
We believe that the time for simple and easily detectable DDoS attacks (and simple tools that can prevent them) is over. Cybercriminals have learned to better conceal these attacks and carry them out with increasing sophistication. The dark industry has moved from brute force to application layer attacks. She receives serious orders for the destruction of business processes, including quite offline ones.
Breaking into reality
In 2017, a series of DDoS attacks targeting Sweden's transport services resulted in long train delays . In 2019, Denmark's national rail operator Danske Statsbaner went offline. As a result, ticket machines and automatic gates did not work at the stations, and more than 15 thousand passengers were unable to go anywhere. In the same 2019, a powerful cyber attack caused a power outage in Venezuela .
The consequences of DDoS attacks are now experienced not only by online users, but also by people, as they say, IRL (in real life). While attackers have historically only targeted online services, they are now often tasked with disrupting any business activity. According to our estimates, today more than 60% of attacks have such a target - for extortion or unscrupulous competition. Transactions and logistics are especially vulnerable.
Smarter and more expensive
DDoS continues to be considered one of the most widespread and fastest growing types of cybercrime. According to experts, from 2020 their number will only grow. This is attributed to various reasons - and with an even greater transition of business to online due to the pandemic, and with the development of the shadowy cybercrime industry, and even with the spread of 5G .
DDoS attacks became popular in due time due to their ease of deployment and low cost: a couple of years ago they could be initiated for $ 50 per day. Today, both the targets and methods of attack have changed, resulting in an increase in their complexity and, as a result, cost. No, prices from $ 5 per hour are still in the price lists (yes, cybercriminals have prices and tariff scales), but they already require from $ 400 per day for a site with protection, and the cost of “individual” orders for large companies reaches several thousand dollars.
There are now two main types of DDoS attacks. The first goal is to make an online resource unavailable for a certain period of time. The cybercriminals charge for them during the attack itself. In this case, the DDoS operator does not care about any specific result, and the client actually makes an advance payment for the start of the attack. These methods are quite cheap.
The second type is attacks that are paid only when a certain result is achieved. It's more interesting with them. They are much more difficult to execute and therefore significantly more expensive, since attackers have to choose the most effective methods to achieve their goals. At Variti, we sometimes play whole chess games with cybercriminals, in which they instantly change tactics and tools and try to break into several vulnerabilities at several levels at once. These are clearly team attacks in which hackers know how to react and counter the actions of defenders. Fighting them is not only difficult, but also very costly for companies. For example, one of our clients, a large network retailer, had a team of 30 people for almost three years, whose task was to fight DDoS attacks.
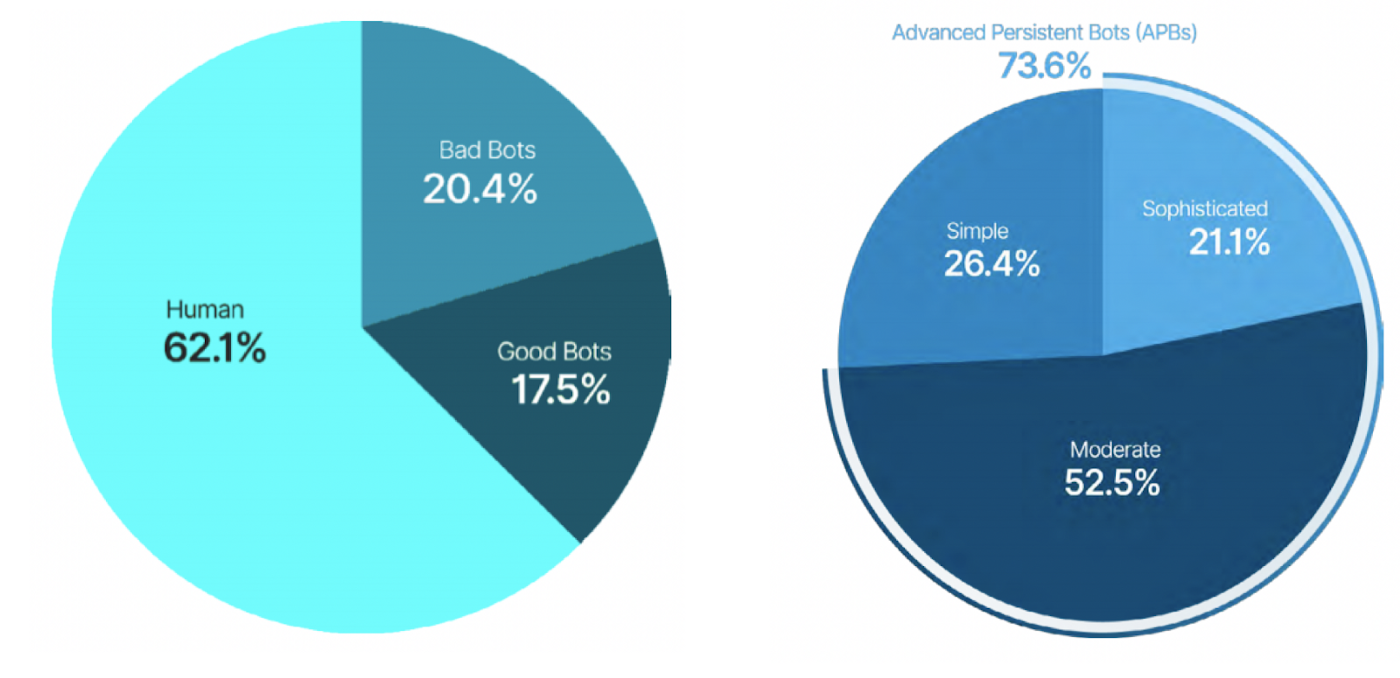
According to Variti, simple DDoS attacks, carried out solely out of boredom, trolling, or dissatisfaction with a certain company, currently account for less than 10% of all DDoS attacks (of course, unprotected resources may have different statistics, we look at the data of our clients ). Everything else is the work of professional teams. At the same time, three quarters of all “bad” bots are complex bots that are difficult to detect using most modern market solutions. They mimic the behavior of real users or browsers and implement patterns that make it difficult to distinguish between “good” and “bad” requests. This makes the attacks less visible and therefore more effective.
Data from GlobalDots
New DDoS targets
The Bad Bot Report from analysts at GlobalDots shows that bots now generate 50% of all web traffic, with 17.5% of them being malicious bots.
Bots are able to spoil the life of companies in different ways: in addition to the fact that they "lay" sites, they are now engaged in the fact that they increase the cost of advertising, clicks of advertisements, scrambling prices to make them a penny less and lure buyers, and steal content for various bad purposes (for example, we recently wroteabout sites with stolen content that force users to solve other people's captchas). Bots greatly distort various business statistics, and as a result, decisions are made based on incorrect data. A DDoS attack is often a smokescreen for even more serious crimes like hacking and data theft. And now we see that a whole new class of cyber threats has been added - this is the disruption of certain business processes of the company, often offline (since in our time nothing can be completely “offline”). Especially often we see that logistic processes and communication with clients break down.
"Not delivered"
Logistics business processes are key for most companies and are often attacked. Here are some of the attack scenarios that can occur.
Not available
If you work in the field of online commerce, then you are probably already familiar with the problem of fake orders. In the event of attacks, bots overload logistics resources and make goods inaccessible to other buyers. To do this, they place a huge number of fake orders equal to the maximum number of items in stock. These goods are then not paid for and after a while are returned to the site. But the job has already been done: they were marked as "out of stock", and some of the buyers have already gone to competitors. This tactic is well-known in the airline industry, where sometimes bots immediately “buy up” all tickets almost immediately after they appear. For example, one of our clients - a large airline - suffered from such an attack by Chinese competitors. In just two hours, their bots ordered 100% of tickets to certain destinations.
Sneakers bots
The next popular scenario is that bots instantly buy the entire line of products, and their owners sell them later at an inflated price (average mark-up is 200%). These bots are called sneakers bots because this problem is well known in the sneaker industry, especially in limited editions. Bots bought up newly appeared new lines in almost minutes, while blocking the resource so that real users could not break through. This is a rare case when bots have been featured in glossy fashion magazines. In general, though, ticket resellers for cool events like football matches use the same scenario.
Other scenarios
But that's not all. There is an even more complex version of attacks on logistics, which threatens with serious losses. This can be done if the service has the option “Payment upon receipt of goods”. Bots leave fake orders for such goods, indicating fake or even real addresses of unsuspecting people. And companies incur huge costs for delivery, storage, clarification of details. At this time, the goods are not available to other customers, and even take up space in the warehouse.
What else? Bots leave massive fake bad reviews about products, hamper the "chargeback" function, block transactions, steal customer data, spam real customers - there are many options. A good example is the recent attack on DHL, Hermes, AldiTalk, Freenet, Snipes.com. Hackers pretended tothat they were "testing DDoS protection systems," and eventually put down the company's business client portal and all the APIs. As a result, there were big disruptions in the delivery of goods to customers.
Call tomorrow
Last year, the Federal Trade Commission (FTC) reported a double increase in complaints from businesses and users about spam and fraudulent phone bot calls. By some estimates, they account for almost 50% of all calls.
As with DDoS, the targets of TDoS — massive bot attacks on phones — range from pranks to foul competition. Bots are able to overload contact centers and not miss real customers. This method is effective not only for call centers with live operators, but also where AVR systems are used. Bots can also massively attack other channels of communication with clients (chats, emails), disrupt CRM systems and even negatively affect HR management to some extent, because operators are overwhelmed trying to cope with the crisis. The attacks can also be synchronized with a traditional DDoS attack on the victim's online resources.
Recently, a similar attack disrupted 911 emergency services.in the US, ordinary people in dire need of help simply could not get through. Around the same time, Dublin Zoo met the same fate: at least 5,000 people received spam in the form of SMS text messages prompting them to urgently call the zoo's phone number and ask for a fictional person.
Wi-Fi will not be
Cybercriminals can also easily block an entire corporate network. IP blocking is often used to combat DDoS attacks. But this is not only ineffective, but also very dangerous practice. The IP address is easy to find (for example through resource monitoring) and easy to replace (or fake). Before joining Variti, our clients had cases where this led to the fact that blocking a certain IP simply turned off Wi-Fi in their own offices. There was a case when the client was “slipped” the required IP, and he blocked access to his resource for users from the whole region, and for a long time did not notice this, because otherwise the whole resource functioned perfectly.
What's new?
New threats require new security solutions. However, this new niche in the market is just beginning to form. There are many solutions for effectively repelling simple bot attacks, but with complex ones, everything is not so simple. Many solutions still practice IP blocking techniques. Others need time to collect primary data to get started, and these 10-15 minutes can become a vulnerability. There are solutions based on machine learning that allow you to identify a bot by its behavior. And at the same time, teams from the “other” side boast that they already have bots that can imitate real, indistinguishable from human patterns. It is not yet clear who will win.
What if you have to deal with professional bot teams and complex, multi-stage attacks on several levels at once?
Our experience shows that you need to focus on filtering illegal requests without blocking IP addresses. Complex DDoS attacks require filtering at several layers at once, including the transport layer, application layer, and APIs. Thanks to this, even low frequency attacks can be repelled, which are usually invisible and therefore often skipped further. Finally, it is necessary to let all real users pass, even while the attack is active.
Secondly, companies need the ability to create their own multi-stage protection systems, where, in addition to tools for preventing DDoS attacks, systems will be built in against fraud, data theft, content protection, and so on.
Third, they must work in real time from the very first request - the ability to instantly respond to security incidents greatly increases the chances of preventing an attack or reducing its destructive power.
The near future: reputation management and big data collection with bots
The history of DDoS has evolved from simple to complex. At first, the goal of the attackers was to stop the site from working. They now find it more efficient to target core business processes.
The complexity of attacks will continue to grow, this is inevitable. Plus what bad bots are doing now - data theft and falsification, extortion, spam bots - will collect data from a large number of sources (Big Data) and create “trusted” fake accounts to manage influence, reputation or mass phishing.
Currently, only large companies can afford to invest in DDoS and bot protection, but even they cannot always fully track and filter out traffic generated by bots. The only positive thing about bot attacks becoming more sophisticated is that it encourages the market to create smarter and better security solutions.
What do you think - how will the bot protection industry develop and what solutions are needed on the market right now?