentication in the router, the login and password are encoded in base64, which makes it easy to decode them. Given the fact that the https protocol is not used by default, for an encrypted connection, then the encoding of the login and password is at least some kind of protection.
It is better to let the data be transmitted in an encoded state than completely open. Frankly, at first, this moment led me astray, and only after a while I realized that the data is encoded.
Login and password are transmitted in an encoded state.

After decoding I
attach PoC video with decoding below.
Base64 decode
It will not be difficult for cybercriminals to listen to the network and, using traffic analysis, identify the username and password and decode them.
Contacting Beeline
Initially, I contacted them using an online chat and they recommended that I call and ask all the questions there, which I did.
I asked just a couple of questions and here's the bottom line: The Smart box router is no longer relevant and updates will no longer be released on it. And as I wrote at the very beginning, it has stopped updating since 2017, and then it was its last update. As the operator Aleksey mentioned (if you are reading this, a big hello to you) that the Smart box one router is still supported and if someone finds a vulnerability in it, they can safely call and the information will be transferred to the security service. As I understand it, Smart box one is the next model after Smart box.
Outcome
The router itself is good, but in terms of security it is unfortunately outdated. If you do use it, it is recommended to disable services such as SSH, FTP and Samba, since they are old versions and many vulnerabilities have been found in them and it is unsafe to use them, especially on the global network. Better yet, change the router to a newer model (No matter from which vendor) which will be supported in terms of security updates.
Finally, let's go to Shodan and see how many Smart box routers are available in the global network.

As we can see, 79 devices were found in total, and this is also taking into account the fact that I have a free version account, without a subscription. Accordingly, with a subscription, there will be much more results and opportunities. It is also worth considering that Smart box routers of different models are available in the global network, as we see on the right. So, most Smart box routers (It doesn't matter from the router model) use the same versions of vulnerable services that I wrote about above and they are available on the global network, and this poses a security threat.
The OS Command Injection vulnerability has been assigned the CVE identifier “CVE-2020-12246”.
At the end of the article, I would like to give a couple of tips to readers:
- Update the firmware of your routers
- Disable services you are not using
- Track activity on your network
The security of the router is really important, because many devices are connected to it, and these devices can become targets of attackers for compromise.
The article is taken from my blog .