The coronavirus has forced millions of people to work from home, and now a large group of companies obsessively advertise their programs to employers across the United States to track employee actions.
Often, advertisements for these services sound relatively harmless. Some manufacturers sell their software under the guise of "automatic time tracking" or "workplace analysis" tools. Others offer products to companies worried about possible data breaches or intellectual property theft. We will refer to all of these tools as bossware. Tracking, though designed to help employers, jeopardize the safety and privacy of workers by recording every mouse click and keystroke, secretly gathering information for future lawsuits, and other spy capabilities that go far beyond necessary and reasonable workforce management.
It is not right. When a home becomes an office, it never ceases to be a home. Workers should not be subject to unauthorized surveillance, or feel under a hood at home - just to keep their jobs.
What can they do?
Usually the tracker lives on a computer or smartphone, and uses privileges to access everything that happens on the device. Most of them track almost all user actions. We reviewed promotional materials, demos and user reviews to understand how these tools work. There are too many types of trackers to list all of them here, but we will try to sort the tracking systems into general categories.
The most extensive and common category of such programs is “activity tracking”. They usually list the applications and sites that employees visit. This may include a list of the recipients of their messages and emails - including the email headers and other metadata - and the posts they make on social media. Most trackers also record the level of keyboard and mouse input - for example, many tools provide a minute-by-minute layout of the number of keystrokes that can be used as a measure of productivity. The productivity tracker will try to collect all of this data into simple graphs or charts that give managers an overview of what employees are doing.
Each of the products we studied has the ability to frequently capture screenshots of an employee's device, and some even provide screen capture and live streaming of that video. The boss can review the snapshots sorted by timeline and examine what the employee was doing at any moment during the day. Some products act as key sequence recorders and record every keystroke, including unsent emails and personal passwords. A couple of programs even offer administrators the ability to take control of a user's desktop. Such products usually do not distinguish between work activity and personal account data, bank data, or health information.
Some trackers go even further, reaching out to the surrounding worker of the physical world. Mobile software companies almost always include GPS tracking. At least two services - StaffCop Enterprise and CleverControl - allow employers to secretly enable webcams and microphones on their employees' devices.
In general, there are two ways to deploy trackers: it is either an application that the employee can see (and sometimes control), or it is a secret background process that is not visible to the employee. Most of the companies we studied gave employers the opportunity to install their programs this way and that.
Visible surveillance
Sometimes employees can see a program tracking their actions. They may have the option to turn off surveillance, and this is often referred to as "entering the office" and "leaving the office." Naturally, if an employee turns off the program, it will be visible to the employer. For example, Time Doctor gives workers the ability to delete certain screenshots taken while they are working. However, deleting this snapshot will also delete the associated working time, so workers will only be credited with the time tracked by the program.
Employees can be given access to a specific piece of information collected about their work. Crossover, which offers WorkSmart, compares it to a fitness tracker for working on a computer. Its interface allows workers to look at the system outputs regarding their activity, presented in the form of graphs and diagrams.
Different companies offering tracking software offer different levels of transparency for employees. Some give employees access to some of the information, or even all of the information that goes to managers. Others, like Teramind, make it clear that they have turned on and collect data, but do not talk about what data they collect. In any case, it is often not entirely clear to the user what kind of data is being collected about him, unless he will ask his employer about it or carefully study the program itself.
Invisible surveillance
Most of the companies that make visible tracking software also make products that try to hide from the people they track. Teramind, Time Doctor, StaffCop and others produce trackers that make them as difficult as possible to detect and remove. From a technical point of view, these programs are no different from stalkerware - spyware for spying on people without their knowledge. Some companies even require employees to configure their antiviruses in a certain way before installing their programs so that they do not detect or block this software.
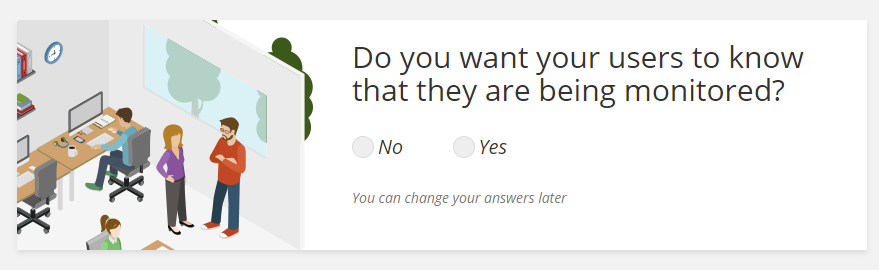
Part of the TimeDoctor registration procedure, where the employer chooses between visible and invisible tracking.
Such software is advertised as a tool for monitoring employees. However, most of these programs are actually surveillance tools for a wide range of uses. StaffCop offers a version of the program to track how children use the Internet at home, and ActivTrak says parents or school administrators can use their software to track their children. Judging by the reviews, many consumers use this software not for office needs.
Most companies offering invisible tracking mode recommend using it only on employer-owned devices. However, many offer features such as remote and "silent" installation, allowing software to be downloaded to workers' machines outside the office., without their knowledge. This works because many employers have administrative privileges on machines that they give their employees to use. However, some employees use their only laptop, so the company monitors the person all the time without interruption. This software has enormous potential for misuse by employers, school leaders and close partners. And the victim of surveillance may never know that she is being followed.
The table below summarizes the tracking and control capabilities for a small sample of tracker manufacturers. The list is not complete and may not provide a correct picture of the industry as a whole. We looked at companies that are referenced in industry guidelines and search results with informative publicly available marketing materials.
Common surveillance capabilities in monitoring software
Track app launches and website visits |
Screenshots or video recording |
Recording keystrokes |
Activating microphone and / or webcam |
Invisible mode of operation |
|
ActivTrak |
confirmed |
confirmed |
confirmed |
||
CleverControl |
confirmed |
confirmed |
confirmed |
confirmed ( 1 , 2 ) |
confirmed |
DeskTime |
confirmed |
confirmed |
confirmed |
||
Hubstaff |
confirmed |
confirmed |
|||
Interguard |
confirmed |
confirmed |
confirmed |
confirmed |
|
StaffCop |
confirmed |
confirmed |
confirmed |
confirmed ( 1 , 2 ) |
confirmed |
Teramind |
confirmed |
confirmed |
confirmed |
confirmed |
|
TimeDoctor |
confirmed |
confirmed |
confirmed |
||
Work Examiner |
confirmed |
confirmed |
confirmed |
confirmed |
|
WorkPuls |
confirmed |
confirmed |
confirmed |
How common are trackers?
The business of spying workers is not new, and even before the outbreak of the pandemic, it was quite large. While it is difficult to gauge the prevalence of trackers, they undoubtedly became more popular after workers were forced to switch to remote work due to the coronavirus. Awareness Technologies, which owns InterGuard, says it expanded its user base by 300% in the first few weeks of the outbreak. Many of the manufacturers we studied use the coronavirus in their advertising claims.
Tracks are used by some of the largest companies. Among Hubstaff clients listed Instacart, Groupon and Ring. Time doctorclaims to have 83,000 users; its clients include Allstate, Ericsson, Verizon and Re / Max. ActivTrak is used by more than 6,500 organizations, including Arizona State University, Amore University, and Denver and Malibu. Companies such as StaffCop and Teramind do not disclose customer information, but state that their areas of business include healthcare, banking, fashion, manufacturing and call centers. According to customer feedback , using sledilki can be judged on how they are using these programs.
We do not know how many of these organizations have chosen to use invisible tracking, since employers do not share such things. In addition, there is no reliable way for workers to find out, since many programs for invisible tracking are specially made so that they cannot be detected. Some workers have contracts in which they agree to certain tracking or prohibit other types of tracking. But many workers are simply unable to find out if they are being watched. If an employee is worried about being monitored, it is best to assume right away that a device given to him by his employer is tracking him.
What is the collected data used for?
Tracking manufacturers offer their software for a variety of applications. Some of the most common options are time tracking, productivity tracking, compliance with data protection laws, and preventing intellectual property theft. Some of these cases are legitimate: Companies handling sensitive data are often required by law to ensure that data does not leak or stolen from their computers. For employees working outside the office, this could mean a certain level of surveillance. However, an employer should not engage in any security surveillance unless it can demonstrate that it is necessary, proportionate and consistent with the problem it is trying to solve.
Unfortunately, many use cases give employers too much power over workers. Probably the largest class of products we've studied is designed for "productivity tracking" or advanced time tracking — that is, recording everything employees do to make sure they are working hard enough. Some companies furnish their software as if it is good for both managers and employees. They argue that gathering information about every second of an employee's workday helps not only the bosses, but the employees themselves. Other manufacturers, such as Work Examiner and StaffCop , directly advertise their services to managers who do not trust their employees. Such companies often recommend building strategiesdismissals or bonuses based on metrics issued by their products.
Promotional Material from the Work Examiner Home Page
Some firms advertise their products as tools for punishment, or to gather evidence for potential lawsuits. InterGuard tellsthat its software "can be installed remotely and covertly, in order to conduct covert investigations and collect irrefutable evidence without frightening off a potential criminal." She goes on to say that this evidence can be used in claims related to wrongful dismissals. In other words, InterGuard can supply employers with astronomical amounts of secretly collected personal information in order to then suppress attempts by employees to prove unfair treatment in court.
None of these use cases justify the amount of information trackers typically collect. Nothing can justify concealing the very fact of surveillance.
Most products take screenshots from time to time, and some programs let workers decide which screenshots they want to share. This means that in addition to snapshots of work letters or social media pages, there may be snapshots of sensitive banking, medical or other personal information. Programs that record keystrokes further interfere with privacy, and often end up recording passwords to employees' personal accounts.
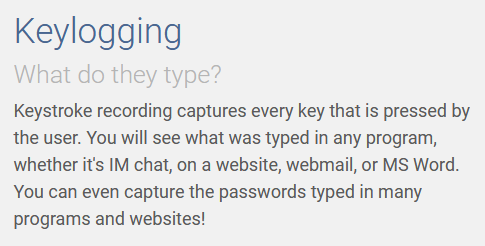
From Work Examiner: Keystroke Recording - What Are They Typing There?
Keystroke recording records all keystrokes made by the user. You will see what he typed in any program, be it messenger, website, webmail, or MS Word. You can even intercept passwords entered in programs and on websites!
Unfortunately, the collection of an excessive amount of information often does not happen by chance, but was originally conceived. Work Examiner directly advertises the ability to save employee personal passwords. Teramind reports all information that has been entered into the mailer - even if it is later removed. Several products extract text data from private messages on social media, so employers get even the most intimate information from users' private messages.
Let's be honest - these programs are specifically designed to help employers read their employees' private messages without their knowledge or consent. This, whatever one may say, is neither necessary nor ethical.
What can you do about it?
Under US law, employers have too much leeway to install tracking software on their own devices. There's also little stopping them from getting workers to install such software on their own devices (as long as it can be turned off during non-business hours). Different states have different rules about what employers can and cannot. However, workers often have very little legal opportunity to influence overly curious surveillance software.
This should change. Together with consumer privacy laws , states must protect workers from their employers. To start:
- Surveillance of employees, even those using employer-owned devices, should be as necessary and proportionate.
- , , .
- , .
- , .
In the meantime, workers who know they are being watched - and have no objection - should start talking to their employers. Companies that use trackers in their work should understand their goals and try to achieve them in less intrusive ways. Tracks often reward false productivity - for example, making people jerk and type every few minutes instead of pausing to think. Constant observation stifles creativity, diminishes trust, and leads to burnout. If employees are concerned about data security, they need to learn tools that are specifically tailored for real threats and minimize the risks of personal data leakage.
Many employees are uncomfortable expressing their opinions, and some suspect that their employer is secretly watching them. If they do not know the extent of this surveillance, they must assume that the devices are collecting all information - from the history of visits to the sites to private messages and passwords. Whenever possible, they should avoid using work computers for personal use. If employees are asked to install trackers on their personal devices, they can ask the employer to provide them with a separate work device, which will make it easier to separate personal information from work.
Finally, workers may be wary of talking about surveillance for fear of being kicked out of their jobs during a period of record unemployment [in the US, unemployment is over 11%]. The choice between obsessive surveillance and unemployment is hardly a choice.
The coronavirus has sent us all new challenges and is likely to fundamentally change the way we work. However, we must not allow him to usher in a new era of even more ubiquitous surveillance. We use electronic devices in our lives more than ever before. This means we have even more privacy rights in our digital lives - and no government, tech companies, or our employers should interfere.