
As you already know, the focus of Acronis today lies in the plane of integrated cyber defense. That is why we not only provide direct data protection, but also study possible threats and vulnerabilities. Acronis CPOC's proprietary security center analyzes global traffic, and our experts study various products - software and hardware.
One of these studies was attended by CISO Acronis Kevin Reed, security researcher Alex Koshelev, and senior security researcher Ravikant Tiwari. Our guys discovered 4 vulnerabilities in GeoVision products that allow access to security devices - IP cameras and fingerprint scanners.
During a routine security audit, a backdoor with administrator rights to manage devices was found, and facts of reusing the same cryptographic keys for authentication via the SSH protocol were discovered. In addition, the attackers had the opportunity to gain access to the system logs on the device without any authentication at all. The most dangerous vulnerability is the lack of protection against buffer overflows, as a result of which an attacker could gain complete control over the device.
Worst of all, the vulnerabilities were discovered back in August 2019 and, according to ethical standards, we notified the manufacturer and began to wait for the release of patches to fix these problems. However, the manufacturer for some reason decided not to rush with corrections.
- 2019 GeoVision
- 2019 90-
- 2019, , Singapore Computer Emergency Response Team (SingCERT). , SingCERT TWCERT
- 2020 4 , … . GeoVision
- TWCERT , GeoVision - .
30.06.2020
What devices were affected
The detected vulnerabilities affect at least six device models, including fingerprint scanners, access card scanners and control devices for access control systems. These are thousands of already installed and used security systems that can be easily compromised by fraudsters and cybercriminals.
Acronis researchers studied a device provided by a Singapore company (our CPOC is located in Singapore). But potentially hacked devices are already on the Shodan list, and you can look at the Shodan tracker distribution of dangerous devices in different regions of the world.
Technical details
If you use GeoVision devices in your work, you should pay attention to the following firmware versions, for which the presence of vulnerabilities has been confirmed:
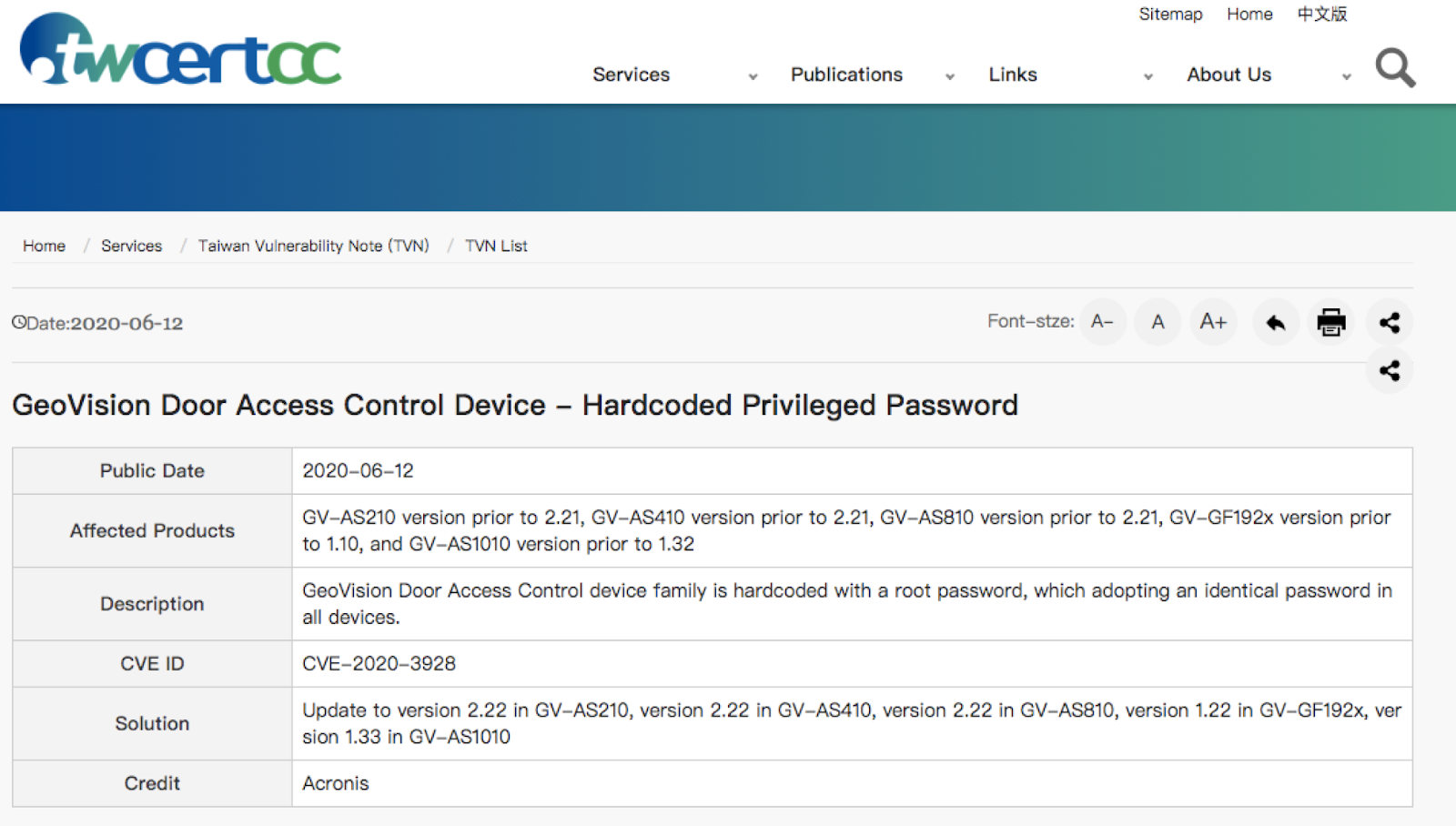
1. Availability of undocumented standard login and password for GeoVision products (CVE ID CVE-2020-3928 )
You can log in with a standard username and password remotely to GeoVision devices with the following firmware:
- GV-AS210 ( http://classic.geovision.com.tw/english/Prod_GVAS210.asp ) versions 2.20, 2.21
- GV-AS410 ( http://classic.geovision.com.tw/english/Prod_GVAS410.asp ) versions 2.20, 2.21
- GV-AS810 ( http://classic.geovision.com.tw/english/Prod_GVAS810.asp ) version 2.20, 2.21
- GV-GF192x ( http://www.geovision.com.tw/product/GV-GF1921%20GV-GF1922 ) version 1.10
- GV-AS1010 ( http://www.geovision.com.tw/product/GV-AS1010 ) version 1.32
By default, SSH server is not running on these devices. However, there is a hidden URL in the device management console [https: //%3cip.of.the.device%3e/isshd.htm]. If you follow this link, the Dropbear SSH service will be launched on port 8009
Yes, you need to know the password to the device management console to make a request for the URL. But since the standard pair for GeoVision devices (admin: admin) is most often not changed, it is not difficult to get root rights to manage the device.
2. Standard cryptographic keys (CVE ID CVE-2020-3929 )
A number of firmware for GeoVision products use wired standard cryptographic keys for connecting via SSH and HTTPs:
- GV-AS210 ( http://classic.geovision.com.tw/english/Prod_GVAS210.asp ) versions 2.20, 2.21
- GV-AS410 ( http://classic.geovision.com.tw/english/Prod_GVAS410.asp ) versions 2.20, 2.21
- GV-AS810 ( http://classic.geovision.com.tw/english/Prod_GVAS810.asp ) version 2.20, 2.21
- GV-GF192x ( http://www.geovision.com.tw/product/GV-GF1921%20GV-GF1922 ) version 1.10
- GV-AS1010 ( http://www.geovision.com.tw/product/GV-AS1010 ) version 1.32
Since anyone can get a cryptographic key, there is a risk of Man-in-the-Middle attacks.
3. Danger of information leakage (CVE ID CVE-2020-3930 )
GV-GF192x Firmware GF192x ( http://www.geovision.com.tw/product/GV-GF1921%20GV-GF1922 ) version 1.10 allows you to access protocols via a web interface without any complexity at all. There is no authorization to view the logs. To do this, just go to the following links:
[http://%3cip.of.the.device%3e/messages.txt] [http://%3cip.of.the.device%3e/messages.old.txt]
It is also highly likely that a similar security flaw is characteristic of other devices. Of course, we can assume that reading the protocols does not pose a great threat. But in the presence of multiple vulnerabilities, studying the operation of the device helps to plan an attack most effectively.
4. Buffer overflow allowing full access to the device
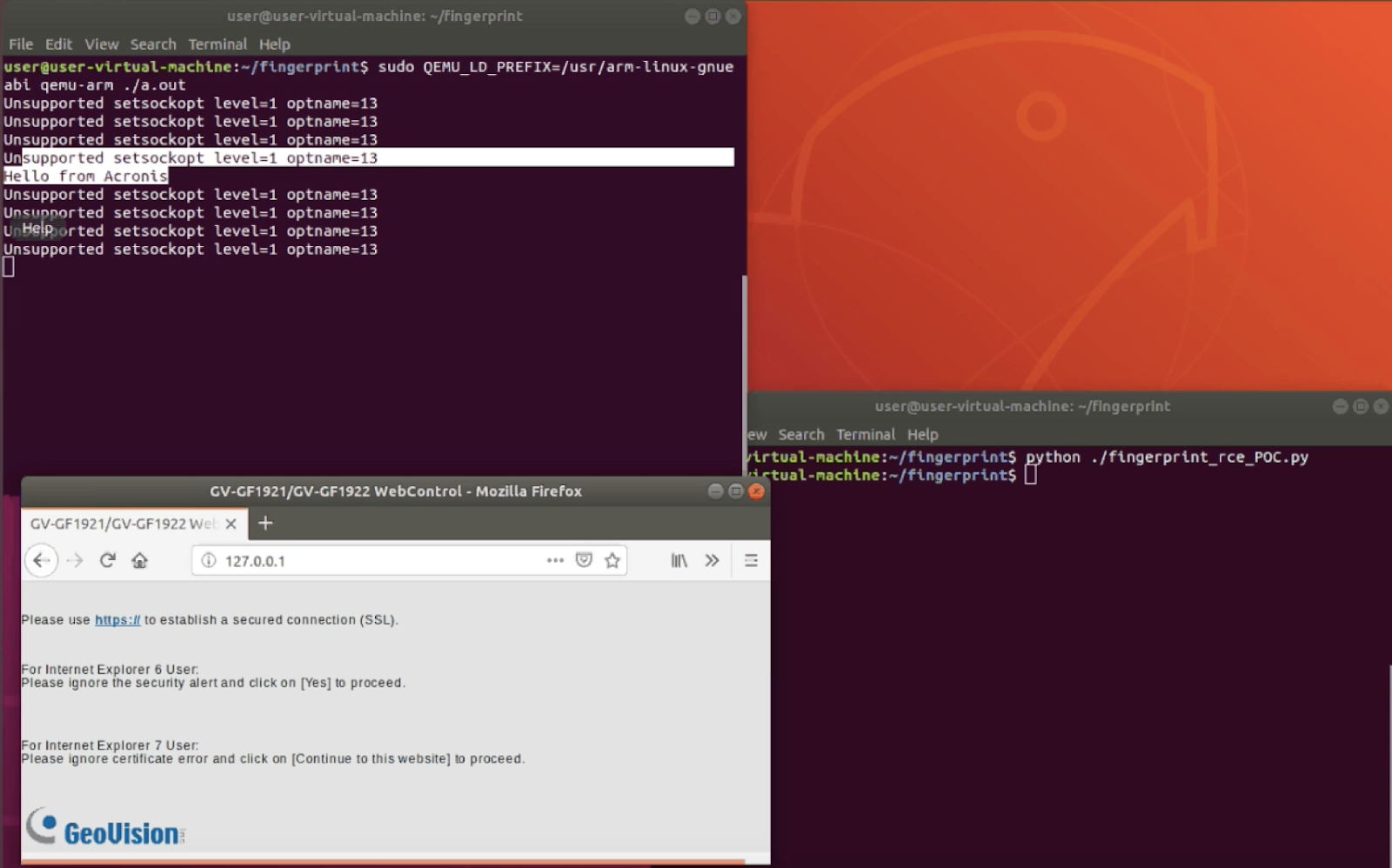
Firmware GV-GF192x ( http://www.geovision.com.tw/product/GV-GF1921%20GV-GF1922 ) version 1.10 allows you to run arbitrary code on the device. At the same time, there are suspicions that the same vulnerability may be found in other firmware of the manufacturer.
When you go to the address / usr / bin / port80 (SHA256: 5B531E50CFA347BBE3B9C667F8D802CDECC6B1CD270719DAC5ECE4CE33696D3A), you can install your own firmware to compromise the security system or install spyware. This does not require any authentication.
This vulnerability was rated 10/10 according to CVSS criteria, as it allows you to get full control over the device, reprogram the protocols and run your commands.
The exploit allows the user to overflow the memory buffer provided for the "Host" header. In this way, you can overwrite the structure responsible for memory allocation. And if an attacker changes pointers in this structure, he can submit his own code for execution. For example, this action might look like this.
“Host: “ + free_space + pointer_to_new_heap(only first free bytes!) + “\r\n” + our_list_of_chunks + free_space.Instead of "free space", you can place your own code (our researchers used the second part of free space in memory. As a result, part of the command
(“Host: “ + free_space + pointer_to_new_heap(only first free bytes!)gets into the g_Host buffer, and pointers to the next commands are overwritten.
Is it really dangerous?
Considering that we are talking about those IoT devices that should be responsible for the safety of people, the discovered vulnerabilities really expose users to risks. What can be done with GeoVision devices if these vulnerabilities are exploited?
- Remotely open doors to enclosed spaces without access cards
- Install Trojans and monitor various network traffic
- Track users and steal their biometric data while remaining completely unnoticed
- Use stolen fingerprints to access other doors
- Conduct transactions and take actions on behalf of the victim using biometrics
The lack of desire to release updates as quickly as possible causes misunderstanding among information security experts. This proves once again that even IoT devices built for security do not guarantee real protection. And the more smart devices (and potential backdoors) appear in our environment, the higher the need for comprehensive cyber defense, which includes countering all five vectors of threats , becomes .