The vulnerability was first discovered on 06/26/2020, which the author immediately reported to Dom.ru technical support. The author long and persistently tried to solve the problem non-publicly, but met with a complete lack of understanding by technical specialists. The provider assures that the author's case is an isolated one, but today confirmation of the problem came from other sources. The author does not publish anyone's personal data and does not call for illegal actions. The writing of this article is a compulsory measure.
Although, if the provider directly says that everything is fine, then the publicly available description of the operation of its services should not bear any risks.
What's the point?
A large Internet provider Dom.ru intercepts the user's http traffic and, from time to time, redirects it to its advertising page instead of the target one. In the body of the advertising page, the provider sends a link to configure or unsubscribe from advertising notifications, which leads to the user's personal account. This link provides full access to the user's personal account without entering a username and password and allows you to do this from anywhere in the world. The advertising page is transmitted over the unencrypted http protocol. This means that a leak could have occurred on any node (or even through an insert ) between you and the server responsible for issuing advertising pages (info.ertelecom.ru), and it doesn't matter that the personal account itself, after clicking on the link, works via https.
Is my data leaked?
The provider itself will not tell you exactly. If you have recently seen a similar page opened via the http protocol, then you are susceptible to a leak.
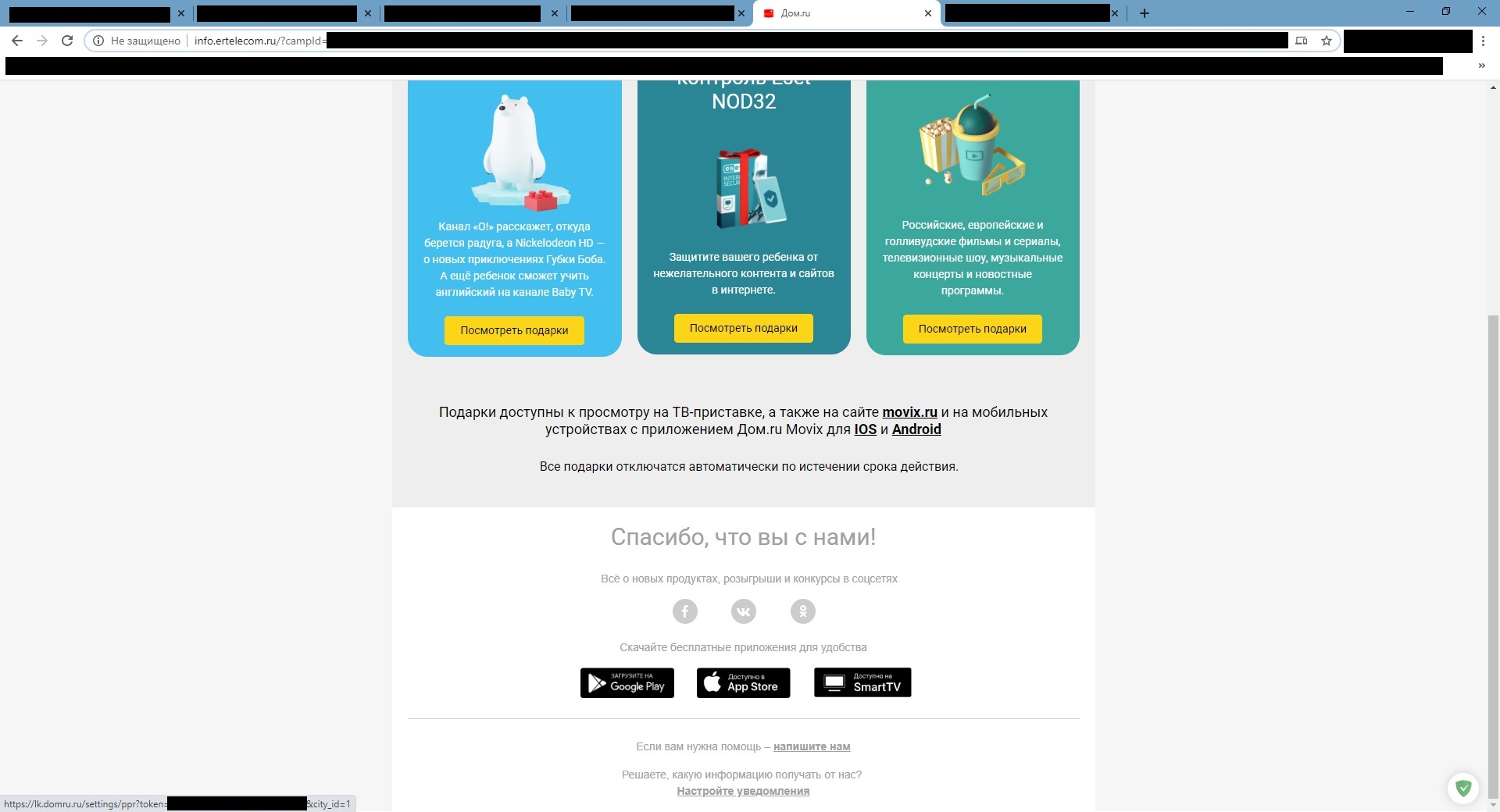
How to protect yourself?
- Go to the settings of your personal account, then at the bottom of the page select "Configure notifications from Dom.ru" and, at least, disable all browser advertising.
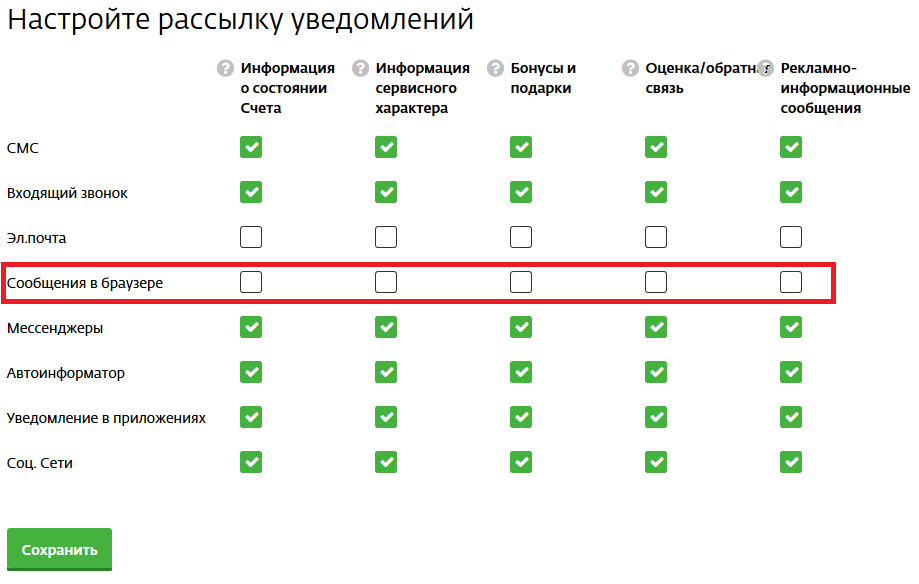
- If you recently saw an advertising page, then you just have to hope that the data has not leaked and that the provider will soon deny access to the backdoor links. At least for those already "exposed".
- If you have never seen such an advertisement, then you can only hope that disabling browser advertising will help. I have no reliable data, but habrayusers in another topic mentioned that other ads were shown despite being disconnected.
Details. What could have leaked?
The vulnerability was first found on 06/26/2020. I have no data on how long this vulnerability was active before 06/26/2020. On 07/02/2020 I received a screenshot from another subscriber, on which the page was opened using the https protocol, but on 07/05/2020 I received another screenshot with an advertising page open via http, which suggests that your data may still leak, even if you have never seen an ad page before. I have long and unsuccessfully tried to draw the attention of the provider's technical specialists to the problem. In the screenshot at the end of the article, the last message from the provider to me, received on 04/07/2020.
And now about the backdoor link itself. At the bottom of the advertising page there is a standard link to unsubscribe from advertising notifications. This is how it looks:
https://lk.domru.ru/settings/ppr?token=&city_id=
city_id is a two-digit number, token is an alphanumeric sequence of 31 characters.
Clicking on the link opens full access to your personal account, its administrative functions, such as changing the tariff, and the user's personal data:
- Full name
- Residence address accurate to the apartment
- Full bank card number, if the card was added to the account, masked with only two asterisks
- Phone number masked with 4 asterisks - easy to link to an existing phone database by city, name
- Client account balance
- Your television preferences for add-on packages services
and other data.
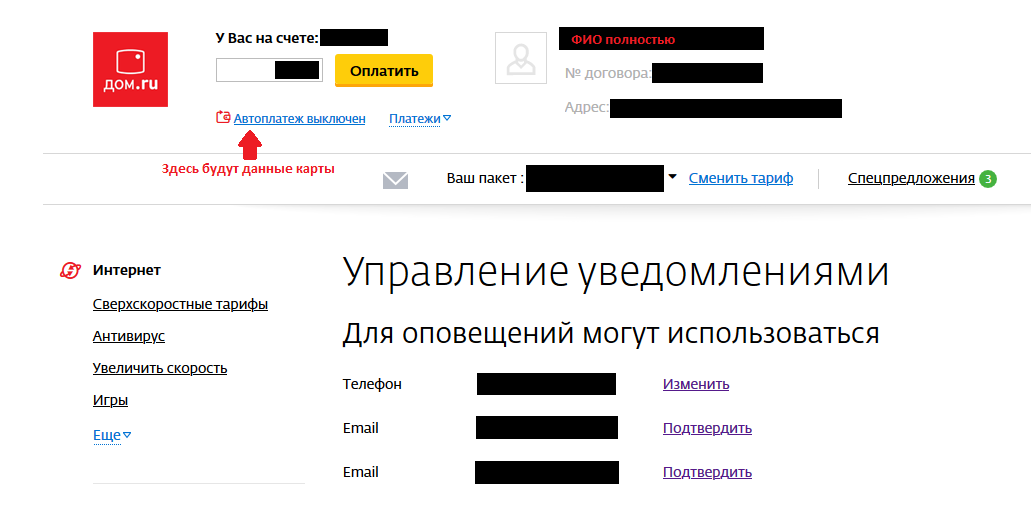
From the good - the provider does not provide any service like a domra wallet, or any other way to withdraw money from the balance. You will only get to the money if the attacker turns on the service.
Nevertheless, the fact that attackers may have another set of data about you, sometimes quite rare data, does not bode well.
- Social engineering. The attacker can introduce himself as you in a telephone conversation with a bank or other organization. The data set for chatting with him is now expanded.
- Telephone fraud. The speech of the pseudo-security officers from the bank will be even more personalized. They will tell you where you live and what your bank card number is, knowing only your phone number and name before.
I do not know if the provider knows how to rip http pages out of the body of unencrypted requests to socks and http proxy and place ads instead.
Also, I do not know how many backdoor links could have leaked, which means how many of them can still be used.
About subjective
My personal opinion is that such a link should not exist here in principle. Even transmitted over https. In this situation, the link should lead either to a non-logged in account, or to a small unsubscribe form, but in no case to the full version of your personal account. Even if the transmission of such a link is guaranteed to be secure, your home Internet users are not always smart. A child who sees such an advertisement can surprise their parents in the form of connecting a new high-speed tariff. The tariff is high-speed, in fact it was shown in advertising.
I'm not going to speculate, but even with a secure transfer of the link, in the worst case, it can be available to very many employees of the provider. I am not sure that it is not logged in the access logs of application servers, just as passwords should not be logged. I am not sure that the token, as a convenient replacement for the user ID, is not used in those. support. The temptation to use such a link "on the side" can be very great if it is available and available anywhere, and its use is not tracked in any way. Provider such activity, if ever tracked down, then finding the culprit will be very problematic. And in the end, it is clearly not worth creating unnecessary temptations and risks where this can be avoided.
As to whether it was done so purposefully, and not by mistake, I am not going to speculate either.
The provider calls this link pass-through, but I believe it is not. And what do you think?
Cherry on the cake, I would like to post the latest response from the provider.

- The page magically appears immediately in my router, and I thought of intermediate nodes in the trace.
- I don't know what the lifetime of the tokens is, but I can still log in using the token dated 06/26/2020 (not the fact that it was not hijacked either). On 07/05/2020, I received another token from my account. Both are valid at the same time.
- And in general, the user's browser is to blame.
By the way, I got the second token in another browser.
On 07/05/2020, I was even lucky to catch the next packet on the router interface.
The browser is to blame
17:04:27.910885 IP (tos 0x28, ttl 126, id 54321, offset 0, flags [none], proto TCP (6), length 415)
___ > __: Flags [P.], cksum 0xad30 (correct), seq 1:376, ack 731, win 65534, length 375: HTTP, length: 375
HTTP/1.1 303 See Other
Cache-Control: no-cache,no-store,max-age=1
Pragma: no-cache
Expires: Thu, 01 Jan 1970 00:00:00 GMT
Connection: close
Content-Length: 13
Location: http://info.ertelecom.ru/?campId=&machine=perm&ourl=__
On 07/06/2020 I received a report from another source about opening an advertising page via http.
UPD 07/14/2020. Old tokens do not work, but advertising, and therefore a link that opens full access to your personal account, is still transmitted via http.
Fresh screenshot


Instead of a conclusion
I still do not have any dislike for the provider, although, I think, many in my place would feel acute anger. I understand that the human factor can sometimes be very strong. I have never pursued goals to make someone bad - this is not about me. My goal is to finally get through to the provider and warn you. And you will warn your friends and loved ones.
Like many companies, Dom.ru does not have a bug bounty program. I urge all readers to never go on about the momentary "black" profit. First of all, you act against people like you, not the "system".
I would like to ask a couple of questions to the Khabrovites.