
We tell how we implemented a system of electronic registration of visits with biometric technologies in the data center: why it was needed, why we again developed our own solution and what advantages we got.
entrance and exit
Access of visitors to a commercial data center is an important point in the organization of the facility. The data center's security policy requires accurate tracking of visits and tracking dynamics.
Several years ago, at Linxdatacenter, we decided to completely digitalize all statistics of visits to our data center in St. Petersburg. We abandoned the traditional registration of access - namely, filling out the visit log, maintaining a paper archive and presenting documents at each visit.
In 4 months our technical specialists developed a system of electronic registration of visits in combination with biometric access control technologies. The main task was to create a modern tool that meets our safety requirements and at the same time is convenient for visitors.
The system provided full transparency of the picture of visits to the data center. Who, when and where got access to the data center, including server racks - all this information became available instantly upon request. Attendance statistics are downloaded from the system in a few clicks - it has become much easier to prepare reports for clients and auditors of certifying organizations.
The starting point
At the first stage, a solution was developed that made it possible to enter all the necessary data on the tablet when entering the data center.
Authorization took place by entering the visitor's personal data. Then the tablet exchanged data with the computer at the security post via a dedicated secure communication channel. Then a pass was issued.
The system took into account two main types of requests: an application for temporary access (one-time visit) and an application for permanent access. Organizational procedures for these types of applications in the data center differ significantly:
- The application for temporary access indicates the name and company of the visitor, as well as the contact person who must accompany him throughout the visit to the data center.
- Permanent access allows the visitor to independently move within the data center (for example, this is important for customer specialists who regularly come to work with equipment in the data center). This level of access requires a person to undergo an introductory briefing on labor protection and sign an agreement with Linxdatacenter on the transfer of personal and biometric data (fingerprint scan, photograph), and also implies the receipt of the entire necessary package of documents about the rules of work in the data center by e-mail.
When registering permanent access, the need to fill out an application each time and confirm the identity with documents completely disappears, just put your finger to authorize at the entrance.

Change!
The platform on which we deployed the first version of the system is the Jotform builder. The solution is used to create polls, we independently modified it for the registration system.
However, over time, during operation, some bottlenecks and points for further development of the solution emerged.
The first difficulty is that Jotform was not "finalized" for the tablet format, and the forms to fill after reloading the page often "floated" in size, going beyond the screen, or vice versa, collapsed. This created a lot of inconvenience during registration.
There was no mobile application either; the system interface had to be deployed on a tablet in a "kiosk" format. However, this limitation played into the hands - in the "kiosk" mode, the application cannot be minimized or closed on the tablet without the Administrator level permission, which allowed us to use a regular user tablet as a registration terminal for accessing the data center.
During the testing process, multiple bugs began to surface. Numerous platform updates caused the solution to freeze and crash. This happened especially often at the moments when the updates covered those modules on which the functionality of our registration mechanism was deployed. For example, the questionnaires filled out by visitors were not sent to the security point, were lost, etc.
The smooth operation of the registration system is extremely important since both employees and customers use the service every day. And for the periods of "freezing" the whole process had to be returned to 100% paper format, which was an unacceptable archaism, led to errors and in general looked like a huge step back.
At some point, Jotform released a mobile version, but this upgrade did not solve all our problems. So, we had to “cross” one form with another among ourselves, for example, for the tasks of training and induction coaching on the basis of the test.
Even with the paid version, an additional extended Pro license was required for all of our clearance tasks. The final “price / quality” ratio turned out to be far from optimal - we got expensive excess functionality, which still required significant improvements on our part.
Version 2.0, or Do It Yourself
After analyzing the situation, we came to the conclusion that the easiest and most reliable way out is to create our own solution and transfer the functional part of the system to a virtual machine in its own cloud.
We ourselves wrote the software for forms in React, deployed all this using Kubernetes, in production at our facilities, and as a result got our own, independent from third-party developers, a system for registering access to the data center.

In the new version, we finalized the form for convenient registration of permanent passes. When filling out a form for access to the data center, the client can go to another application, undergo express training on the rules of finding in the data center and testing, and then return back to the "perimeter" of the form on the tablet and complete the registration. Moreover, the visitor himself does not notice this movement between applications!
The project was implemented quite quickly: the creation of a basic form for admission to the data center and its deployment in a productive environment took only a month. From the moment of launch until today, we have not registered a single failure, let alone a "crash" of the system, and saved ourselves from minor troubles like the interface mismatch with the screen size.
Whack - and you're done
Within a month after deployment, we transferred to the own platform all the forms we need in the work:
- Access to the data center,
- Application for the production of work,
- Induction training.
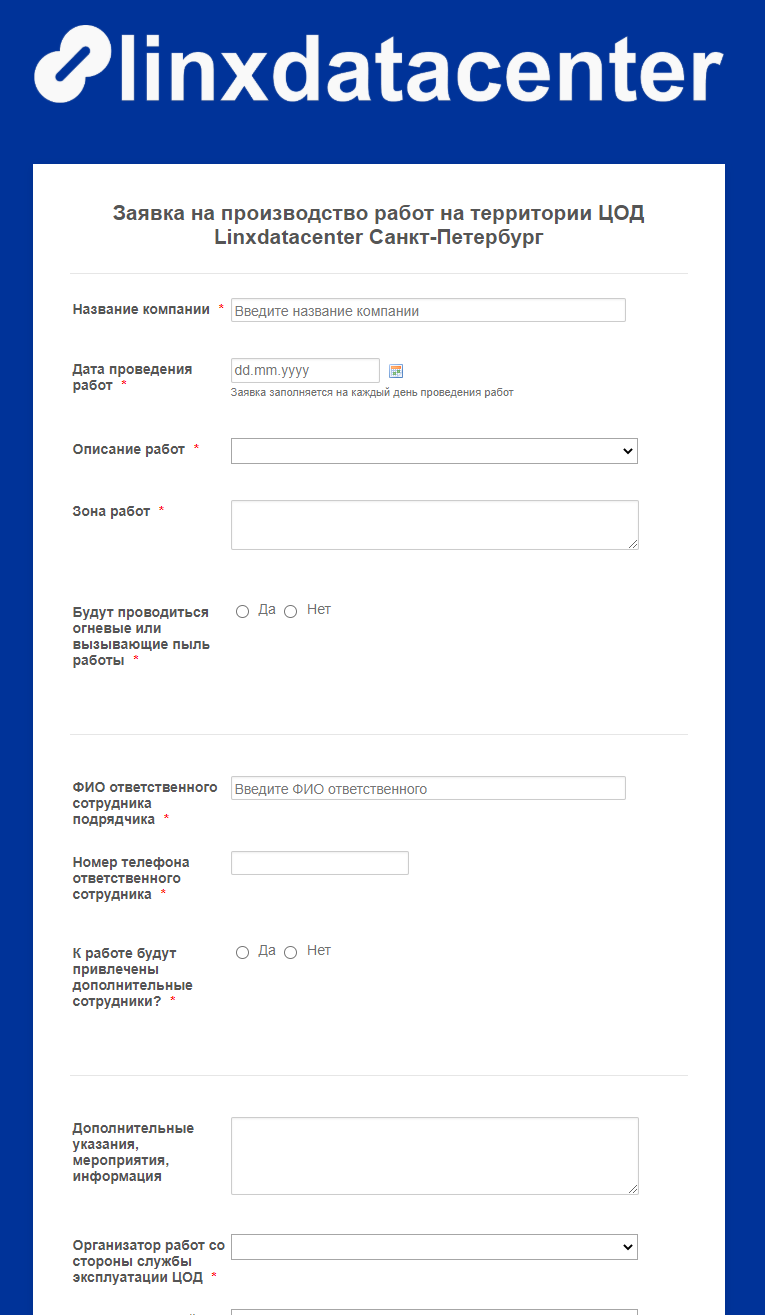
This is how the application form for the production of work in the data center looks like.
The system is deployed in our cloud in St. Petersburg. We fully control the operation of the VM, all IT resources are reserved, and this gives us confidence that the system will not break down and will not lose data in any scenario.
The software for the system is deployed in a Docker container in its own repository of the data center - this greatly simplifies the system configuration when adding new functions, editing existing capabilities, and also in the future will make it easier to update, scale, etc.
The system requires a minimum amount of data center IT resources, while fully meeting our requirements in terms of functionality and reliability.
What's now and what's next?
In general, the admission procedure remains the same: an electronic application form is filled in, then the data of visitors "fly away" to the security post (name, company, position, purpose of the visit, accompanying person in the data center, etc.), a check with the lists takes place and a decision is made on admission.

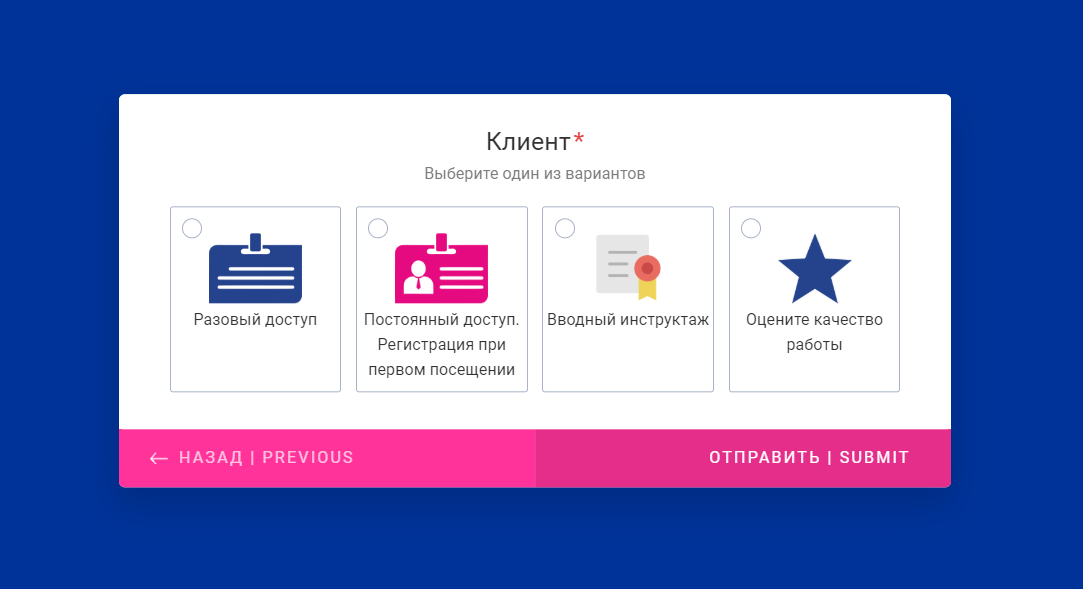
What else can the system do? Any analytic tasks in historical perspective, as well as monitoring. Some customers request reports for internal staff control purposes. We use this system to track the periods of maximum attendance, which allows us to more efficiently plan work in the data center.
Future plans include transferring all existing checklists into the system - for example, the process of preparing a new rack. The data center has a regulated sequence of steps to prepare the rack for the client. It details what exactly and in what order needs to be done before starting - power requirements, how many remote controllers and patch panels for switching to bring, which plugs to remove, whether to install access control systems, video surveillance, etc. Now all this is being implemented as part of a paper workflow and partly on an electronic platform, but the company's processes are already ripe for the complete migration of maintenance and control of such tasks into a digital format and a web interface.
In this direction, our solution will develop further, covering new back-office processes and tasks.