<< Before: Statist
From about 1975 to 1995, computers became more widely available much faster than computer networks. First in the United States, and then in other rich countries, computers became commonplace for wealthy households, and appeared in almost all institutions. However, if the users of these computers had the desire to combine their machines - to exchange e-mail, download programs, search for communities to discuss their favorite hobbies - they did not have many options. Home users could connect to services like CompuServe. However, until in the late 1980s, services introduced a fixed monthly fee, the cost of connection was paid for every hour, and tariffs were not available to everyone. Some university students and faculty were able to connect to packet-switched networks,but for most it was not available. By 1981, only 280 computers had access to ARPANET. CSNET and BITNET will eventually include hundreds of computers, but they didn't start working until the early 1980s. At that time, there were more than 3,000 institutes in the United States where students received higher education, and almost all of them had several computers, from large mainframes to small workstations.
Communities, DIYers and scientists without access to the web turned to the same technical solutions that allowed them to communicate with each other. They hacked into the good old telephone system, Bell's network, turning it into something like a telegraph, transmitting digital messages instead of voices, and on their basis - messages from computer to computer throughout the country and around the world.
All articles of the cycle:
-
- « »,
- , ,
-
- ENIAC
-
-
- , .1
- , .2
- ARPANET —
- ARPANET —
- ARPANET —
-
These were some of the earliest decentralized [peer-to-peer, p2p] computer networks. Unlike CompuServe and other centralized systems, to which computers were connected, sucking information from them like calves are milk, information spread over decentralized networks in the manner of circles on water. It could start anywhere and come anywhere. And still, heated debates over politics and power arose in them. When the Internet attracted the attention of the community in the 1990s, many believed that it equalized social and economic ties. By allowing everyone to connect with everyone, the middlemen and bureaucrats who have dominated our lives will be cut off. A new era of direct democracy and open markets will come, where everyone will have equal votes and equal access. Such prophets might have refrained from such promises,by examining the fate of Usenet and Fidonet in the 1980s. Their technical structure was very flat, but any computer network is only part of the human community. And human communities, no matter how you stir and roll them, still remain full of lumps.
Usenet
In the summer of 1979, Tom Truscott's life was like the dream of any young computer enthusiast. He recently graduated in computer science from Duke University, had an interest in chess, and was an intern at Bell Labs headquarters in New Jersey. It was there that he had a chance to talk with the creators of Unix, the latest craze that swept the world of scientific computing.
The origins of Unix, like the Internet itself, lie in the shadow of American telecommunications policy. Ken Thompson and Dennis RitchieBell’s laboratories decided in the late 1960s to create a more flexible and truncated version of the massive MIT Multics system, which they participated in as programmers. The new OS quickly became a hit in the laboratories, gaining popularity both with modest requirements for hardware (thanks to which it was launched even on low-cost machines) and high flexibility. However, AT&T could not capitalize on this success. Under a 1956 agreement with the US Department of Justice, AT&T was required to license all non-telephony technology at reasonable prices and not engage in any business other than communications.
So AT&T started selling Unix licenses to universities for scientific use on very favorable terms. The first licensees to gain access to the source code began to create and sell their own Unix variants, of which it is worth noting the Berkeley Software Distribution (BSD) Unix, created on the flagship campus of the University of California. The new OS quickly swept over the academic community. Unlike other popular OSs like DEC TENEX / TOPS-20, it could run on hardware from various manufacturers, and many of these computers were quite inexpensive. Berkeley distributed the software at a negligible cost, in addition to the modest cost of a license from AT&T. Unfortunately, I could not find the exact numbers.
It seemed to Truscot that he was at the source of all things. He spent the summer as an intern at Ken Thompson, and began every day with several volleyball matches, then after midday he worked, and shared pizza dinner with his idols, then sat up late, writing down the code for Unix in C. At the end he didn’t want to lose contact with this world, so as soon as he returned to Duke University in the fall, he figured out how to connect a PDP 11/70 computer from the computer science department to the womb ship in Murray Hill using a program written by his former colleague , By Mike Lescom. The program was called uucp - Unix to Unix copy - and was one of a set of "uu" programs included in the recently released Unix version 7. The program allowed one Unix system to communicate with another over a modem. Specifically,uucp allowed files to be copied between two modem-connected computers, allowing Truscott to exchange emails with Thompson and Ritchie.

Tom Truscot
Jim Ellis, another PhD student at the Truscot Institute, installed a new version of Unix 7 on a Duke University computer. However, the update brought not only pros but also cons. Distributed by a group of Unix users, USENIX, a program designed to send news to all users of a particular Unix system, has stopped working in the new version. Traskot and Ellis decided to replace it with their own new program compatible with the 7th system, give it more interesting features, and return the improved version to the user community in exchange for prestige and honor.
At the same time, Traskot used uucp to communicate with a Unix-based machine at the University of North Carolina, 15 km southwest, in Chapel Hill, and chatted with local student Steve Belovin.
It is not known how Truscot and Belovin met, but it is possible that they became close on the basis of chess. Both of them participated in the annual Computer Systems Association chess tournament, although not at the same time.
Belovin also made his own program for distributing news, in which, interestingly, there was a concept of news groups, divided into topics that you could subscribe to - instead of one channel, into which all the news was dumped. Belovin, Truscott, and Ellis decided to join forces and write a web-based news system with newsgroups that would use uucp to spread news across multiple computers. They wanted to spread Unix-related news to USENIX users, so they called their system Usenet.
Duke University was to serve as a central clearing house, and use autodial and uucp to connect to all nodes on the network at regular intervals, pick up news updates, and send news to other network members. Belovin wrote the original code, but it worked on shell scripts, so it was very slow. Then Stephen Daniel, another graduate student at Duke University, rewrote the program in C. Daniel's version became known as A News. Ellis touted the program in January 1980 at the Usenix conference in Boulder, Colorado, and handed out all eighty copies of it brought with him. By the next Usenix conference in summer, the organizers had already included A News in their software package distributed to all participants.
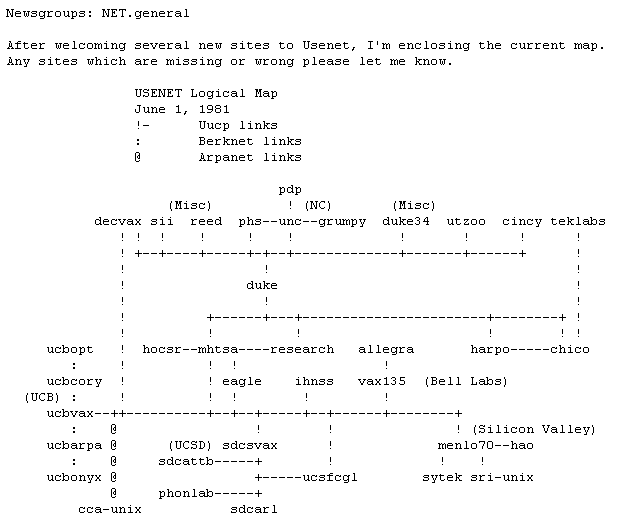
The creators described this system as "ARPANET for the Poor." You may not consider Duke University as some second-rate, but at that time he did not have such an influence in the world of computer science that would allow him to connect to this premium American computer network. But permission was not required to access Usenet — all that was needed was a Unix system, a modem, and the ability to pay phone bills for regularly broadcasting news. By the early 1980s, virtually all institutions offering higher education could meet these requirements.
Private companies also joined Usenet, accelerating the network's expansion. Digital Equipment Corporation (DEC) has agreed to take on the role of intermediary between Duke University and the University of California, Berkeley, reducing the cost of long distance and data bills between coasts. As a result, Berkeley on the west coast became Usenet's second hub, and connected the network with the University of California at San Francisco and San Diego, as well as other institutions, including Sytek, one of the first companies to do business related to LAN. Berkeley also hosted the ARPANET node, which allowed for a link between Usenet and ARPANET (after Mark Horton and Matt Glickman rewrote the news exchange once again, calling it B News). ARPANET nodes started typing content from Usenet and vice versa,although ARPA rules, strictly speaking, forbade communication with other networks. The network grew rapidly, from fifteen nodes processing ten posts per day in 1980, to 600 nodes and 120 posts in 1983, and then 5000 nodes and 1000 posts in 1987.
Initially, its creators saw Usenet as a way for members of the Unix user community to communicate and discuss the development of this OS. To do this, they created two groups, net.general and net.v7bugs (the latter discussed problems with the latest version). However, they left the system free to expand. Anyone could create a new group in the hierarchy of “net”, and users quickly began to add topics that were far from the technology, for example, net.jokes. Just as anyone could send anything, recipients could ignore groups of their choice. For example, the system could connect to Usenet and request data only for the net.v7bugs group, ignoring the rest of the content. Unlike the carefully planned ARPANET, Usenet organized on its own, and grew in an anarchist manner without supervision from above.
However, in this artificially democratic environment, a hierarchical order quickly emerged. A certain set of nodes with a lot of links and a lot of traffic came to be considered the backbone of the system. This process developed naturally. Since each transfer of data from one node to another added a communication delay, each new node connecting to the network wanted to contact a node that already had a large number of connections to minimize the number of "hops" required to propagate its messages over the network. Among the nodes of the ridge, there were both educational and corporate organizations, and usually every local computer was run by some wayward person who voluntarily took upon himself the ungrateful task of administering everything that passed through the computer.These were Gary Murakami of Bell Laboratories in Indian Hills, Illinois, or Gene Spafford of the Georgia Institute of Technology.
The most significant manifestation of the power of site administrators from this ridge came in 1987 when they pushed through the reorganization of the newsgroup namespace, introducing seven new first-level sections. There were sections like comp for computer topics, and rec for entertainment. The subsections were organized hierarchically under the Big Seven — for example, comp.lang.c for discussing the C language, and rec.games.board for discussing board games. The rebel group, who saw the change as a coup orchestrated by the Spine Clique, created their own offshoot of the hierarchy, whose head directory was alt, and their own parallel ridge. It included topics that were considered indecent for the Big Seven - for example, sex and soft drugs (alt.sex.pictures), as well as all sorts of bizarre communities,which administrators didn’t like with something (for example, alt.gourmand; admins preferred the harmless group rec.food.recipes).
By then, software supporting Usenet had expanded beyond the distribution of plain text, and introduced support for binary files (so named because they contained arbitrary binary digits). The most common files included pirated computer games, pornographic pictures and films, bootlegging live recordings and other illegal material. Groups in the alt.binaries hierarchy were among the most blocked on Usenet servers due to their combination of high cost (images and videos took up much more traffic and storage space than text) and disputed legal status.
But despite all this controversy, by the end of the 1980s, Usenet had become a place where computer experts could find international communities of like-minded people. In 1991 alone, Tim Berners-Lee announced the creation of the WWW in the alt.hypertext group; Linus Torvalds asked to leave feedback on his new small Linux project in the comp.os.minix group; Peter Adkison, thanks to a story about his gaming company, which he posted to the rec.games.design group, met Richard Garfield. Their collaboration led to the creation of the popular card game Magic: The Gathering.
Fidonet
However, while ARPANET for the poor was gradually spreading across the globe, microcomputer hobbyists, who had far fewer resources than a run-down college, were largely cut off from electronic communications. Unix, which was a cheap and angry option by academic standards, was not available to owners of 8-bit microprocessor computers running CP / M, which did little other than provide storage. However, they soon began their own simple experiment to create a very cheap decentralized network, and it all started with creating bulletin boards.
It is possible that due to the simplicity of the idea and the huge number of computer enthusiasts that existed at that time,electronic bulletin board (BBS) could be invented several times. But by tradition, the championship is recognized for the project of Word Christensen and Randy Sewess from Chicago, which they launched during a protracted snowstorm in 1978... Christensen and Sewess were computer enthusiasts, both were 30 years old, and both went to a local computer club. They had long planned to create their own server in the computer club where club members could upload news articles using modem file transfer software Christensen wrote for CP / M - the home equivalent of uucp. But the blizzard that held them home for several days gave them the incentive they needed to start working on it. Christensen was mainly involved in software, and Sewess - in iron. In particular, Sewess developed a scheme that automatically rebooted the computer from the running BBS program every time it detected an incoming call. This hack was necessary in orderso that the system is guaranteed to be in a suitable state to receive this call - such was the precarious state of home hardware and software in those days. They called their invention CBBS, a computerized bulletin board, but later most system operators (or sysops) dropped C for short and called their service simply BBS. At first, BBS were also called RCP / M, that is, remote CP / M (remote CP / M). They described the details of their creation in the popular computer magazine Byte, and soon a crowd of imitators followed.They described the details of their creation in the popular computer magazine Byte, and soon a crowd of imitators followed.The details of their offspring, they described in the popular magazine for computer engineers Byte, and soon a crowd of imitators followed.
A new device - Hayes Modem - fertilized the blooming BBS scene. Dennis Hayes was another computer fanatic, and he really wanted to connect a modem to his new machine. But commercially available commercials fell into only two categories: devices intended for business buyers, and therefore too expensive for home hobbyists, and modems with acoustic communication.... To communicate with someone using an acoustic modem, you first had to call someone on the phone or answer the call, and then hang up the phone on the modem so that he could communicate with the modem on the other end. It was not possible to automate an outgoing or incoming call in this way. So in 1977, Hayes designed, made, and began selling his own 300 bps data modem that could be plugged into his computer. Christensen and Sewess used one of these early Hayes modem in their BBS. However, the first breakthrough product of Hayes was the 1981 Smartmodem, which was delivered in a separate case, with its own microprocessor, and connected to the computer via a serial port. It sold for $ 299, which was quite affordable for amateurs,who usually spent several hundred dollars on their home computers.

Hayes Smartmodem for 300 baud
One of them was Tom Jennings, and it was he who launched the project, which became something like Usenet for BBS. He worked as a programmer at Phoenix Software in San Francisco, and in 1983 decided to write his own program for the BBS, not just for CP / M, but for the newest and best OS for microcomputers - Microsoft DOS. He named it Fido [a typical name for a dog], after the computer he used at work, so named because it consisted of an eerie jumble of components. John Madil, a salesman at ComputerLand in Baltimore, found out about Fido and called Jennings across the country to ask him to help him modify his software to run on his DEC Rainbow 100 computer. The couple began to collaborate on software and then to they were joined by another Rainbow fan, Ben Baker from St. Louis.The trio spent a significant amount of money on long distance calls while they called each other's cars at night to chat in chats.
In the process of all these negotiations on different BBSs, Jennings began to have an idea in his head - he could create a whole network of BBSs that would exchange messages at night when the cost of long-distance communication was low. This idea was not new - many amateurs imagined such a message passing between BBS, since the appearance of the article by Christensen and Sewess in Byte. However, they generally assumed that for this scheme to work, one must first achieve very high BBS density and build complex routing rules so that all calls remain local, that is, inexpensive, even when passing messages from coast to coast. However, Jennings made quick calculations and realizedthat with the increased speed of modems (amateur modems were already working at a speed of 1200 bps) and decreasing long-distance tariffs, such tricks were no longer needed. Even with a significant increase in message traffic, it was possible to transfer texts between systems, spending only a few bucks a night.

Tom Jennings, frame from a 2002 documentary
Then he added another program to Fido. From one o'clock until two in the night Fido was closed and started by FidoNet. She checked the list of outgoing messages in the host list file. Each outgoing message had a node number, and each element of the list denoted a network node - Fido BBS - which had a phone number nearby. If outgoing messages were found, FidoNet took turns dialing the phones of the corresponding BBS from the list of sites and passing them on to the FidoNet program that was waiting for a call from that side. Suddenly, Madill, Jennings and Baker were able to work together easily and simply, albeit at the cost of delayed reactions. They did not receive messages during the day; messages were transmitted at night.
Previously, amateurs rarely contacted other amateurs in other areas, as they mostly called local BBSs for free. But if this BBS was connected to FidoNet, then users were suddenly able to exchange emails with other people across the country. The scheme immediately turned out to be incredibly popular, and the number of FidoNet users began to grow rapidly, and in a year reached 200. In this regard, Jennings was getting worse and worse at managing her own site. So during the first FidoCon meeting in St. Louis, Jennings and Baker met with Ken Kaplan, another DEC Rainbow fan who soon took on an important role in the leadership of FidoNet. They came up with a new scheme dividing North America into subnets, each with local nodes.On each of the subnets, one administrative node took responsibility for managing the local host list, accepting incoming traffic for its subnet, and relaying messages to the appropriate local hosts. Above the layer of subnets were zones covering the entire continent. At the same time, the system still supported one global list of nodes, containing the phone numbers of all computers connected to FidoNet in the world, so theoretically any node could directly call any other to deliver messages.containing the phone numbers of all computers connected to FidoNet in the world, so theoretically any node could directly call any other to deliver messages.containing the phone numbers of all computers connected to FidoNet in the world, so theoretically any node could directly call any other to deliver messages.
The new architecture allowed the system to continue to grow, and by 1986 it had increased to 1,000 nodes, and by 1989 to 5,000. Each of these nodes (which was a BBS) had an average of 100 active users. The two most popular applications were the simplest mail exchange Jennings built into FidoNet, and Echomail, created by Jeff Rush, a BBS sysop from Dallas. Echomail was the functional equivalent of Usenet newsgroups, and allowed thousands of FidoNet users to conduct public discussions on various topics. Echoes, as the individual groups were called, had single names, as opposed to the hierarchical Usenet system, from AD&D to MILHISTORY and ZYMURGY (home brewing).
Jennings' philosophical views gravitated towards anarchy, and he wanted to create a neutral platform governed only by technical standards:
I told users that they could do whatever they wanted. I have been holding this point of view for eight years, and I had no problems supporting BBS. Only people with fascist inclinations seeking to keep everything under control have problems. I believe that if you clearly state that the callers are following the rules - it's even unpleasant for me to talk about it - if the callers define the content, then they will be able to rebuff all the goats.
However, as with Usenet, FidoNet’s hierarchical structure has enabled some sysops to gain more power than others, and rumors have circulated about the emergence of a powerful clique (this time based in St. Louis) that wants to take control of the network from people. Many feared that Kaplan or others around him would try to commercialize the system and start charging money for using FidoNet. Particularly suspicious was the International FidoNet Association (IFNA), a not-for-profit association that Kaplan founded to pay for a fraction of the cost of maintaining the system (especially long distance calls). In 1989, it seemed that these suspicions were realized when the IFNA group of leaders put forward a referendum to make every FidoNet sysop a member of IFNA,and make the association the official organization that manages the network and is responsible for all its rules and regulations. The idea failed and IFNA disappeared. Of course, the absence of a symbolic governing structure did not mean that there was no real power in the network; regional site list administrators introduced their own arbitrary rules.
Internet shadow
From the late 1980s onward, FidoNet and Usenet gradually began to overshadow the Internet's shadow. By the second half of the next decade, they were completely absorbed in it.
Usenet became intertwined with Internet websites through the creation of NNTP, a network news transfer protocol, in early 1986. It was conceived by a couple of UC students (one from the San Diego branch, the other from Berkeley). NNTP allowed TCP / IP network nodes on the Internet to create Usenet-compatible news servers. For several years, most of Usenet traffic has already gone through these nodes, and not through uucp over the good old telephone network. The independent uucp network gradually waned, and Usenet became the next application running over TCP / IP. The incredible flexibility of the Internet's layered architecture easily allowed it to absorb networks tailored for a single application.
Although there were several gateways between FidoNet and the Internet in the early 1990s that allowed networks to exchange messages, FidoNet was not the only application, so its traffic did not migrate to the Internet the way it did with Usenet. Instead, when people outside of academia first began to study Internet access in the second half of the 1990s, BBS gradually either became absorbed in the Internet or became unnecessary. Commercial BBS gradually fell into the first category. These mini-copies of CompuServes offered access to the BBS for a monthly fee to thousands of users, and they had multiple modems to receive multiple incoming calls at the same time. With the advent of commercial Internet access, these businesses connected their BBSs to the nearest part of the Internet and began offering access to it to their customers as a subscription.The more sites and services appearing on the booming World Wide Web, the fewer users are subscribing to specific BBS services, and therefore these commercial BBSs have gradually turned into simple Internet service providers, ISPs. Much of the amateur BBS has become ghost towns as users looking to get online moved to local ISPs as well as affiliates of larger organizations like America Online.and branch offices of larger organizations such as America Online.as well as branches of larger organizations such as America Online.
All this is wonderful, but how did the Internet take such a dominant position? How did the little-known academic system spread over elite universities for years, while systems like Minitel, CompuServe, and Usenet attracted millions of users, suddenly burst into the foreground and spread like a weed, absorbing everything that came before it? How has the Internet become the force that has completed the era of fragmentation?
What else to read and see
- Ronda Hauben and Michael Hauben, Netizens: On the History and Impact of Usenet and the Internet, (online 1994, print 1997)
- Howard Rheingold, The Virtual Community (1993)
- Peter H. Salus, Casting the Net (1995)
- Jason Scott, BBS: The Documentary (2005)