How it all started
Some time ago, the apartment was connected to the Internet from a new provider; earlier, Internet services were delivered to the apartment using ADSL technology. Since I spend little time at home, mobile Internet was more in demand than home. With the transition to a remote location, I decided that the speed of 50-60 Mb / s for home Internet is quite small and decided to increase the speed. With ADSL technology, for technical reasons, the speed above 60 Mb / s cannot be raised. It was decided to switch to another provider with a different declared speed of work and already with the provision of non-ADSL services.
It could have been somehow different
I contacted a representative of the Internet provider. The installers came, drilled a hole into the apartment, and installed an RJ-45 patch cord. They gave a contract and instructions with network settings that need to be set on the router (dedicated ip, gateway, subnet mask and ip addresses of their DNS), took payment for the first month of work and left. When I entered the network settings given to me into my home router, the Internet burst into the apartment. The procedure for the initial entry into the network of a new subscriber seemed too simple to me. No initial authorization was performed, and my identifier was the ip address given to me. The Internet worked quickly and stably. A wifi router worked in the apartment and the connection speed dropped a little through the load-bearing wall. One day, it was necessary to download a file of two tens of gigabytes. I thoughtwhy not connect the RJ-45 going to the apartment directly to the pc.
Know your neighbor
After downloading the entire file, I decided to get to know the neighbors of the switch sockets better.
In apartment buildings, the Internet connection often goes from the provider via optics, enters the wiring closet in one of the switches and is distributed between the entrances, apartments via Ethernet cables, if we consider the most primitive connection scheme. Yes, there is already a technology when optics goes straight to the apartment (GPON), but this is not yet so widespread.
If we take a very simplified topology on the scale of one house, it looks like this:
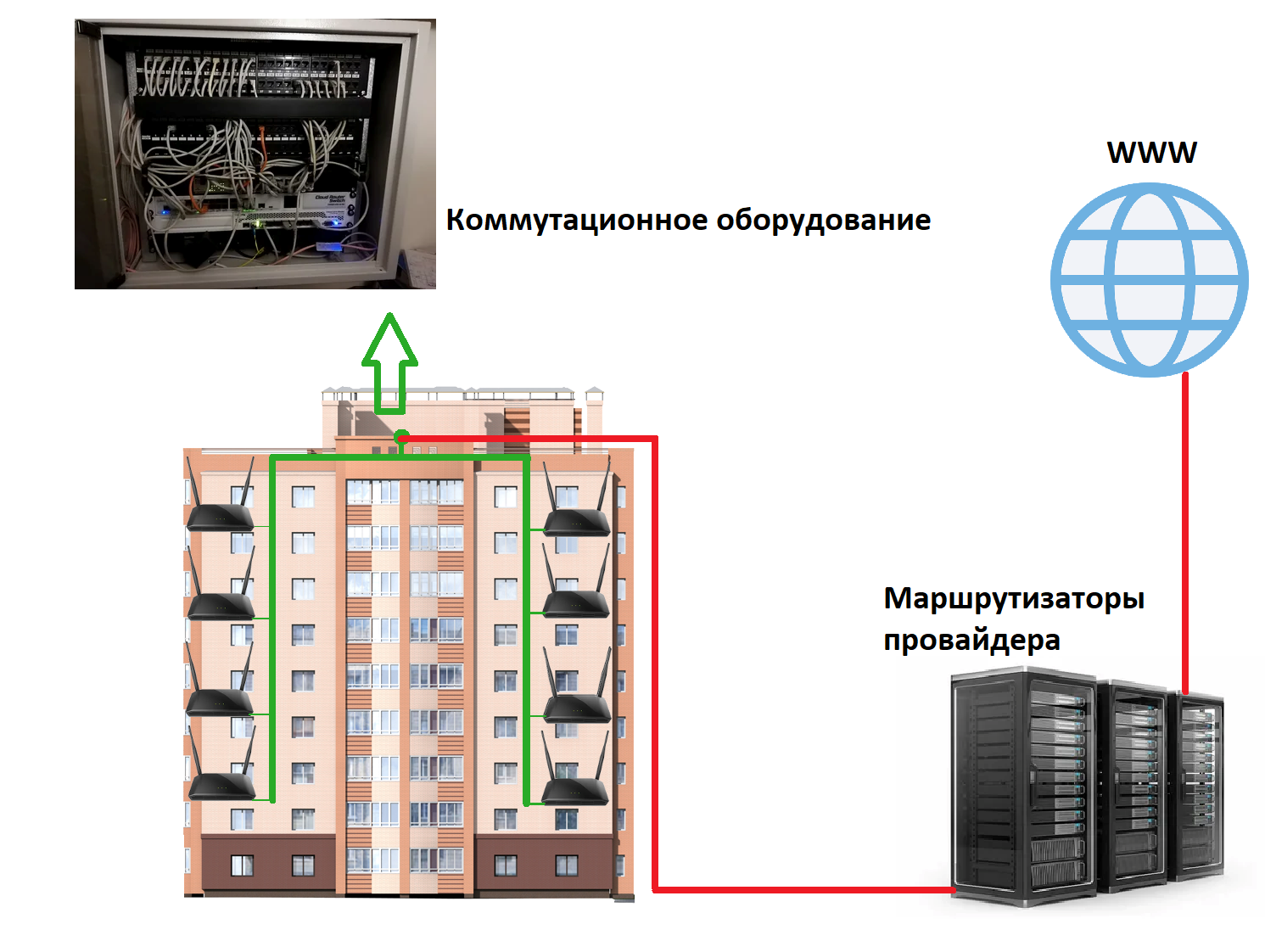
It turns out that the clients of this provider, some neighboring apartments, work in the same local network on the same switching equipment.
By enabling listening on an interface connected directly to the provider's network, you can see broadcast ARP traffic flying from all hosts on the network.
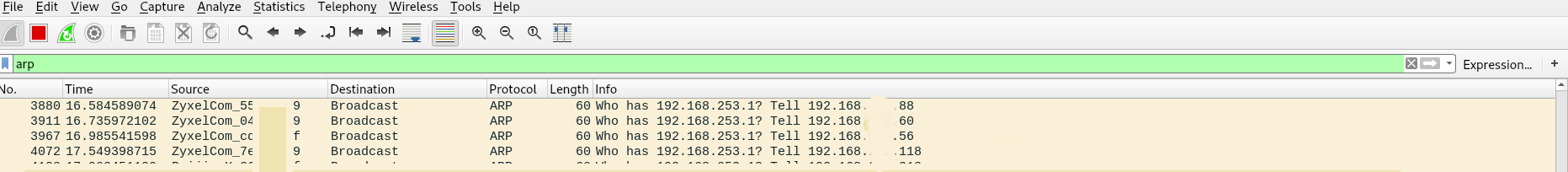
The provider decided not to bother too much with dividing the network into small segments, so broadcast traffic from 253 hosts could walk within the same switch, not counting the switched off ones, thereby clogging the channel bandwidth.
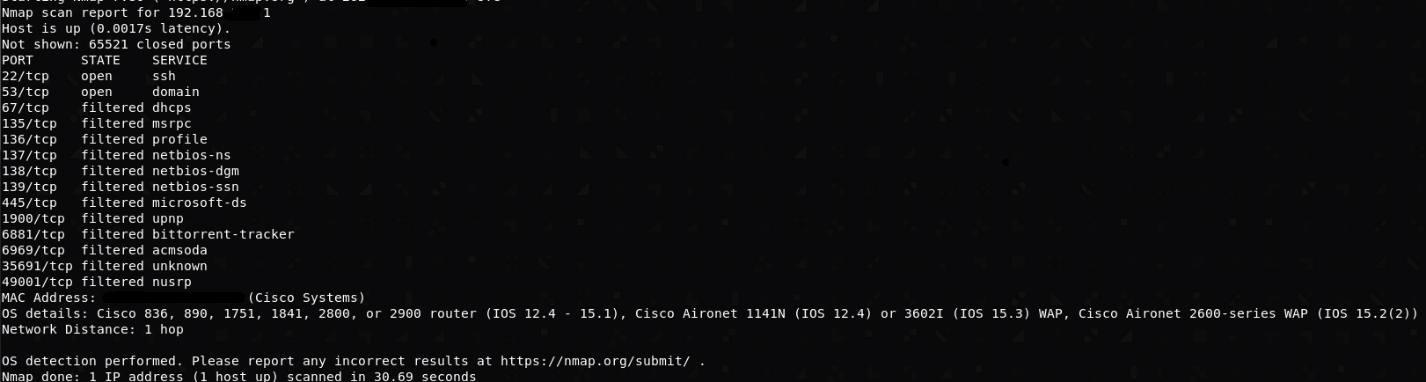
Having scanned the network using nmap, we determined the number of active hosts from the entire pool of addresses, the software version and open ports of the main switch:

And where ARP is there and ARP-spoofing
To carry out further actions, the ettercap-graphical utility was used, there are more modern analogues, but this software attracts with its primitive graphical interface and ease of use.
The first column contains the IP addresses of all routers that responded to the ping, and the second contains their physical addresses.
The physical address is unique, it can be used to collect information about the geographical location of the router, etc., so it will be hidden within the framework of this article.
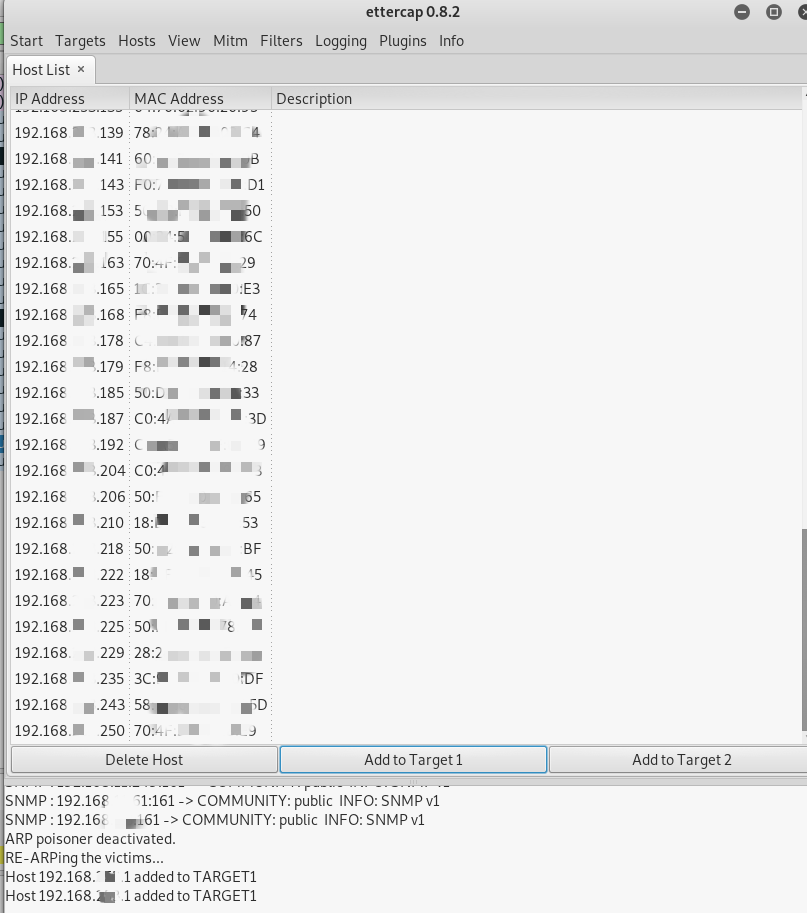
Goal 1 add the main gateway with the address 192.168.xxx.1, goal 2 add one of the other addresses.
We present ourselves to the gateway as a host with the address 192.168.xxx.204, but with its own MAC address. Then we present ourselves to the user router as a gateway with the address 192.168.xxx.1 with our MAC. The details of this ARP vulnerability are detailed in other easily googled articles.
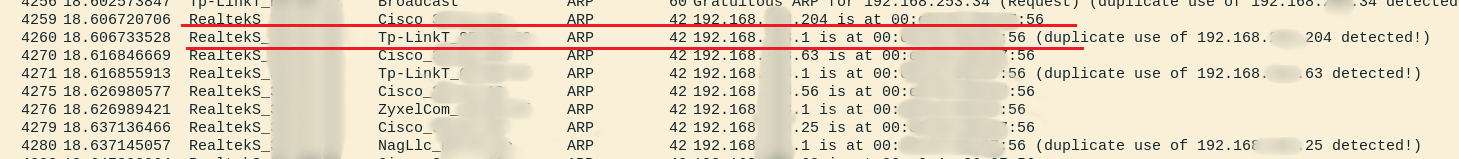
As a result of all the manipulations, we have traffic from hosts that goes through us, having previously enabled packet forwarding:
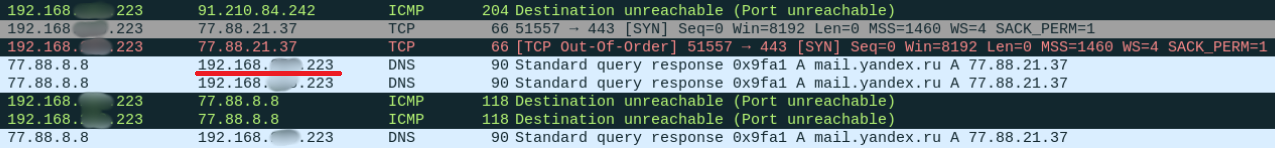
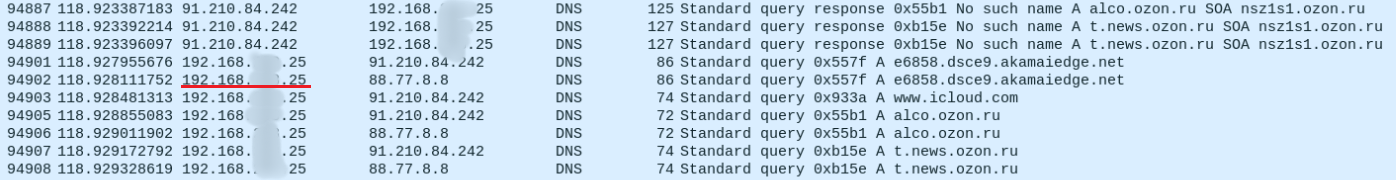
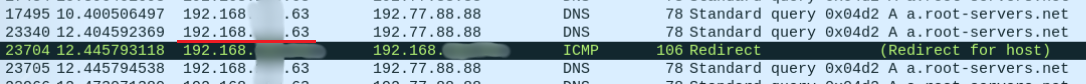


Yes, https is already used almost everywhere, but the network is still full of other insecure protocols. For example, the same DNS with the DNS spoofing attack. The very fact that an MITM attack is possible gives rise to many other attacks. Things get worse when there are several dozen active hosts available on the network. It is worth considering that this is the private sector, not a corporate network, and not everyone has the means of protection for detecting and countering associated attacks.
How to avoid it
The provider should be concerned about this problem, it is very simple to configure protection against such attacks, in the case of the same Cisco switch.

Enabling Dynamic ARP Inspection (DAI) would prevent the master gateway from spoofing the MAC address. Splitting the broadcast domain into smaller segments prevented at least the propagation of ARP traffic to all hosts in a row and a decrease in the number of hosts that could be attacked. The client, in turn, can protect against such manipulations by setting up a VPN directly on the home router, most devices already support this functionality.
conclusions
Most likely, providers do not care about this, all efforts are aimed at increasing the number of customers. This material was written not to demonstrate the attack, but to remind you that even your ISP's network may not be very secure for the transmission of your data. I am sure that there are many small regional Internet service providers who have done nothing more than is necessary for the basic operation of network equipment.