We would like to share a small selection of information security incidents for June 2020. Let's make a reservation right away that it does not pretend to be a complete picture of all world news in the field of information security. We bring to your attention only those that seemed the most interesting to Reksoft specialists.

Gas stations in St. Petersburg
Fraudsters hacked into the servers of gas stations in St. Petersburg and stole fuel.
In total, they managed to execute 417 free gas stations at 15 gas stations
and steal more than 2 million rubles. To carry out illegal activities, a malicious program was used that destabilized the work of servers at the gas station. As a result, immediately after refueling the required amount of fuel, the paid money was automatically returned to the bank card of one of the criminals.
The attackers poured the stolen fuel into a Gazelle truck with a 1,000-liter tank, and then resold it at the parking lots of heavy vehicles.
Source
Lg electronics
The hacker group Maze reported a successful attack on LG Electronics.
In a press release, cybercriminals warn against the company trying to recover lost data. To prove the hacking, screenshots with a list of firmware files and source codes and an sql dump of one of the company's databases are attached to the press release.
Source: https://cybleinc.com/2020/06/25/maze-ransomware-operators-claims-to-breach-lg-electronics-a-renowned-south-korean-multinational-electronics-company-data-leak/
Honda
Honda said it was the victim of a ransomware cyberattack. The incident affected some of the company's operations, including production systems outside of Japan.
According to preliminary data, one of the company's internal servers was infected with the ransomware Snake. This program blocks ACS from General Electric used in industrial enterprises.
Researchers found a sample Snake software on VirusTotal that validates Honda's mds.honda.com domain name. If the domain name cannot be resolved (determine the IP address), the ransomware terminates without encrypting any files. According to the researchers, this may indicate deliberate actions of the attackers.
Source
Telegram
A database with the data of several million users of the Telegram messenger has appeared on the network, its volume is approximately 900 MB.
The Telegram press service confirmed the existence of the database, explaining that information is collected through the built-in contact import function even during user registration. The company representatives added that no service that allows users to communicate with contacts from their phone book can completely rule out such a bust.
Press officers also stressed that most of the "leaked" accounts are no longer relevant, and the measures taken by the company in 2019 help not to "shine" your number.
Source
Elexon
Cybercriminals from the REvil group posted on their page confidential data from the electric power company Elexon, stolen during a cyber attack on May 14, 2020. The released data includes 1,280 files, including Elexon employee passports and company confidential information.
The attackers exploited the CVE-2019-11510 vulnerability in the outdated version of the Pulse Secure SSL VPN server used by the company. Presumably, the company refused to comply with the ransomware demands and restored its IT infrastructure from backups. After that, the attackers published the company's confidential information.
Source
Postbank
As a result of the actions of an insider who stole the master key in one of the data centers, the South African Postbank will have to replace more than 12 million bank cards. The bank's own employees are behind the incident.
Postbank will be forced to reissue all customer cards ever generated with this master key. The bank believes it will cost about $ 58 million. Both regular payment cards and social cards will have to be replaced in order to receive state social benefits.
Source
Claire and Intersport
A web-skimming hacker group (also known as Magecart) hacked online retailers Claire and Intersport and injected malicious code that recorded payment card data entered into cash forms.
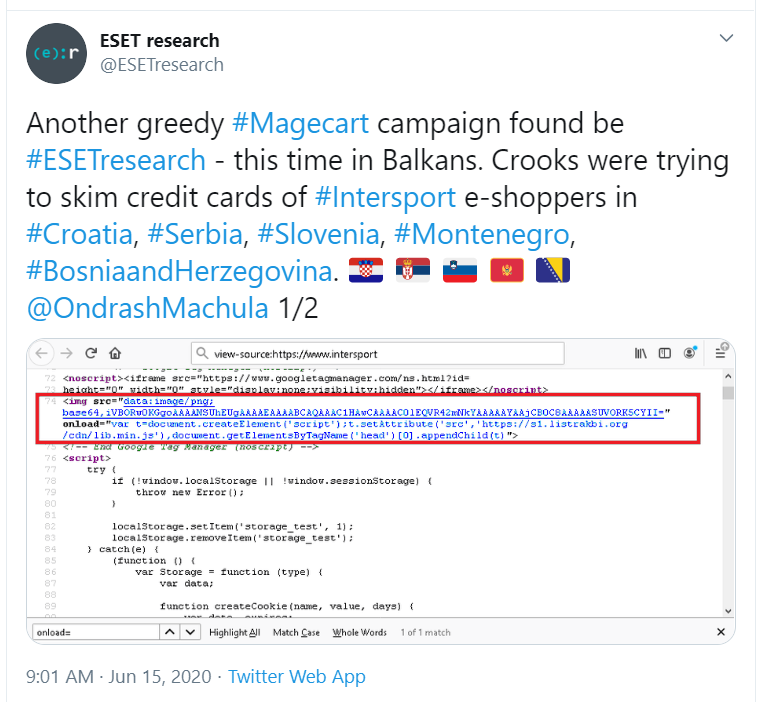
The code embedded by cybercriminals intercepted all user data entered into the forms and sent it to the server claires-assets (.) Com. The domain was registered four weeks before the attacks began specifically for this malicious campaign.
Source
What do you remember from June?