
The analytics we provide below are based on data from attacks on Rostelecom networks from January to May 2020.
How the number of attacks changed
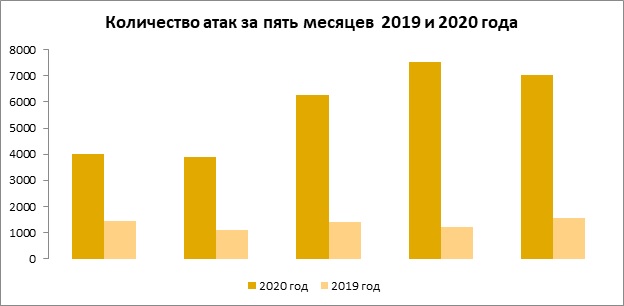
So. In March-May 2020, the number of DDoS attacks increased 5 times in comparison with the same period last year. In general, in the first five months of 2020, the total number of such attacks year-over-year increased by more than 4 times.
It is clearly seen how cybercriminals increased their activity with the introduction of quarantine measures. The peak was in April, when the number of attacks increased by 88% compared to January. It is worth noting here that a year earlier the dynamics were not so bright, and the number of attacks from month to month remained the same plus or minus.
During the period of self-isolation, the nature of Internet traffic also changed. Many organizations that previously worked only offline have launched their own Internet resources
Attack characteristics
With a sharp increase in the number of DDoS attacks, their complexity and power have generally decreased. Basically, the attackers used ordinary DNS or NTP amplification of small volumes (up to 3 Gb / s).
It is noteworthy that at the end of 2019, we recorded an opposite trend: a sharp increase in power and the technical complexity of attacks. During the pandemic, the number of such did not decrease, but the share as a whole fell against the background of a sharp increase in simple "worker-peasant" DDoS attacks. This once again indicates that during the self-isolation, it was not the “pros” who were especially active, but rather the “amateurs” who decided to take advantage of the situation.
Who were hunted
As we said above, in the first five months the attackers' interest in educational resources sharply increased. Taking into account the fact that in most cases "junk" traffic was sent by clearly "amateurs", conclusions about the organizers suggest themselves (and yes - this is not a diary to hide under your bed or warm a thermometer in order to avoid the control one).
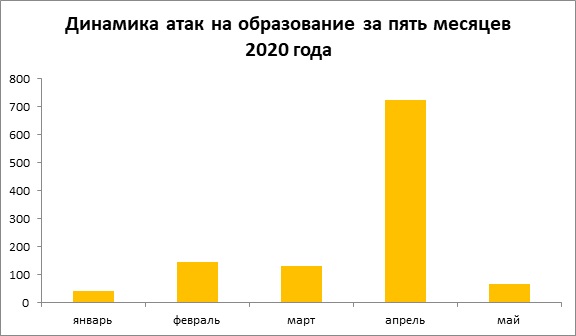
But DDoS was not the only school. The number of attacks on state institutions also increased - in April more than 3 times compared to March.

The third industry with the most pronounced dynamics was gaming (the growth of attacks in April was almost 3 times in comparison with March). The isolation mode attracted not only a lot of new users to this industry, but also

Despite the fact that overall attack power fell during the reporting period, telecom operators and data centers stood out in the general statistics: 150+ GB attacks more often than usual. DDoS in these two segments makes it possible to disable not one specific site, but to “wholesale” the operator's customers and the resources served by the data center. Moreover, such companies are better protected than, for example, state institutions or the educational segment. Therefore, attackers have to use more sophisticated tools. During the pandemic, attacks on these two segments were fast and powerful and were carried out, most likely, through real hosts assembled into one botnet with the ability to redirect it to a new victim in a matter of minutes.
In general, such a division by industry continues the trend that was formed back in 2019. For example, in 2018, the telecom industry accounted for only 10% of all DDoS attacks, and in 2019 - already 31%. Small regional Internet providers, hosting services and data centers, which usually do not have the resources necessary to repel attacks, became targets of hackers.
Total
- During the quarantine period, against the backdrop of the spread of COVID-19 (March-May 2020), five times more DDoS attacks were recorded than a year earlier.
- The share of simple and low-power attacks has increased, which indicates the activity of “non-professional” attackers.
- The number of attacks on educational resources increased by 5.5 times, and the most powerful attacks in the reporting period fell on telecom operators and data centers.

The largest volume of attacks in March-May occurred in the online trading sector (31%), which is traditionally one of the main targets for DDoS. The public sector became the second most popular (21% of attacks). This is followed by the financial sector (17%), telecom (15%), education (9%) and the gaming segment (7%).
The most difficult month for the owners of Internet resources was April, when in Russia there was a strict regime of self-isolation. In May, the activity of the deserters gradually began to decline - this trend will continue further if the situation in Russia and the world stabilizes. It is also possible to predict a decrease in the number of attacks in the field of education when the entrance and final exams are over.
However, as the past quarantine showed, it is impossible to predict for sure when exactly DDoS will come to the company, so it is better to lay the straw in advance.